Today we’re covering two cybercrime stories:
- Cybersecurity practitioners living double lives and allegedly working with ALPHV
- Russian police arrested three threat actors accused of developing and selling the Meduza stealer malware
Leaky Weekly is taking a break this week and Nick spoke with Simply Cyber – Gerald Auger, PhD for 2025 Cybercrime Wrapped:
Keep reading for current events in cybercrime.
Cyber Practitioners Living Double Lives as Ransomware Collaborators
Two cybersecurity professionals have been indicted in Florida earlier this month for allegedly working with ransomware ALPHV, also known as BlackCat, as affiliates to extort companies across the US.
According to a recently unsealed federal indictment, former incident response manager Ryan Clifford Goldberg and former ransomware negotiator Kevin Tyler Martin allegedly conspired to deploy ransomware and extort victims for profit.
On June 17, 2025, the FBI spoke with Clifford Goldberg and after initially denying any involvement with BlackCat, he confessed that he was recruited to “try and ransom some companies.”
Prosecutors say the two, along with an unnamed accomplice from Florida, partnered with BlackCat between May 2023 and April 2025. The group allegedly targeted at least five organizations, demanding multimillion-dollar ransoms.
In one case, a Tampa-based medical device manufacturer paid roughly $1.27 million in cryptocurrency to regain access to its encrypted servers. Just one year after the alleged $1.27M ransom, Ryan presented at the Technology Law Conference in Texas about helping companies with ransom negotiations.
The indictment charges the defendants with:
- Conspiracy to interfere with interstate commerce
- Extortion
- Intentional damage to protected computers.
BlackCat is a ransomware-as-a-service operation that has targeted hundreds of organizations worldwide. Law enforcement seized its leak sites in late 2023 and released a decryptor to over 500 victims, but they remained active until 2024 before being disbanded.
Meduza Stealer Arrests
Russian police have arrested three hackers accused of developing and selling the Meduza stealer malware, in a rare case of a domestic cybercrime arrest.
Meduza stealer has common features such as:
- Web panel for administration
- Encrypted logs
- Support to exfiltrate data from 107 different cryptocurrency wallets, and 106 different browsers
- File exfiltration by extension
- Environment variables
- Installed software
- Windows credential manager
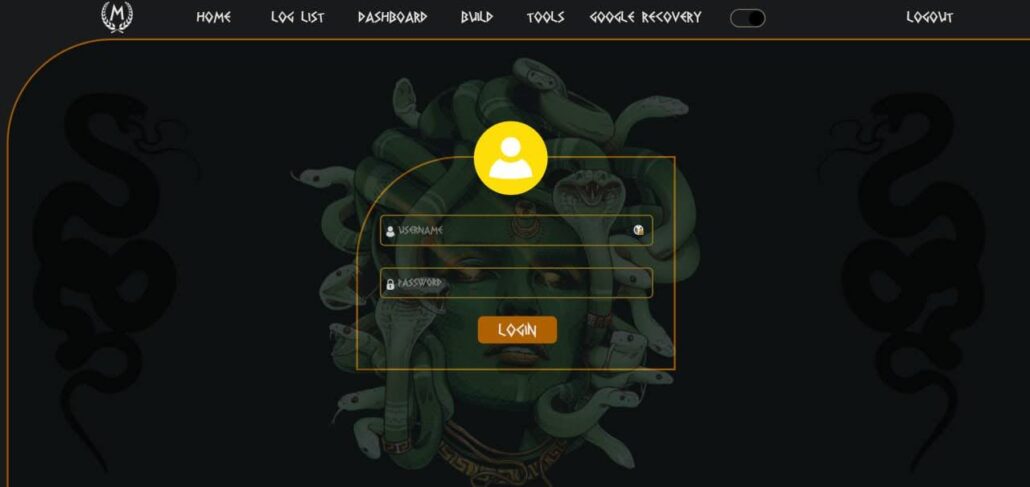
Screenshot of Meduza login portal (Source: Flare)
Authorities said the group began distributing Meduza stealer on hacker forums about two years ago. In one case earlier this year, they allegedly used it to steal data from a region of Russia.
Chatter from their official Telegram communication channel (Source: Flare)
During raids on the threat actors’ homes, police seized computers, phones, and bank cards.
Meduza first appeared in 2023 and is sold on forums like XSS and Telegram channels as a paid service. The malware has been used in attacks stealing personal and financial data, and has also been linked to campaigns in Ukraine, Poland, and inside Russia itself.
Russia’s arrest of domestic hackers is rare, but it is suspected that the arrest has happened due to the malware infecting a Russian government network in the Astrakhan region last year. Targeting Russia or CIS countries is perceived as a social blunder within the cybercrime world.
Leaky Weekly and Flare Academy
Leaky Weekly is brought to you by Flare, Threat Exposure Management solution and industry-leading dataset on cybercrime that integrates into your security program in 30 minutes. Check out what’s on the dark web (and more) about your organization with a free trial.
Check out Flare Academy:
- Our free training series led by experts on critical topics such as threat intelligence, operational security, and advanced investigation techniques (earn CPE credits towards cybersecurity certifications)
- Our Discord community is a space to learn from and with cybersecurity professionals and students, check out previous training resources, and keep up with upcoming training