By Flare Research
KNP Logistics, a UK-based transport company, collapsed in June 2023 after a ransomware attack. The full story surfaced later through bankruptcy filings and news coverage of the aftermath.
This is how many ransomware incidents become known: not through voluntary disclosure, but through the wreckage they leave behind. This doesn’t provide much for security teams to learn from to better fortify their operations.
That’s why we analyzed 500 records of SafePay’s victims to better understand who’s actually getting targeted. Keep reading for the highlights, and read our full report for details.
The SafePay Victim Profile is Remarkably Consistent
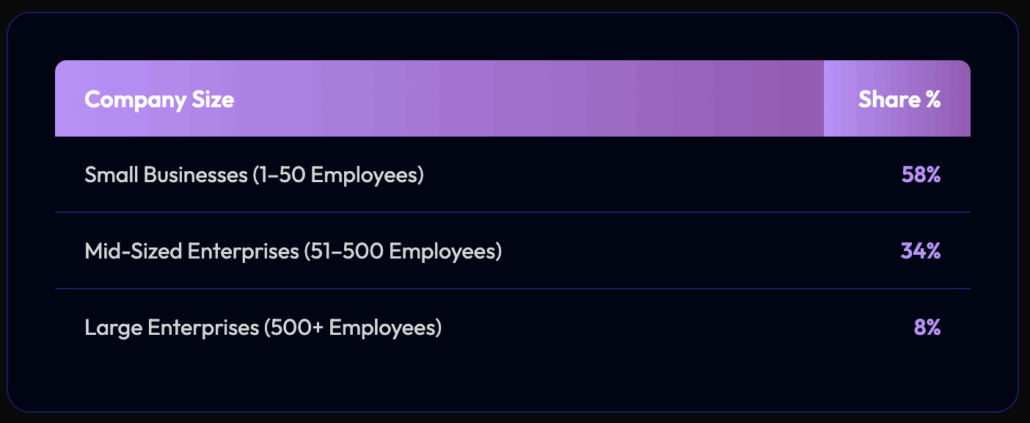
Over 90% of the Victims are Small and Mid-Sized Businesses
These are organizations with 1-500 employees, typically generating under $100M USD in annual revenue. Instead of hunting Fortune 500 targets that may have more resources to pay, they are actually targeting companies that are big enough to pay but small enough to lack the resources to respond to attacks.
Two-Thirds are Service-Based Organizations
Service-based companies make up 66% of the victims though they make up much less than that percentage of all businesses.
Geography Clusters around Regulation
41% of victims are in North America, 38% in Western Europe. The US and Germany alone account for nearly half of all cases. This isn’t coincidental, as GDPR, NIS2, HIPAA, and state breach-notification laws turn data leaks into existential business threats. Threat actors understand this leverage and exploit it deliberately.
Why Data About SafePay Victims Matter
Most ransomware incidents never get publicly reported. The FBI, ENISA, and UK authorities have all documented severe underreporting. Companies stay quiet to avoid regulatory scrutiny, customer panic, and insurance complications.
