Dark Web Monitoring


Dark Web Intelligence for Your Security Team

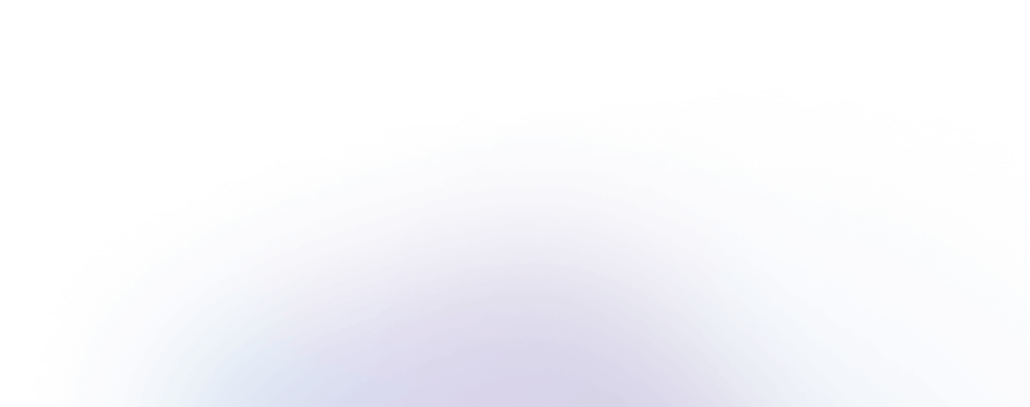
How You Can Monitor the Dark Web with Flare
Experience the Cutting Edge of Dark Web Monitoring
Act Quicker with Tailored Insights
Better Understand Risks with Threat Actor Analytics
Make Informed Decisions with AI Event Contextualization
Comprehensive Surveillance of Key Dark Web Forums & Markets
Flare helps companies build a threat intelligence-led cybersecurity program.
Cybercrime Communities Monitored
Stealer Logs Ingested
Threat Actor Profiles Tracked
Automate and Scale Threat Detection Across Millions of Dark Web Data Points

Monitor Illicit Sources with Flare
Dark Web/Tor
Telegram Cybercrime Channels
Stealer Logs
Proactive Protection Starts with Dark Web Monitoring

