
It was the best of times for criminals, and the worst of times for lovers of cracked software. Infostealer campaigns represent a major issue today for consumers and corporations worldwide. Dedicated threat actors develop infostealer variants, a type of remote access trojan (RAT) that infects a host and extracts credentials saved in the browser, session cookies, and other data from the victim’s machine. This information is then packaged into log files and distributed throughout the cybercrime ecosystem via the dark web and Telegram.
This article will examine two infostealer campaigns, one from 2022 and one from 2023. We will map out how each campaign operates using victim screenshots—images captured by the malware shortly after infection—that often reveal key details of how the infection occurred. The purpose of this article is to demonstrate common pathways for infostealer campaigns.
The Snow* Microsoft 2022 Campaign
*Snow because “yuki” is Japanese for snow
The Snow infostealer campaign targeted a wide pool of victims from all over the world. Victims that included French, English, Spanish, Turkish, Portuguese, Chinese, and even Korean language devices were identified across multiple months.
All these devices were infected by the same process: threat actors seeded a cracked version of Microsoft Office 2022 with the Aurora infostealer variant and spread it via YouTube videos via a link in the Youtube description. 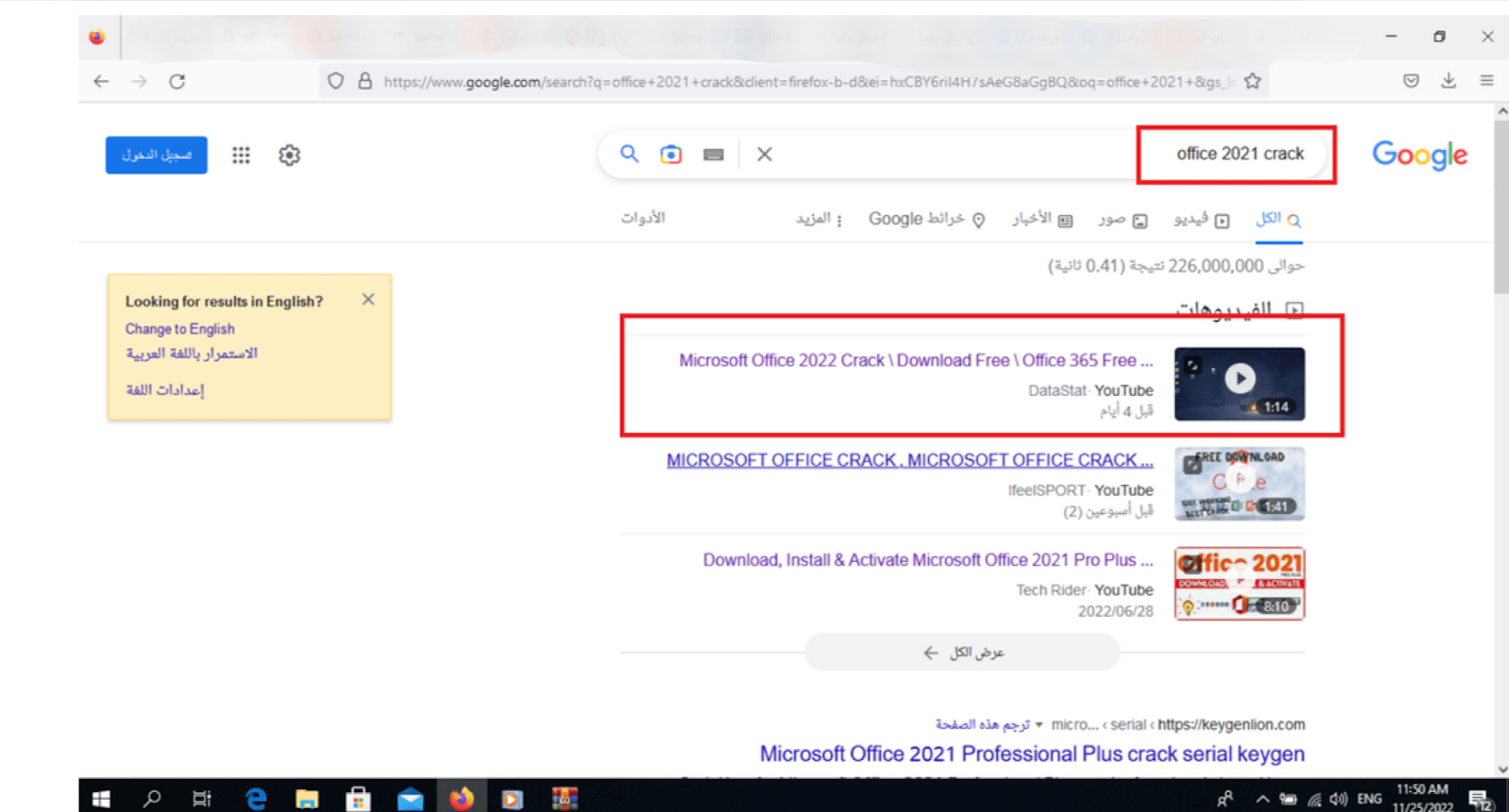
A Google search for “office 2021 crack” pulls up the YouTube video that promoted the infostealer
The choice to use well-known, widely trusted, and essential software like Microsoft Office (which has a costly license, pushing some users to seek illegal alternatives) is a strategic one. Microsoft Office is recognized globally as the standard for basic computer tasks, with popular programs like Word, Excel, and PowerPoint included in the suite. Leveraging such a ubiquitous tool as bait to distribute infostealer malware provides access to an enormous pool of potential victims, spanning the world. Even in countries with different alphabets, the name “Microsoft” is universally recognized. This makes it a perfect fit for one of the most potentially far-reaching malware campaigns to date.
