
While malicious actors have developed countless attack methods, spam remains to this day a significant threat vector for companies. The most recent statistics on spam are indicative of the danger that spam poses:
- 95% of all attacks targeting enterprise networks are caused by successful spear phishing.
- A single spear phishing attack results in an average loss of $1.6 million.
- 30% of phishing emails are opened by users, and 12% of these targeted users click on the malicious link or attachment.
- 1 in every 8 employees shares information on a phishing site.
Many spammers do not have the time, expertise and resources to acquire an infrastructure that can pump out large amounts of spams. Instead, spammers rent out infrastructures that have been hacked by others, and use it to send spam for as long as they can.
Abusing PHPMailer Library
PHPMailer is perhaps the oldest, and most popular library in PHP to send emails. Anyone can download it from Github and install it in a matter of minutes. The library is known for its reliability and efficiency. It also offers features such as the ability to send HTML and non-HTML emails, and provide extensive error messages to report on its activities.
It is no surprise to see that this script has been adopted extensively in the criminal underground. Many posts in underground forums talk favourably about the library. We find for example:
Using a SMTP mailer (like phpmailer for example) is a much better and easier option, as it gives you much more options out of the box.
The script can be installed by malicious actors on a web server that has been hacked. The server’s resources and reputation is then abused to send out spam that appears to be coming from a legitimate source.
Another option is for malicious actors to exploit a vulnerability in an installed version of PHPMailer to make it send spam. PHPMailer is regularly updated to fix security flaws, but is not always timely updated on web servers. This opens an important window of attack that can be abused by malicious actors.
Renting PHPMailers
There are dozens of marketplaces that facilitate the sale of numerous illicit goods and services, including hacked PHPMailer installations. We collected for a period of 10 days in April 2021 all of the PHPMailers for rent on one such marketplace from three countries: Canada, the United States and France. We present below our analysis of the PHPMailers for rent. More specifically, we look at the profile of vendors as well the profile of hacked PHPMailer installations.
Profile of vendors
Some vendors appear to be more active than others on the marketplace. Unfortunately, very little is known about the vendors themselves beyond an ID created by the market. The main seller, seller26, posted about 20% of all PHPMailer installations for rent. Seller165 and seller138 come in with 10% each of all PHPMailers. There is therefore a distinct group of sellers that is able to post more PHPMailers, and this group is composed of about 10 sellers.
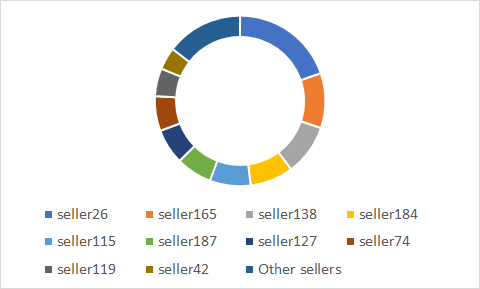
To calculate the sellers’ revenues, we added up the price of PHPMailers that were sold for each seller. This provided us with an estimate of the revenues for 9 days for each seller, which we can use to extrapolate revenues over the course of a year, if their revenues scaled linearly.
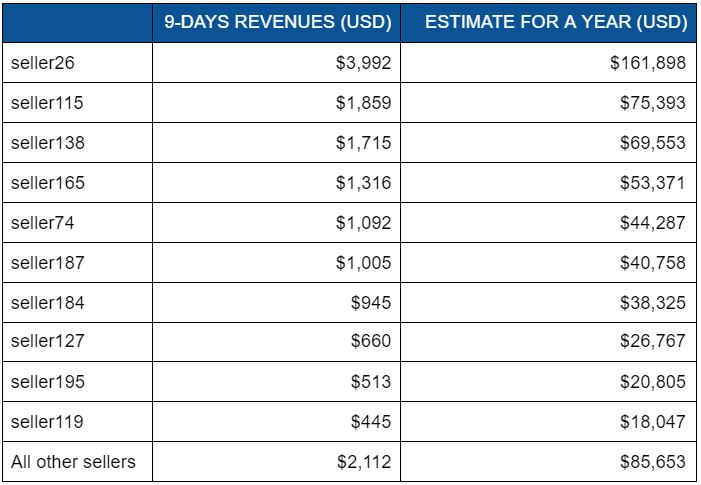
Our estimates suggest that sellers on average only make a few hundred dollars per year selling PHPMailers. Of course, these sellers can probably count on multiple revenue streams so this figure does not represent the entirety of their income. The top earner, seller26, probably earned over $165,000 through this marketplace alone. Only 8 other sellers probably broke through the $20,000 barrier. While there appears to be a correlation between the number of PHPMailers for sale and revenues, the link is not perfect as seller115, for example, is the second top earner, but comes in 5th when we count the number of PHPMailers for sale.
