
2024 has started off dramatic shifts in the ransomware landscape. In December of 2023 international law enforcement took down the BlackCat leaks site, leading to the group removing all ethical restrictions for their affiliates and declaring all organizations in Western Europe and the United States viable targets to include nuclear power plants and childrens hospitals.
Weeks later a mysterious post appeared on the dark web forums RAMP, XSS, and Breach, claiming to be selling data from a ransomware attack perpetrated against the Russian company AN-SECURITY[.].ru, using LockBit ransomware.
Even more recently the LockBitSupp account was banned from one of the primary Russian language cybercrime forums for scamming an initial access broker, soon after followed by a law enforcement takedown of the LockBit blog.
Each of these events is interesting in turn, but together they paint a broader picture of a ransomware ecosystem undergoing a period of turbulence and a radical shift. The Flare Research team delved into various forums across the dark web to investigate. This article is going to explore each event in turn, and focus on explanatory factors that provide the “why” for the rapid change in the ecosystem. First we’ll provide a brief summary of each event before providing conclusions at the end.
The December 2023 Alphv Takedown
BlackCat is one of the largest Ransomware en tant que service (RaaS) groups in the ecosystem, second only to LockBit in number of attacks perpetrated in 2023. BlackCat is a Russian ransomware as a service group and operates on an affiliate model in which the group provides the ransomware application and other threat actors launch attacks and split the profit of ransom payments.
In December 2023 the FBI working with international law enforcement successfully compromised BlackCat’s infrastructure. According to the U.S. Department of Justice Press release on the takedown:
