
Threat actors’ actions can have far-reaching consequences, from a “trolling” message stirring up journalists and researchers, to a phishing email and few lines of code affecting thousands of developer machines.
In this Leaky Weekly recap, we cover three cybercrime stories:
- NPM supply chain attack
- Fake Europol bounty for Qilin admin
- Operation Secure
Tune in as host and security researcher Nick Ascoli covers these stories below at Spotify, at Apple Podcasts, on YouTube (below), and/or keep reading this article for the highlights.
NPM Supply Chain Attack Hits Thousands of Developers
On September 8th, a phishing email sent to a trusted package maintainer (“qix.”) triggered one of the most far-reaching supply chain compromises in NPM’s history.

Phishing email disguised as a 2FA authentication update
How the Attack Played Out
The threat actor tricked Qix into handing over credentials by impersonating NPM support. Once inside, the attacker published malicious updates to 18 popular NPM packages, including several widely used dependencies.
The injected payload was a Clipper malware designed to hijack cryptocurrency transactions. It intercepted browser-based wallet addresses for Bitcoin, Ethereum, and others, swapping them with attacker-controlled addresses that closely resembled the originals.
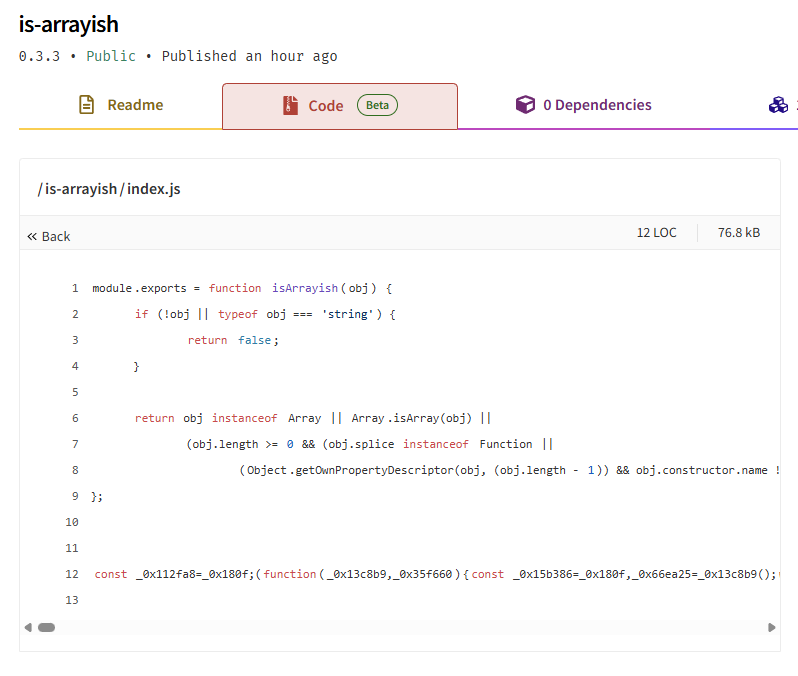
What the threat actor embedded into the packages
Impact of Attack
Combined, the affected packages see 2.5 billion weekly downloads. Chalk alone receives over 320 million downloads per week. Fortunately, the malicious code was detected within just two hours of publication.
Despite the scope, the threat actor only netted about $500 in stolen crypto before takedown. Still, researchers estimate thousands of developer machines may have been impacted.
Trend of Targeting Package Managers?
Just days later, a second attack targeted 40 additional NPM packages, this time aiming to steal API keys and secrets rather than crypto. This suggests that threat actors are increasingly experimenting with targeting package maintainers as an infection vector.
Fake Europol Bounty
On August 16th, a Telegram channel claimed to be Europol and offered a $50,000 bounty for information on two Qilin ransomware administrators, “Haise” and “XORacle.” Qilin, formerly known as Agenda, is a Ransomware-as-a-Service operation active since August 2022, known for worldwide attacks disrupting companies and infrastructure.

Original fake message posted in Telegram
The fake law enforcement announcement quickly spread among researchers and journalists, as it seemed convincing and mimicked the style of official press releases.
