Flare Research conducted some threat hunting activity based on cybercrime intelligence to search for live phishing infrastructure. We explored how threat actors’ advertisements for phishing capabilities translate into real, operational attack infrastructure.
This research is part of our “True vs. Fake: The Phishing Kits Economy in Underground Markets” report, which analyzes the cybercrime economy and will be published early in 2026. This blog explores the gap between what threat actors sell on forums and what actually gets deployed against victims.
By pivoting from Russian-language threat actor posts advertising Browser-in-the-Middle (BitM) and MFA-bypass capabilities, we traced those claims into the wild. We uncovered live, cloud-native phishing operations targeting Gmail, Facebook, and Microsoft O365 at scale.
Key Takeaways
- Modern phishing kits defeat web authentication, not just users: Today’s phishing kits directly target authentication flows using Browser-in-the-Browser (BitB), Adversary-in-the-Middle (AiTM), and reverse-proxy techniques, allowing attackers to bypass MFA, intercept live sessions, and operate inside legitimate login processes rather than spoofing them.
- Session theft has replaced password harvesting: These platforms no longer rely on static credentials alone. They support real-time session cookie theft, MFA relay, SMS-based OTP interception, and fake SSO/OAuth flows, enabling immediate account takeover even when strong authentication is enabled.
- Capabilities are marketed, not kits: Threat actors advertise outcomes (“MFA bypass,” “live validation,” “proxy login”) rather than specific tool names. This reflects a mature ecosystem where tooling is white-labeled, repackaged, and continuously evolving.
- Phishing infrastructure is now cloud-native and Kubernetes-backed: Attackers are deploying phishing environments using modern cloud-native practices, including containerized services and Kubernetes clusters, enabling rapid provisioning, high availability, and infrastructure reuse.
- Massive scale-up is built in by design: Kubernetes-based deployment allows operators to scale from dozens to hundreds or thousands of phishing endpoints within seconds, rotate IPs automatically, and absorb takedowns with minimal operational impact.
- Phishing-as-a-Service (PhaaS) dramatically lowers the barrier to entry: Commercialized phishing platforms remove technical complexity entirely, allowing non-technical actors to launch advanced AiTM campaigns against any SaaS platform with minimal effort and cost.
- The phishing server is now the most hidden link in the kill chain: Instead of hiding emails or domains, attackers increasingly focus on concealing the phishing backend itself using blank pages, delayed rendering, anti-debugging logic, and infrastructure-level evasion.
- Cybercrime intelligence is predictive, not retrospective: Monitoring underground markets offers early visibility into what will be deployed next, often before campaigns are detected by email security tools or reported by victims.
From Cybercrime Advertising to Live Campaigns
During this analysis, we identified an intriguing lead on the Russian-language cybercrime forum Exploit, where a threat actor advertised phishing capabilities through short tutorial videos and marketing posts. Rather than focusing on brand names of kits, the actor emphasized capabilities such as:
- MFA bypass
- live credential validation
- browser-based interception
We used this cybercrime intelligence as a pivot point to search for live infrastructure. While it is difficult to conclusively attribute every discovered asset to this single seller, the behavior, tooling, and architectural patterns we observed in the wild show a striking resemblance to what was advertised.
Underground Leads: Browser-in-the-Middle for Sale
Two related posts stood out during the underground analysis:
- A sales post advertising Gmail phishing capabilities
- A second post promoting a Browser-in-the-Middle (BitM) solution, including tutorial videos
These posts referenced a phishing approach consistent with reverse-proxy interception, commonly described underground as “MFA bypass,” “live validation,” or “proxy login,” rather than naming kits like EvilProxy or Tycoon 2FA directly.
This distinction matters. In cybercrime markets, techniques often outlive brand names, and actors frequently repackage or white-label tooling. Tracking keywords such as BitM, reverse proxy, session hijack, or AiTM often reveals emerging phishing capabilities before they are widely reported.

Post in Exploit forum about a phishing kit BitM (Flare link to post, sign up for free trial to access if you aren’t already a customer)
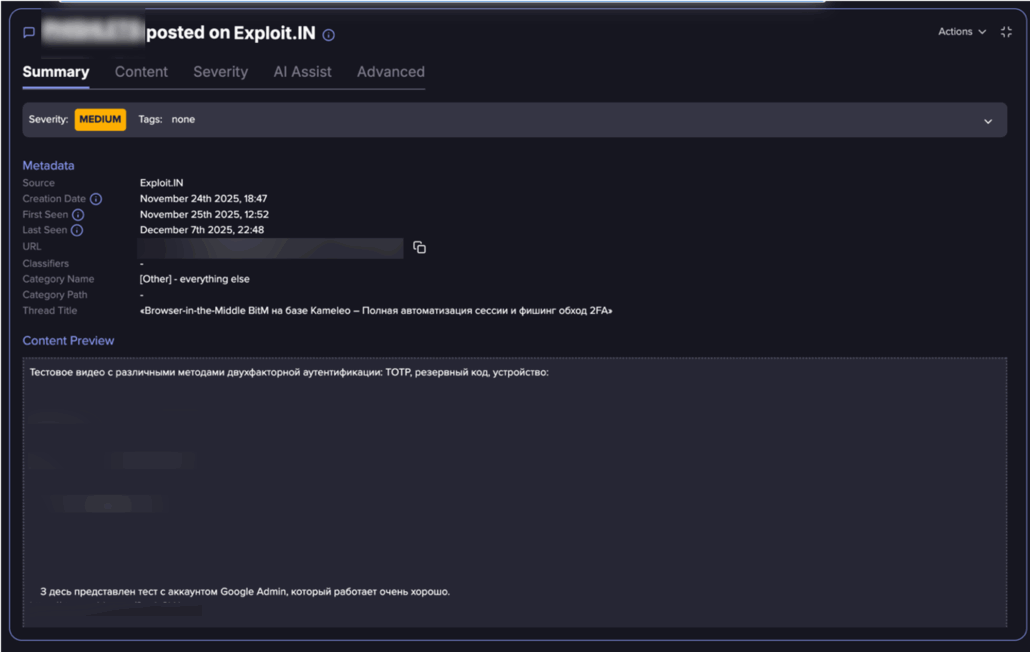
Threat actor post about targeting Google products with BitM (Flare link to post, sign up for free trial to access if you aren’t already a customer)
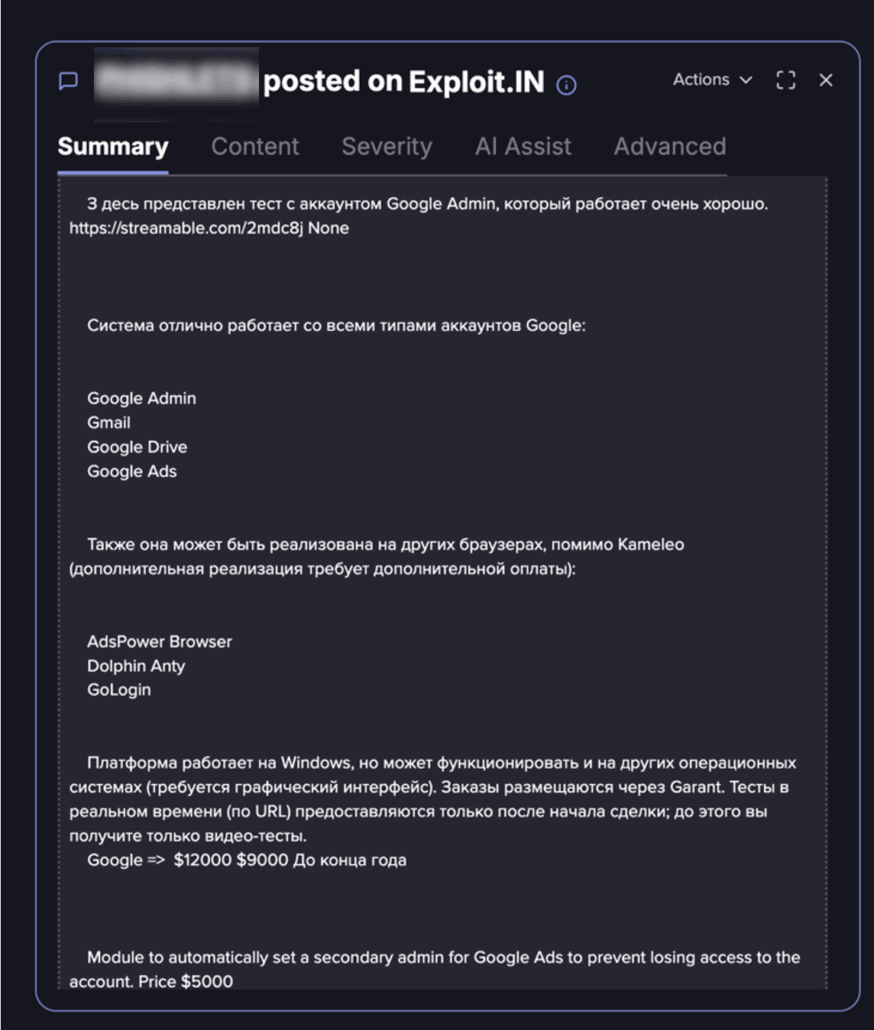
Threat actor post about targeting Google products with BitM, continued from the image above (Flare link to post, sign up for free trial to access if you aren’t already a customer)
This threat actor is selling a BitM with similar capabilities and a tutorial video to what we’ve seen in the wild.