First users search for “Office [Year] crack” and click on the first few videos they are suggested: “Microsoft Office 2022 Crack \Download Free\ Office 365 Free Version \ World Language” video from the DataStat Youtube Channel. DataStat YouTube channel is written in Azerbaijani and has 37 videos for a little over 2k subscribers (as of September 18th, 2024). The video previously available at www.youtube.com/watch?v=kP58gLnluLY\n4 was only a minute and 13 seconds long and presented a tutorial on how to download and install the cracked version of the software. However, the video is no longer available on the channel.
YouTube is a major vector of malware distribution. Threat actors launch account takeovers against legitimate small YouTube channels and publish videos on how to obtain/run specific types of cracked software. Typically the actor then links to “their” download of the cracked application in the YouTube description.
We see this exact scenario play out in the Snow infostealer campaign, a seemingly harmless YouTube video lures viewers into downloading a malicious cracked version of popular software. In the video’s description box, users are enticed by a download link claiming to provide access to free software.
When the link is clicked, it redirects the user to a Telegraph page, where they are promised a “free version of Office.”
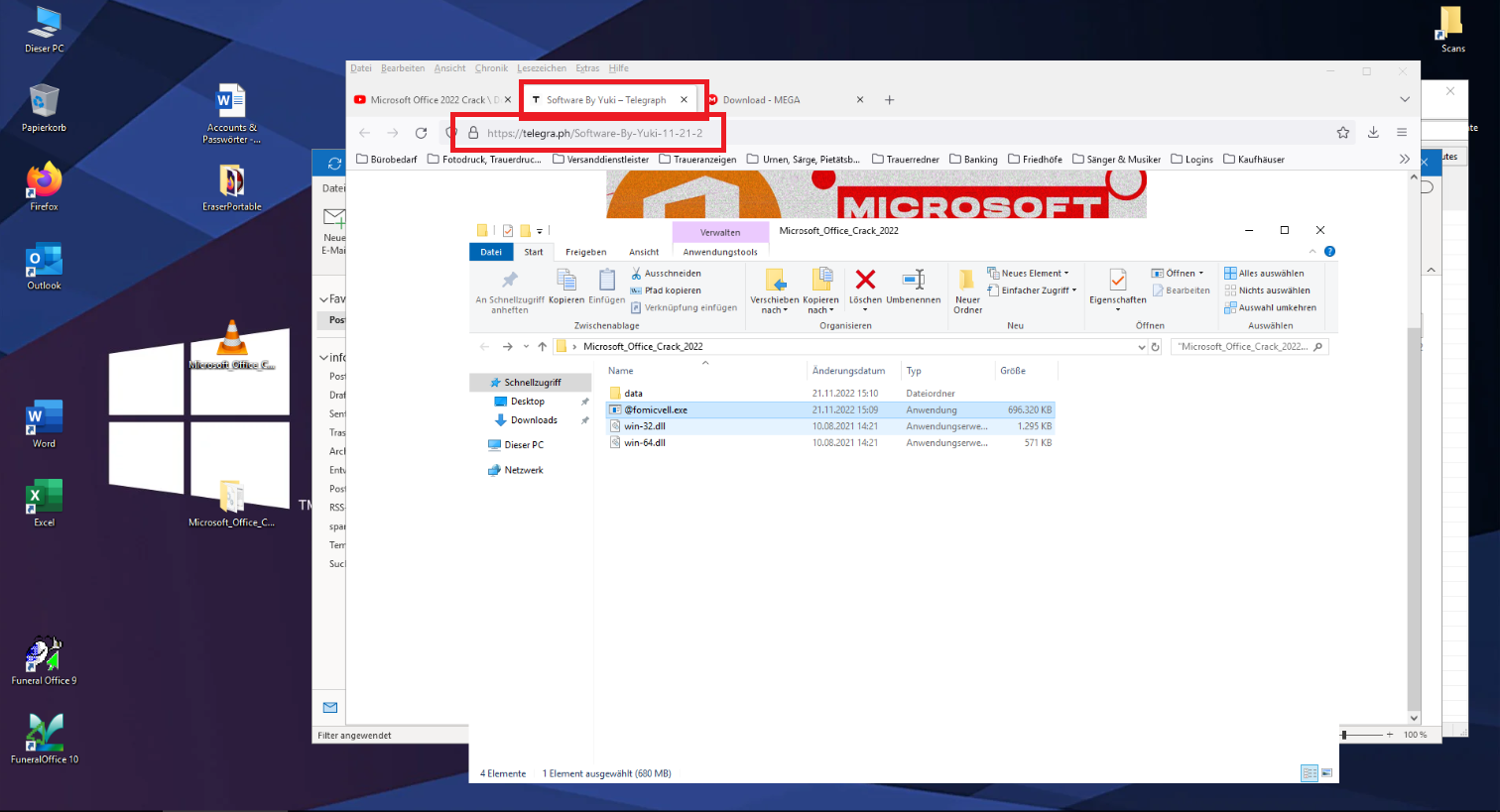
Clicking on the link to download redirects the user to the Telegraph page for “Software by Yuki”
The malware is hosted on MEGA.nz, a popular file-sharing platform, and the link provided (https://mega.nz/file/DZxXBB5#iNTbuEP4K83I-5Blx114xYmGJIgZZStjTc352iU) allows users to download a compressed archive. 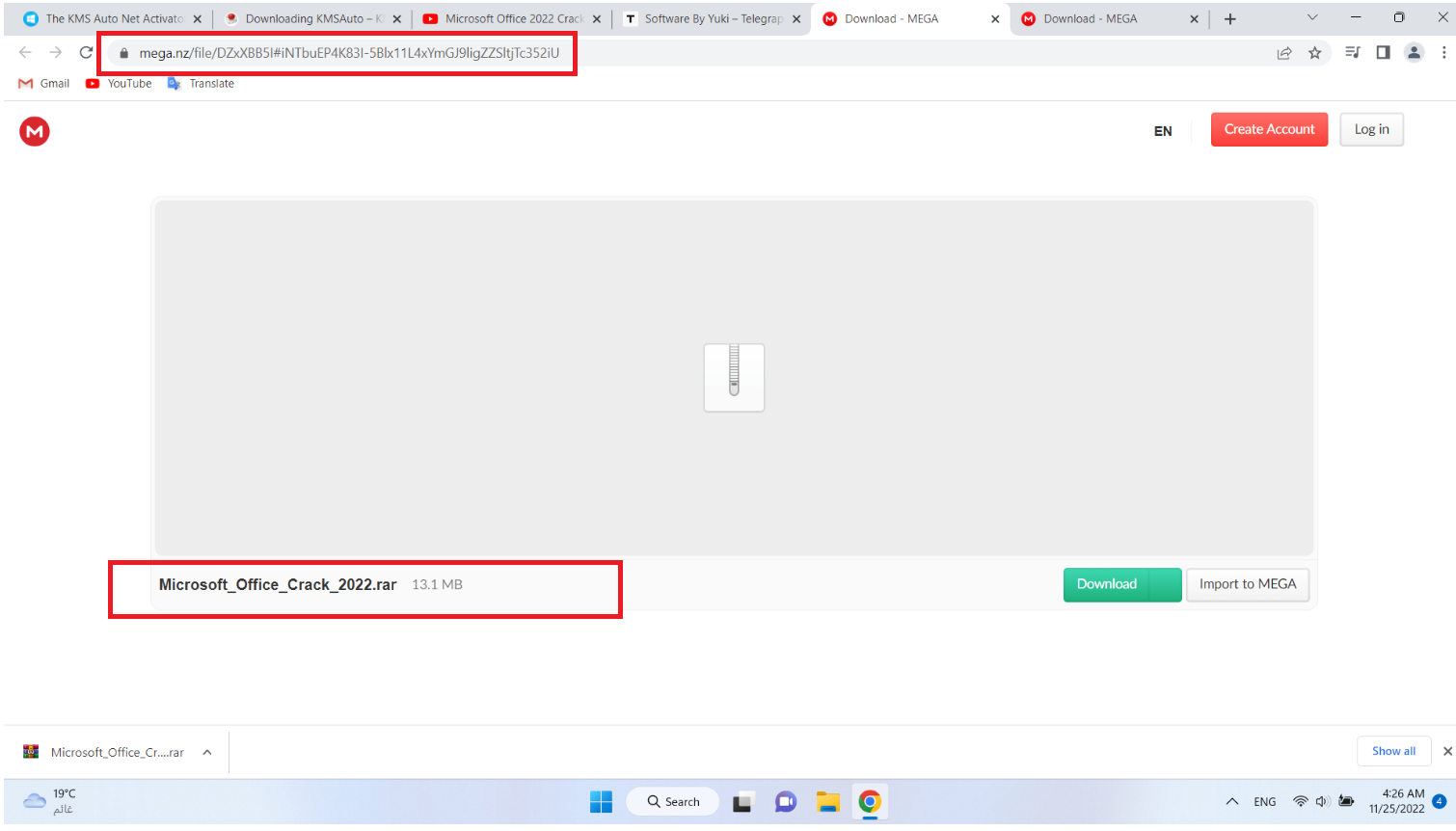
The MEGA.nz link shows a compressed archive for “Microsoft_Office_Crack_2022”
Inside this archive, users will find:
- two Dynamic Link Library (DLL) files (win-32.dll and win-64.dll)
- An executable (@fomicvell.exe)
- a folder named “data”
The file is protected by a password—”YUKI”—which is provided alongside the download link in the video’s description.
