Estimates from 2024 indicate that global losses attributed to online scams exceed USD $1 trillion. This figure likely represents only a portion of the true impact, as many incidents go unreported due to victim underreporting and limited confidence in the ability of institutions to investigate or recover losses. More recent reporting has also drawn attention to the role of social media platforms, which, rather than proactively preventing scam activity, have monetized advertising and infrastructure that facilitate fraudulent campaigns.
We examined a specific type of social engineering: the celebrity impersonation scam operation specifically targeting Canadians, illustrating the scale, sophistication, and reach of a single coordinated campaign.
Celebrity Impersonation Scams: An Inside Look
In this scam, identified by Flare, the operators employ a common social engineering technique: the use of a purported celebrity endorsement to establish credibility and initiate victim engagement. This approach mirrors tactics observed in celebrity impersonation and romance scams, where threat actors exploit the perceived trust and familiarity associated with well-known public figures. The selected celebrity or public figure is deliberately aligned with the geographic region to be targeted. Social media advertising platforms are then used to ensure initial exposure is largely limited to users geolocated within the intended country, based on their profile attributes and activity history. Without this key driver, initial engagement is unlikely to occur, as a political figure or celebrity endorsing a “money back scheme” in another country will not appeal to someone with no ties or links to that country.
In addition, the scam operators deliberately exploit emotional responses, most commonly sympathy. Sponsored ads and associated posts frequently depict the selected celebrity as having suffered an injury, misfortune, or institutional retaliation. Common narratives include claims that the celebrity has been “taken off air” after disclosing how they accumulated significant wealth, or that they have been arrested at the direction of the “bank of [insert country]” for allegedly revealing a financial “loophole.” Our analysis indicates that one of the most prevalent themes involves portraying the celebrity as injured or confined to a hospital bed, often framed as a final or urgent disclosure of financial advice intended to encourage immediate victim engagement.
Related Sponsored Ad Campaigns Featuring False Information About the Celebrity
Our research identified a sponsored ad campaign hosted on Meta that leverages likely unauthorized images of Canadian businessman and television personality Kevin O’Leary. The advertisements depict O’Leary as being arrested or injured and are accompanied by sensationalized headlines designed to encourage user interaction. These taglines, commonly referred to as “clickbait,” employ misleading and inflammatory text to prompt users to engage with the content. Captions such as: “Accusations against O’Leary have been confirmed! The celebrity’s secret has finally been exposed!” and “The accusations against him have been confirmed!” often accompany the images.
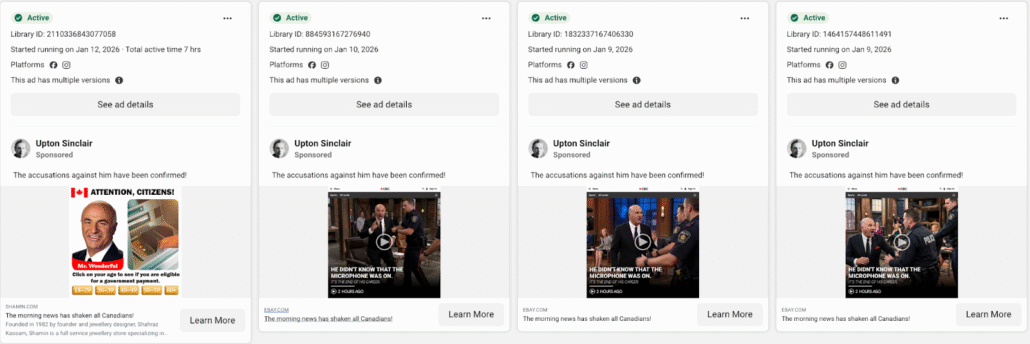
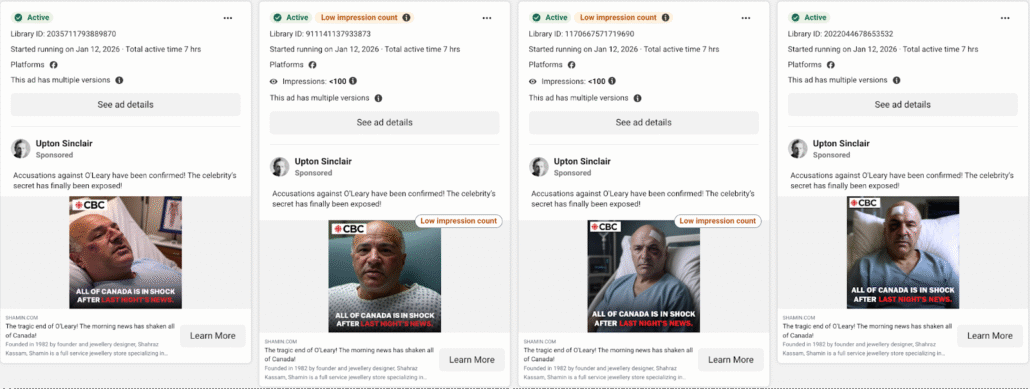
Meta scam ads featuring Kevin O’Leary
Related Falsified News Articles as “Evidence”
All 190 advertisements identified within this campaign to date, including the earliest observed on January 6th, 2026, redirect users to fraudulent news articles falsely purporting to originate from the Canadian Broadcasting Corporation (CBC).
