
By Tammy Harper, Senior Threat Intelligence Researcher
Recent leaked footage and screenshots from the LockBit 5.0 affiliate panel demonstrate that the notorious ransomware-as-a-service (RaaS) operation has largely maintained its infrastructure and operational procedures following the Operation Cronos disruption. While the group’s core functionality remains unchanged, newly obtained materials reveal minor cosmetic updates, including holiday-themed interface elements. Senior CTI Analyst Arda Büyükkaya and IR Analyst Matthew Maynard provided valuable insights into this investigation.
Exclusive Screenshots from LockBit Affiliate Dashboard
The leaked materials provide unprecedented visibility into LockBit’s affiliate management system, showing the interface used by ransomware operators to coordinate attacks and manage victim negotiations.
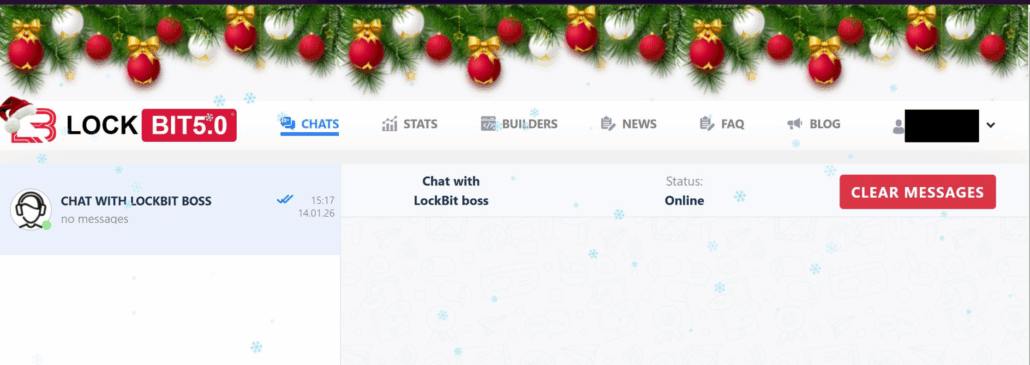
Screenshots of LockBit’s internal infrastructure with a holiday theme (Source: Arda Büyükkaya)
Video Evidence: Inside the LockBit Affiliate Control Panel
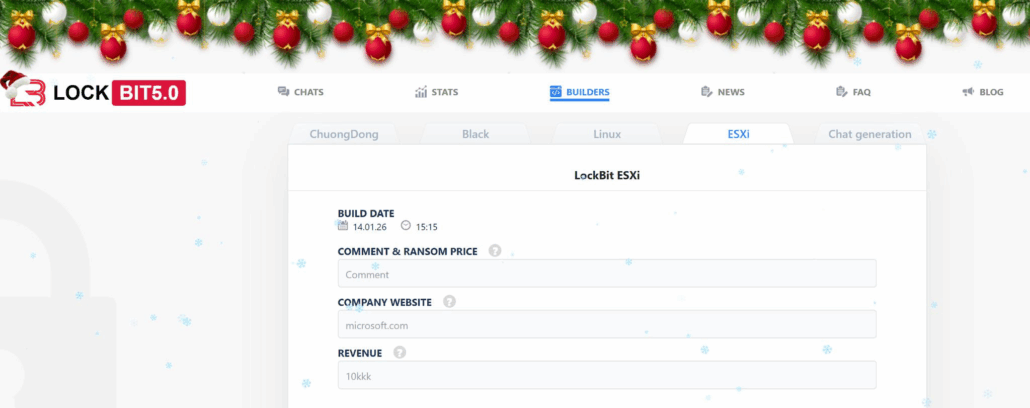
Exclusive video footage obtained from IR Analyst Matthew Maynard provides a rare operational view of the LockBit affiliate panel in action, demonstrating:
- LockBit builders
- Affiliate program rules and payment structures
- Onboarding message exchange
Video footage demonstrates the LockBit affiliate panel in action (Source: Matthew Maynard)
Download Latest LockBit 5.0 Malware Samples (January 14th, 2026)
Cybersecurity researchers can access the most recent LockBit variants for analysis.
Available LockBit 5.0 Variants:
- LB_Black_14_01_2026
- LB_Linux_14_01_2026
- LB_ESXi_14_01_2026
- LB_ChuongDong_14_01_2026
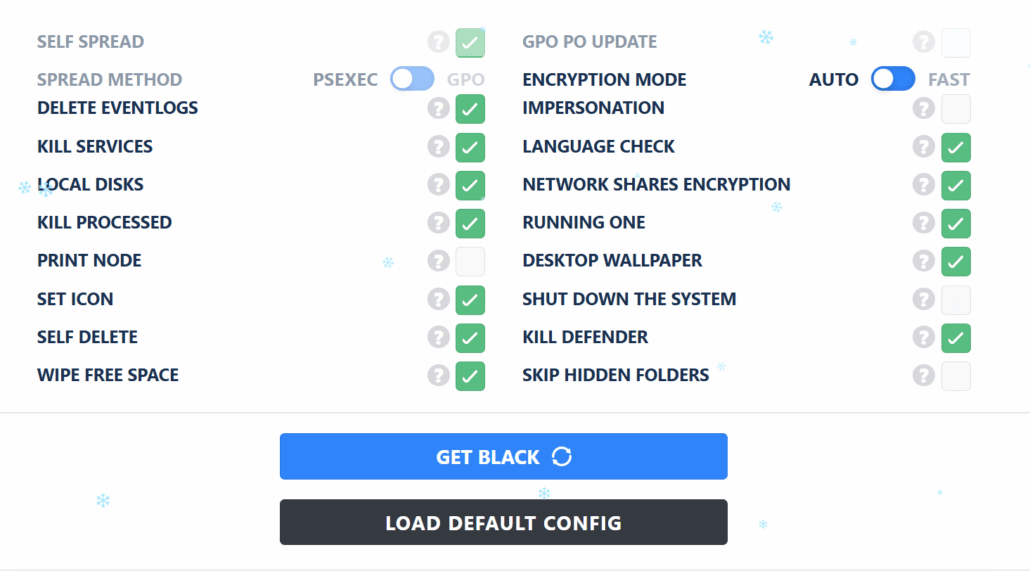
LockBit Black Configuration (Source: Arda Büyükkaya)
Key Takeaways for Security Teams
Here’s what security teams should know about LockBit 5.0:
- LockBit’s reputation isn’t as highly regarded as before, and affiliates largely do not want to work with them (but the group is proceeding forward as if the law enforcement actions didn’t happen)
- New variants target multiple operating systems and virtualization platforms
- Latest samples provide updated indicators of compromise (IoCs) for defensive measures
Track Ransomware Groups with Flare
The Flare Threat Exposure Management solution empowers organizations to proactively detect, prioritize, and mitigate the types of exposures commonly exploited by threat actors. Our platform automatically scans the clear & dark web and prominent threat actor communities 24/7 to discover unknown events, prioritize risks, and deliver actionable intelligence you can use instantly to improve security.
Flare integrates into your security program in 30 minutes and often replaces several SaaS and open source tools. See what external threats are exposed for your organization by signing up for our free trial.





