By Christopher Budd, Cybersecurity Evangelist
This post contains links to Flare Events. Flare has an archive of the dark web, continuously indexes more than 50,000 cybercrime Telegram channels, and has one of the largest cybercrime databases.
The December 9th, 2025 Microsoft Patch Tuesday was one of the two lightest releases of 2025. At 56 new CVEs, it ties with February 2025 for the fewest number of new Microsoft CVEs in a Patch Tuesday release.
We look at the December 2025 Patch Tuesday to highlight information of greatest importance for threat hunters and defenders focused on vulnerability management and attack prevention.
We examine the vulnerabilities that are most notable by the following criteria in the following decreasing order of priority based on information Microsoft provided at the time of release, December 9th, 2025:
- Those that are known by Microsoft to be exploited
- Those that are known by Microsoft to be publicly disclosed
- Those with a “Severity Rating” of “Critical”
- Those with an “Exploitability Assessment” of “More Likely”
I use these criteria as based on my experience with Patch Tuesday they are the markers for vulnerabilities that are most likely to be used in attacks against unpatched systems and of greatest interest and concern for defenders.
For each of the vulnerabilities that meet these criteria below, I provide some information on the technology and information about the threat environment around that vulnerability as of this writing.
The information in this posting is intended to help you understand and better prioritize vulnerabilities for remediation in your environment.
In Appendix A, you will find the complete listing of this month’s Microsoft bulletins with hyperlinks to information about the individual vulnerabilities on the MSRC website.
In Appendix B, you will find a complete listing of Flare resources for protecting your environment against attacks attempting to exploit these vulnerabilities.
Top-Level Findings
| Exploited | 1 |
| Publicly Disclosed | 2 |
| Severity Rating of “Critical” | 2 |
| Exploitability Assessment of “More Likely” | 6 |
CVE-2025-62221 – Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability
| Exploited | Yes |
| Publicly Disclosed | No |
| Severity Rating | Important |
| Exploitability Assessment | Detected |
CVE-2025-62454 – Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability
| Exploited | No |
| Publicly Disclosed | No |
| Severity Rating | Important |
| Exploitability Assessment | Likely |
CVE-2025-62221 is the most important vulnerability to track this month as Microsoft and the research community both agree it is being used in “zero day attacks,” meaning it’s been under attack before this patch was released. By indicating it’s not “Publicly Disclosed” Microsoft is indicating that this is being used in “limited and targeted attacks,” meaning it’s not being widely or openly used.
CVE-2025-62221 addresses a CWE-416: Use After Free vulnerability in the Windows Cloud Files Mini Filter Driver that results in an Elevation of Privilege (EoP). It’s one of three patches this month for this component. Microsoft is also providing patches for CVE-2025-62454 and CVE-2025-62457 (which is rated “Exploitation Unlikely” so isn’t discussed here but is included in the Appendixes).
The Windows Cloud Files Mini Filter Driver is poorly documented (actually not authoritatively documented by Microsoft at all) but secondary discussions online indicate that it’s the cldflt.sys file and “is primarily used for managing and facilitating the operations of cloud-stored files.” This makes this a client system component and thus most likely useful for attacks against users, like through malware or malicious sites.
This is the second Patch Tuesday in three months that this component has been patched and under attack and the fifth patch in the past twelve months.
Microsoft patched this component in October 2025 for another EoP, CVE-2025-55680, in that case for a CWE-367: Time-of-check Time-of-use (TOCTOU) Race Condition that was reportedly also under attack. Microsoft patched another vulnerability at that time in October, CVE-2025-55336, but this was only information disclosure.
In August 2025 Microsoft patched CVE-2025-50170 and in January 2025 CVE-2025-21271. Both were also EoPs but also tagged as “Exploitation Unlikely” and there have been no reports of attacks against these.
In case of all the EoP vulnerabilities discussed, a successful attack can give the attacker SYSTEM privileges, meaning they have the same level of control over the system as the Windows operating system itself. This makes these vulnerabilities attractive to attackers, especially for use in chained attacks.
This is borne out by a forum posting we found in Flare from January 2025 on IranHack linking to an exploit for another EoP vulnerability in this component, CVE-2024-49114 that was patched in December 2024, had been sighted. Further investigation by Flare researchers shows that this posting points to a PacketStorm download link of the Google Project Zero exploit.