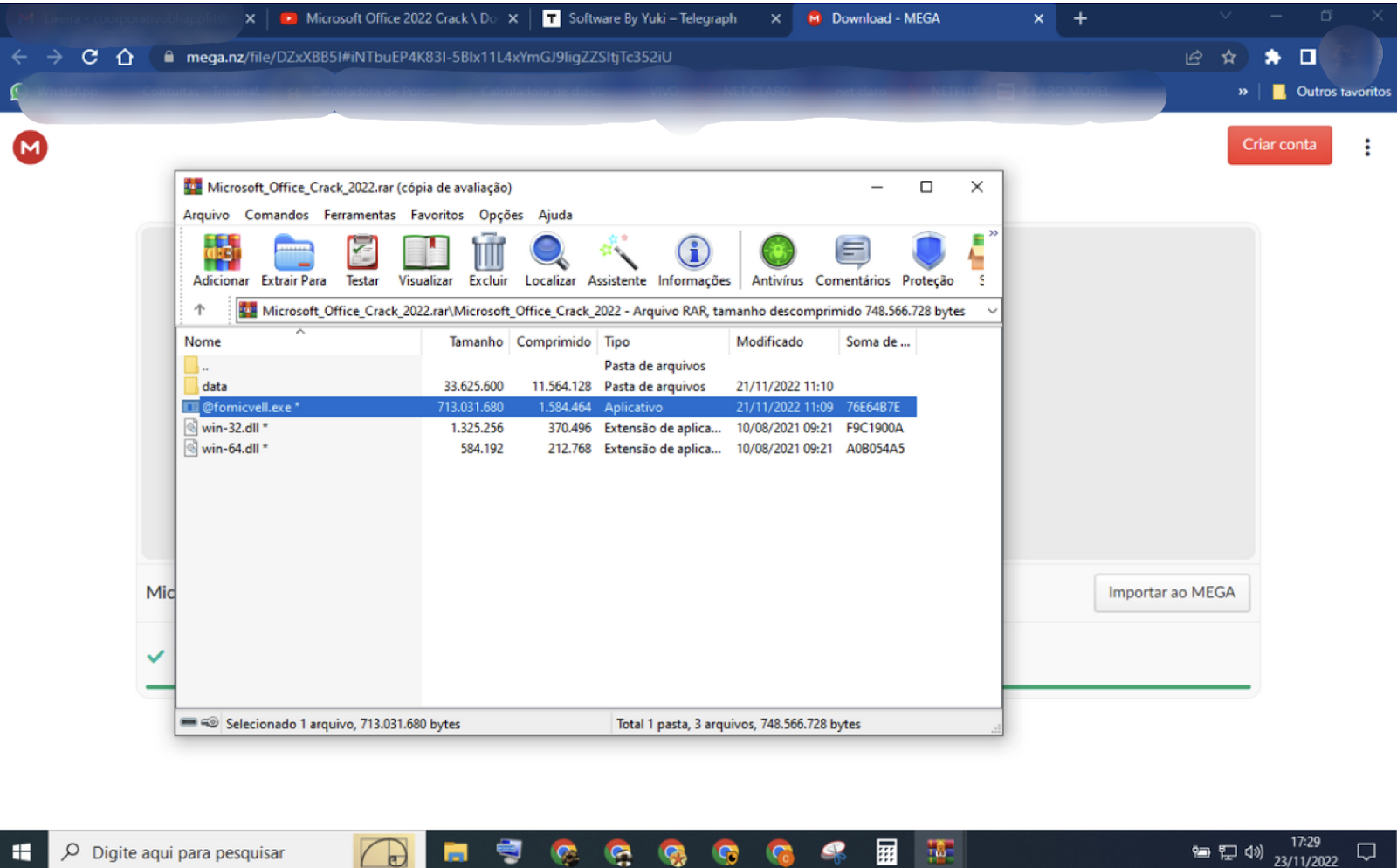
The archive shows two Dynamic Link Library (DLL) files, an executable, and a folder named “data”
In many cases infostealer variants deliberately password protect the ZIP files to prevent anti-malware scans from detecting viruses when the file is downloaded. In some cases we’ve seen actors provide specific instructions to new infostealer distributors on the best ways to maximize the chances of evading AV technologies.