These articles are hosted on randomly generated domains with no affiliation to the legitimate news organization. For the purposes of this analysis, we selected the domain synapsetder[.]pro from the URLs referenced in the sponsored ad found on Meta.
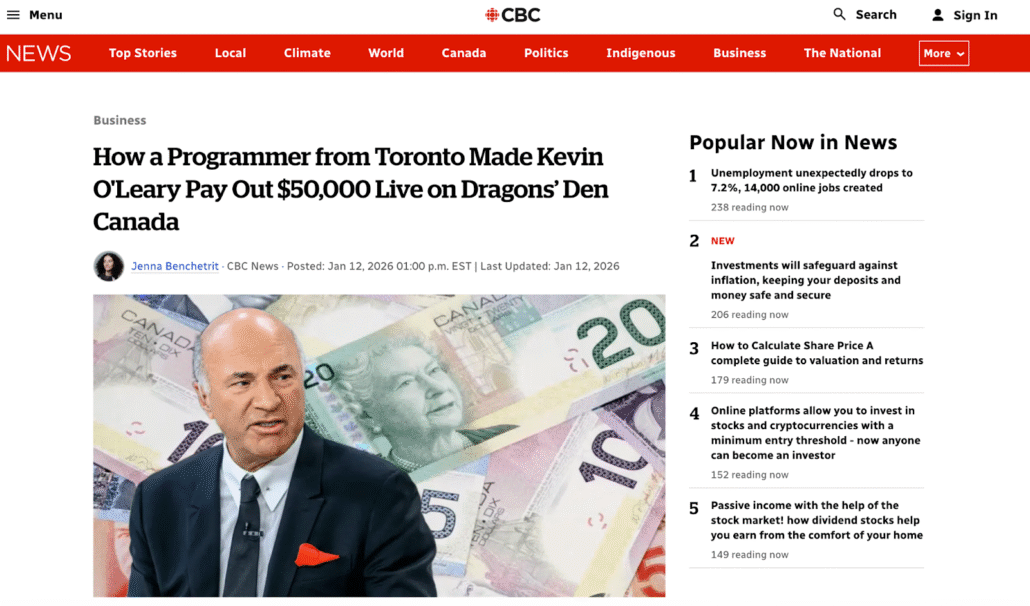
Fraudulent news article about Kevin O’Leary
The domain, registered on January 9th, 2026, displays an updated headline aligned with the alleged “investment platform” promoted within the article. The page also features false “Popular Now” items designed to create a false perception of financial opportunity or economic urgency, thereby influencing reader behavior.
The website design observed is consistent with this scam campaign. Using the platform URLscan, our research identified 1,285 instances of matching page templates, with some observed as recently as five days prior to this analysis. While individual templates may vary in imagery and headlines, they typically reflect the celebrity or public figure being impersonated. None show any legitimate association with the platforms or organizations they allegedly represent.
