By Tammy Harper, Senior Threat Intelligence Researcher
One of the most trusted ransomware-adjacent forums in the cybercrime ecosystem is now offline. A seizure banner now greets visitors to RAMP, indicating coordinated action by US authorities against the platform that served as a hub for some of the most notorious ransomware operations in recent years.
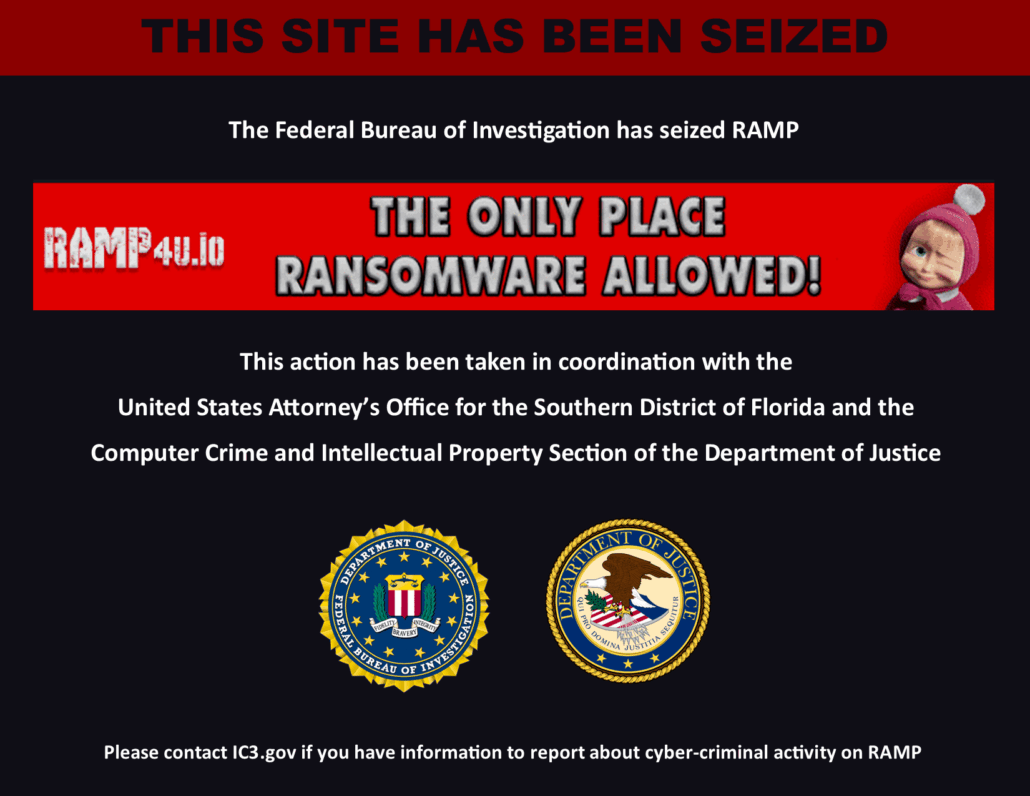
Seizure banner on the RAMP homepage
What Made RAMP Significant
RAMP was not just another discussion board. Ransomware groups including LockBit, ALPHV, Conti, DragonForce, Qilin, RansomHub, and others all operated on this forum at various points. The platform functioned as a preferred gathering space for ransomware operators, intermediaries, and affiliates, and was widely regarded as a high-trust escrow environment. The RAMP seizure represents a meaningful disruption to a core piece of criminal infrastructure.
Details of the RAMP Forum Seizure
While official details remain limited, the forum’s clear web and onion infrastructure appear to have been taken over, with DNS records reportedly pointing directly to the FBI. This suggests the RAMP seizure is not simply a voluntary shutdown or an exit scam, but rather an enforcement action with full control of the platform.