The FBI developed a decryption tool that allowed FBI field offices across the country and law enforcement partners around the world to offer over 500 affected victims the capability to restore their systems. To date, the FBI has worked with dozens of victims in the United States and internationally to implement this solution, saving multiple victims from ransom demands totaling approximately $68 million
Weeks later BlackCat posted the message below announcing that affiliates would get up to 90% of ransom payments and that they were removing all targeting restrictions from affiliates.
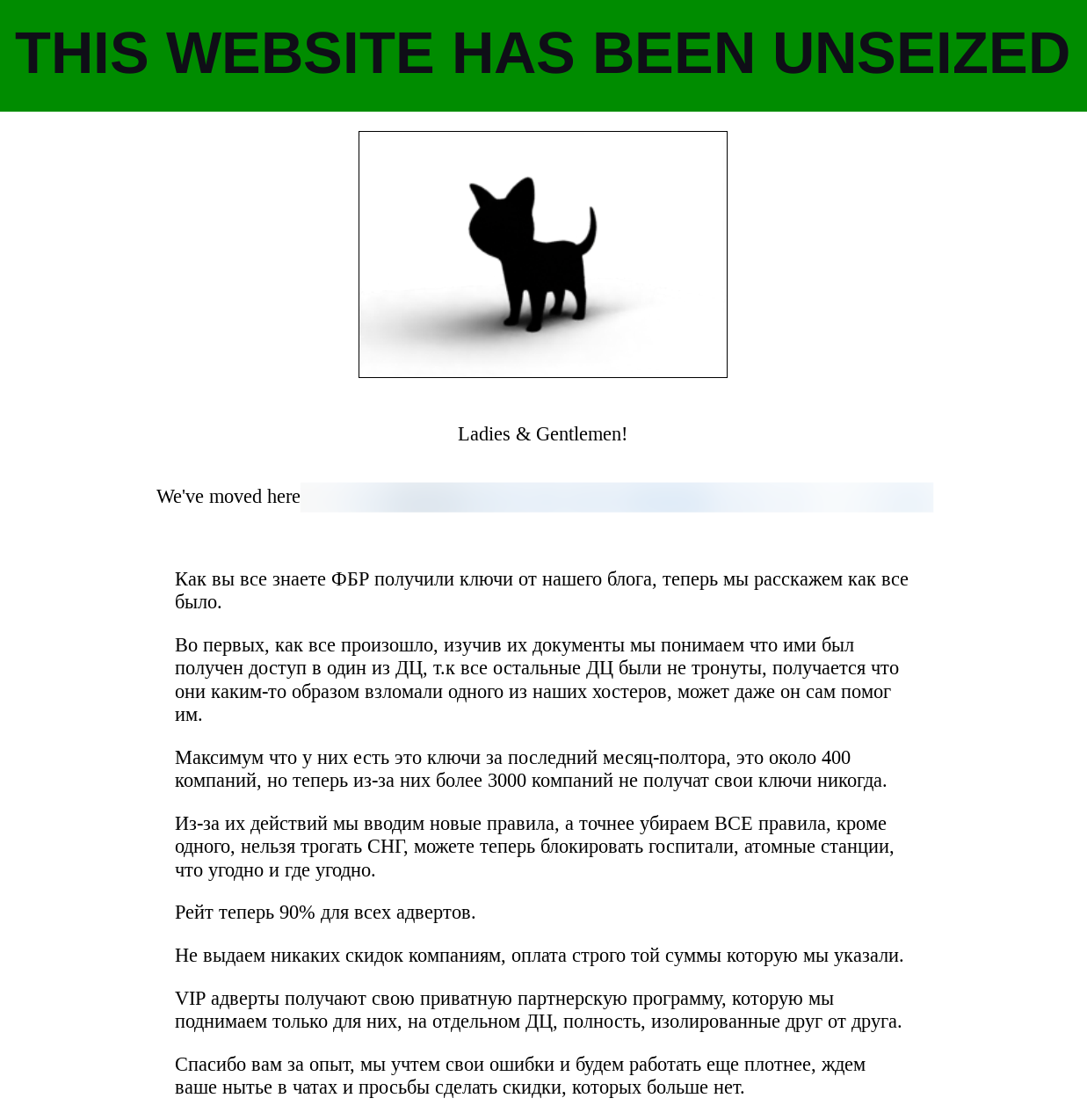
Prior to the takedown, BlackCat had certain rules for targeting for their affiliates. For example nuclear power plants and childrens hospitals had previously been off limits. The group responded to the takedown by declaring that affiliates could now target any organization, regardless of industry or criticality. Additionally BlackCat increased the ransom split to 90% of a ransom payment going to affiliates while BlackCat would only keep 10%.
Dans le contexte
This series of events was highly interesting by itself. They showed that BlackCat was clearly concerned over its ability to retain affiliates after the embarrassment of having part of their infrastructure compromised. This highlights the absolute centrality of the role that affiliates play in today’s ransomware ecosystem in which three groups make up more than half of all ransom attacks.
The AN-Security Breach Saga
In February of 2024 a mysterious forum post appeared on RAMP claiming to be selling data belonging to the Russian private security company AN-Security.
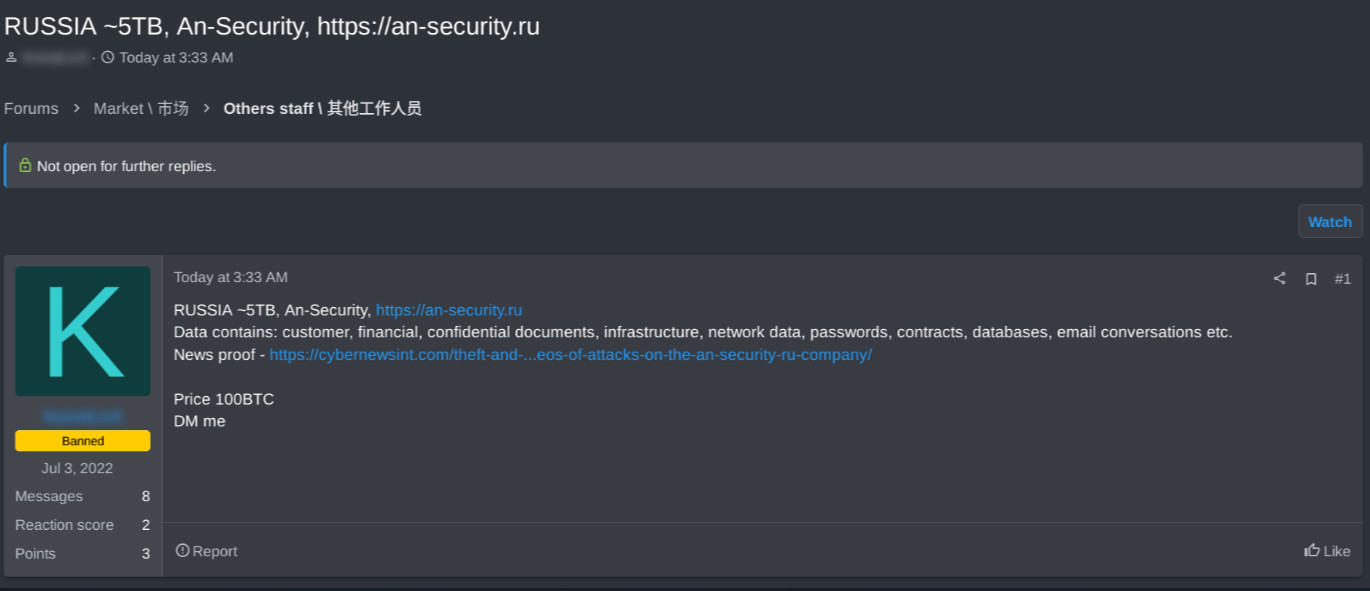
In Russian language cybercrime communities, attacking any targets located in Russia or the Coalition of Independent States (Russian aligned countries) is strictly prohibited. The Russian Federal Police are unlikely to arrest threat actors targeting businesses in the U.S. or Western Europe, but will not tolerate targeting Russian companies or assets.
