Effectively combating cybercrime requires not just strong technical skills but also strong crime detection skills, and the need for both is something that’s often overlooked as people focus on the newer, more novel technical aspects of cybercrime.
Nowhere in the battle against cybercrime is the combination of cutting-edge technical skills and old-fashioned detective work as necessary as tracking threat actors’ use of cryptocurrencies.
Cryptocurrencies are literally the point at which the newest and oldest elements in cybercrime meet. The “crypto” represents some of the latest cutting-edge technologies, including encryption and blockchains. The “currency” represents one of the oldest innovations that fuels crime: money.
Threat actors use the combination of old and new technologies in cryptocurrencies to create new opportunities and horizons for their enterprises. This means that security teams and those pursuing them have to be able to follow them and their trails by blending knowledge of today’s technologies with classic investigation techniques.
Learning how criminals use cryptocurrency requires instruction that breaks down both the technical mechanisms and the investigative approaches needed to counter them.
Tammy Harper, Senior Threat Intelligence Researcher and Certified Dark Web Investigator at Flare presented the Flare Academy training: CRYPTOS: Hunting for Adversaries in the Crypto Underground to share tactics, techniques, and procedures (TTPs) that criminals use with cryptocurrencies. The training covers lessons learned on defending against cybercrime that abuses cryptocurrency. Keep reading for the highlights, and/or join the Flare Academy Discord to access the full training.
Key Takeaways
- Pseudonymity, global access, speed, and irreversibility contribute to cryptocurrency working well for cybercrime
- Threat actors use cryptocurrency for:
- Ransomware payments
- Data theft extortion payments
- Sale of network access
- Credential resale
- Exploit sales
- Community credibility
- Threat actors protect their gains with:
- Peel Chains
- Mixers and Tumblers
- Cross-Chain Bridges
- Privacy Coins
- Decentralized Exchanges (DEXs)
Why Cryptocurrency Works Well for Cybercrime
Four Reasons Why Crypto is Ideal for Threat Actors
Tammy sets the stage with this important question: “why does crypto[currency] work so well for cybercrime?” She gives four reasons:
- Pseudonymity
- Global access
- Speed
- Irreversibility
These elements of cryptocurrency make them ideal for criminal activity in today’s online world. They also represent ways in which attackers can effectively exploit cryptocurrency’s technological capabilities to maximize their own ends.
It’s important to emphasize here that cryptocurrency is not inherently bad or malicious: it’s just powerful. Like money and technology, whether cryptocurrency is used for good or bad is entirely up to the intentions and motivations of those using it.
Pseudonymity refers to the fact that cryptocurrency doesn’t use legal names and addresses but instead public keys for the wallets that hold it. While this means it’s not easy to match wallets to specific individuals, it’s not impossible. And the public nature of much of cryptocurrency combined with that pseudonymity means that with a little good detective work, investigators can turn cryptocurrency wallets into an investigational asset.
Cryptocurrency is permissionless and borderless, giving it true global access. Cryptocurrency is a currency born of the internet: its global access reflects the internet’s global nature. Its threats for potential harm reflect the internet’s global threats for potential harm.
There is no central bank or governing body for cryptocurrency, by design. This lack of centralization can mean freedom for some, but it means no police, no regulators, no safety net. There’s a saying, “if everyone is in charge, no one is in charge,” and that applies here. This aspect of cryptocurrency makes it ideal for global crime, not just cybercrime, but it excels as a tool for cybercrime.
Cryptocurrency again mirrors the internet in speed: it’s not just global in scope but fast at the same time in the same way. Financial transactions used to take days or weeks. As Tammy said: “All of this is done in literally one second, or the transaction was done within a minute…the speed at which you can make and automate this process [of transactions] is truly baffling.”
Speed almost always favors attackers, and the speed aspect of cryptocurrency makes it very attractive for criminals. They can be done with their crime and have their money in hand before anyone even knows anything has happened.