Below you can see further analysis of phishing kits and services in the cybercrime economy.
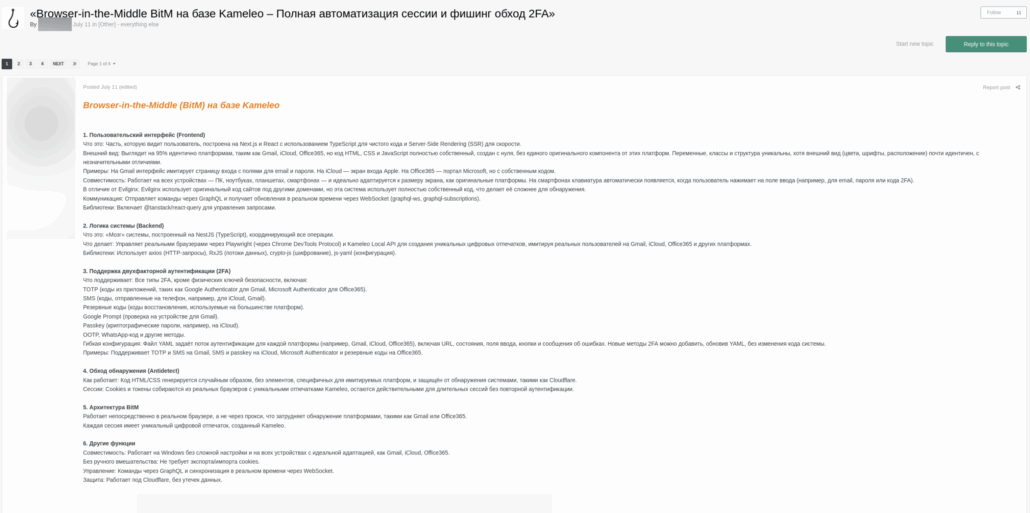
The threat actor’s original post in Exploit
Below you can see the translated message:
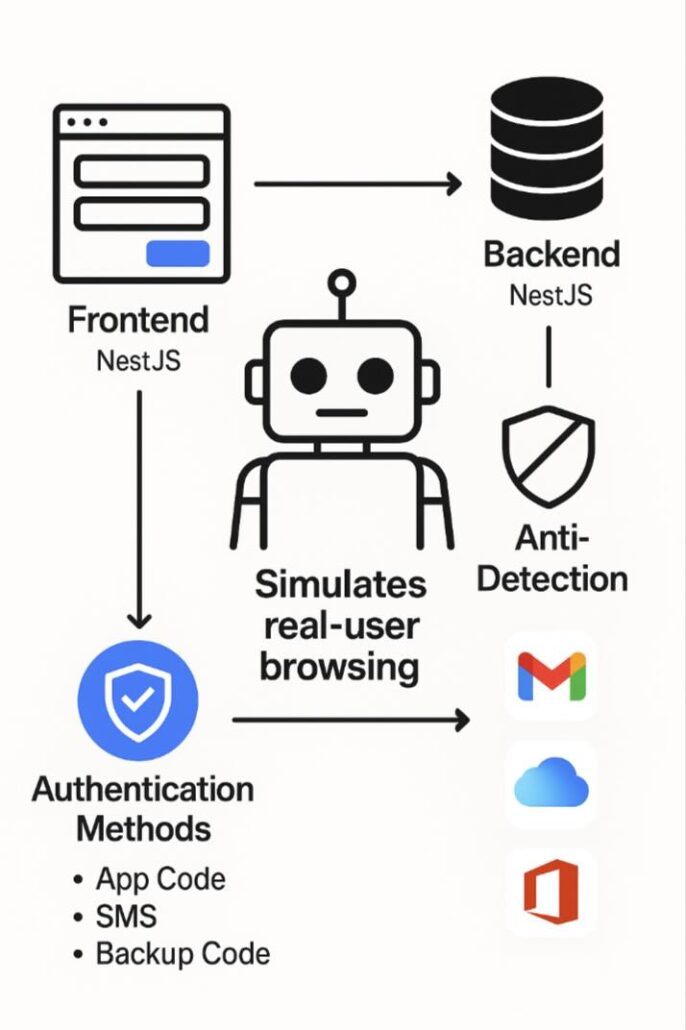
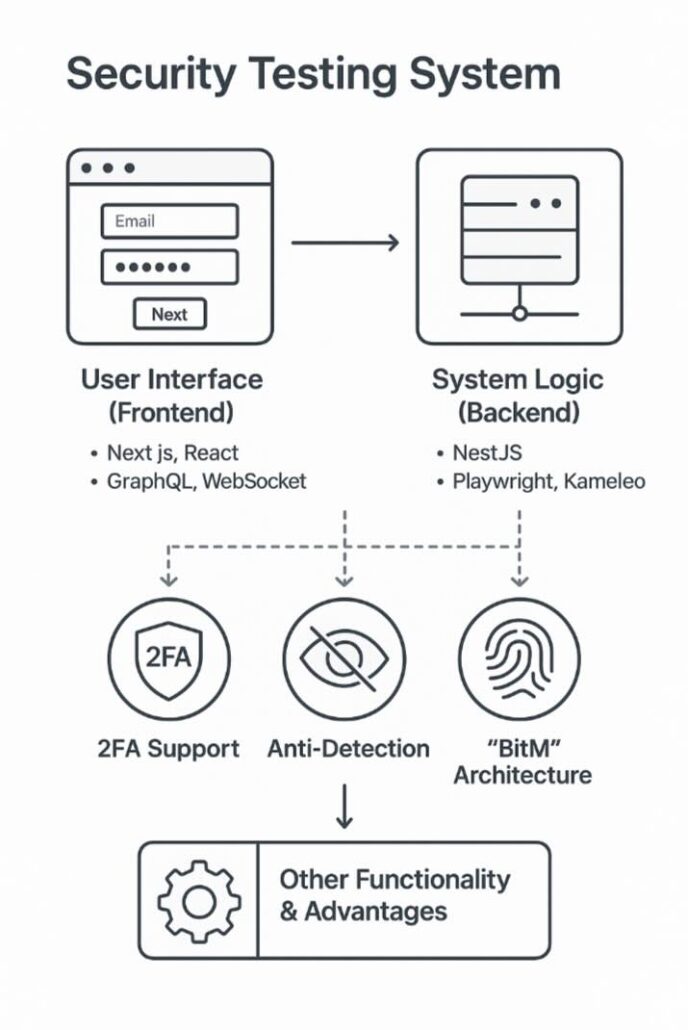
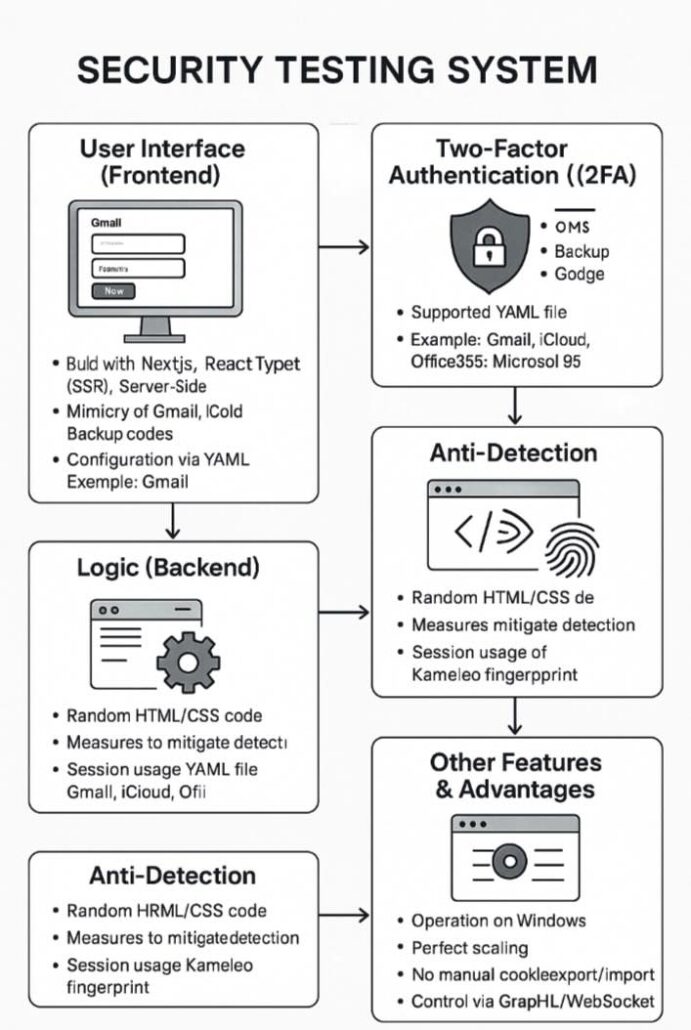
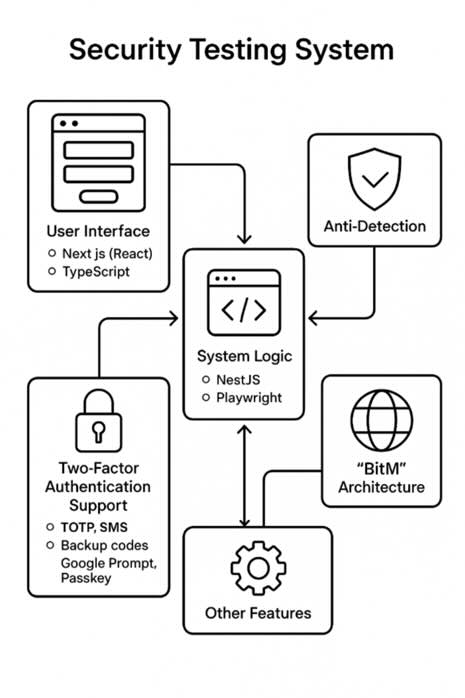
1. User Interface (Frontend)
What it is: The user-facing portion is built on Next.js and React, using TypeScript for clean code and Server-Side Rendering (SSR) for speed.