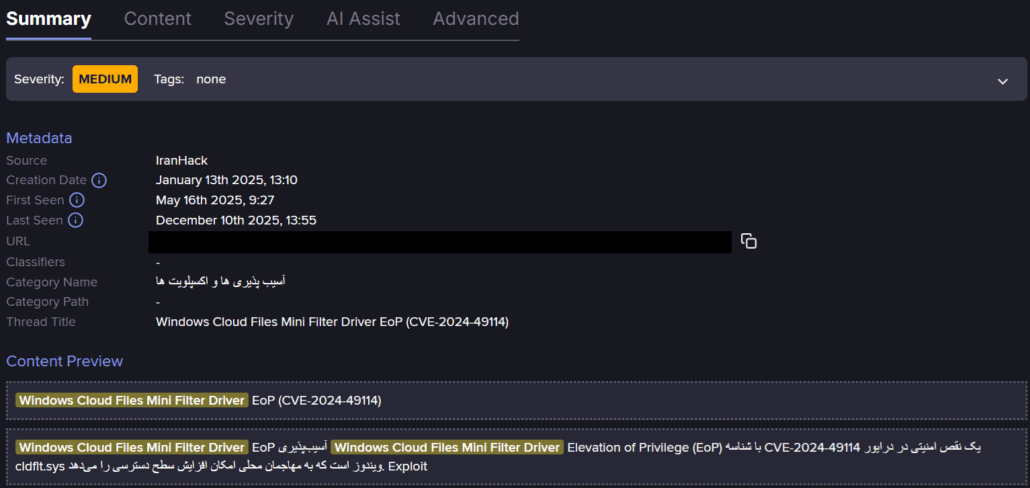
Forum posting about CVE-2024-49114 (Flare link to post, sign up for the free trial to access if you aren’t already a customer)
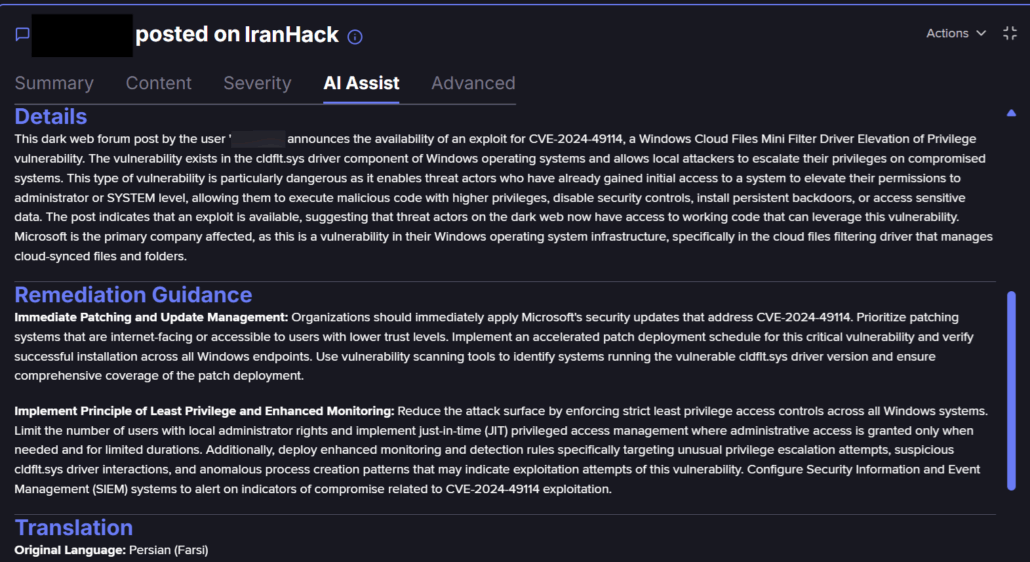
AI-based translation from Flare about CVE-2024-49114 (Flare link to post, sign up for the free trial to access if you aren’t already a customer)
This posting is particularly notable because CVE-2024-49114 at the time of release was also listed by Microsoft as not publicly disclosed or exploited but “Exploitation More Likely” just like this month’s CVE-2025-62454. Also the availability of this exploit is not widely known.
For that reason, while it’s obvious that CVE-2025-62221 makes sense to be a top priority for patching due to reports of it being under attack, it makes sense to also equally prioritize at least CVE-2025-62454. And if you’re going to touch this component anyway, it makes sense to apply CVE-2025-62457 as well for good security hygiene.
You can keep an eye on the threat environment around this component area generally by doing a search on “Windows Cloud Files Mini Filter Driver” within Flare.
