
In Collaboration with Socura
The Financial Times Stock Exchange (FTSE) 100 Index includes some of the United Kingdom’s largest and most recognizable brands. These companies may be expected to have the most expansive cybersecurity budgets and capabilities, but many of these companies struggle with the same security issues that challenge small and mid-sized businesses. Companies of all sizes are vulnerable to security risks arising from weak passwords, employees using corporate email addresses for personal services, and devices infected with infostealer malware.
With all organizations facing similar risks, Socura and Flare collaborated to analyze the domains of all FTSE 100 companies for insight into leaked and stolen credentials to help security teams and organizational leadership make data-driven decisions. Here are the key takeaways from our findings:
What are the Top Five Findings About Leaked and Stolen Credentials on the Clear and Dark Web?
- 460,000 instances of leaked credentials are linked to corporate email addresses across FTSE 100 companies
- 45,000 instances of leaked credentials are associated with one FTSE 100 company alone
- 28,000 instances of corporate credentials from FTSE 100 business are leaked via stealer logs
- 59% of FTSE 100 companies have at least one instance of an employee using “password” as a password
- CEOs and CXOs have email addresses and passwords shared on dark web sites like Doxbin
What are the Risks When Employees Link Corporate Emails Addresses to Personal Services?
For a sense of scope, the number of leaked credentials related to this problem is approximately the same as the entire population of Bristol in the U.K. or Long Beach in California.
When employees use corporate emails for personal services, a company’s data breach risk now extends far beyond the traditional use case. Since people often reuse passwords across multiple services, a corporate email with a password linked to a video game service suddenly creates a corporate risk if the person reused the password for their work access.
Most often, threat actors have collections of login information in combolists, large files with stolen data sold or distributed across the dark web. With this data, they can sort by email domain which is usually related to the company’s name. From there, they can try all emails and passwords from the consumer data breach in a credential-based attack against the corporation.
We found that some organizations have as many as 45,000 instances of leaked credentials that exist outside their corporate control.
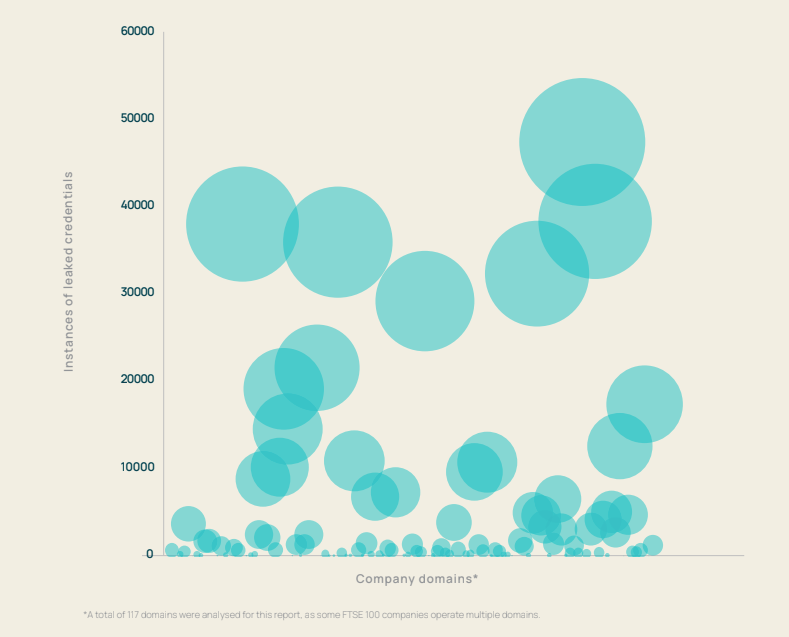
Graph of number of instances of leaked credentials for each FTSE 100 company domain (company names are left blank on the x-axis to anonymize the data)
Why Do Stealer Logs Matter?
Stealer logs come from infostealer malware that users accidentally download to their devices. The malware often collects more than credentials, also extracting documents or other data stored on the devices.