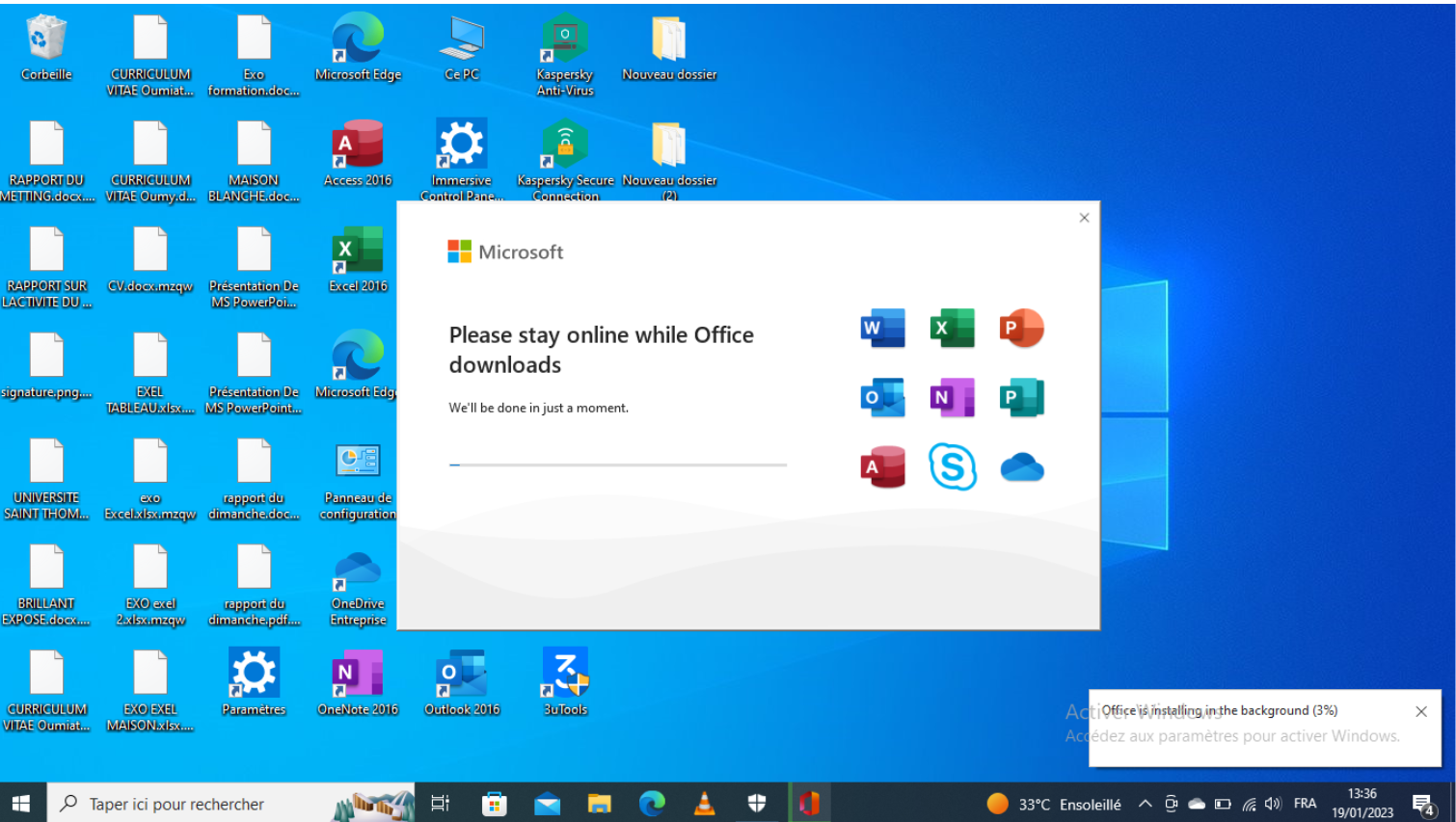
While downloading the infostealer malware, the user sees what looks like a legitimate Microsoft popup
Once the archive is extracted, the user believes they are gaining access to a free, cracked version of Office. However, instead of legitimate software, they’ve unwittingly installed an infostealer malware variant designed to harvest sensitive information, including passwords, credentials and cookies.
The Midjourney Campaign
Midjourney is an AI-based art generation platform, launched in July 2022, that quickly established itself as one of the leading tools for AI-generated art. Initially free to use, it has since transitioned to a subscription-based model. Surfing on this new wave of public interest, cybercriminals decided to capitalize on users’ desire to access Midjourney’s services without paying.
Midjourney users currently and have historically accessed the service through Discord which allows them to join channels and generate images through those channels.
Several malicious domains mimicking Midjourney’s legitimate site were identified, including “ai.mid-journey.org” and “get.mid-journey.com”. One of the primary infection vectors is a sponsored Google ad for get.mid-journey.org. Despite users’ browsers displaying a verified security badge for the legitimate site below the ad, many click on the sponsored link, assuming it is safe.

The search for “midjourney” shows sponsored posts that lead to malicious domains
Once users fall for the trap, they are presented with a web page that closely resembles Midjourney’s official platform. Upon clicking, the user is redirected to a page that introduces a supposed “beta version” of the software, accompanied by a warning that the program may trigger antivirus alerts.
The malware authors work to reassure users by claiming such alerts are “typical” and “expected” for beta versions, encouraging them to disable their antivirus software for a “successful installation.”