Profile of hacked PHPMailer installations
When we tested the 5,773 PHPMailers we observed on the marketplace, we only received 2,395 test emails. This suggests a 41% success rate.
This does not mean that 59% of PHPMailers for sale are fraudulent, meaning that they could not be used to send out spam if rented. There are many reasons why emails do not get to their destination, and we could not unfortunately test each PHPMailer more than once for technical reasons. Still, it is something to consider when evaluating the service of the marketplace.
For each PHPMailer, we obtained the domain name of the server it was hosted on. We tried to download the home page of each domain, pinging either the domain name itself, or prepending www to it if nothing was returned on the first try. In this analysis, we found that only 394 websites were actually up and running. This suggests that only 7% of PHPMailers are being run on servers actually hosting a website, most of them being run from web servers that appear to not be in use currently to host a website. We extracted for each the content of the title tag of the page. The word cloud below presents the main words found in the titles. We notice that WordPress and blog are the two most common words found, perhaps pointing to these as targets of malicious actors. The word Greece appears to be predominant, but that is mainly due to a single web page about Greek yachts and sailing that has the word repeated over and over again in the title. Another interesting finding is the word company which suggests that many hosting services appear to be related to companies rather than individuals.

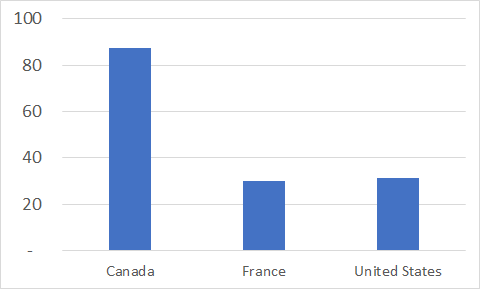
Finally, we calculated the average age of PHPMailers, meaning how long they had been for sale. Our data suggests that, on average, PHPMailers are for sale between 30 days (France, Canada) and 87 days (United States). The higher number for the United States can be explained by the higher level of competition among sellers, and the increased supply of PHPMailers. The maximum age of PHPMailers is around 450 days, meaning that unsold PHPMailers remain available on the website even when they are probably not operational anymore, or have not been maintained for quite some time.
Conclusions
Our analysis of the marketplace suggests that it is extremely easy for malicious actors to rent out PHPMailers to send out spam. There are thousands of PHPMailers available on any given day. These can be rented out for just a few dollars. This means that even when the mailers do not perform adequately, they can be quickly and cheaply replaced.
Our findings highlight the challenge of detecting and blocking spam coming into your corporate network. Malicious actors rent out virtual private servers that should have a somewhat high reputation. They are, or were at some point, used to host blogs and corporate websites, and therefore appear legitimate. Emails coming from these servers are likely to be seen as innocuous even though they could be spreading malware, or links to phishing sites.
Our analysis questions the role of web hosting services in the prevention of spam. Some web hosting companies actively monitor what their customers do with their servers, and their internet connection. There is clearly a debate to be had about the freedom to operate with no surveillance from large companies, and the freedom that the internet was supposed to afford to its users. Still, given the significant impact that spam has on companies large and small, the question remains whether web hosting services should be good citizens and detect as often as possible these hacked PHPMailers. The limited number of web hosting services also help us understand how small changes in just a few providers could go a long way to fight against spam.
So what should your company do?
This report suggests that spam you receive on a daily basis could be coming from virtual private servers with a high reputation. Your company should inquire with your email filtering providers how such emails are treated, and if they are given extra inspection given the suspicious nature of their sender.
You should also know that spam can and will be coming from all countries in the world, and that Canadian servers are not immune from sending out spam. Many believe that spam is mostly coming out of servers from Russia and China, but most spam facilitated by Olux.io should be expected to be coming from the United States. This reminds us that any geolocation analysis for spam is likely not to protect us much from the incoming spam.
You could also incorporate the data stream for the hosting service provider into your spam filtering systems to look more closely at emails coming from hosting services that appear to be victimized by hacked PHPMailers. We identified the biggest players in this ecosystem, and it may be reasonable to give a second look at emails that are coming from these companies’ web servers.





