
This article was updated on August 18th, 2025.
While both the dark and deep web represent parts of the internet that fall outside the scope of traditional search engines, they differ in accessibility, use cases, and the types of threats they expose.
Understanding these differences, and implementing monitoring across both, is essential to building a Threat Exposure Management (TEM) program. That includes not only obscure forums and leak sites, but also widely used developer platforms like GitHub, which have increasingly become a source of risk for modern organizations.
Differences Between Dark and Deep Web Monitoring
There are multiple internet layers, and not everything is available for everyone. We’ll quickly define the dark and deep webs before getting into different monitoring approaches for security teams.
What Is the Deep Web?
The deep web refers to any part of the internet that is not indexed by traditional search engines like Google or Bing. This includes content that is behind paywalls, logins, or dynamic queries—essentially anything you can’t access without credentials or a direct URL.
Deep web monitoring focuses on data sources that are semi-public or semi-private, such as:
- Invite-only forums
- Niche marketplaces
- Paste sites and code-sharing platforms
- Messaging apps like Telegram
- Developer platforms like GitHub (this would mostly be considered the clear web but we’ll include this in the list for now)
While the deep web is not inherently malicious, it can be where threat actors gather, organize, and communicate—especially in underground forums that require vetting or technical access.
Why Monitor the Deep Web?
The deep web can include secrets that get accidentally leaked, such as sensitive data from GitHub repos and paste sites. In addition, messaging platforms such as Telegram can be a complement to dark web forums and marketplaces. They offer a place for threat actors to connect and discuss tactics, sell stealer logs, and more.
Security teams can use deep web monitoring to uncover early warning signs of compromise, identify accidental data leaks, and track emerging threat activity across semi-public platforms that threat actors increasingly use for coordination and reconnaissance.
Source Spotlight: GitHub
GitHub can be a source for data leaks, especially as developers can accidentally upload:
- Hardcoded credentials
- API keys and tokens
- Internal configuration files
- Proprietary code and IP
Organizations of all sizes, even large enterprises, can regularly leak sensitive data via public GitHub repos. The platform represents an often overlooked vector for cybercriminal reconnaissance and initial access.
With GitHub leak monitoring, security teams can detect exposed secrets and code before attackers exploit them, reduce the risk of supply chain compromise, and proactively mitigate threats by automating the identification and takedown of leaked credentials and sensitive assets.
Source Spotlight: Telegram
While the dark web isn’t going anywhere, threat actors are moving away from it in favor of more accessible platforms like Telegram. Threat actors find these encrypted messaging apps appealing because:
- It’s easier to connect with other threat actors without setting up a complicated dark web forum or marketplace.
- Threat actors don’t need to provide personally identifying information to create accounts and can stay anonymous.
- Telegram is designed for user-friendly messaging with no technical skills required to use it.
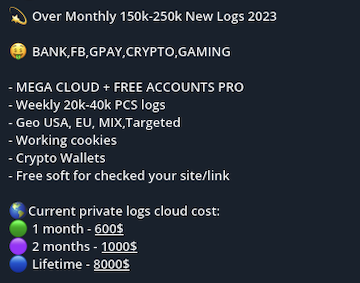
Stealer log advertisement on Telegram
Following the January 2025 arrest of CEO Pavel Durov, Telegram updated its privacy policy to allow the sharing of users’ IP addresses and phone numbers with law enforcement upon receiving valid legal orders. While some cybercriminals considered abandoning the platform in response, few viable alternatives exist at the same scale.
Niche apps like qTOX haven’t gained traction, and although Signal saw a slight uptick in use, it remains marginal. Discord and Session trail behind as the second and third most-used platforms, but Telegram continues to dominate as the preferred messaging app among threat actors, with its policy changes having little impact on overall usage.
Security teams can monitor Telegram to track stealer logs, malware sales, exploit chatter, and other emerging threats in real time—often before they appear on dark web forums—gaining earlier visibility into adversary behavior and intent.
What Is the Dark Web?
The dark web is a smaller, intentionally hidden part of the internet that requires special software (like the Tor browser or I2P) to access. It is designed to provide anonymity to both users and site operators.
Common Dark Web Sources
- Ransomware leak sites (e.g., LockBit, BlackCat)
- Marketplaces for stolen data, exploits, and malware
- Forums where threat actors discuss techniques, tools, and targets
- Carding shops and PII brokers
Why Monitor the Dark Web?
The dark web is the traditional place for threat actors to engage in cybercrime through selling stolen credentials, sharing guides for techniques, posting ransomware victims’ information, and more.
By monitoring the dark web, security teams can:
- Detect if your stolen credentials or internal data are being sold before threat actors abuse them
- Identify ransomware extortion events involving your infrastructure and mitigate risks instead of waiting for the third party vendor to detect it and notify your organization
- Track threat actor chatter and targeting activity to manage external threats before they’re acted upon
Key Differences: Deep Web vs. Dark Web Monitoring
To compare the differences between deep and dark web monitoring, we’ve put together this table below.
| Dark Web Monitoring | Deep Web Monitoring | |
| Access Method | Requires Tor/I2P and anonymizing tools | Login, invitation, or public platforms not indexed by search |
| Examples | Ransomware blogs, darknet forums, dark marketplaces | Telegram, Pastebin, GitHub, invite-only forums |
| Risk Type | Active criminal behavior, extortion, breach data | Early warning indicators, misconfigurations, accidental leaks |
| Monitoring Challenges | Hidden services, technical crawling constraints | Rapid content turnover, human validation required |
| Value | Detect active exploitation and monetization of your data | Identify early threats and mistakes before actors exploit them |
With an automated Threat Exposure Management solution, your security team can monitor both of these areas of the internet effectively.
Dark and Deep Web Monitoring for Effective Threat Exposure Management
Security teams often focus on dark web monitoring while overlooking equally critical deep web sources like GitHub or Telegram. However, threats can often originate in the deep web before escalating to the dark web.
Here are some possible scenarios:
- A developer posts a credential to GitHub → a bot scrapes it in minutes
- A Telegram user shares a cracked corporate tool → forum chatter follows
- A ransomware actor leaks data on a Tor site → extortion begins
By combining deep web coverage (GitHub, Telegram, etc) with dark web monitoring (ransomware leaks, dark web markets), your team can build a proactive, layered approach to Threat Exposure Management.
Dark and Deep Web Monitoring with Flare
The Flare Threat Exposure Management solution empowers organizations to proactively detect, prioritize, and mitigate the types of exposures commonly exploited by threat actors. Our platform automatically scans the clear & dark web and prominent threat actor communities 24/7 to discover unknown events, prioritize risks, and deliver actionable intelligence you can use instantly to improve security.
Flare integrates into your security program in 30 minutes and often replaces several SaaS and open source tools. See what external threats are exposed for your organization by signing up for our free trial.