Which brings us to irreversibility. One thing that differentiates cryptocurrency from other forms of electronic financial transactions and makes it more “cash-like” is the irreversibility of transactions. Put simply, when the money is gone, it’s gone for good. Tammy puts it like this in her talk:
“[A cryptocurrency transaction is] a one-direction transaction, which is really, really, important because it’s not like you can pay for something and then do [like you can with] a credit card and cancel it and do your charge back. That’s not possible with Bitcoin or with cryptocurrencies in general.”
The irreversibility of cryptocurrency combined with its speed makes it very attractive for illegal activities. Not only can the criminals be done with their crime and have their money in hand before anyone knows anything has happened, but once someone does figure out what has happened, it may be too late.
Taken all together, these four aspects make cryptocurrency very attractive for cybercrime. It provides a means to irrevocably move money around the world quickly in a way that makes it hard (if not impossible) to identify where it’s gone and to whom.
What Threat Actors Use Crypto for
Tammy lists out some of cryptocurrency’s attractiveness and usefulness for a wide variety of criminal activity. These include:
- Ransomware Payments: Victim uses cryptocurrency to pay ransom to attackers to decrypt their data.
- Data Theft Extortion Payments: Victim pays attackers in exchange for attackers not leaking data they have stolen.
- Sale of Network Access: Criminals buying and selling information from each other that can be used to illicitly gain access to networks or resources.
- Credential Resale: Criminals buying and selling stolen credentials, typically obtained from infostealers and used to illicitly gain access to networks or resources.
- Exploit Sales: Criminals buying and selling active exploits attacking vulnerabilities (previously unknown 0-days, recently patched 1 or more days), and proof of concept code (PoCs) that can be used to build exploits.
- Community Credibility: Making deposits on underground and dark web forums like XSS.is to establish trust and bona fides within the community to gain access.
This isn’t a complete list of criminal uses of cryptocurrency: criminals are always innovating to get more money in creative ways and try to keep ahead of defenders.
Tammy notes that “community credibility” is her favorite, and it’s worth looking at more as a peek into criminal culture.
Unlike the other uses, community credibility isn’t about theft or directly making money: it’s about a means to establish credibility to gain trust among strangers who have every reason not to trust anyone. It’s a reminder that communities, even ones with criminals in them, require trust to function and show how communities that need to find trust among the untrustworthy have solved that problem. As Tammy notes:
“[The deposit] establishes credibility that you are able to do transactions and you can buy and sell, and you’re a credible person or a credible group. Without that, it’s really hard because it shows that you have an investment in the community, and it shows that you have funds to back…You’re talking to talk, you can walk the walk. “
Money solves many problems in life: apparently, building trust among criminals is another.
Understanding why cryptocurrency is such a natural fit for threat actors on the internet is helpful for also understanding some of the challenges and obstacles you face when using it to track them down.
The Business of Cryptocurrency Crime
As the saying goes, to understand your adversary, you have to think like them. The first step in investigation tactics Tammy covers is to understand how threat actors actually do their work.
Not surprisingly, threat actor workflows have evolved to maximally exploit the capabilities and advantages that the internet and cryptocurrency afford them. They increasingly mirror legitimate business models, and we’ve dubbed this the “cybercrime assembly line.”
Over the past few years, we’ve seen an increase in specialization among online criminal threat actors. Where 10 or 15 years ago you would see criminals doing all the work themselves, today there’s more of both professionalization and specialization.
Internet crime has become organized crime. And organized crime means business. Organizing itself efficiently like a business, malicious actors have evolved the “ransomware as a service” (RaaS) model. The name itself is both a pun and a statement of truth. It’s a pun on “software as a service” (SaaS). And it’s a truth indicating how these cybercriminals have adopted some of the very same best practices that modern technology companies have. The “as a service” model has been hugely efficient and transformative for legitimate businesses for the past decade, and the same is true for “RaaS.”
As with all “as a service” models, it’s critical to understand who owns what in terms of shared responsibility. In the case of ransomware, there are two key parties to be aware of: affiliates and operators.