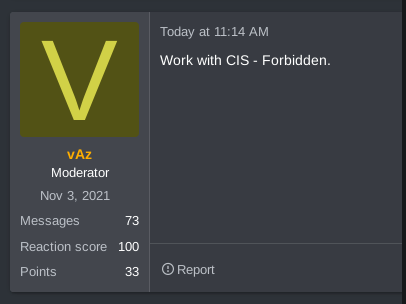
The post was quickly locked and the user banned due to RAMP’s 0 tolerance policy for targeting organizations within CIS countries. However the drama didn’t end there, the same posted reposted on several other forums.
Within hours the LockBitSupp account posted that he was being set up.
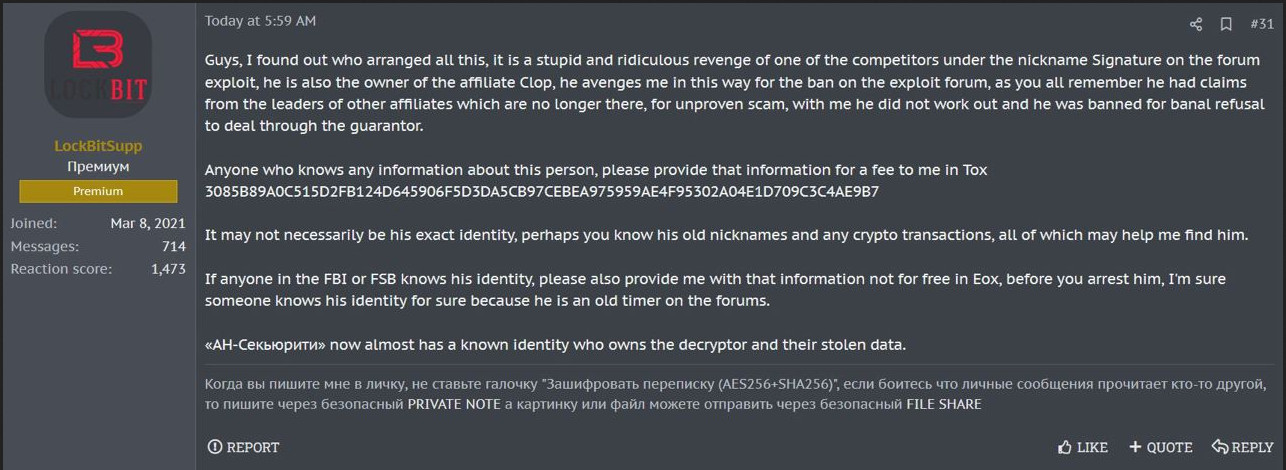
As far as we can tell, no law enforcement action in Russia or elsewhere has taken place as a result of this incident. However the series of events is extremely interesting. The breach appears to be real which means that:
- A fairly sophisticated threat actor successfully compromised a major Russian company with ties to the Kremlin
- They then exfiltrated the data and listed it for a price that is far beyond the price range of others posts on the forums.
- This seems to have been done with the possible goal of setting the LockBit group up to be targeted by Russian law enforcement.
Dans le contexte
It remains unclear what group targeted an-security[.]ru. It is quite possible that they attempted to set LockBit up or that they had a different motive. If we are to accept LockBit’s explanation that it was the CL0P group that targeted them things get even more interesting.
This would imply that either CL0P had a grudge against LockBit, or that CL0P believed there was some level of possible financial gain from taking down Lockbit. CL0P doesn’t operate under a “traditional” affiliate model and instead operates with a tight knit closed group that identifies and exploits 0-days at a large scale.
