Simplifying compliance with real-time data protection
Flare for Compliance
Improve Your Compliance Posture with Threat Exposure Management
Start a Free Trial



Protecting Your Digital Footprint
Flare Threat Exposure Management
Flare Threat Exposure Management helps customers meet higher compliance standards by enabling broader visibility across a variety of threat exposures while addressing requirements related to threat intelligence, third-party risk, and incident response.
Start a Free Trial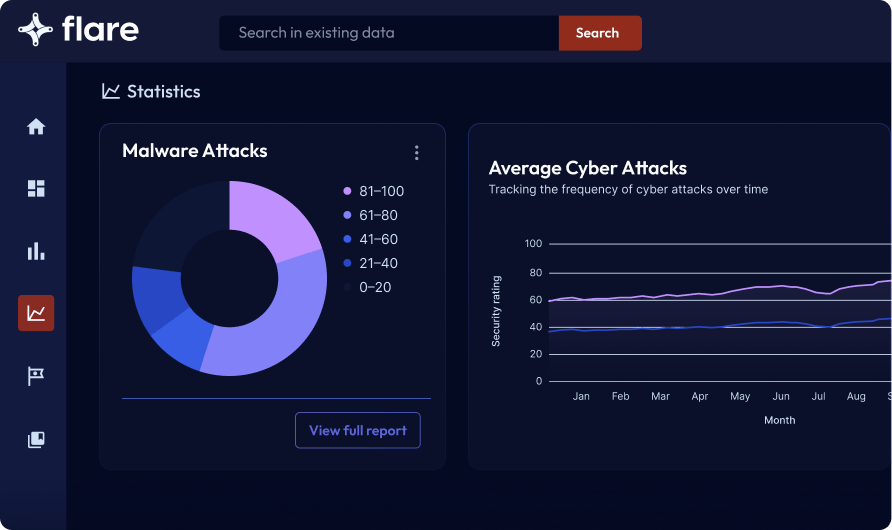
Streamlined compliance for GRC teams
What Your GRC Team Will Love about Flare
Flare brings together threat intelligence, digital risk protection, and attack surface management in a powerful, flexible solution. With unlimited seats, collaboration between GRC and SecOps teams is seamless, enhancing overall security.
Versatility
Flare unifies the core elements of threat intelligence, digital risk protection, and attack surface management into a simple, flexible, and powerful Threat Exposure Management solution.
Accessibility
You don’t need to be a threat hunting expert to use Flare. The platform is easy to use and typically set up in 30 minutes, making it accessible to GRC professionals.
Collaboration
Unlimited seat count means anyone at your organization can use Flare, presenting a unique collaboration opportunity for GRC and SecOps teams, leading to an improved overall security posture.
Robust Integrations
Easily integrate with SIEM, SOAR, Ticketing, and other core systems for alignment with existing security workflows.

