
We all know we should have backups. It’s not a task we particularly love doing, and it is definitely something that we forget to do unless automated. How many people religiously plugged in their iPhone in their computer to back it up a few years ago, when backups were not sent automatically to the cloud every day?
Of course, all backup strategies are not equal, and some, such as the 3-2-1 backup strategy, have proven their worth over time. As a refresher, this strategy suggests to have:
- 3 copies of your backups, so that at least one should be working when disaster hits
- 2 types of backups, so that you are not dependent on a single file format that may not be easily readable in a few years
- 1 remote site backup, so that your data is safe in the event of a disaster such as a fire destroying your offices and your computers with their data
Where to Store Backups
The 3-2-1 strategy is effective to protect against data loss, but doesn’t answer an essential question: where should you store your backups, whether they are on your network, or at a remote site? This is a complex question for two reasons.
First, backups are big, and often even huge. Making backups of customer information when there are millions of them is likely to take time, and to require large disk space. This means that the backups cannot conveniently be stored everywhere, and that a specific type of hardware must be purchased to store this information.
Second, backups include everything. They include trade secrets, intellectual property, customer information, employees’ social security numbers, and even private communications by your executives. Backups therefore include some of the most sensitive information your company possesses, and makes the question who has access to backups all the more important.
Backups as a Backdoor
Law enforcement have acknowledged this fact for quite some time now, and have been known to search for backups when building evidence, rather than the data itself. Backups were for example at the centre of a national case around a terrorist in California in the mid 2010s. Law enforcement needed to access a locked iPhone, but could not unlock it since the phone’s owner was dead. Apple did provide law enforcement with a backup of the phone that contained all of its content, thereby bypassing the need to unlock the phone. To this day, there are reports that Apple backups are not encrypted only by a user’s password, and that law enforcement can therefore access those backups.
Now, if that is true for legitimate investigations, it is also true for malicious actors. Our database includes references to malicious actors targeting backups since at least 2012.
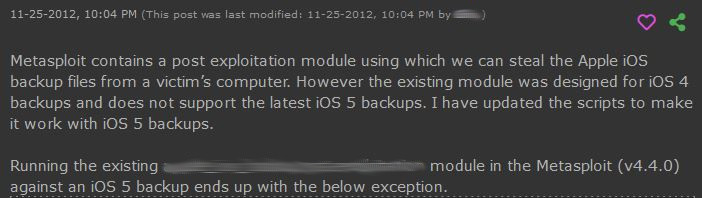
Newer indications also suggest that backups are still very much a target of malicious actors.
Unintended Backup Leaks
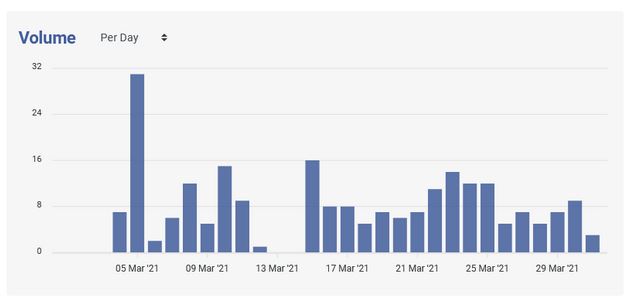
In addition to targeted attacks, backups are also exposed because of unintended leaks on misconfigured public repositories. Over the last month alone, our systems have detected on a single source code repository dozens of examples of database dumps every single day using a single database name in a query. Our systems however collect many times this using other keywords associated with database dumps, every single day once again.
Of course, many of those dumps will not contain sensitive corporate information. But enough do to cause many concerns to organizations like yours. In the example below, George is a customer of a company, and as evidenced on the right of the image, his password is kept encrypted in the database. Malicious actors have however developed sophisticated attacks against encryption. And if George’s password proves too difficult to crack, there are thousands more in this dump that could be decrypted, and taken advantage of.
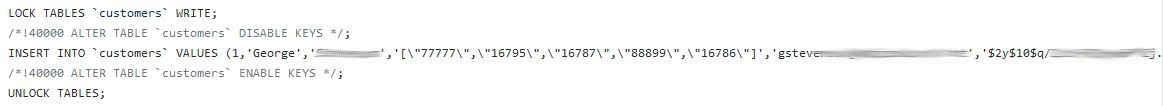
Working Towards a Solution
On this International World Backup Day, it is important to recognize the risks that backups pose to your organization. Backups need to be treated as the most sensitive information that your organization possesses, and this means carefully building a backup strategy with clear rights management.
Any information that you would not put up on the internet publicly should not be included in a backup stored in an online bucket, for example. All backup strategies should also be evaluated by trained security professionals who can identify flaws and vulnerabilities, and suggest how to properly store the backups, especially when they are stored on a remote site.
When all else fails, it is important to monitor your digital footprint to ensure rapid detection of leaked backups. Our systems provide up to the minute scanning of source code repositories and other code sharing platforms to ensure that any mention of your company, by malicious actors or in accidentally leaked backups, are known to you instantly, and that the appropriate measures are taken to take down the public backups.