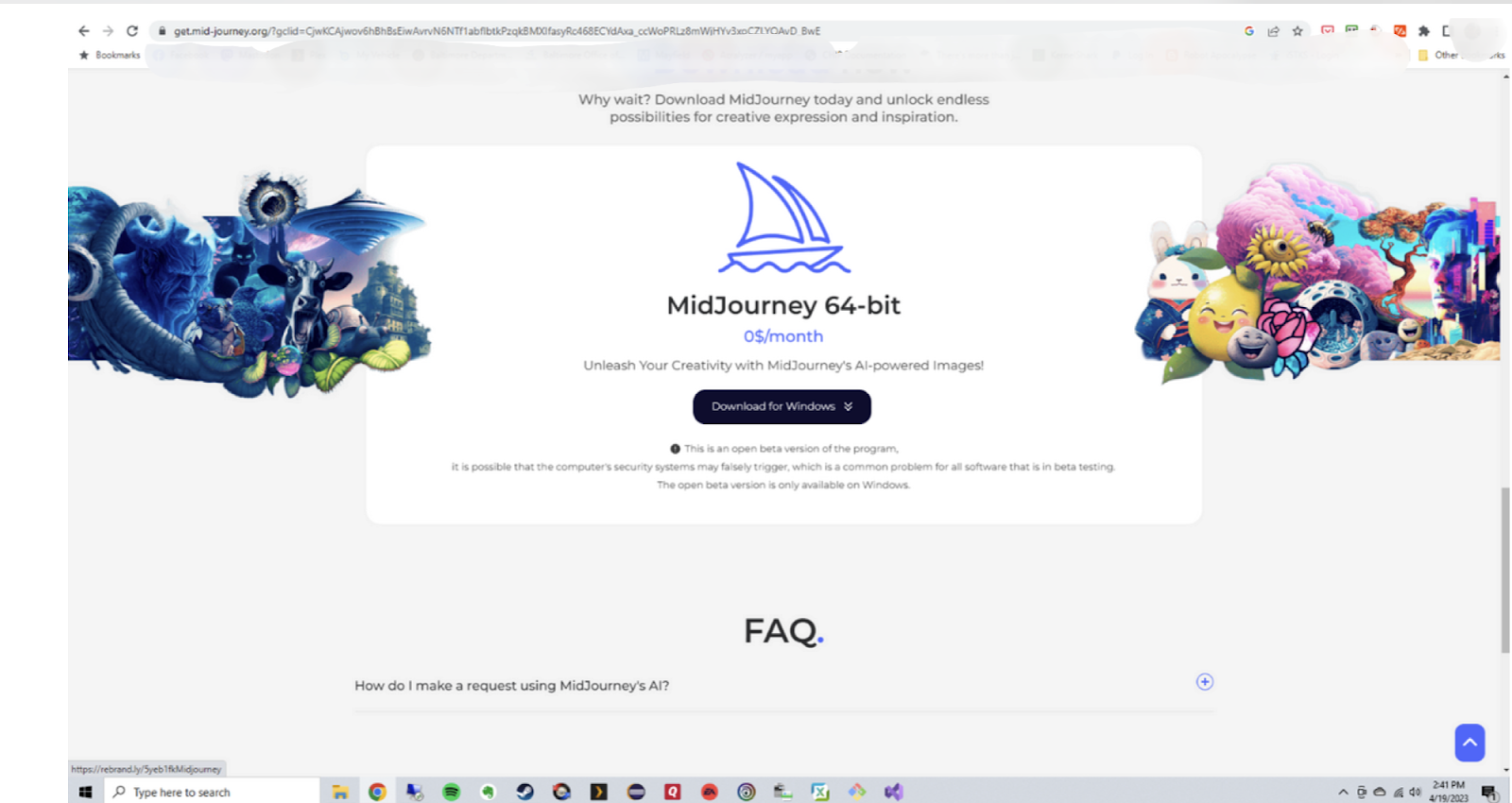
The falsified Midjourney download page shows a button to “Download for Windows”
Note that this screenshot includes a “Download for Windows” option even though Midjourney is primarily accessed through Discord (and does include a downloadable file).