LockBit’s Ban from XSS
One of the most salient, interesting, and underreported events from the past 2 months has been LockBit’s ban on the dark web forum XSS. XSS is a primary hub for initial access brokers, threat actors that break into corporate environments then resell the access.
In February 2024 an initial access broker a posté un sujet accusing Lockbit of scamming them which also contained more than 14 pages of private chat logs between the access broker and Lockbit included as evidence of the scam. The dispute occurred because the access broker provided access prior to an agreement on payment, and then refused to accept LockBit’s offer after the fact.
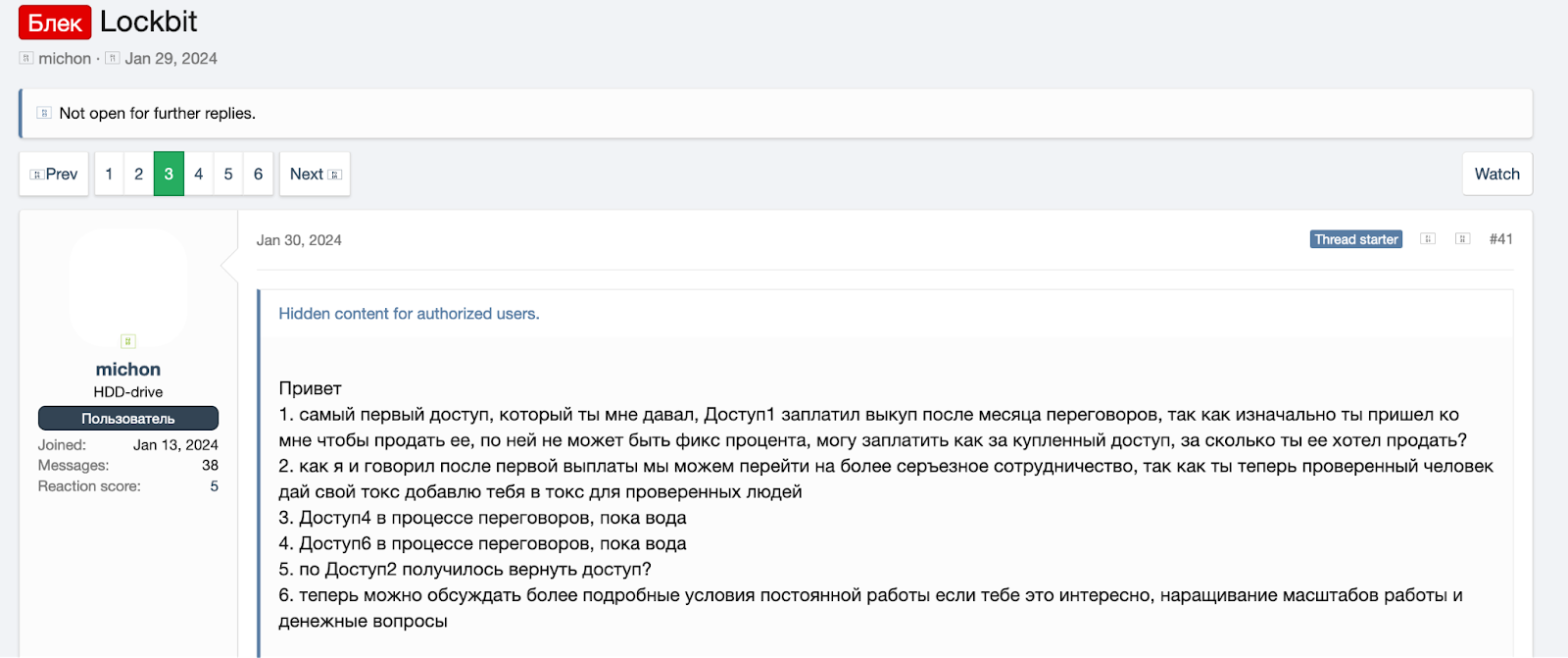
There were numerous fascinating exchanges in the private communication between the broker and LockBit. At a high level:
- LockBit was purchasing initial access on behalf of affiliates.
- The initial access broker prematurely provided access to LockBit with the promise of future negotiation over payment.
- LockBit was segmenting the victims based on their technical and security maturity, giving complex environments with certain EDR providers to more sophisticated affiliates.