Appearance: It looks very similar to legitimate sites (like Gmail, iCloud, and Office365), but small differences exist. Buttons, logos, and structure are unique, although the appearance (icons, fonts, layout) is almost identical, with minor differences.
Examples: On Gmail, the interface mimics a login page with email and password fields. On iCloud, it may replicate the screen. On Office365, it mimics Outlooks UI, with its own code.
Compatibility: Works on all devices (PCs, laptops, tablets, and smartphones) and adapts perfectly to screen size.
Dynamic Behavior: When a user inputs data (e.g., email, password, or 2FA code), the frontend automatically captures these inputs and forwards them to the backend, making it near real-time.UI Libraries: Custom components and design logic (not standard browser UI). No iframes. Full website replication.
2. System Logic (Backend)
What it is: The “brain” of the system built on Node.js (TypeScript), coordinating all processes.
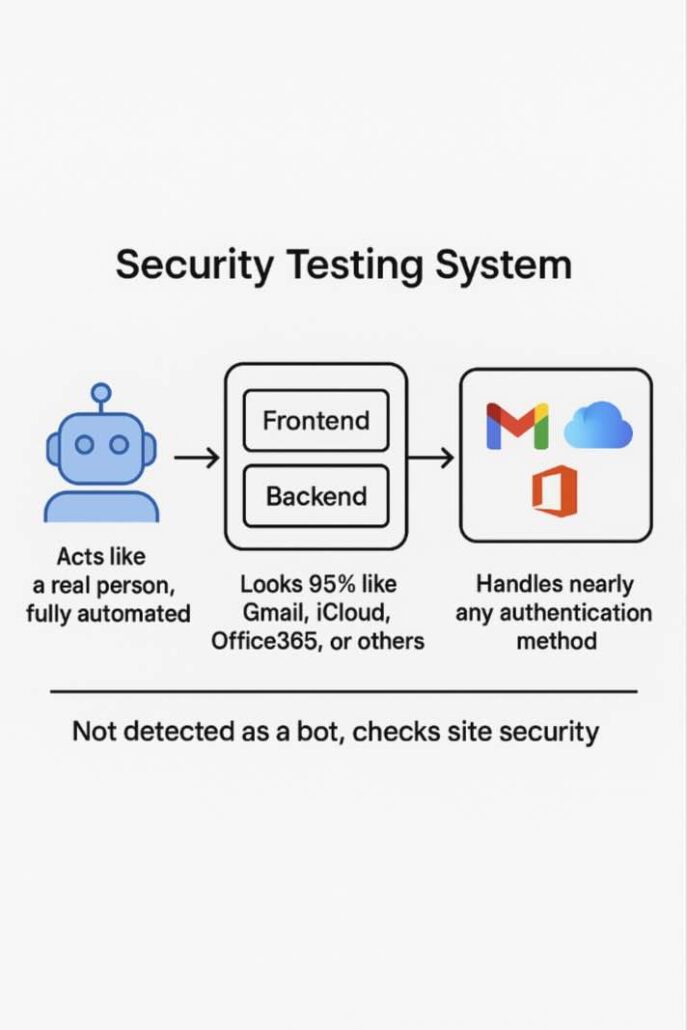
What it does: Acts as a Browser-in-the-Middle, via the Chrome DevTools Protocol, and the Kameleo Local API to create unique digital fingerprints, simulating real users on Gmail, iCloud, Office365, and other platforms.
Libraries Used: Playwright / Puppeteer, TLS fingerprinting, HTTP/2 manipulation, proxy configuration.
3. Support for Two-Factor Authentication (2FA)
What it supports: All types of 2FA, especially those used by major platforms.
Supported 2FA methods:
- TOTP (codes from apps like Google Authenticator, Microsoft Authenticator for Office365)
- SMS codes sent to the users phone (Gmail, iCloud)
- Push notifications (where applicable)
- Backup codes
Flexible Behavior: The system dynamically adapts to the authentication flow of each platform (e.g., Gmail, iCloud, Office365), including redirect URLs, input fields, buttons, and error messages. New 2FA methods can be added by updating logic without changing the entire system code.
4. Bypass Detection (Anti-Detection)
How it works:
- HTTP requests look like randomly generated, legitimate browser sessions
- Uses real Chrome fingerprints
- Protected from detection systems by services like Cloudflare
- Cookies and tokens are collected from real browsers using Kameleo fingerprints and remain valid for long sessions without re-authentication
5. Session Architecture
- Each victim has a unique browser session, not shared via proxy reuse
- Sessions are created using unique fingerprints
- Makes detection by Gmail or Office365 extremely difficult
6. Other Functions
Compatibility: Works on Windows without complex configuration and on all devices with perfect adaptation (same as Gmail, iCloud, Office365).
No manual interaction: No need to manually perform actions – everything is automated.
Command-and-Control: Controlled remotely via script, with real-time synchronization via WebSocket.Security: Powered by Cloudflare, no data leaks.
The threat actor’s original post in Exploit (continued)
The threat actor’s original post in Exploit (continued)
BitB vs. AiTM: A Brief Primer
Browser-in-the-Browser (BitB) and Adversary-in-the-Middle (AiTM) are closely related phishing techniques designed to bypass modern authentication controls.
- BitB creates a fake browser window rendered inside the victim’s browser. These pop-ups mimic legitimate OAuth or SSO dialogs with near-perfect fidelity, making them extremely difficult to distinguish from real login windows.
- AiTM goes further by placing a reverse proxy between the victim and the real service. Instead of stealing static passwords, the attacker intercepts live session cookies, MFA tokens, and authentication flows, enabling immediate account takeover.
Attackers often blur these terms, but both approaches point to real-time interception, not static credential harvesting.
Pivoting from Underground to Live Phishing Infrastructure
Using unique markers derived from the cybercrime posts, we conducted large-scale searches across internet-wide scanners (including Shodan and Censys), combined with targeted Google dorking.
Most results were noise:
- dormant servers
- unrelated test environments
- low-quality phishing pages
However, several clusters stood out, each exhibiting consistent infrastructure patterns and authentication-aware behavior.
Rather than discovering phishing emails or malicious links first, we identified the phishing servers themselves, which is a critical but often hidden component of the attack chain.
Live Gmail Phishing Infrastructure
Our first high-confidence cluster targeted Google Gmail users. We identified multiple IP addresses across hosting providers such as Hetzner, Ultahost, Proton66, and AlexHost. Despite hosting diversity, the infrastructure exhibited near-identical behavior:
- SSL-less Gmail-themed login pages
- Built using React / Next.js
- No cookies set during page load
- Identical JavaScript bundles and page structure
Below you can see what the phishing website looks like. This UI is similar across all the IP addresses we discovered.