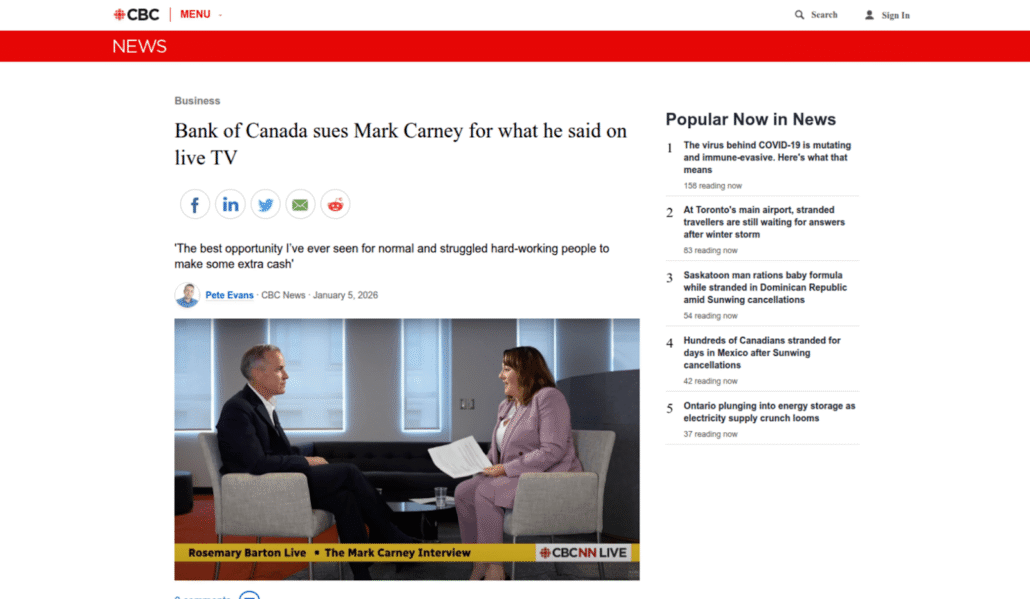
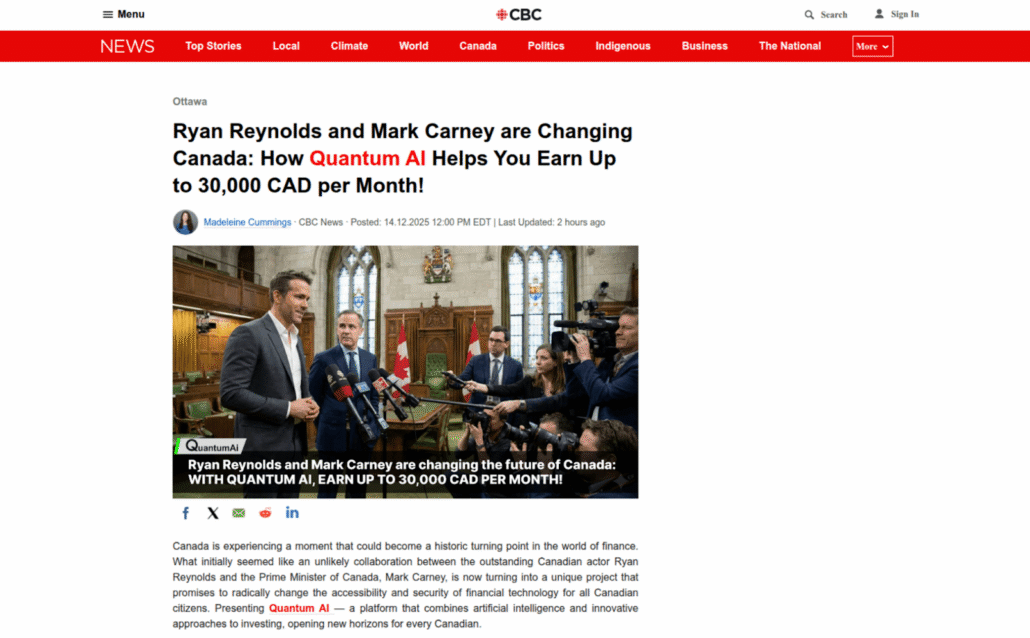
Fraudulent news articles about Mark Carney and Ryan Reynolds
These websites can be identified and traced within the Domain Name System (DNS), which functions as the internet’s phone book. However, the scale of this campaign involves hundreds of thousands of domains. More importantly, these domains primarily serve as intermediary infrastructure, acting as redirection points that funnel victims onward to the next stages of the scam operation rather than representing the final destination.
Driving Readers to Scam Investment Platforms
Interaction with any hyperlink in the article redirects users to a separate website falsely presented as a sign-up page for the associated investment platform. The platform branding and underlying domains change regularly, with embedded links often becoming inactive as new fraudulent sites are introduced. During this analysis, the domain ironwoodd[.]info was identified as hosting the investment registration page.