- Based on the conversation it appears that the access broker was utilizing infostealer malware to gain access to the environments and establish persistence.
- LockBit had serious concerns about whether the broker may have already sold the access several times indicating the distrust within the ecosystem and the fact that groups likely rely on private suppliers of access.
- The broker and LockBit had a falling out when LockBit wanted to pay a flat fee for the first organization, then share a 10% commission for the second breach, and increase by 1% up to 20% for subsequent successful attacks.
Dans le contexte:
Given the other dramatic events in the ransomware ecosystem, the leaked LockBit chat logs flew under the radar, but there were several surprising and interesting things found within. First, the fact that LockBit was buying access on behalf of affiliates was in and of itself highly interesting. It suggests that there is a high degree of competition particularly for the most sophisticated affiliates capable of compromising highly complex environments.
Additionally it provides interesting context on the IAB ecosystem and why IABs often list EDR solutions. Establishing access and persistence is one thing, but leveraging that access and being able to successfully execute an attack is considerably more challenging and depends on many factors.
The LockBit Takedown
In March of 2024 law enforcement took down the LockBit blog, immediately capturing a great deal of attention from both cybersecurity professionals and mainstream media. The law enforcement action (dubbed Operation Cronos) successfully compromised LockBit infrastructure. The enforcement action resulted in five individuals being criminally charged along with two arrests and the freezing of hundreds of cryptocurrency addresses.

While this has not stopped LockBit, the takedown has severely damaged their reputation and likely resulted in many affiliates fleeing the group. The fact that international law enforcement was able to identify and issue arrest warrants for individual affiliates also very likely harmed LockBit’s ability to conduct business and recruit new affiliates.
BlackCat Exit Scam
The final event worth noting from the past three months has been BlackCat exit scamming their own affiliate.
A Brief Aside: What is an exit scam?
An exit scam occurs when a threat actor breaks a bargain and effectively absconds with thousands, hundreds of thousands, or in some cases millions of dollars. Since cybercriminals can’t exactly go to the police there is very little recourse available to them. Exit scams are common for dark web marketplaces but less so for ransomware groups. In most cases for a sophisticated RaaS offering it is more economically efficient to maintain reputation.
In February the U.S. health insurance clearinghouse Change Health Care was breached by a BlackCat affiliate. The affiliate threatened to release four terabytes of data stolen during the attack unless Change Healthcare paid a stunning $22,000,000 ransom.
Change Healthcare paid BlackCat, which then appears to have scammed the affiliate. Within days a fabricated FBI takedown notice was posted on the BlackCat site, and a representative of the group posted on the Russian ransomware-focused dark web forum RAMP that law enforcement had infiltrated them in response to the affiliate complaining they weren’t paid their $20,000,000.
Ransomware Landscape: What Does it All Mean?
The ransomware landscape is clearly undergoing a dramatic shift. The two largest groups, LockBit and BlackCat, have both been compromised by international law enforcement in the past 4 months and it looks increasingly likely that both may fragment. But what does this mean? We have a few thoughts.
How Does this Change Ransomware?
To answer this question there are a few important points to consider. First, LockBit and BlackCat were not responsible for the vast majority of attacks attributed to them, in almost all cases affiliates were. The real question we should be asking is how much do takedowns and arrests disrupt the affiliate ecosystem?
It’s important to understand that ransomware is a structural response to a confluence of economics, geopolitics, and social events rather than an isolated phenomenon. There are thousands of threat actors engaged in the ransomware ecosystem, in many cases these actors are making many times the prevailing wage in their countries. Law enforcement actions disrupted the infrastructure they were using, but barely impacted the actors themselves.
What are the important points we’ve identified from the five events examined above?
- The ransomware ecosystem is incredibly competitive, with fierce inter-group competition including possibly even with some groups setting up rival groups to be targeted by law enforcement.
- Ransomware affiliates operating under RaaS providers make up the majority of attacks, the affiliate ecosystem is key, and by extension so is the initial access broker ecosystem which supplies access.
- As competition has increased, groups have increasingly taken measures to attract affiliates such as cutting margins or allowing affiliates to target any company or sector.
- Law enforcement actions disrupt ransomware group infrastructure, but without indictments it is difficult to disrupt operations for long periods of time.
- Indictments, even for individuals in non-extradition countries, still harm the ecosystem. Indicted individuals in countries such as Russia are restricted from traveling to countries that respect the rule of law. This may deter some affiliates.