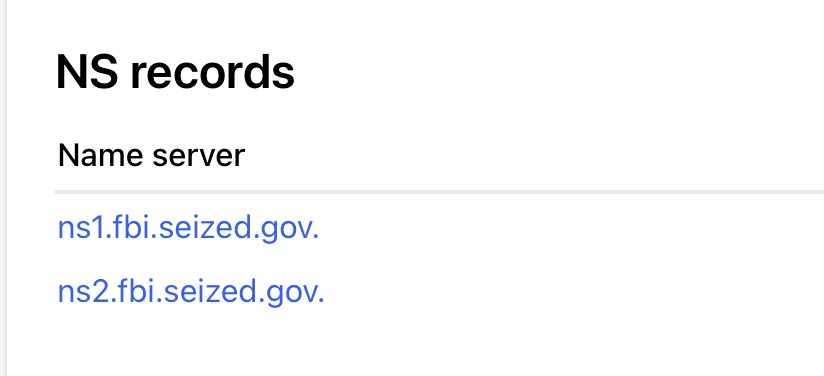
DNS records show FBI seizure
Ecosystem Fallout and Migration
The immediate fallout from the RAMP seizure is already unfolding. As with previous takedowns, the removal of a major hub does not eliminate the ecosystem, but forces migration. Groups such as Nova and DragonForce are reportedly shifting activity toward Rehub, illustrating the underground’s ability to reconstitute quickly in alternative spaces.
These transitions are often chaotic, opening new risks for threat actors: loss of reputation, escrow instability, operational exposure, and infiltration during the scramble to rebuild trust.
Forum Administrator Responds
Notably, Stallman (the forum administrator) has issued an official comment on the RAMP seizure, circulating widely across underground discussion spaces. In a message shared on XSS, he wrote:
“I regret to inform you that law enforcement has seized control of the Ramp forum… This event has destroyed years of my work building the freest forum in the world… It’s a risk we all take.”
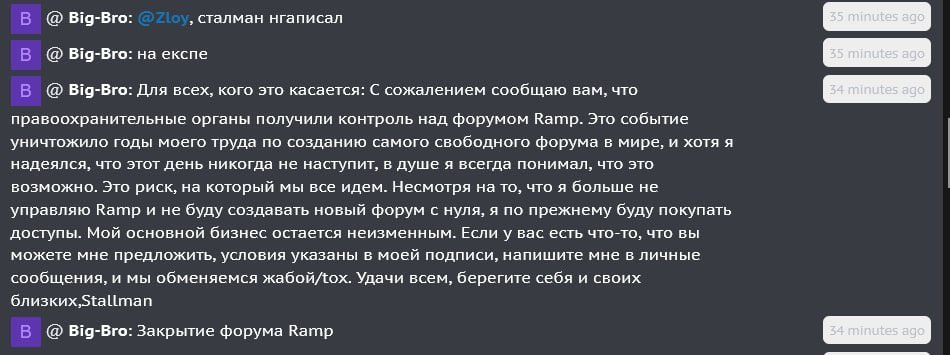
Chat from Stallman, the admin of RAMP, confirming the takedown on XSS (Source: Katya Kandratovich)
The statement underscores a recurring reality of cybercrime infrastructure: even the most established platforms remain vulnerable to law enforcement pressure, technical compromise, or human error.
What This Means for Security Teams
For security teams and intelligence analysts, seizures like the RAMP takedown provide rare opportunities, not only to disrupt ongoing criminal collaboration, but potentially to collect insight into affiliate networks, financial relationships, and operational security failures.
The RAMP seizure is significant, but the secondary effects may prove even more important: fragmentation, distrust, new forums rising to prominence, and the next generation of escrow-based ransomware marketplaces emerging in its place.
Monitor Cybercrime Activity with Flare
The Flare Threat Exposure Management solution empowers organizations to proactively detect, prioritize, and mitigate the types of exposures commonly exploited by threat actors. Our platform automatically scans the clear & dark web and prominent threat actor communities 24/7 to discover unknown events, prioritize risks, and deliver actionable intelligence you can use instantly to improve security. Flare has the broadest range of cybercrime coverage, and as RAMP users and criminal activity shifts toward Rehub, security practioners can trust that Flare includes Rehub coverage, as it has since Rehub’s inception.
Flare integrates into your security program in 30 minutes and often replaces several SaaS and open source tools. See what external threats are exposed for your organization by signing up for our free trial.