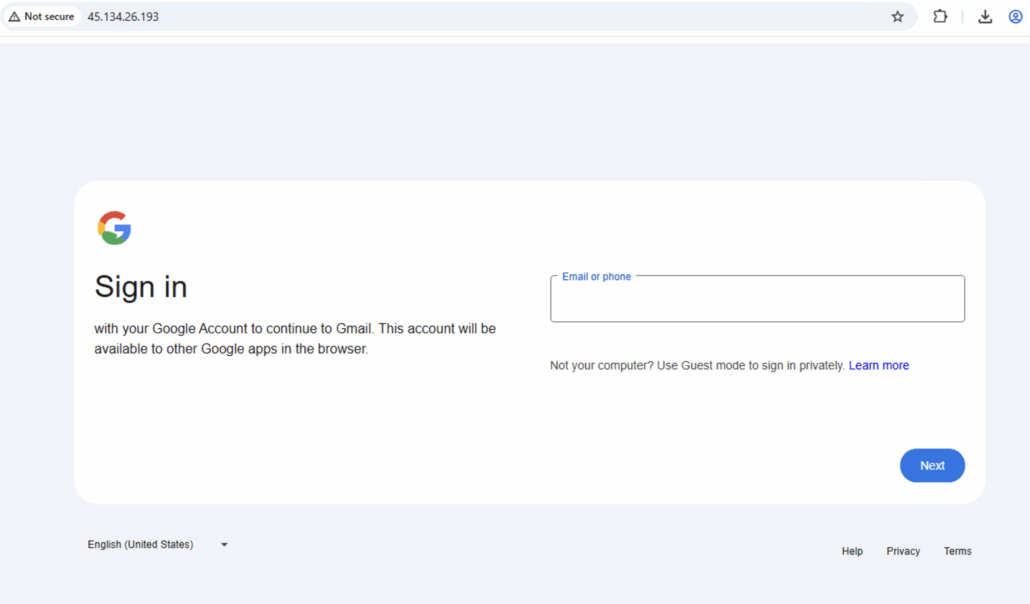
Fake Gmail login page
When inspecting the website’s components and characteristics, there are no cookies created. The structure of these IP addresses is similar across all the IPs.
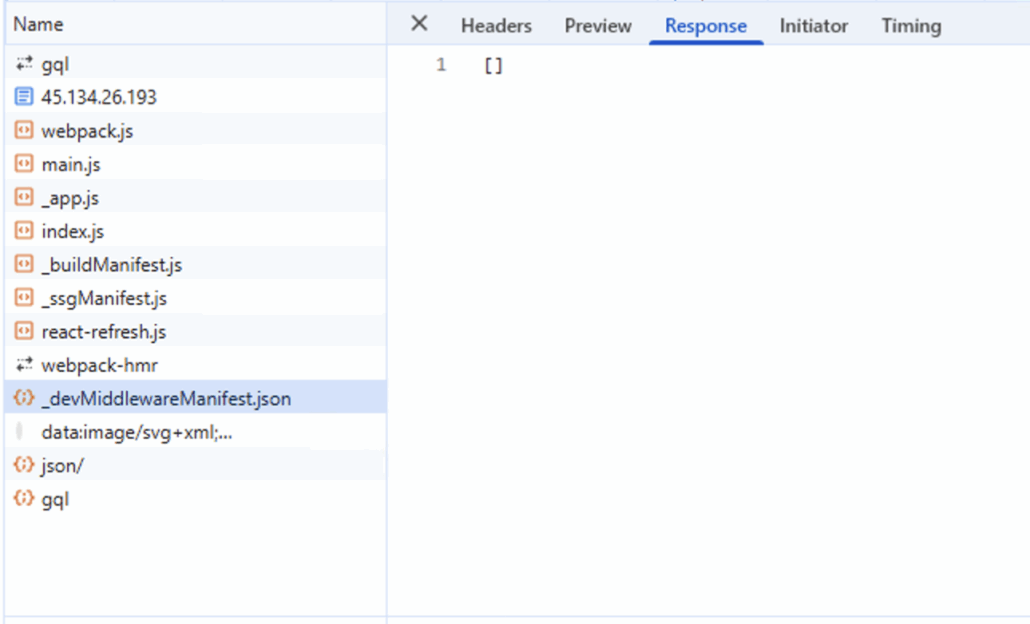
Several suspicious API calls pass the credentials in real time and test them against Gmail
When inserting a random fake email to the form, an API request is made to http://IP/gql.
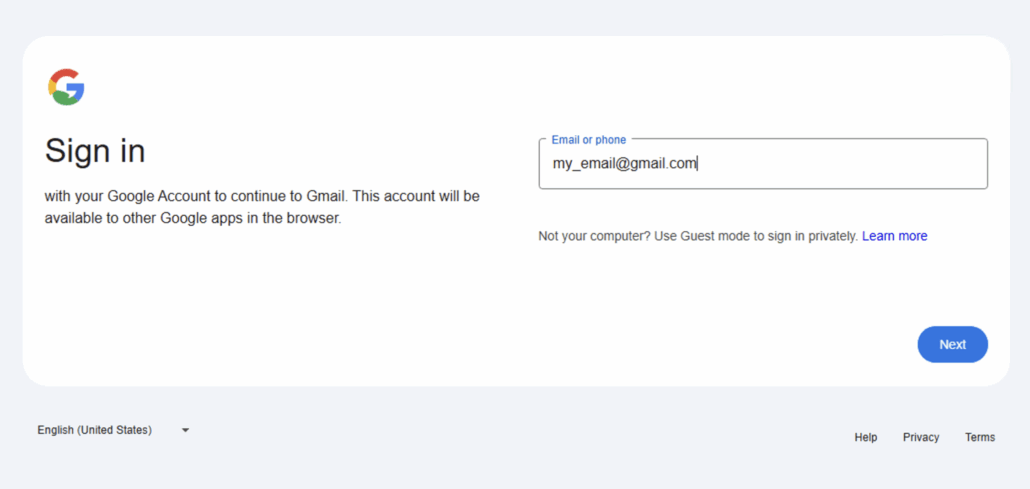
Trying a fake email
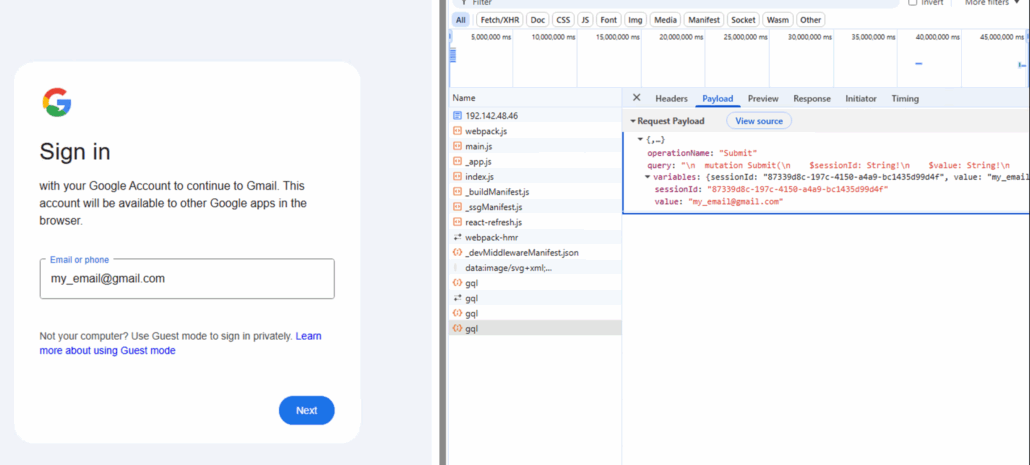
The gql api payload included the email
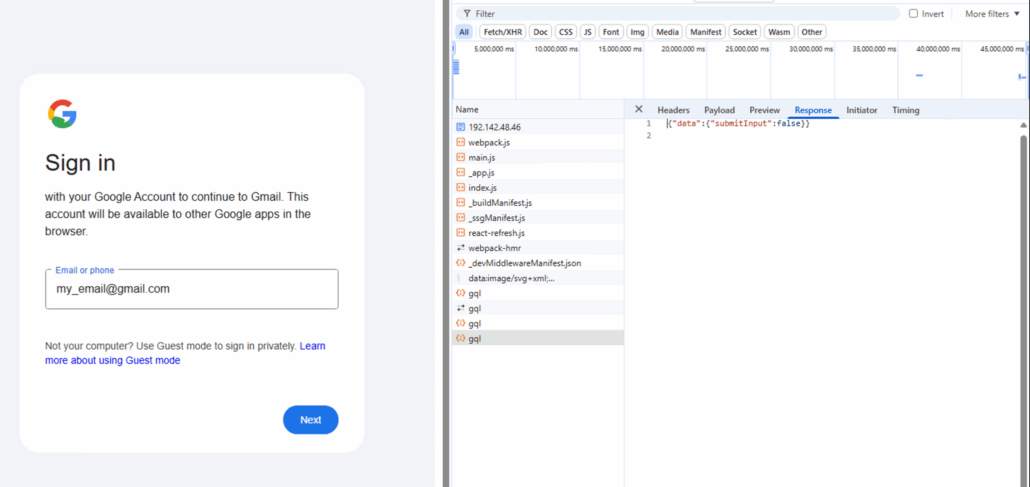
The gql api returns a false result saying the email doesn’t exist
If the email doesn’t exist in the Gmail database, it will return a failure. Thus, this phishing kit is testing the data live against Gmail.