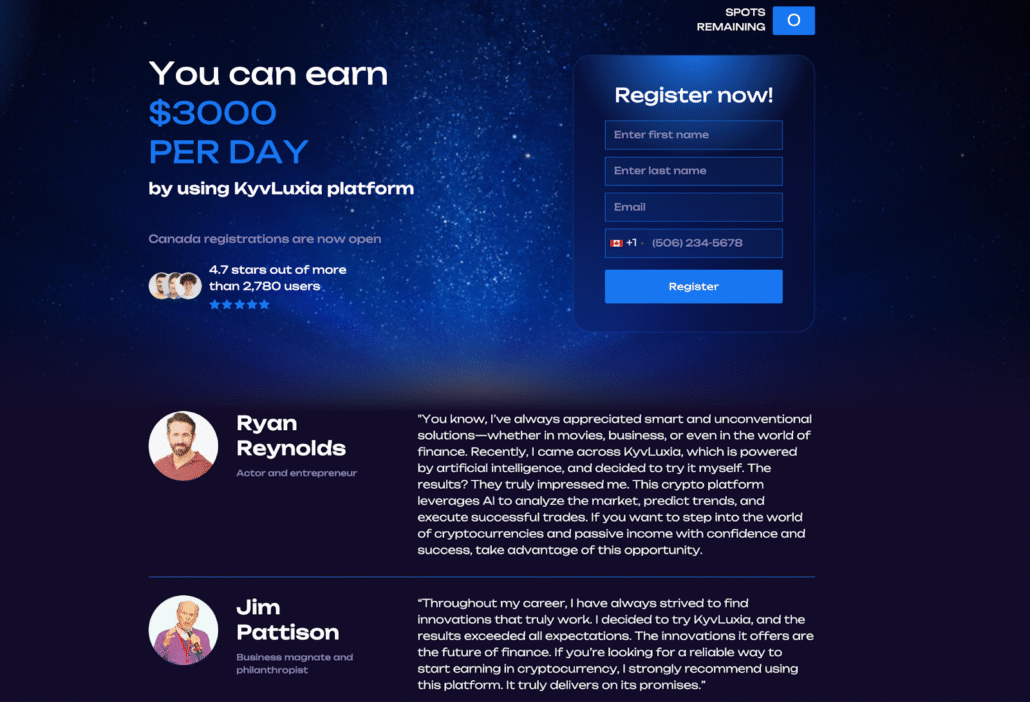
Website for the associated fraudulent investment platform
The page includes fabricated statements attributed to well-known Canadian public figures, intended to further reinforce the perceived legitimacy of the platform. A countdown timer is also present, which our analysis shows initializes at “21” before rapidly decreasing to zero. This mechanism is designed to create artificial urgency by implying a limited subscription window. In reality, the timer has no functional impact: once it reaches zero, no action occurs, and victims may still submit their information via the webform. Refreshing the page resets the countdown.
Similar to the earlier-stage article pages, hundreds of domains were identified in our research hosting identical content and embedded webforms. After a user submits information through the webform, the site performs two successive redirects before delivering the victim to the final stage of the scam: a fraudulent investment platform.
Following submission of personal details, victims are ultimately redirected to a website presented as an investment platform. During this analysis, the domain qipcapital[.]com served as the final destination. Although the domain was initially registered in June 2025, this does not reflect the duration of its use within the scam, as platform domains are regularly rotated by the operators and often registered in advance as part of bulk registration processes.
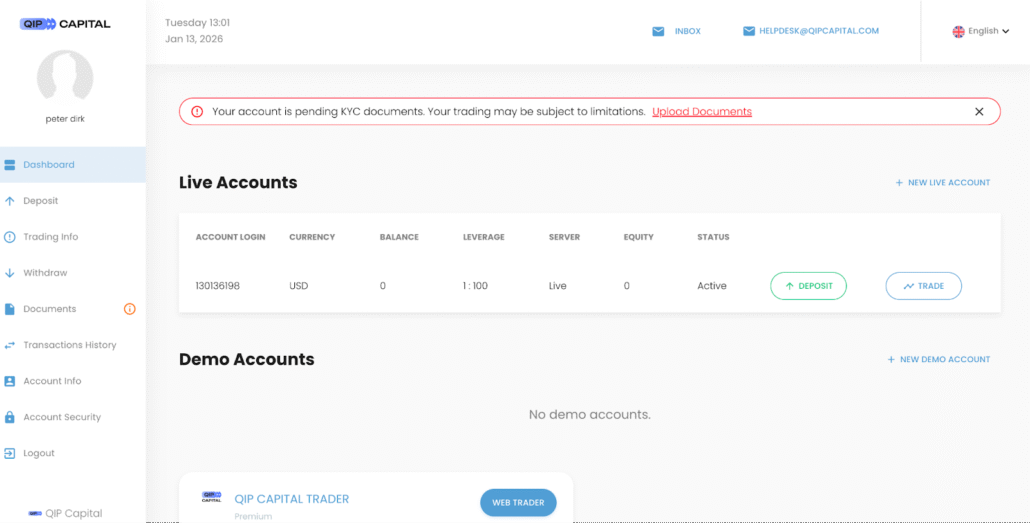
A look into the fraudulent investment platform
Before a victim is allowed to deposit the minimum amount of $250, they are required to upload identification documents, providing the scam operators with name, address, credit card number, and photographs. All these details will be used not only to extract payment at the time, but also to further additional illicit activity.