CVE-2025-64671 – GitHub Copilot for Jetbrains Remote Code Execution Vulnerability
| Exploited | No |
| Publicly Disclosed | Yes |
| Exploitability Assessment | Exploitation Less Likely |
| Severity Rating | Important |
This vulnerability is notable not simply in its own right but because the “publicly disclosed” in this case is that it is one of many vulnerabilities affecting AI-assisted development tools that can result in information disclosure or remote code execution.This all comes about as a result of a research paper titled “IDEsaster: A Novel Vulnerability Class in AI IDEs” by Ari Marzuk who is credited by Microsoft for this vulnerability.
As Tom’s Hardware notes, the paper found vulnerabilities in “GitHub Copilot, Cursor, Windsurf, Kiro.dev, Zed.dev, Roo Code, Junie, Cline, Gemini CLI, and Claude Code, with at least twenty-four assigned CVEs and additional advisories from AWS.”
The component in question is a client system component: it provides a means to integrate GitHub Copilot into your Integrated Development Environment (IDE). This means once again the likely attack vectors are client-side attacks: malicious links, malware, and phishing emails. While Microsoft isn’t specific in its information, it’s reasonable to presume that code execution would be limited to the user’s privileges: limits on the user’s accounts would also limit attacks.
That said, while the attack vectors are classic client-side vectors, the vulnerability itself is quite interesting and worth reading about, if only to understand the emerging world of AI-focused attacks. And this paper is particularly notable because it outlines a novel attack vector in this already fast-moving world.
The paper provides more details, but the key point is that Marzuk’s research does what good security research does: focus on an element that has been overlooked due to assumptions. From his paper:
AI IDEs effectively ignored the base IDE software as part of the threat model, assuming it’s inherently safe because it existed for years. However, once you add AI agents that can act autonomously, the same legacy features can be weaponized into data exfiltration and RCE primitives. The base IDE’s features should be an integral component of the threat model.
The paper goes into much more detail and is worth reading. And it’s worth using it to reflect on how many “unknown unknowns” regarding AI tools and risks.
Coming back to the specifics of this vulnerability, as we discussed above, attacks can be chained with EoP vulnerabilities. And realistically, developers tend to run with full admin privileges on their system, so it would be reasonable to treat the impact of the vulnerability as a SYSTEM-level compromise.
In addition to getting the update for this specific product, if you use AI-assistants with your IDEs in your environment, it would be good to review the whitepaper and see if any other products are affected and need updating.
Fortunately, at the time of this writing, there are no known attacks against any of the IDEs called out as vulnerable. But this is clearly something that warrants prompt attention.
You can watch for activity around this issue broadly in Flare by searching on IDEsaster (if you’re not a customer, sign up for a free trial here). As of this writing there is little activity around this vulnerability or these issues.
CVE-2025-54100 – PowerShell Remote Code Execution Vulnerability
| Exploited | No |
| Publicly Disclosed | Yes |
| Exploitability Assessment | Exploitation Less Likely |
| Severity Rating | Important |
While Microsoft lists this as “Exploitation Less Likely” and rated as “Important,” information now available means that this ought to be treated as a “Critical” in most people’s environments.
One day after the release of the bulletin, a detailed write-up of the vulnerability with a sample proof of concept (PoC) was released by Osman Eren Güneş, one of the researchers credited by Microsoft for reporting the vulnerability.
As outlined in the write-up, this is another client-side vulnerability. The specific attack vector outlined in the write-up is a web-based attack vector, but any of the standard client-side attack vectors already outlined would seem to apply. Once again, limits on the user’s account should limit any attacks as well.
CVE-2025-62557 – Microsoft Office Remote Code Execution Vulnerability and CVE-2025-62554 – Microsoft Office Remote Code Execution Vulnerability
| Exploited | No |
| Publicly Disclosed | No |
| Exploitability Assessment | Exploitation Less Likely |
| Severity Rating | Critical |
CVE-2025-62554 and CVE-2025-62557 are also standard client-side vulnerabilities affecting Microsoft Office components. The attack vectors and the impact of these are the same as those outlined above: malicious links, malware, and phishing emails with successful attacks running in the security context of the logged-on user.
What’s most notable is that both of these are rated as “Critical” because they have a preview pane vector where an attacker could execute malicious code with no user interaction, just from a malicious email rendering in Outlook’s preview pane.