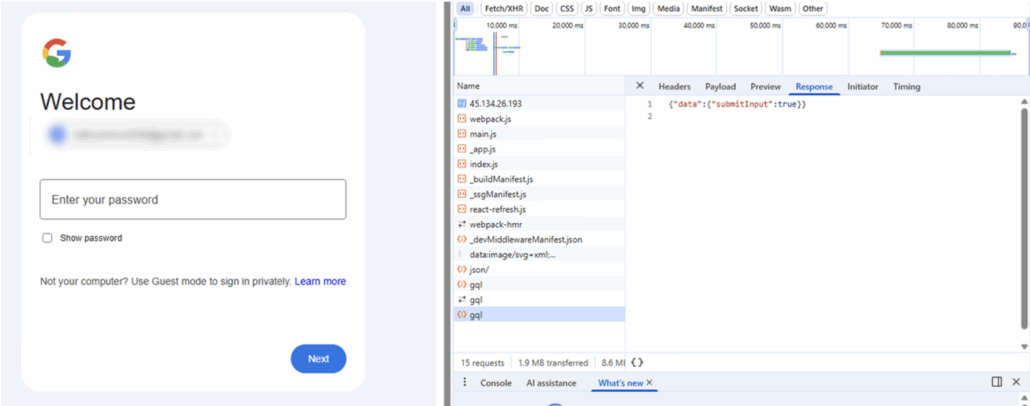
Request with real user data returns true and leads to the password form
When inserting a valid Gmail it will result in success and ask for the password.
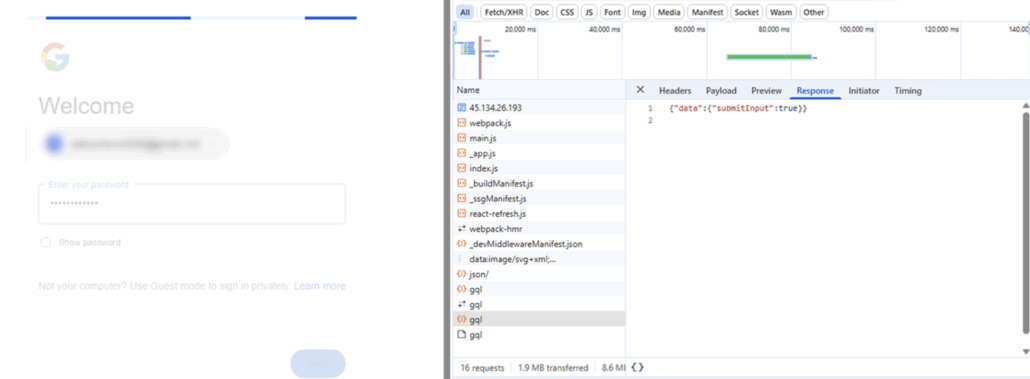
This GraphQL endpoint validates the address live against Gmail:
- Non-existent accounts fail immediately
- Valid Gmail addresses proceed to password capture
After password submission, victims are silently redirected back to the legitimate Gmail login page, creating the illusion of a failed or expired session.
Analysis of the collected assets revealed a modern phishing application:
- Most JavaScript bundles are benign framework components
- The malicious logic resides in the login flow
A GraphQL-over-WebSocket backend enables real-time data exfiltration
This architecture allows attackers to:
- Receive credentials instantly
- Track victims live
- Potentially automate follow-up actions
The missing server-side GraphQL schema prevents full visibility into backend operations, but the intent and capability are clear.
Live Facebook Phishing Infrastructure (Now Taken Down)
In parallel, we uncovered a second cluster targeting Facebook users, consisting of approximately 60 IP addresses.
Observed Behavior
- Phishing pages loaded a login-check.html component
- Credentials were validated live against Facebook
- Victim IP geolocation data was collected during authentication
- MFA challenges were relayed in real time
- Victims were redirected to the legitimate Facebook website after submission
- Infrastructure is hosted on DigitalOcean, LLC servers
Some pages enforced time-boxed MFA windows, giving users a limited period to complete authentication, which is an indicator of active session interception rather than static credential harvesting.
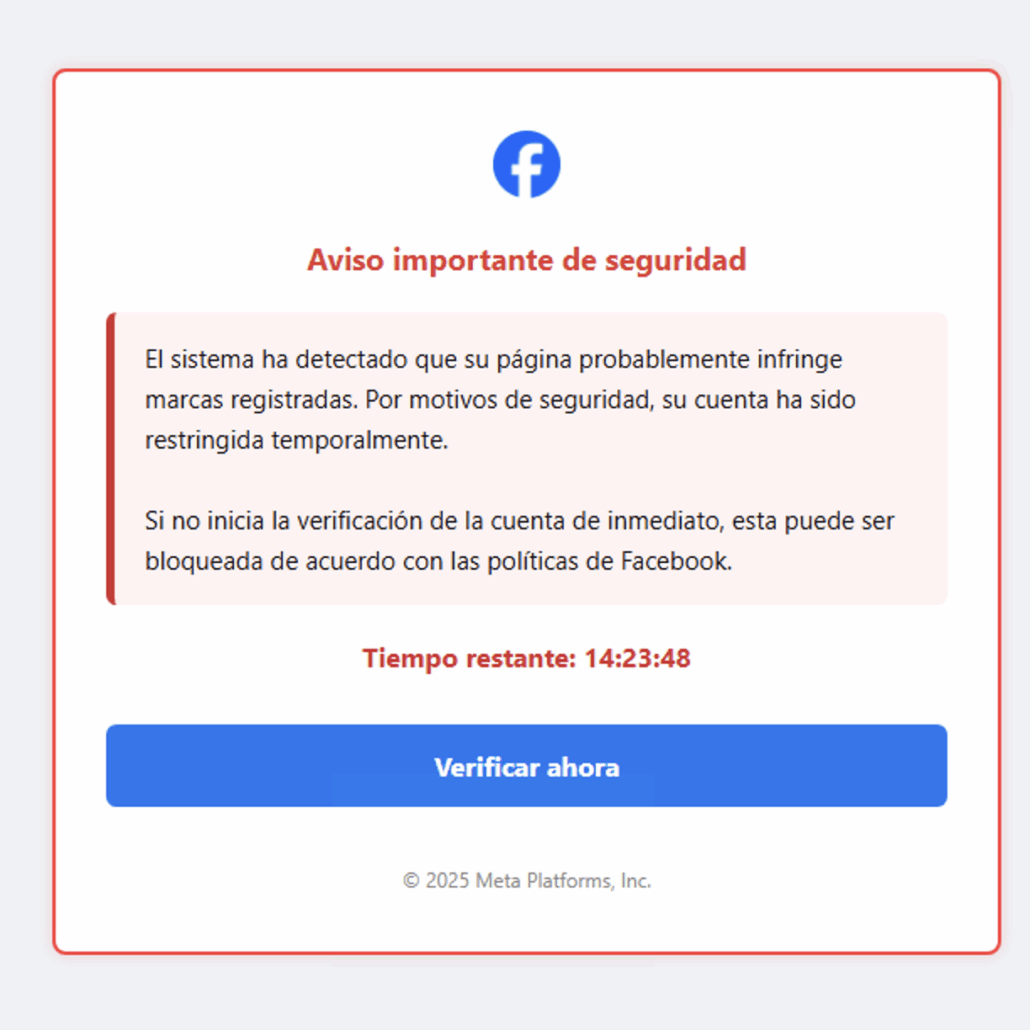
Fake Facebook login urging the user to authenticate to the account
This infrastructure was hosted entirely on DigitalOcean, and Meta acted quickly to detect and dismantle it after reporting.
Attribution Noise
Although the reachable nodes displayed a wide range of languages and regional indicators (Italian, Hungarian, Russian, Portuguese, Korean, Polish, French, Spanish, German, and Taiwanese), this diversity appears artificial.