On average, our research found that each FTSE 100 business had 280 instances of employee credentials stolen. For each of those 280 instances of employee credentials, the stealer malware may also have collected any of the following information stored on the user’s device:
- Financial information
- Browser history
- System details
Armed with this information, attackers can:
- Sell sensitive information on the dark web
- Blackmail users for financial gain
- Use system information to impersonate a device to evade security detections
For example, the Snow infostealer campaign targeted a cracked version of Microsoft Office 2022, infiltrating devices across French, English, Spanish, Turkish, Portuguese, Chinese, and Korean devices. The threat actors harvested passwords, credentials, and cookies that they could then either use for gaining initial access or sell to other malicious actors.
How Does the Credential Economy Work?
The credential economy thrives in cybercrime forums and illicit Telegram channels where threat actors discuss, sell, and use stolen credentials. Our researchers identified mentions of FTSE 100 credentials across these conversations.
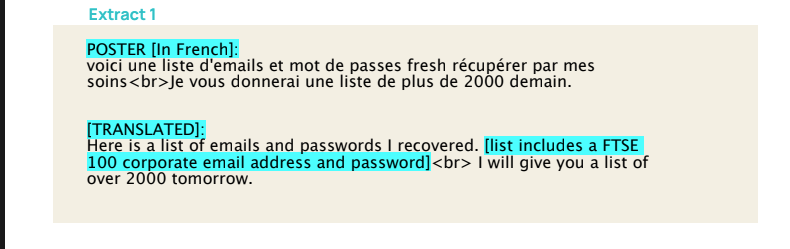
Example of a threat actor discussion
The credential economy also includes stealing session cookies and session hijacking. Earlier this year, we took a random sample of 20 of the 100 web applications used to access multiple industries, identifying a median of 2.1 exposed user accounts and a median of 1.4% web application account takeover exposure rate.
For many threat actors, infostealer malware that collects these credentials and session cookies offers high financial return on investment when they sell them across these illicit channels. Malicious actors purchase these credentials so that they can gain initial access to deploy payloads, like ransomware.
Why Do Threat Actors Target the C-Suite?
While leaked credentials occur across all organizational levels, our research identified a few leaks related specifically to senior leadership members. Our researchers used a sample of 12 FTSE 100 CEOs. Among other findings, we identified 4 who had personal information shared on Doxbin and 1 who had used a corporate email for a personal service.
Malicious actors actively seek out these credentials for several reasons:
- Senior leadership often has access to highly sensitive corporate information that malicious actors can use for extortion or corporate espionage
- Senior leadership often has privileged access to systems, especially financial applications
- Impersonating senior leadership team members enables malicious actors to improve social engineering attacks, like phishing emails
For example, recent research notes that 72% of senior executives have been targeted by cyberattacks in the past 18 months.
How Can Organizations Mitigate Password Reuse Problems?
In 2024, the average number of passwords used for business-related accounts was 87. To prevent the friction of making a new password every time they forget it, many people choose a word or phrase that has personal meaning and use it in different locations.
In the UK, the premier league’s popularity and people’s favorite teams were apparent in various corporate passwords:
- “Liverpool” was the most popular club name used as a password with 9% of FTSE companies using the football/soccer team’s name
- Meanwhile, two variants of Arsenal showed up in the list, indicating the fan base’s expansiveness
Researching premier league passwords may seem inconsequential, but it provides insight into how people think when building their login data. For attackers, this reduces the barrier to initial access. If they know that people commonly use a word, they can deploy brute force attacks that try the password against all emails related to a domain. Even if organizational credentials remain off the illicit markets, the malicious actors can use geographic regions to try common terms, hoping to succeed at least once.
The Common Credential Risk Struggle
While this report focuses on the UK’s biggest and wealthiest companies, the reality is that mitigating stolen credential risk is a problem for organizations of all sizes. Our research focused on these organizations because they have more people which means more potential risk and, likely, more mentions across illicit channels.
Access the complete report: FTSE 100 for sale here.
Monitor for Stealer Logs with Flare
The Flare Threat Exposure Management solution empowers organizations to proactively detect, prioritize, and mitigate the types of exposures commonly exploited by threat actors. Our platform automatically scans the clear & dark web and prominent threat actor communities 24/7 to discover unknown events, prioritize risks, and deliver actionable intelligence you can use instantly to improve security.
Flare integrates into your security program in 30 minutes and often replaces several SaaS and open source tools. See what external threats are exposed for your organization by signing up for our free trial.