Important Severity Elevation of Privilege Vulnerabilities (EoPs) with Exploitation More Likely
| Exploited | No |
| Publicly Disclosed | No |
| Exploitability Assessment | Exploitation More Likely |
| Severity Rating | Important |
- CVE-2025-59517 – Windows Storage VSP Driver Elevation of Privilege Vulnerability
- CVE-2025-59516 – Windows Storage VSP Driver Elevation of Privilege Vulnerability
- CVE-2025-62472 – Windows Remote Access Connection Manager Elevation of Privilege Vulnerability
- CVE-2025-62470 – Windows Common Log File System Driver Elevation of Privilege Vulnerability
- CVE-2025-62458 – Win32k Elevation of Privilege Vulnerability
We’ve already outlined one of this month’s “Exploitation More Likely” vulnerabilities, one of the three Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerabilities. The five other “Exploitation More Likely” vulnerabilities have enough in common that they can be treated in bulk together.
All are local EoP vulnerabilities that can be attacked to elevate privileges to SYSTEM, once again enabling an attacker to take the same actions as the operating system.
As with most EoP vulnerabilities like these, they require some kind of code on the local system to attack them.
Two of the vulnerabilities (CVE-2025-62470 and CVE-2025-62458) are CWE-122: Heap-based Buffer Overflow vulnerabilities, one (CVE-2025-62472) is CWE-908: Use of Uninitialized Resource and CWE-416: Use After Free, one (CVE-2025-59516) is CWE-306: Missing Authentication for Critical Function and CWE-73: External Control of File Name or Path and one (CVE-2025-59517) is CWE-284: Improper Access Control.
As noted before regarding EoP vulnerabilities, these bear watching for their usefulness in being used as part of an attack chain with other vulnerabilities.
Appendix A: December 2025 Microsoft CVEs
Below is the complete list of CVEs released this month. This data is taken from the Microsoft Security Response Center (MSRC) Security Update Guide and contains all CVEs that were released on December 9, 2025. It does not contain any third-party or Chromium (Microsoft Edge) vulnerabilities.
The data below has been grouped and sorted as follows:
- All where Exploited = Yes
- All where Publicly Disclosed = Yes
- All where Severity = Critical
- All where Exploitation = More Likely, sorted by decreasing severity, sorted alphabetically by impact
- All where Exploitation = Less Likely, sorted by decreasing severity, sorted alphabetically by impact
- All where Exploitation = Unlikely, sorted by decreasing severity, sorted alphabetically by impact
- Any remaining items
| Release Date | CVE Number | CVE Title | Publicly Disclosed | Exploitability Assessment | Exploited | Impact | Max Severity |
| Exploited = Yes | |||||||
| Dec 9, 2025 | CVE-2025-62221 | Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability | No | Exploitation Detected | Yes | Elevation of Privilege | Important |
| Publicly Disclosed = Yes | |||||||
| Dec 9, 2025 | CVE-2025-64671 | GitHub Copilot for Jetbrains Remote Code Execution Vulnerability | Yes | Exploitation Less Likely | No | Remote Code Execution | Important |
| Dec 9, 2025 | CVE-2025-54100 | PowerShell Remote Code Execution Vulnerability | Yes | Exploitation Less Likely | No | Remote Code Execution | Important |
| Severity = Critical | |||||||
| Dec 9, 2025 | CVE-2025-62557 | Microsoft Office Remote Code Execution Vulnerability | No | Exploitation Less Likely | No | Remote Code Execution | Critical |
| Dec 9, 2025 | CVE-2025-62554 | Microsoft Office Remote Code Execution Vulnerability | No | Exploitation Less Likely | No | Remote Code Execution | Critical |
| Exploitation = More Likely | |||||||
| Dec 9, 2025 | CVE-2025-59517 | Windows Storage VSP Driver Elevation of Privilege Vulnerability | No | Exploitation More Likely | No | Elevation of Privilege | Important |
| Dec 9, 2025 | CVE-2025-59516 | Windows Storage VSP Driver Elevation of Privilege Vulnerability | No | Exploitation More Likely | No | Elevation of Privilege | Important |
| Dec 9, 2025 | CVE-2025-62472 | Windows Remote Access Connection Manager Elevation of Privilege Vulnerability | No | Exploitation More Likely | No | Elevation of Privilege | Important |