The Roles of Ransomware Affiliates and Operators
Affiliates execute intrusions and handle things like malware payload delivery. Operators maintain the malware, infrastructure, and negotiation portals. To continue with the “as a service” model analogy, affiliates are the front-line business while operators are the “as a service” providers on the back end.
Together, affiliates and operators work together to carry out attacks that, when successful, net them ransom payments in the form of cryptocurrency.
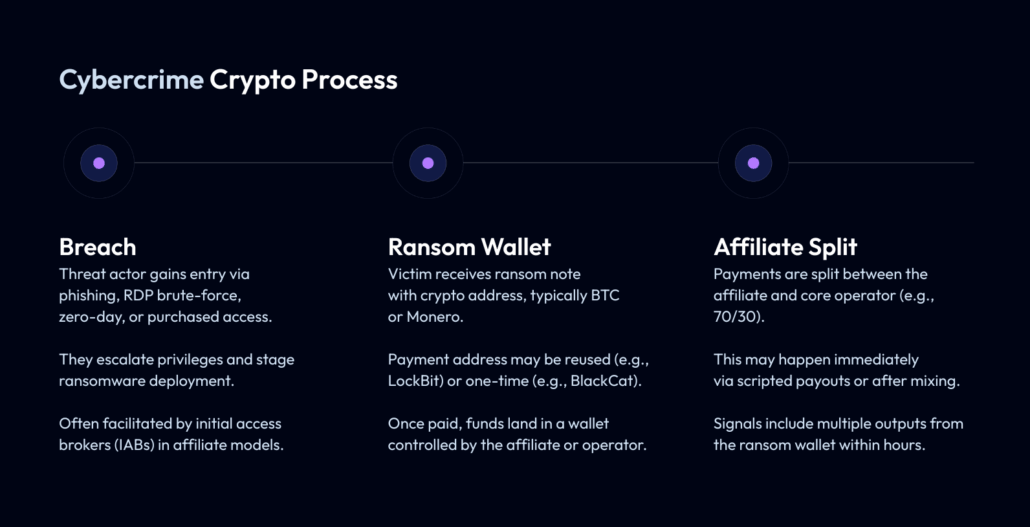
The cybercrime crypto process starts from breach, then ransom wallet, then affiliate split
Payment is the whole point of crime like ransomware and what makes it a business. If there’s no payment, there’s no point. This makes the “cashing out” part of the transaction, where they finally “get the goods” key.
Because it’s so important to the enterprise, cashing out is also of particular interest and usefulness for investigations. It’s where the age-old mantra of “follow the money” in investigations comes into play.
The Tricky Nature of the Cash Out Phase
In investigating the cash out phase, it’s important to remember that many modern ransomware campaigns are not the work of a single, monolithic entity but rather a joint operation of affiliates and operators.
The business model of affiliates and operators plays an important part here. RaaS operators don’t provide services to affiliates using the same revenue model as legitimate “as a service” providers do for services like cloud or generative AI. Legitimate “as a service” providers generally charge either by monthly subscriptions, or per use-of-resources. RaaS affiliates and operators follow agreed-upon revenue splits with affiliates keeping the larger share and operators taking a commission for infrastructure and support. The splits are typically 70/30, 80/20, or 90/10.
This means the cash out phase isn’t a simple, single payout to one person or even one group of several people. Instead, there are multiple payouts involved after a successful attack, at least to ensure that operators get their cut.
Multiple payouts are a key point when it comes to chasing money through cryptocurrency. Benjamin Franklin spoke to the risk this structure creates when he said that “three may keep a secret so long as two are dead.”
More people, and especially more groups splitting the “take” after a successful attack, means that the proceeds have to be distributed through multiple distribution transactions. Each distribution transaction carries risk around detection. More distributions mean the “attack surface” for detection increases. Greater attack surface means more opportunities for investigators to find and track payments potentially back to individuals.
This is the point where the hunter becomes the hunted, the attackers become defenders. Instead of looking for and exploiting weaknesses, threat actors are now focused on looking for and eliminating or mitigating weaknesses. Having stolen money through attacks, now the criminals have to defend their stolen money from others.
