Identity Exposure Management


Exposed Credentials are an Open Door for Attackers
Millions of Corporate Credentials are Exposed Every Week
Attackers Find New Exposures at Scale
Speed is the Real Weakness

Tracking and Remediation are Costly and Noisy
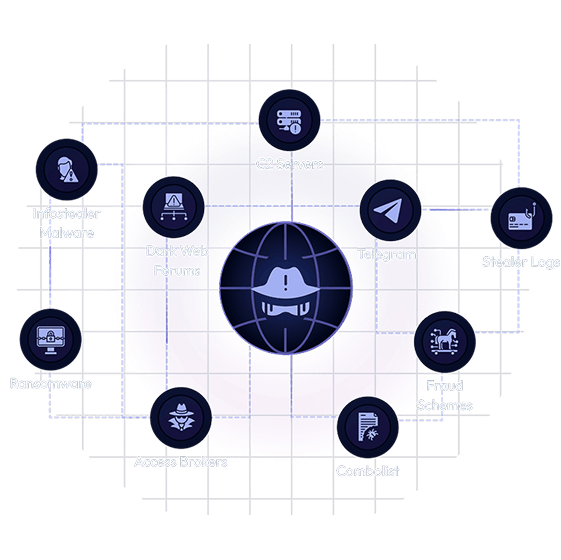
Flare Turns Credential Chaos into Clarity
The Industry’s Best Coverage of Identity Exposures
Near Real-Time Detection
Automated Validation and Remediation with Entra ID
Proven Risk Reduction and Cost Savings
Flare’s Identity Exposure Management Toolkit
Entra ID Exposed Credential Validation & Remediation
Identity Profile & Blast Radius Visualization
Leaked Credentials Browser
Stealer Log Events
Dark Web Monitoring of Access Brokers
Robust API Endpoints & Integrations
Results You Can Expect With Identity Exposure Management
321% ROI
25% Reduced Breach Risk
1300+ Hours Reallocated
Frequently Asked Questions
What is IEM?
Identity Exposure Management (IEM) is a security approach that continuously monitors for compromised credentials and session tokens across the dark web, Telegram channels, and other sources where threat actors trade stolen data.
Unlike traditional identity security products that focus on authentication and access controls within your environment, IEM looks outward to detect employee credentials that have been exposed before attackers can use them.
Flare’s IEM solution pairs comprehensive credential monitoring with automated validation and remediation workflows. When exposed credentials are detected, the platform can automatically verify whether passwords are still valid against your identity provider and trigger remediation actions like forcing password resets, revoking active sessions, or flagging accounts as compromised in Microsoft Entra ID.
Why is IEM especially important now?
The threat landscape has fundamentally shifted in this era of “logging in” instead of “hacking in.” Infostealer malware now infects millions of devices globally, harvesting not just passwords but session cookies that allow attackers to bypass multifactor authentication entirely. These stolen credentials appear in dark web marketplaces and Telegram channels within minutes of infection, giving threat actors a window to access corporate systems before anyone knows there’s a problem.
Traditional security controls assume credentials are either protected or breached in a single event. In reality, credentials leak continuously through phishing, malware, and third-party breaches. According to Verizon’s Data Breach Investigation Report, stolen credentials are involved in 88% of basic web application attack breaches. And with 46% of personal device stealer logs containing corporate credentials, the line between personal and professional exposure has effectively disappeared. In addition, the median time between ransomware victim disclosure and detection of related stolen credentials is two days, suggesting that ransomware operators frequently leverage infostealer malware. IEM addresses this by providing continuous visibility into credential exposure and automating the response.
According to our research, enterprise identity exposure is projected to reach 15-16% of all infostealer infections by late 2026 under baseline assumptions. However, this number could be 20% (one in five infections yield enterprise credentials) as early as Q3 2026. Read the full details in our 2026 State of Enterprise Infostealer Identity Exposure report.
How can IEM save you money on remediation?
Remediating identity exposures is expensive. Forrester puts the cost of a single password reset at $70, factoring in IT overhead and loss of productivity, and those costs quickly add up across hundreds or thousands of annual incidents.
Time compounds the problem: organizations average 11 hours to investigate a single identity-related alert. With threat actors bypassing MFA and weaponizing valid credentials, security teams remain locked in a cycle of investigation and cleanup.
With IEM, security teams can continuously monitor for identity exposures and automate remediation within minutes.
The business case for IEM extends well beyond risk. Forrester’s 2025 Total Economic Impact study quantifies the value: 321% ROI for Flare customers. Organizations attributed this return to a 25% decrease in the likelihood of severe data breaches and $167,000 saved annually in threat intelligence labor. These aren’t abstract benefits; they translate to faster detection, fewer costly incidents, and less time lost to investigations.


“What used to take about 1500 hours to complete can now be done in 1 week. Flare allows me to empower junior analysts to do dark web investigations that were previously impossible, hence liberating bandwidth.“
“Other solutions would present us with thousands of potential leaks which were impossible to work with for our small team, Flare was the only one that could successfully filter and prioritize data leaks with their 5-point scoring system.”
“What used to take about 1500 hours to complete can now be done in 1 week. Flare allows me to empower junior analysts to do dark web investigations that were previously impossible, hence liberating bandwidth.”
“We audited dozens of different solutions and Flare was the only one making CTI easy and understandable for all, with the right data.”
“Flare enables us to react quickly when threats are publicized. It helps us protect our brand and financial resources from data breaches.”
“We audited dozens of different solutions and Flare was the only one making CTI easy and understandable for all, with the right data.”