| Dec 9, 2025 | CVE-2025-62470 | Windows Common Log File System Driver Elevation of Privilege Vulnerability | No | Exploitation More Likely | No | Elevation of Privilege | Important |
| Dec 9, 2025 | CVE-2025-62458 | Win32k Elevation of Privilege Vulnerability | No | Exploitation More Likely | No | Elevation of Privilege | Important |
| Dec 9, 2025 | CVE-2025-62454 | Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability | No | Exploitation More Likely | No | Elevation of Privilege | Important |
| Exploitation = Less Likely | |||||||
| Dec 9, 2025 | CVE-2025-62465 | DirectX Graphics Kernel Denial of Service Vulnerability | No | Exploitation Less Likely | No | Denial of Service | Important |
| Dec 9, 2025 | CVE-2025-62463 | DirectX Graphics Kernel Denial of Service Vulnerability | No | Exploitation Less Likely | No | Denial of Service | Important |
| Dec 9, 2025 | CVE-2025-64680 | Windows DWM Core Library Elevation of Privilege Vulnerability | No | Exploitation Less Likely | No | Elevation of Privilege | Important |
| Dec 9, 2025 | CVE-2025-64679 | Windows DWM Core Library Elevation of Privilege Vulnerability | No | Exploitation Less Likely | No | Elevation of Privilege | Important |
| Dec 9, 2025 | CVE-2025-64661 | Windows Shell Elevation of Privilege Vulnerability | No | Exploitation Less Likely | No | Elevation of Privilege | Important |
| Dec 9, 2025 | CVE-2025-62565 | Windows File Explorer Elevation of Privilege Vulnerability | No | Exploitation Less Likely | No | Elevation of Privilege | Important |
| Dec 9, 2025 | CVE-2025-62569 | Microsoft Brokering File System Elevation of Privilege Vulnerability | No | Exploitation Less Likely | No | Elevation of Privilege | Important |
| Dec 9, 2025 | CVE-2025-62474 | Windows Remote Access Connection Manager Elevation of Privilege Vulnerability | No | Exploitation Less Likely | No | Elevation of Privilege | Important |
| Dec 9, 2025 | CVE-2025-62467 | Windows Projected File System Elevation of Privilege Vulnerability | No | Exploitation Less Likely | No | Elevation of Privilege | Important |
| Dec 9, 2025 | CVE-2025-62464 | Windows Projected File System Elevation of Privilege Vulnerability | No | Exploitation Less Likely | No | Elevation of Privilege | Important |
| Dec 9, 2025 | CVE-2025-62461 | Windows Projected File System Elevation of Privilege Vulnerability | No | Exploitation Less Likely | No | Elevation of Privilege | Important |
| Dec 9, 2025 | CVE-2025-62455 | Microsoft Message Queuing (MSMQ) Elevation of Privilege Vulnerability | No | Exploitation Less Likely | No | Elevation of Privilege | Important |
| Dec 9, 2025 | CVE-2025-64673 | Windows Storage VSP Driver Elevation of Privilege Vulnerability | No | Exploitation Less Likely | No | Elevation of Privilege | Important |
| Dec 9, 2025 | CVE-2025-64666 | Microsoft Exchange Server Elevation of Privilege Vulnerability | No | Exploitation Less Likely | No | Elevation of Privilege | Important |
| Dec 9, 2025 | CVE-2025-64658 | Windows File Explorer Elevation of Privilege Vulnerability | No | Exploitation Less Likely | No | Elevation of Privilege | Important |
| Dec 9, 2025 | CVE-2025-62573 | DirectX Graphics Kernel Elevation of Privilege Vulnerability | No | Exploitation Less Likely | No | Elevation of Privilege | Important |
| Dec 9, 2025 | CVE-2025-62572 | Application Information Service Elevation of Privilege Vulnerability | No | Exploitation Less Likely | No | Elevation of Privilege | Important |
| Dec 9, 2025 | CVE-2025-62571 | Windows Installer Elevation of Privilege Vulnerability | No | Exploitation Less Likely | No | Elevation of Privilege | Important |
| Dec 9, 2025 | CVE-2025-62466 | Windows Client-Side Caching Elevation of Privilege Vulnerability | No | Exploitation Less Likely | No | Elevation of Privilege | Important |
| Dec 9, 2025 | CVE-2025-62570 | Windows Camera Frame Server Monitor Information Disclosure Vulnerability | No | Exploitation Less Likely | No | Information Disclosure | Important |
| Dec 9, 2025 | CVE-2025-64670 | Windows DirectX Information Disclosure Vulnerability | No | Exploitation Less Likely | No | Information Disclosure | Important |
| Dec 9, 2025 | CVE-2025-62473 | Windows Routing and Remote Access Service (RRAS) Information Disclosure Vulnerability | No | Exploitation Less Likely | No | Information Disclosure | Important |