How Do Threat Actors Protect Their Gains?
Like security analysts, criminals who are protecting their money rely on a number of operational security (OpSec) TTPs. Below are some specific obfuscation techniques that are meant to make it harder to track specific transactions:
- Peel Chains: A sequence of transactions where small amounts are “peeled” off one at a time to try and prevent being noticed, much like “hiding in plain sight”.
- Mixers and Tumblers: Services that break the link between a sender and receiver by pooling funds from many users to help the fund get “lost in the crowd.”
- Cross-Chain Bridges: Tools that allow movement of assets between different blockchains much like a suspect taking multiple trains or taxis to lose surveillance.
- Privacy Coins: Specific cryptocurrencies that have fully private ledgers that help mitigate the risks around pseudonymity leading to discovery. Monero (XMR) is the most popular privacy coin today.
- Decentralized Exchanges (DEXs): Specific cryptocurrency exchanges that can be used to convert ransom cryptocurrencies into stablecoins or privacy tokens.
In her training, Tammy goes into detail on the specifics of these countermeasures as well as ways to look for them and counter the attackers’ countermeasures as a defender.
Cashing Out: Bringing the Money Home
All of the obfuscation techniques threat actors use are meant to try and throw investigators (and other criminals who might want to steal stolen money) off the money trail. These obfuscation techniques are steps that criminals carry out as they move to the final, important cash out phase where they move their gains out of the blockchain to lock in their gains and make them usable.
Tammy notes:
“This [cash out] phase is about converting crypto into usable money, or spendable value with as little risk of detection or seizure as possible.”
This is where the threat actors are nearly home free with their funds. But this phase has risks for the threat actors and opportunities for investigators who know where the criminals need to go to convert those funds into usable, spendable form, and can go looking there.
Centralized Exchanges (CEXs)
The best known places to cash out are through centralized exchanges (CEXs) like Coinbase or Binance. Because they are well known, they are heavily monitored but also have the most money and liquidity.
Security is all about risk versus reward, even for criminals, and one reason these can be attractive, despite the risks, is that the liquidity they offer can be hard to match elsewhere. Tammy notes, “when you’re moving over a million dollars’ worth of Bitcoin, you want to basically find someone that can pay you over a million dollars in fiat [spendable money].”
Over-the-Counter (OTC) Brokers
Another option is over-the-counter (OTC) brokers. These are brokers who will match buyers and sellers directly. They can also facilitate transactions where cryptocurrency is exchanged for more durable, harder to track items like gold, art, or real estate. But these transactions have risks because they’re individual and personal. And liquidity can be a concern.
Peer-to-Peer (P2P) Platforms
There are also peer-to-peer (P2P) platforms that can be found on Telegram channels and Binance P2P. Once again, liquidity is a concern, even more than with OTC. Which is why this tends to be used for smaller cash outs.
Finally, some will avoid cashing out into cash and instead go the route of other durable goods, like we already saw with OTC brokers, or even things like stolen gift cards.
In the end, regardless of where and how it’s done, the goal in cashing out is to have the money or value in hand, scot-free.
Role of Cybercrime Researchers: Blocking the Cash Out
Of course, the goal of security researchers is to ensure that cashing out never happens. While threat actors can use the technology of cryptocurrency and good tradecraft to try and succeed in their endeavors, defenders and investigators use their knowledge and skills to unravel those plans.
Access the full training, CRYPTOS: Hunting for Adversaries in the Crypto Underground in the Flare Academy Discord.
Monitor Ransomware Group Chatter with Flare
The Flare Threat Exposure Management solution empowers organizations to proactively detect, prioritize, and mitigate the types of exposures commonly exploited by threat actors. Our platform automatically scans the clear & dark web and prominent threat actor communities 24/7 to discover unknown events, prioritize risks, and deliver actionable intelligence you can use instantly to improve security.
Flare integrates into your security program in 30 minutes and often replaces several SaaS and open source tools. See what external threats are exposed for your organization by signing up for our free trial.