Such patterns are consistent with:
- Reused server images
- Default OS locales
- Off-the-shelf web content
- Intentional attribution obfuscation
Below you can see our test on the phishing page:
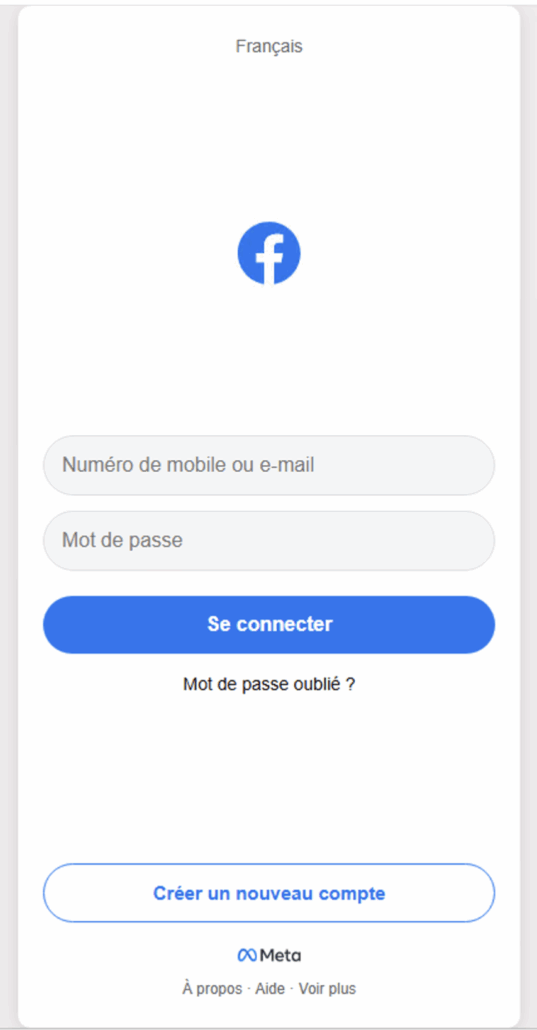
Initial fake login page (mobile app)
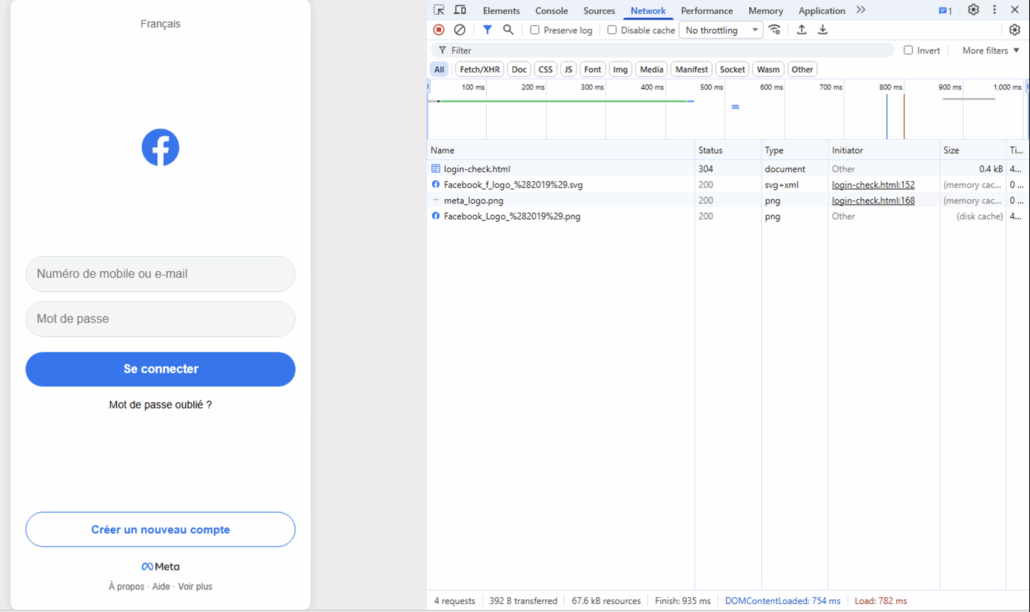
login-check HTML file and original pictures loaded from Facebook
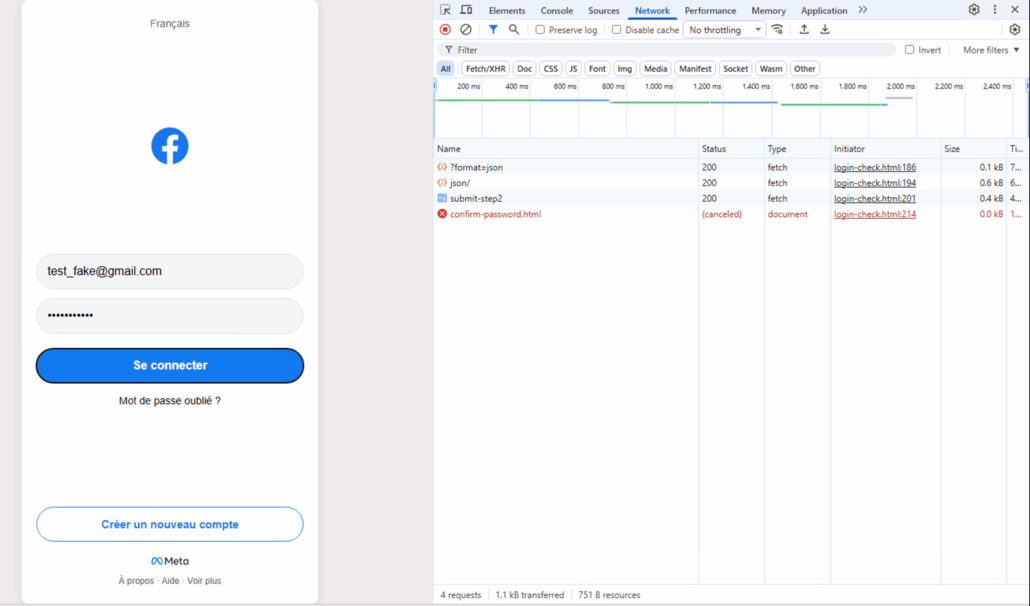
Failed attempt with fake login (transmitted to the real Facebook login page)
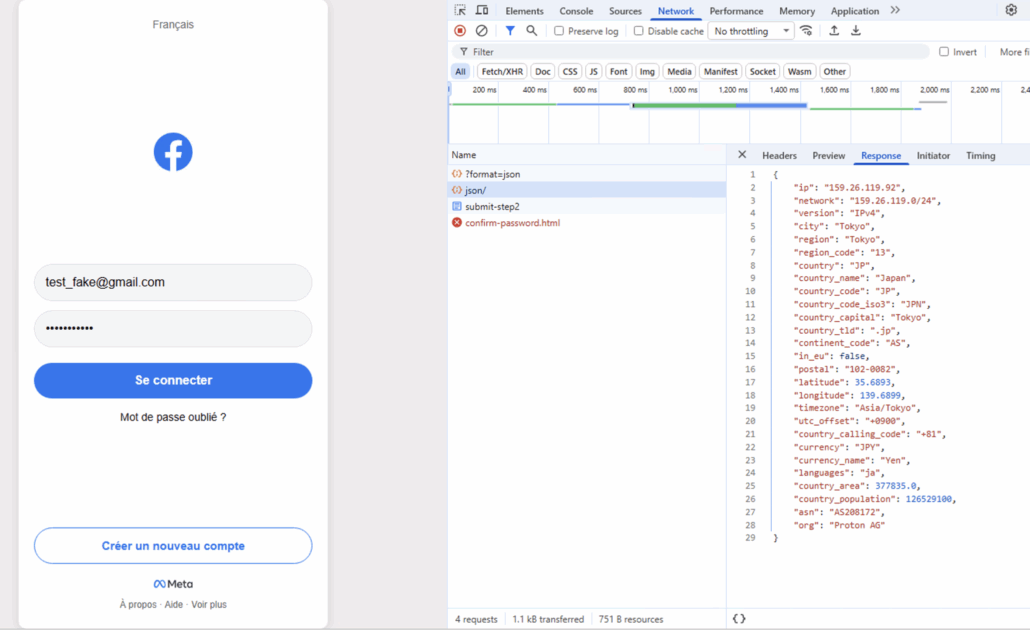
Collecting geo-location data
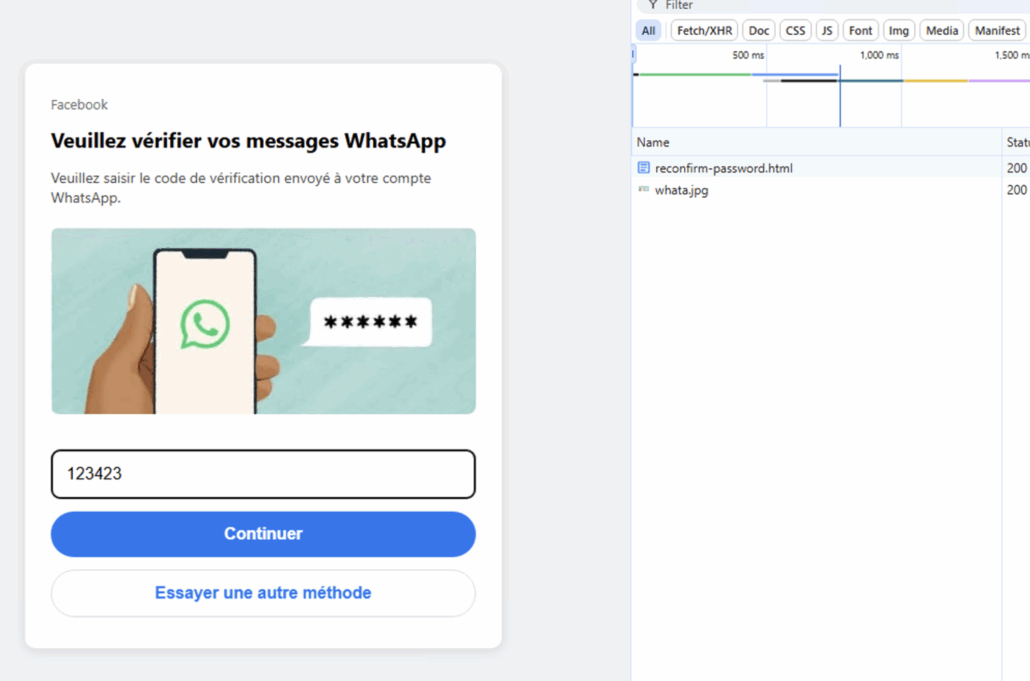
When inserting real credentials, a live 2FA request is displayed
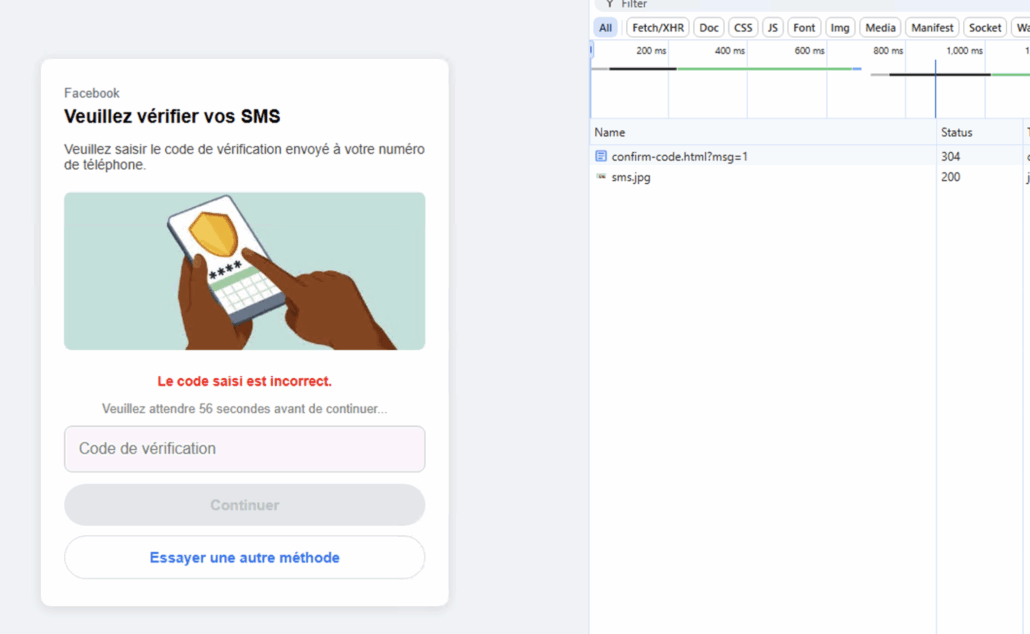
Once failed, 2FA code leads to another request for the SMS
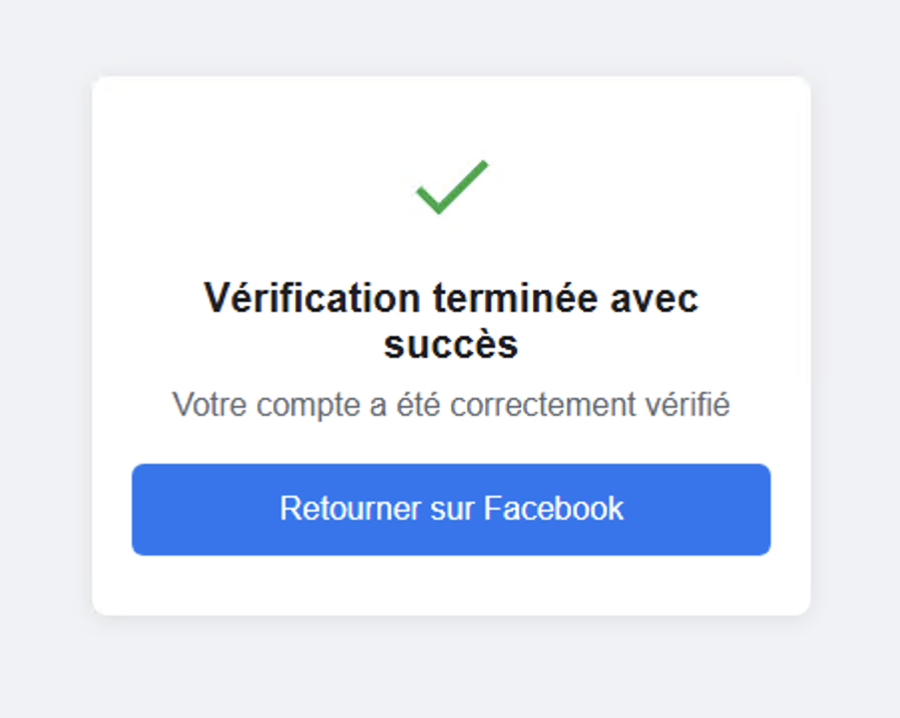
A second false SMS code leads to a successful notification (the link leads to the real Facebook site)
Live Microsoft O365 Phishing-as-a-Service Infrastructure
The most complex infrastructure uncovered targeted Microsoft O365 users and exhibited characteristics consistent with Phishing-as-a-Service (PhaaS).
Infrastructure Scale and Architecture
We identified 172 IP addresses, predominantly hosted on Linode (Akamai Connected Cloud), with smaller clusters on Vultr and Datacamp.
Each IP exposed a highly consistent set of ports:
- Web services: 80, 443 (Phishing sites)
- SSH: 22
- Kubernetes NodePorts: 53201–53202 (Phishing sites)
- Frequently: kubelet (10250), kube-proxy (10256)
- Occasionally: Calico Typha (5473)