However, when asked for comment, Europol stated, “The announcement didn’t come from us,” and “we were also surprised to see this story gaining traction.” Shortly after, the operator behind the fake channel admitted it was a trolling campaign designed to embarrass journalists and security researchers who reported the story without verification. The troll was signed by “Rey,” a threat actor previously linked to major telecom breaches.
Operation Secure: One of INTERPOL’s Largest Takedowns
INTERPOL recently concluded Operation Secure, a massive global initiative against cybercrime infrastructure.
Scope of the Takedown
Coordinated across 26 countries, the operation achieved:
- 20,000 malicious IP addresses neutralized
- 69 malware families disrupted
- 41 servers taken down
- 32 suspects arrested
INTERPOL took down C2 infrastructure for Vidar, Lumma Stealer, and Rhadamanthys infostealer malware. Active ransomware operations were disrupted overnight, temporarily cutting off attacker access to victims. Though threat actors may bring these malware campaigns back online, disruptions are still valuable.
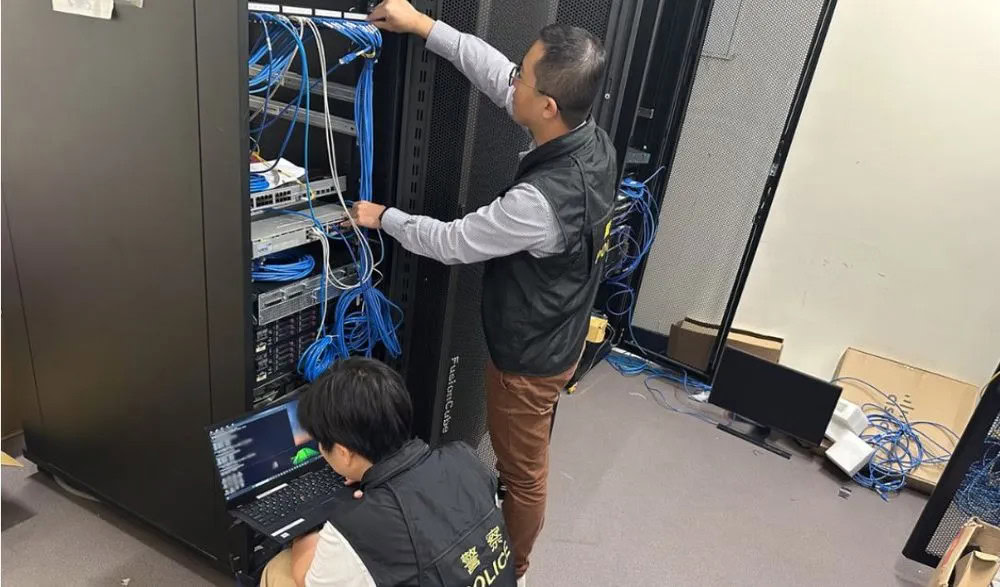
Law enforcement taking down malicious infrastructure
Law enforcement detained 18 suspects in Vietnam and 12 in Sri Lanka. The alleged ringleader was caught with cash, SIM cards, and shell company documents, possibly pointing to a scheme to open and sell corporate accounts.
More than 216,000 victims and potential victims were alerted following the takedown.
Always Stay Cautious…
Threat actors’ whims from a phishing email to a disinformation Telegram message can gain traction to cause a massive supply chain crisis or stir up the news cycle.
For security teams, staying vigilant, validating your sources, and collaborating with other organizations will go a long way in protecting your organization from threat actors.
Leaky Weekly and Flare Academy
Brought to you by Flare, Threat Exposure Management solution and industry-leading dataset on cybercrime that integrates into your security program in 30 minutes. Check out what’s on the dark web (and more) about your organization with a free trial.
Check out Flare Academy:
- Our free training series led by experts on critical topics such as threat intelligence, operational security, and advanced investigation techniques (earn CPE credits towards cybersecurity certifications)
- Our Discord community is a space to learn from and with cybersecurity professionals (including Nick!) and students, check out previous training resources, and keep up with upcoming training