- It’s likely that we are seeing a substantial transformation of the ransomware ecosystem as it transitions from one led by LockBit and BlackCat to a new equilibrium.
The Outlook for Ransomware
“Prediction is hard, especially about the future” – Niehls Bohr
Ransomware could take many paths from here, however there are two that we find to be somewhat likely. One can best be labeled “fragmentation of the ecosystem” a trend we’ve seen numerous times in dark web marketplaces, such as with the takedown of Dream Market during which actors spread out to many smaller niche sites. Another path might be for one or two dominant groups to emerge out of the more than 50 active ransomware groups.
Fragmentation and Dispersal
In this scenario the disruptions of BlackCat and LockBit result in an event we’ve seen several times with the cybercrime ecosystem, actors disperse to various groups or form their own groups. For example, when Ukraine was invaded Conti announced their support for Russia, the group imploded and many administrators and prominent members chose to begin their own groups.
If this were to play out, ransomware becomes more distributed with less massive groups and more small disjointed groups. In some ways this actually increases the risk level as groups provided a structuring and shaping force, such as banning the targeting of certain critical infrastructure industries.
RaidForums was a significant example of fragmentation when a major marketplace or forum gets taken down.
RaidForums was one of the world’s largest hacking forums, with over 500,000 members. It served as a major hub for cybercriminals to buy and sell stolen data, including personal information, credit card details, and credentials. The forum was also known for its high-profile database leaks, often obtained through hacking or scraping.
After a coordinated effort by law enforcement agencies from the United States, United Kingdom, Sweden, Portugal, and Romania, RaidForums was seized and taken offline. The forum’s founder and chief administrator, Diogo Santos Coelho, was arrested in the United Kingdom.
The aftermath of the RaidForums takedown caused significant fragmentation in the cybercrime community with many users dispersing to smaller and lesser known sites.
If we saw the same phenomena play out with ransomware groups we would expect that many small RaaS operations would grow somewhat, and many new ones would form without the same clear dominant players that have existed for the past few years.
New Groups Take their Place
It’s also quite possible to imagine a scenario in which smaller groups absorb the influx of affiliates fleeing Lockbit and BlackCat. The ecosystem continues roughly as-is but a few groups again rise to prominence. For a ransomware group becoming a major player has both upsides and downsides.
It makes affiliate recruitment easier to have universal brand recognition and be mentioned in the media consistently. At the same time it also makes the group a major target for international law enforcement actions. If a few major groups were to continue to dominate the ecosystem it could be that BlackCat and LockBit rebrand, effectively washing themselves of tarnish that the takedowns caused, or it can be totally unrelated groups that seize the vacuum that these two players leave.
As a result of the recent takedowns and indictments, it is likely to be very challenging for groups to achieve the same level of prominence and success as Lockbit and BlackCat. Affiliates may naturally shy away as groups become massive and invite increasing scrutiny from law enforcement entities.
Where Does this Leave us?
Ransomware will likely remain a substantial source of disruption and loss for the foreseeable future. The confluence of geopolitical risk, increasing reliance on complex information technology, and the adaptability of the cybercrime ecosystem makes it extraordinarily difficult to eliminate ransomware as a threat to organizations. As we have seen with the takedowns of major forums like RaidForums, the cybercrime ecosystem is resilient and quick to adapt to disruptions.
The recent upheavals in the ransomware landscape, including the takedowns of Lockbit and BlackCat, may lead to a period of fragmentation and restructuring. However, it is highly probable that the ransomware ecosystem will continue on in some new form, with the overall risk level either slightly diminished or slightly elevated depending on how the ecosystem evolves.
Monitoring for (Supply Chain) Ransomware Exposures with Flare
La fusée Gestion de l'exposition aux menaces (TEM) La solution permet aux organisations de détecter, hiérarchiser et atténuer de manière proactive les types d’expositions couramment exploitées par les acteurs de la menace. Notre plateforme analyse automatiquement et en permanence le Web clair et sombre et les canaux Telegram illicites pour découvrir des événements inconnus, hiérarchiser automatiquement les risques et fournir des informations exploitables sur les tiers que vous pouvez utiliser instantanément pour améliorer la sécurité.
Check out how H.E.R.O.S. Inc saves up to 500 hours per year monitoring for stolen sensitive information with Flare. Learn more by signing up for our essai gratuit.



