By Andréanne Bergeron, Security Researcher
We recently attended the 80th annual American Society of Criminology (ASC) Annual Meeting to learn from and with academic criminologists from around the world. The thousands of presentations included:
- Latest research findings
- Theoretical advances
- Methodologies
- Emerging trends
Over the course of five days, more than 2,200 sessions took place. Our review found 59 sessions that had some connection to cybercrime, representing just slightly over 2% of all presentations, proving a growing interest among this community.
Key Themes in Cybercrime Research
Several panels explored who commits cybercrimes and why, examining the psychology, motivations, and behavioral patterns of offenders. Another strong theme focused on victimization, including studies on digital harassment, online coercion, and exploitation.
Many sessions also discussed how law enforcement and institutions are adapting to the evolving cyber threat landscape. As in previous years, a recurring observation was that police agencies continue to struggle to keep pace with technological change.
One particularly insightful presentation by Wei-Gin Lee (George Mason University) highlighted several systemic challenges:
- Lack of specialized skills and training in cybercrime investigation
- Absence of clear, unified definitions of “cybercrime”
- Insufficient funding for cyber training and research
Lee emphasized the need for empirical data, experimental research designs, and evaluations of training programs, concluding that partnerships with the private sector could help bridge many of these gaps.
A smaller cluster of panels delved into the digital underground, covering topics such as online marketplaces, decentralized finance, and cryptocurrency use.
Several sessions explored emerging technologies (AI, automation, robotics, and OSINT) and their intersection with criminal justice systems. Others emphasized education and prevention, showcasing research initiatives that build awareness, capacity, and collaboration in the fight against cybercrime.
One standout presentation came from Timothy A. Engle (University of Cincinnati), who examined the concept of “laziness” in adopting cybersecurity hygiene practices. His study found that enhancing perceptions of confidence and importance around cyber hygiene can significantly improve user behaviors.
The findings also hint at a form of cybercrime apathy: individuals feeling overwhelmed by the growing number of security practices they are expected to follow. Understanding this human element is essential when designing realistic, user-centered cybersecurity solutions. Related to that finding, researchers from Flare studied how shifts in policy changes and design practices over the course of about two decades increased password strength by 20x.
Flare at ASC 2025
And yes: Flare was there!
We participated in the poster session, widely considered one of the most enjoyable events of the week: a lively wine and cheese networking evening where informal discussions often spark great research ideas.
Our poster (appears below) presented our ongoing research on scoring users’ exposure levels, focusing on how different types of exposed information influence overall risk. We revealed a hidden hierarchy among 89 types of personally identifiable information (PII), empirically confirming that not all personal data carries equal risk.
Our findings show that high-risk PII (such as encryption keys, SMS messages, web activity, credentials, and identity documents) deserves the strongest protective controls. This methodology offers a foundation for prioritizing cybersecurity interventions based on actual exposure risk.
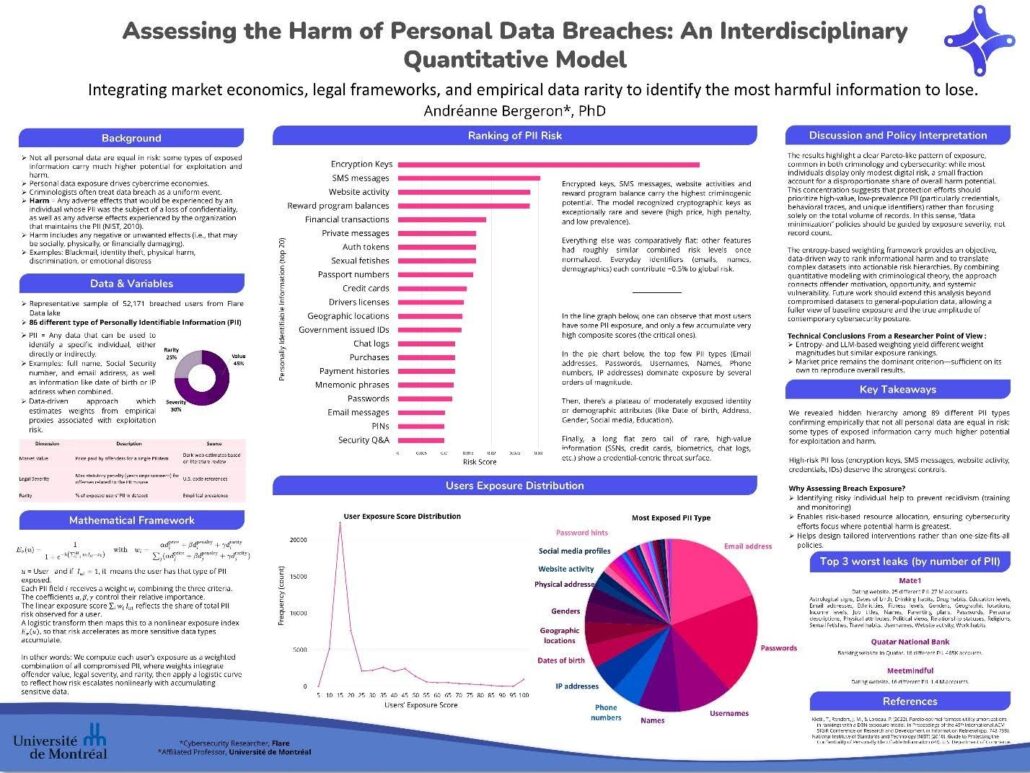
Poster presented about the negative impacts of personal data breaches
New Collaborations in this Fast-Paced Chapter of Cybercrime
While cybercrime remains a niche topic at ASC compared to traditional criminological research, the field is gaining traction. The discussions around law enforcement readiness, public–private collaboration, AI, and behavioral factors demonstrate a growing recognition that crime in the digital era demands new perspectives and new partnerships.
And Flare is proud to be part of that conversation.
Monitor Cybercrime with Flare
The Flare Threat Exposure Management solution empowers organizations to proactively detect, prioritize, and mitigate the types of exposures commonly exploited by threat actors. Our platform automatically scans the clear & dark web and prominent threat actor communities 24/7 to discover unknown events, prioritize risks, and deliver actionable intelligence you can use instantly to improve security.
Flare integrates into your security program in 30 minutes and often replaces several SaaS and open source tools. See what external threats are exposed for your organization by signing up for our free trial.