This shows the downloaded “MidSetup” file
After downloading the executable and disabling their antivirus software, as advised, the installation proceeds. However, the software fails to run, instead prompting users to further disable their antivirus. Although this raises suspicion, users proceed since they were “warned” this would happen on the download page.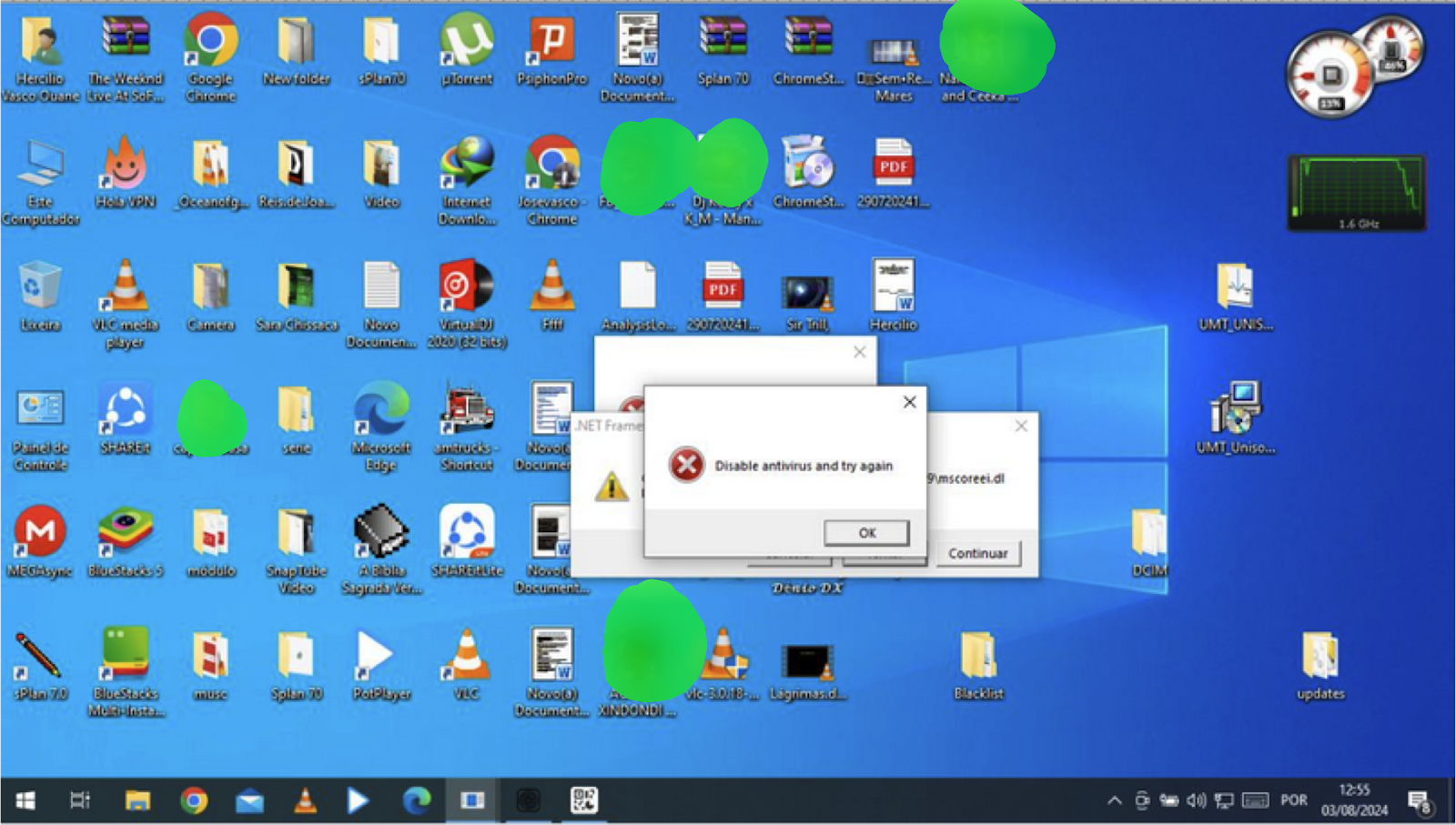
When installing the file, a few popups display asking the user to disable the antivirus
Users search on how to disable their antivirus. After following instructions to disable the antivirus, the system becomes vulnerable, and the infostealer malware executes. While users may initially hope for access to free Midjourney software, they soon discover that the program still doesn’t work.
Further investigation is initiated by user searches such as “is ai.midjourney a virus?”, which reveals that the user has been deceived. By then, their system has already been infected, leading to the theft of sensitive information such as passwords, cookies, and personal files.