Dark Web Monitoring FAQs:
What is the dark web?
The dark web is intentionally hidden and requires the use of special tools like the Tor browser, which enables anonymous communication and browsing.
In contrast, the clear web is the publicly accessible portion of the internet that standard search engines index and search. It consists of websites and resources that are openly available to users without any special access requirements or encryption protocols. The deep web includes all the pages that search engines don’t index including password-protected websites and websites that choose not to be “crawled” by search engines. The deep web contains content that’s stored in databases that support services on the clear web, such as social media platforms or subscription streaming services.
While the dark web hosts various illegal activities, such as the sale of stolen data, drugs, and weapons, it also facilitates other activities, including privacy-focused communication, political activism, and sensitive information sharing in oppressive regimes.
The anonymity provided by the dark web makes it appealing for both legal and illegal purposes, as it allows users to communicate and share information without revealing their identities or locations.
Though threat actors are often associated with the dark web, they gather in many cybercrime communities across the clear & dark web and illicit Telegram channels. Dark web monitoring is one essential piece of a comprehensive Threat Exposure Management strategy.
What types of information are sold on the dark web?
Here are some common types of data you might find on the dark web:
- Personal/protected health information (PHI)
- Names and birthdays
- Login credentials and security question answers
- Exposed technical data and source codes
- Personally Identifiable Information (PII) such as home addresses
- Financial data, bank accounts, and credit cards
- Software source code
- Company proprietary information
What is dark web monitoring?
Dark web monitoring involves proactively scanning and analyzing the dark web to identify external threats linked to your organization’s data.
Cybercrime forums and markets facilitate threat actors in buying and selling stolen data, hacking tools, and more. Their actions can then provide your security team with threat intelligence to mitigate these risks.
What are the benefits of dark web monitoring?
Dark web monitoring offers multiple benefits:
- Early threat detection: By continually scanning the dark web for your business or personal data, it can alert you to a data breach before it has a chance to escalate.
- Reputation protection: Businesses that are victim to a data breach not only suffer financially but can also lose their customers’ trust. By identifying threats early, you can take action to mitigate the impact and maintain your reputation.
- Peace of mind: Putting processes in place to monitor your data 24/7 can help reduce the harm of potential external threats by enabling your team to shut down the risks quickly.
Is monitoring the dark web necessary?
As threat actors are increasingly logging in rather than hacking in for their attacks, dark web monitoring is even more crucial in helping organizations identify the presence of compromised sensitive data in illicit communities. This allows your security team take steps to prevent further damage. You could also detect if your sensitive information ended up on the dark web through a third-party, and secure the information before receiving official notice of a compromise from that third-party. By shortening the time to mitigate risks through robust dark web monitoring, your security team can better avoid and decrease costly consequences.
Is dark web monitoring safe?
Yes, dark web monitoring is safe when executed through trusted cybersecurity platforms or with managed security service providers (MSSPs).
They use advanced technology and security protocols to navigate the dark web. They can monitor various illicit communities without jeopardizing their own systems or their clients’ data.
Furthermore, cybersecurity platforms and professionals adhere to ethical guidelines and legal requirements, so they do not engage with illegal activities on the dark web. Their goal is to identify and mitigate potential threats, not to interact with the illicit components of this hidden network.
What are dark web monitoring services?
A dark web monitoring service is a cybersecurity solution offered by specialized firms such as with managed security service providers (MSSPs). It involves scanning the dark web for data related to a specific organization or individual within that organization. This could include personally identifiable information (PII), credit card details, login credentials, or sensitive company information. If the service detects such data, it alerts the client, enabling them to take action.
What is dark web monitoring software?
Dark web monitoring software is a tool that can scan, identify, analyze, and provide actionable intelligence from external threats on the dark web that are relevant to your organization.
Dark web monitoring software can makes monitoring through automation. Using this tool can enable your security team to act quicker with mitigating potential risks.
How do I monitor the dark web?
Navigating the dark web independently can be risky and technically complex. Trusting a dark web monitoring service or platform would serve your team well. This way, you benefit from advanced cybersecurity measures from experts without needing to dive into the dark web yourself, as manual monitoring can be time-consuming.
What is dark web credential monitoring?
Leaked credential monitoring is a specialized aspect of dark web monitoring. It focuses on tracking stolen or leaked login credentials, such as usernames and passwords, on the dark web. With many people reusing passwords across multiple platforms, a single data breach can potentially unlock multiple accounts for threat actors. Credential monitoring helps prevent such scenarios by promptly identifying compromised credentials and enabling swift password changes or other appropriate security measures.
Does my organization need dark web monitoring?
Considering the rise in data breaches, cybersecurity threats, and the value of data in today’s digital economy, proactive monitoring provides an essential layer of protection.
Dark web monitoring is a valuable measure in protecting your organization against cyber threats. A monitoring service or platform can support your CTI team in staying one step ahead of potential threats and cybercriminals’ evolving tactics.
What’s the benefit of automating dark web monitoring?
Manually searching through the dark web is one possible way of monitoring, but it is inefficient, prone to missing items, and emotionally/mentally exhausting. Automated monitoring tools can accurately and continuously scan illicit communities much more comprehensively than is possible with manual methods. Automated dark web monitoring enables reliable surveillance and also significantly faster response times to mitigate threats (with prioritized alerts).
In addition, automated dark web monitoring can make gathering dark web analytics easier, so that security teams can benefit from cleaned and structured information about the dark web that is relevant to their organization.
Can I automate searching through dark web search engines?
Flare is not a dark web search engine, but tracks dark web forums and markets (as well as illicit Telegram channels), so your security team can safely monitor these sources in the platform without manually searching for them.

“What used to take about 1500 hours to complete can now be done in 1 week. Flare allows me to empower junior analysts to do dark web investigations that were previously impossible, hence liberating bandwidth.“
“Other solutions would present us with thousands of potential leaks which were impossible to work with for our small team, Flare was the only one that could successfully filter and prioritize data leaks with their 5-point scoring system.”
“What used to take about 1500 hours to complete can now be done in 1 week. Flare allows me to empower junior analysts to do dark web investigations that were previously impossible, hence liberating bandwidth.”
“We audited dozens of different solutions and Flare was the only one making CTI easy and understandable for all, with the right data.”
“Flare enables us to react quickly when threats are publicized. It helps us protect our brand and financial resources from data breaches.”
“We audited dozens of different solutions and Flare was the only one making CTI easy and understandable for all, with the right data.”