| Dec 9, 2025 | CVE-2025-64678 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability | No | Exploitation Less Likely | No | Remote Code Execution | Important |
| Dec 9, 2025 | CVE-2025-62559 | Microsoft Word Remote Code Execution Vulnerability | No | Exploitation Less Likely | No | Remote Code Execution | Important |
| Dec 9, 2025 | CVE-2025-62558 | Microsoft Word Remote Code Execution Vulnerability | No | Exploitation Less Likely | No | Remote Code Execution | Important |
| Dec 9, 2025 | CVE-2025-62556 | Microsoft Excel Remote Code Execution Vulnerability | No | Exploitation Less Likely | No | Remote Code Execution | Important |
| Dec 9, 2025 | CVE-2025-62555 | Microsoft Word Remote Code Execution Vulnerability | No | Exploitation Less Likely | No | Remote Code Execution | Important |
| Dec 9, 2025 | CVE-2025-62553 | Microsoft Excel Remote Code Execution Vulnerability | No | Exploitation Less Likely | No | Remote Code Execution | Important |
| Dec 9, 2025 | CVE-2025-62550 | Azure Monitor Agent Remote Code Execution Vulnerability | No | Exploitation Less Likely | No | Remote Code Execution | Important |
| Dec 9, 2025 | CVE-2025-62564 | Microsoft Excel Remote Code Execution Vulnerability | No | Exploitation Less Likely | No | Remote Code Execution | Important |
| Dec 9, 2025 | CVE-2025-62563 | Microsoft Excel Remote Code Execution Vulnerability | No | Exploitation Less Likely | No | Remote Code Execution | Important |
| Dec 9, 2025 | CVE-2025-62561 | Microsoft Excel Remote Code Execution Vulnerability | No | Exploitation Less Likely | No | Remote Code Execution | Important |
| Dec 9, 2025 | CVE-2025-62549 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability | No | Exploitation Less Likely | No | Remote Code Execution | Important |
| Dec 9, 2025 | CVE-2025-64672 | Microsoft SharePoint Server Spoofing Vulnerability | No | Exploitation Less Likely | No | Spoofing | Important |
| Exploitation = Unlikely | |||||||
| Dec 9, 2025 | CVE-2025-62567 | Windows Hyper-V Denial of Service Vulnerability | No | Exploitation Unlikely | No | Denial of Service | Important |
| Dec 9, 2025 | CVE-2025-55233 | Windows Projected File System Elevation of Privilege Vulnerability | No | Exploitation Unlikely | No | Elevation of Privilege | Important |
| Dec 9, 2025 | CVE-2025-62462 | Windows Projected File System Elevation of Privilege Vulnerability | No | Exploitation Unlikely | No | Elevation of Privilege | Important |
| Dec 9, 2025 | CVE-2025-62469 | Microsoft Brokering File System Elevation of Privilege Vulnerability | No | Exploitation Unlikely | No | Elevation of Privilege | Important |
| Dec 9, 2025 | CVE-2025-62457 | Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability | No | Exploitation Unlikely | No | Elevation of Privilege | Important |
| Dec 9, 2025 | CVE-2025-62468 | Windows Defender Firewall Service Information Disclosure Vulnerability | No | Exploitation Unlikely | No | Information Disclosure | Important |
| Dec 9, 2025 | CVE-2025-62560 | Microsoft Excel Remote Code Execution Vulnerability | No | Exploitation Unlikely | No | Remote Code Execution | Important |
| Dec 9, 2025 | CVE-2025-62552 | Microsoft Access Remote Code Execution Vulnerability | No | Exploitation Unlikely | No | Remote Code Execution | Important |
| Dec 9, 2025 | CVE-2025-62562 | Microsoft Outlook Remote Code Execution Vulnerability | No | Exploitation Unlikely | No | Remote Code Execution | Important |
| Dec 9, 2025 | CVE-2025-62456 | Windows Resilient File System (ReFS) Remote Code Execution Vulnerability | No | Exploitation Unlikely | No | Remote Code Execution | Important |
| Dec 9, 2025 | CVE-2025-64667 | Microsoft Exchange Server Spoofing Vulnerability | No | Exploitation Unlikely | No | Spoofing | Important |
Monitor for Emerging Threats with Flare
Flare helps security practitioners stay ahead of newly disclosed CVEs by continuously monitoring the clear and dark web and threat actor communities for early signals of exploitation. Flare’s collection includes more than 50,000 cybercrime Telegram channels, hundreds of cybercrime forums, ransomware leak sites, and dark web marketplaces, in addition to one of the most comprehensive sets of breached identity data in the industry.
See what external threats are exposed for your organization by signing up for our free trial.