This port profile strongly indicates attacker-operated Kubernetes clusters, rather than compromised standalone servers.
Web Behavior
Visiting the web ports initially displayed a blank page. After removing anti-debugging logic, a Microsoft login page became visible, though partially broken due to blocked Microsoft CDN assets.
The intended behavior appears to be:
- First visit: hide page body
- Attempt silent sign-in redirect
- If redirect fails, reveal phishing UI
Microsoft CDN domains were actively blocked at the network level, preventing CSS and JavaScript assets from loading, likely an indirect mitigation by hosting providers.

In 172 X 4 ports, when reaching with a browser, you get a blank page
Behind the scenes, the web page is actually full of data, but a small snippet in the HTML is set to display a blank page.
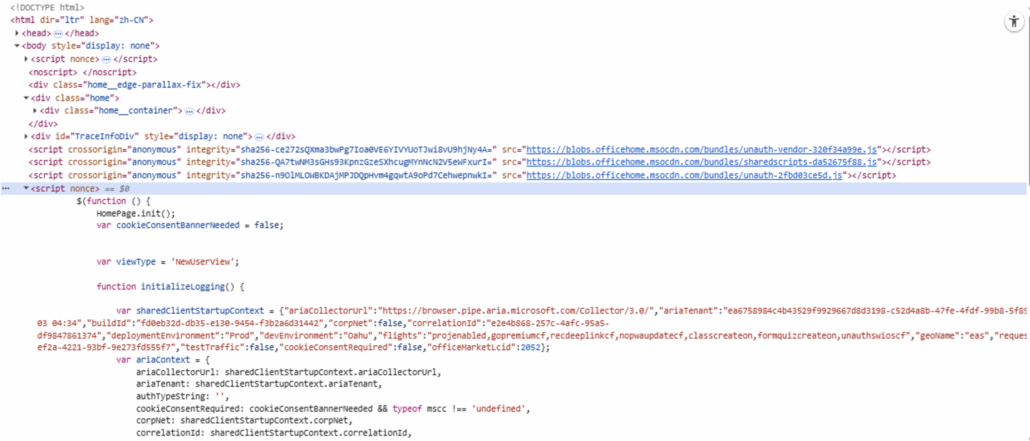
Part of the HTML code reveals a lot of connections to Microsoft
In the snippet below, you can see a simple but effective evasion mechanism by hiding the page body on the first visit and only revealing it on subsequent loads once a session storage flag (DefaultSignInCalledBefore) is set.
The additional conditions (!true and hard-coded string comparisons) are intentionally false and serve as logic noise to obscure the real control flow. This technique is commonly observed in modern phishing and AiTM infrastructures, where delaying UI rendering helps evade automated scanners and casual inspection, ensuring the login page becomes visible only after a user-driven redirect or interaction has already occurred.