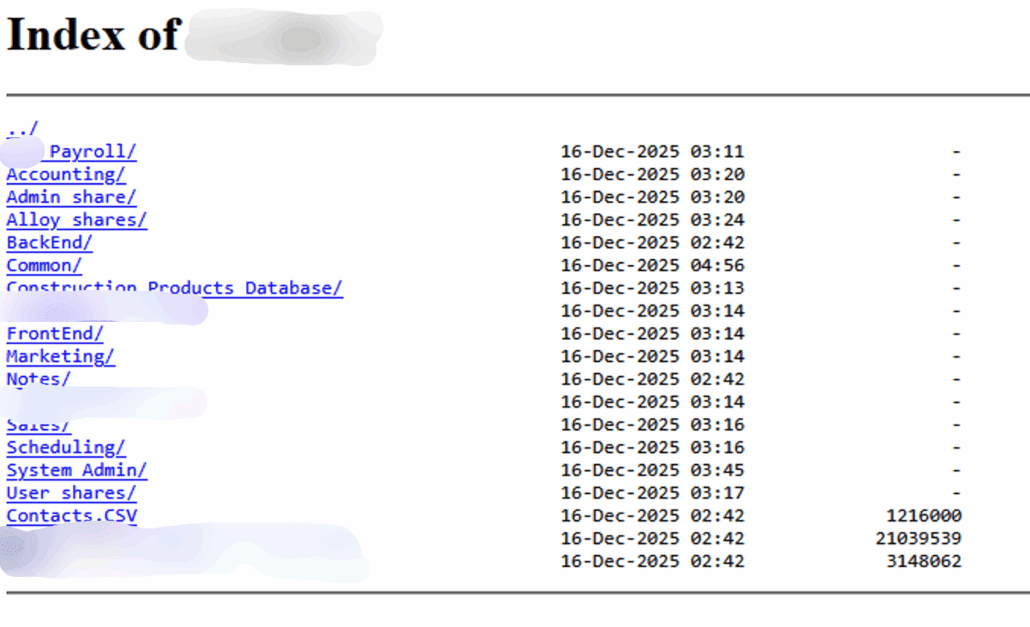
A screenshot from the Tor leak site, with invaluable business operational data
Leak site data fills that intelligence gap. It captures actual incidents rather than self-reported security postures or compliance checkboxes, but real evidence of who got breached and when. This makes it uniquely valuable for:
- Third-party risk management: Standard vendor questionnaires won’t tell you if a supplier was a ransomware victim last year, but leak site records will.
- M&A due diligence: Ransomware history affects valuation, data integrity assumptions, and post-merger integration risk. Finding out after the deal closes is expensive.
- Cyber insurance underwriting: Self-reported security controls only reveal so much. Claims data from leak sites provide information about which sectors and company profiles are repeatedly compromised.
SafePay’s Deliberate Targeting Strategy
SafePay isn’t spraying attacks randomly. The victim distribution reveals calculated economic targeting of:
- Companies whose operations stop immediately when IT goes down
- Organizations handling sensitive data (PII, PHI, legal/financial records)
- Businesses with limited security resources but significant regulatory obligations
- Regions where data breach laws create maximum financial and legal pressure
SMBs fit this profile perfectly. They lack enterprise-scale resilience but carry enterprise-scale liability. When systems are encrypted and data is stolen, they face the same GDPR fines and breach notification requirements as much larger companies, but without the resources to absorb the impact.
Recommendations for Security Teams
The consistent victim profile suggests clear defensive priorities:
- We recommend that organizations matching SafePay’s target demographic such as service-based SMBs in regulated industries can greatly benefit from focusing on the basics that prevent initial access: enforced MFA, credential hygiene, rapid patching, and network segmentation.
- Automated dark web monitoring provides intelligence that traditional vendor assessments may miss. Solutions like Flare continuously scan ransomware leak sites and can alert you when vendors, acquisition targets, or business partners appear, often before the compromised organization publicly acknowledges anything happened.
Ransomware groups succeed because they understand pressure points better than most defenders do. They know which companies can’t afford downtime, which sectors handle the most sensitive data, and which regulatory environments amplify extortion leverage. The SafePay data confirms what incident responders already know from the field: attackers aren’t opportunistic anymore. They’re running calculated operations against carefully selected targets.
The question isn’t whether your organization or your third-party vendors match the victim profile. It’s whether you’re monitoring the right signals to know when someone in your ecosystem gets hit, before the consequences reach you.
Learn more about our research into the 500 SafePay victim records with our full report, SafePay Ransomware: Mapping the Real Victims Behind the Leak Sites.
Ransomware Readiness with Flare
The Flare Threat Exposure Management solution empowers organizations to proactively detect, prioritize, and mitigate the types of exposures commonly exploited by threat actors. Our platform automatically scans the clear & dark web and prominent threat actor communities 24/7 to discover unknown events, prioritize risks, and deliver actionable intelligence you can use instantly to improve security.
Flare integrates into your security program in 30 minutes and often replaces several SaaS and open source tools. See what external threats are exposed for your organization by signing up for our free trial.