“With all the European Union and German data protection laws, customers want to have comprehensive coverage and understanding about their external threat exposures. Implementing automated identity intelligence monitoring made sense for our team and our customers”
CTO, German MSSP
Navigating Compliance with Confidence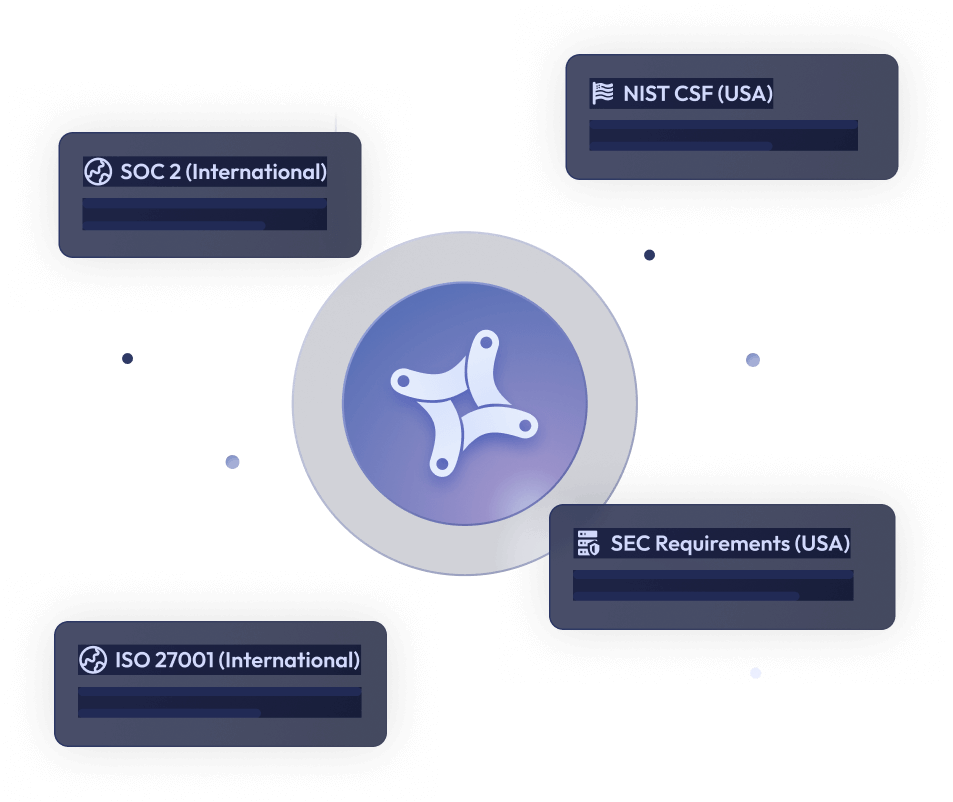
How Flare Aligns within Frameworks and Laws
Solving compliance challenges is a cumulative and ongoing effort with many moving parts. Investing in Flare can contribute to a better cybersecurity compliance posture for the following laws and frameworks.
Start a Free Trial
NIST CSF (USA)
Telemetry between clear & dark web sources of risk ranging from secrets disclosure on public GitHub repositories to Attack Infrastructure being set up
ISO 27001 (International)
Annex A Control 5.7: Threat Intelligence requires organizations to collect, analyze, and produce threat intelligence regarding information security threat
SOC 2 (International)
SEC Cybersecurity Requirements (USA)
HIPAA (USA)
PHIPA (Canada)
NIS2 (Europe)
automatically detects threats
What is Continuous Threat Exposure Management (CTEM)?
Continuous Threat Exposure Management (CTEM) is an emerging strategic security program that integrates cyber threat intelligence (CTI), digital risk protection (DRP), external attack surface management (EASM), and other functions.
This convergence enables organizations to proactively identify, prioritize, and respond to the types of exposure threat actors most commonly leverage to attack companies.
Flare’s platform serves as the focal point for integrating exposure management throughout the security function creating continuous risk reduction and improving compliance posture.
Start a Free TrialCTEM is Gartner's Top Strategic Technology Trend for 2024
Companies implementing Threat Exposure Management processes will see a 66% decline in data breach risk by 2026
60% of organizations are actively developing or considering implementing a Continuous Threat Exposure Management Program

Flare Compliance Use Cases
Empower your organization by navigating compliance challenges with comprehensive Flare solutions
Governance Risk and Compliance
Get Ahead of the Changing Compliance Landscape
- Improve your compliance posture by accounting for a variety of threat exposures and vulnerabilities.
- Ensure broad threat exposure coverage including vulnerabilities, leaked credentials, cloud misconfigurations, GitHub repositories, and more.
- Utilize unified threat intelligence, attack surface management, and dark web monitoring.
Third-Party Risk
Innovative Supply Chain Threat Exposure Detection
- Boost your TPR function by understanding your level of exposure from breaches that occur in your supply chain with precision.
- Establish robust monitoring and data collection of third party ransomware incidents.
- Achieve rapid detection and risk determination of threat exposures found in ransomware data leaks.
Incident Response
Augment Incident Response Plans and Playbooks
- Achieve timely breach detection, reduced IR costs, and solidified post-breach exposure monitoring.
- Monitor for threat exposures that are early indicators of a potential data breach.
- Account for risks and exposures related to previous breaches indefinitely.
Threat Intelligence
Satisfy Common Threat Intelligence Requirements
- Directly address threat intelligence requirements in NIST CSF and ISO 27001.
- Gain ungated and unlimited threat intelligence access.
- Utilize AI-powered reporting to accelerate analysis and communication.

Essential Information in One Place
Explore ResourcesFeatured Resources
Explore Flare’s Resource Center for the latest research, security updates, expert blogs, and valuable insights.