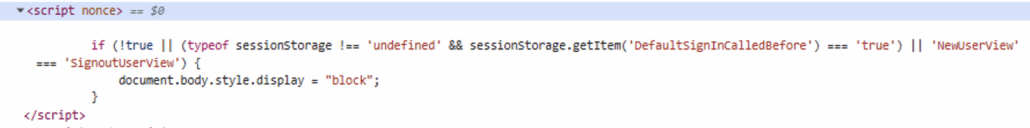
The condition in the snippet responsible for the blank page
When removing this condition, this is the page that loads:
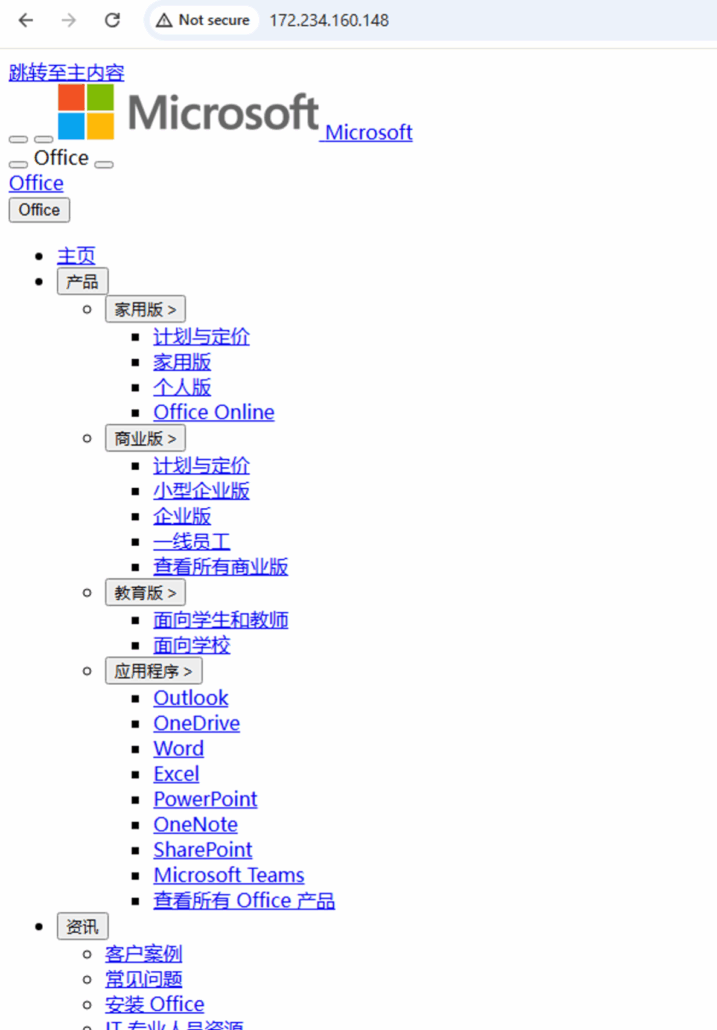
This is a Microsoft pixel identical to the original page, but since the CSS file wasn’t loaded, the website looks peculiar
Infrastructure Reuse and Certificate Correlation
Across the O365 cluster, we observed bit-for-bit identical Cloudflare Origin SSL certificates reused across dozens of IP addresses. These certificates shared:
- Serial numbers
- Public keys
- Validity periods
- Subject Alternative Names (with DNS reference to *.5ggiare.com)
This level of reuse is a strong indicator of centralized backend management, where IP addresses are treated as disposable while certificates and deployment templates persist.
Certificate reuse provides a higher-fidelity tracking signal than IP addresses alone and enables defenders to identify infrastructure clusters even as hosts rotate.
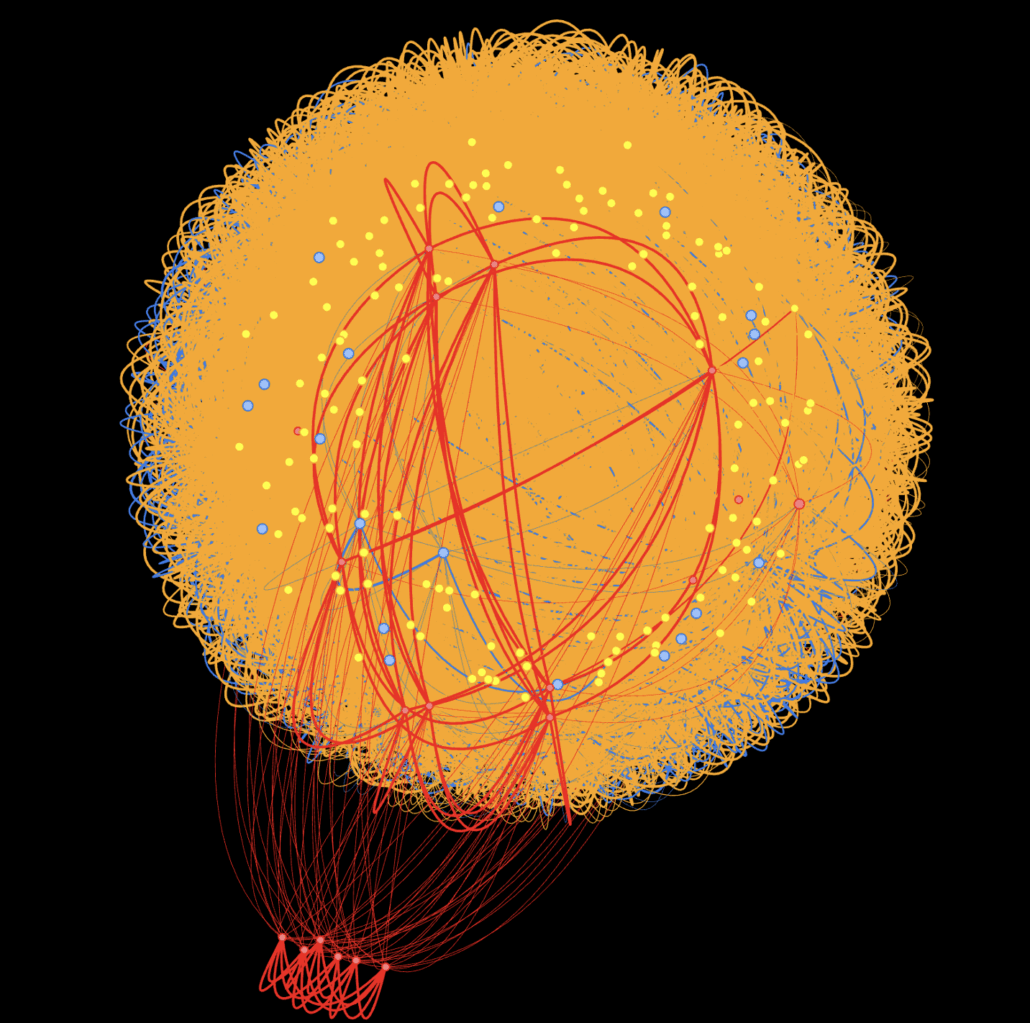
Visualization of the infrastructure as a similarity graph, where each node represents an IP address and edges connect hosts exposing nearly identical services
Kubernetes-Backed Automation at Scale
Visualizing the infrastructure as a similarity graph revealed a dense, highly connected core rather than organically diverse servers. Sub-clusters reflected minor deployment variations rather than independent operators.
Taken together, the evidence points to:
- Automated provisioning
- Cloned Kubernetes-based environments
- Centralized control
- Rapid IP rotation for resilience
- Massive scale up with NodePorts or LoadBalancer Service for instance
Reporting and Disclosure
We reported these findings to the Meta, Google, and MS CERT. Meta was very quick, and soon after we found the infrastructure, they detected it and shut it down.
We publish these findings to ensure visibility in case the operators:
- Restore Microsoft asset loading
- Repurpose the infrastructure
- Pivot to additional SaaS targets
Leveraging Cybercrime Intelligence to Find Phishing Infrastructure
This investigation demonstrates how cybercrime intelligence can be operationalized to uncover live phishing infrastructure across multiple platforms.
Modern phishing operations are no longer defined by static HTML pages. They are:
- Cloud-native
- Kubernetes-backed
- Real-time
- Commercialized
- Designed for resilience and rapid redeployment
Understanding what attackers sell underground is no longer optional,it is essential for anticipating what will be deployed next.
Indicators of Compromise
We are sharing the list of IP addresses found so that outbound traffic can be blocked.
Monitor Cybercrime Intelligence with Flare
The Flare Threat Exposure Management solution empowers organizations to proactively detect, prioritize, and mitigate the types of exposures commonly exploited by threat actors. Our platform automatically scans the clear & dark web and prominent threat actor communities 24/7 to discover unknown events, prioritize risks, and deliver actionable intelligence you can use instantly to improve security.
Flare integrates into your security program in 30 minutes and often replaces several SaaS and open source tools. See what external threats are exposed for your organization by signing up for our free trial.