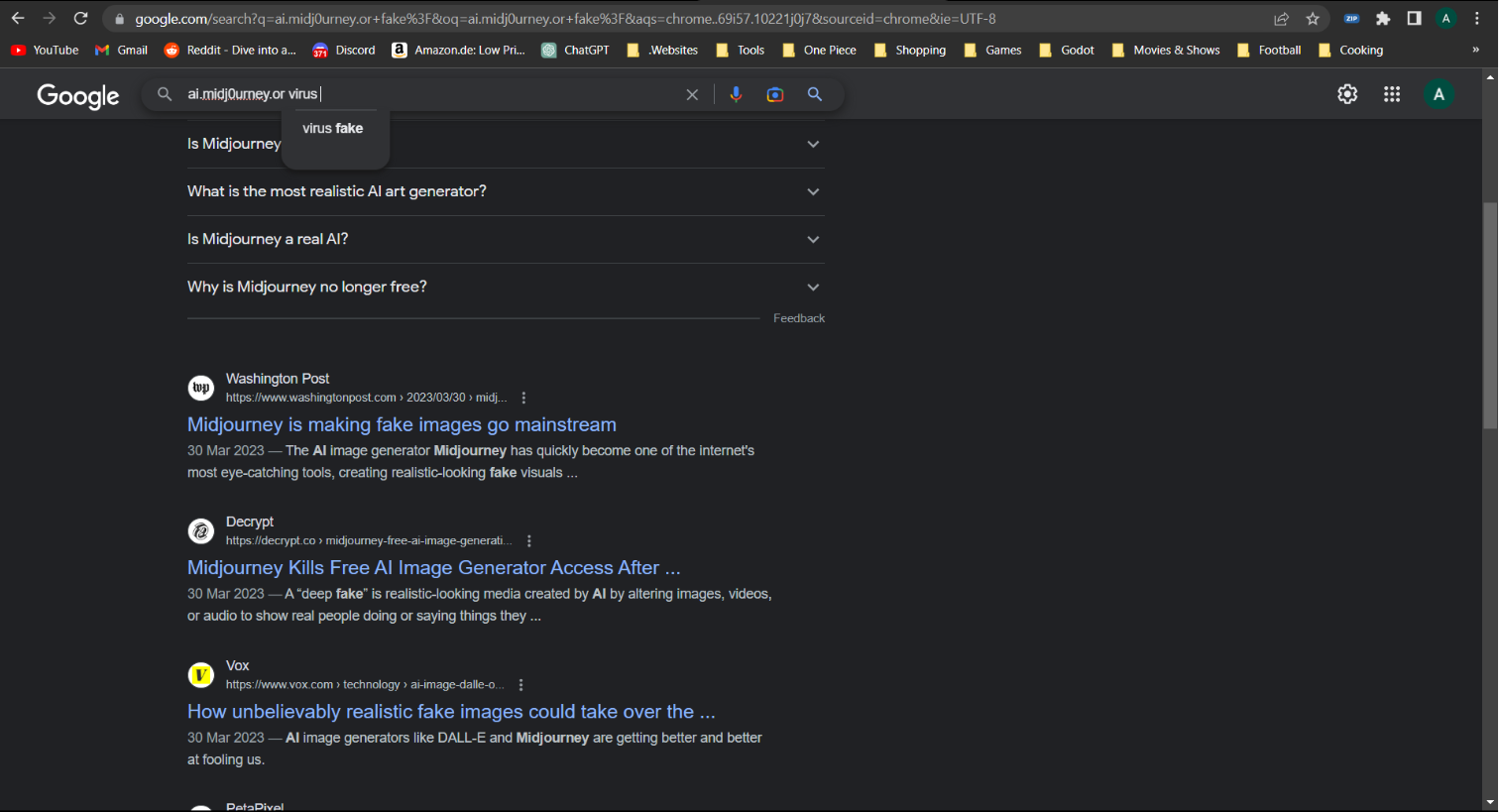
A user who has downloaded the malware searches for “ai.midj0urney.or virus”
In this final screenshot, we can see where a user who has downloaded the malware is now searching to verify whether the website “ai.midj0urney” is real or a virus. In many cases we saw victims searching to try and identify why their software wasn’t working or whether they had just downloaded a virus (spoiler: unfortunately they had).
The Dynamics of a Campaign
From the two campaigns we’ve discussed, the architecture of an infostealer campaign is clear. Threat actors target commonly used software packages (or new and exciting products being released in the case of Midjourney). They advertise by taking over legitimate YouTube and Google Ads accounts, then run those until they are banned which enables them to gain mass audience reach.
The first campaign ran the following playbook:
- Victim searches for “Microsoft Office 2022 crack” on YouTube.
- YouTube video from the DataStat channel lures victims with a download link for “free Office.”
- Link redirects to a Telegraph page promising free Office software.
- Malware hosted on MEGA.nz, users download a compressed archive.
- Inside the archive: two DLL files (win-32.dll and win-64.dll), an executable (@fomicvell.exe), and a folder named “data.”
- Archive password is provided as “YUKI” in the video description.
- Once extracted and executed, the malware installs infostealer to harvest sensitive information (passwords, credentials, cookies).
And the second instead leveraged malvertising:
- Users search for free access to Midjourney and click on a Google-sponsored ad for a fake domain (e.g., get.mid-journey.org).
- Users are redirected to a website mimicking Midjourney’s platform, offering a “Download for Windows” option.
- Download page warns about antivirus alerts and advises users to disable their antivirus.
- Users download a malicious executable and follow instructions to disable their antivirus.
- The malware installs, stealing sensitive data (passwords, cookies, personal files).
- Victims often search afterward to verify if the website was a virus, realizing they’ve been infected.
These campaigns don’t happen in isolation. Instead every step is supported by various elements of the cybercrime ecosystem which equip actors with the malware, accounts, and infrastructure they need to successfully run campaigns.
Monitoring for Stealer Logs with Flare
The Flare Threat Exposure Management (TEM) solution empowers organizations to proactively detect, prioritize, and mitigate the types of exposures commonly exploited by threat actors. Our platform automatically scans the clear & dark web and illicit Telegram channels 24/7 to discover unknown events, prioritize risks, and deliver actionable intelligence you can use instantly to improve security.
Our customer CISO said:
“Stealer logs have been the [sources] where we have seen the most actionable intelligence [with Flare] regarding leaked credentials.”
Flare integrates into your security program in 30 minutes and often replaces several SaaS and open source tools. Learn more by signing up for our free trial.