Our DNS analysis identified the domain qip[.]capital, registered in January 2025, which redirects to qipcapital[.]com via the account registration and login process. The site presents scrolling market information alongside generic corporate content, including company information, FAQs, and other elements commonly associated with legitimate investment platforms. Active links to social media platforms, including YouTube, X (formerly Twitter), TikTok, and Medium, were also observed.
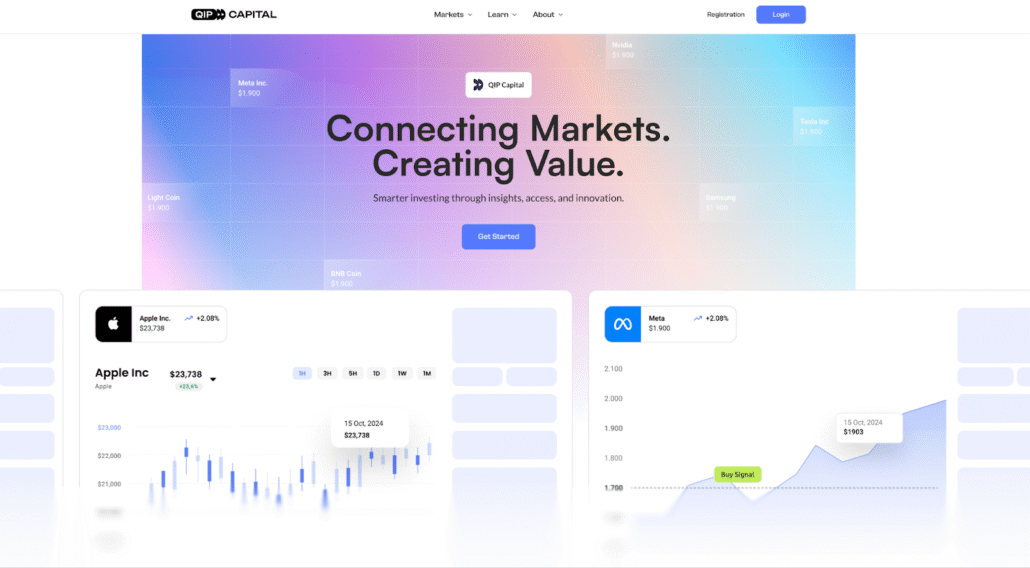
QIP Capital website
Our analysis uncovered a distinct technical indicator linked to this scam campaign to preserve its utility for continued detection and tracking, we have elected not to disclose this indicator publicly at this time). Application of the indicator enabled the identification of additional websites with digital characteristics matching those associated with Qip Capital.
IPO Capital website, similar to digital characteristics of Qip Capital
While the site’s social media functionality remains active, the registration form is no longer operational, indicating the website may have already fulfilled its role within the scam operation. This conclusion is reinforced by the domain’s expiration date of August 2025.
Teed Trades, a website similar to IPO Capital
Teed Trades, registered in April 2025, maintains a functioning website similar to IPO Capital. However, the removal of cryptocurrency payment functionality indicates that the domain has likely completed its role within the scam operation and has since been discarded.
Continued Monitoring of Celebrity Impersonation Scams
We continue to identify domains associated with this scam operation, with several thousand observed to date. New sponsored advertisements are appearing on an almost daily basis, redirecting unsuspecting victims to multiple fraudulent websites that often leverage convincing branding and fabricated articles. Without comprehensive domain infrastructure mapping and payment flow analysis, disruption efforts risk becoming reactive and inefficient, resulting in a “whack-a-mole” effect rather than meaningful mitigation of large-scale scam activity.
At Flare, we will continue to monitor, analyze, and report on these campaigns as they impact Canadians and others around the globe.
Want to learn about other timely scams targeting consumers? Check out the new research blog “New Threat Actor Group PayTool Targets Canadians with Traffic Scams.”



