At a basic level, phishing kits are pre-built infrastructure that allow threat actors to harvest credentials from applications at scale. A phishing kit typically includes cloned login pages that mimic legitimate services, backend code to capture and exfiltrate submitted credentials, and evasion mechanisms to avoid detection by security tools and researchers.
The simplest phishing kits are little more than static HTML pages with a form that sends captured data to an attacker-controlled server. Modern kits are far more sophisticated. They function as complete platforms with admin panels, real-time credential delivery via Telegram, proxy capabilities that enable MFA bypass, and antibot systems that fingerprint visitors to block security researchers.
Detect Phishing Campaigns Before They Launch
Flare monitors for lookalike domains and tracks phishing kit infrastructure targeting your organization. Get alerted when attackers register fraudulent domains or harvest your employees’ credentials.
What makes phishing kits particularly dangerous is their accessibility. A threat actor with no coding ability can purchase a kit, deploy it on bulletproof hosting, and begin harvesting credentials within hours. The technical barrier that once limited phishing to skilled attackers has effectively disappeared.
What are Phishing Kits
At a basic level phishing kits are pre-built infrastructure that allow threat actors to harvest active credentials and 2FA tokens to applications at scale. The phishing kit economy is large and sophisticated, operating across the Dark Web and Telegram, with hundreds to thousands of buyers and sellers.
Anatomy of a Modern Phishing Kit
A typical phishing kit consists of several interconnected components:
Login page templates replicate the exact appearance of legitimate services. High-quality kits include pixel-perfect clones of Microsoft 365, Google Workspace, Okta, banking portals, and dozens of other high-value targets. Kit developers monitor their targets for UI changes and push updates to maintain accuracy. Some kits dynamically fetch logos and styling from the legitimate service to ensure the phishing page always matches the real one.
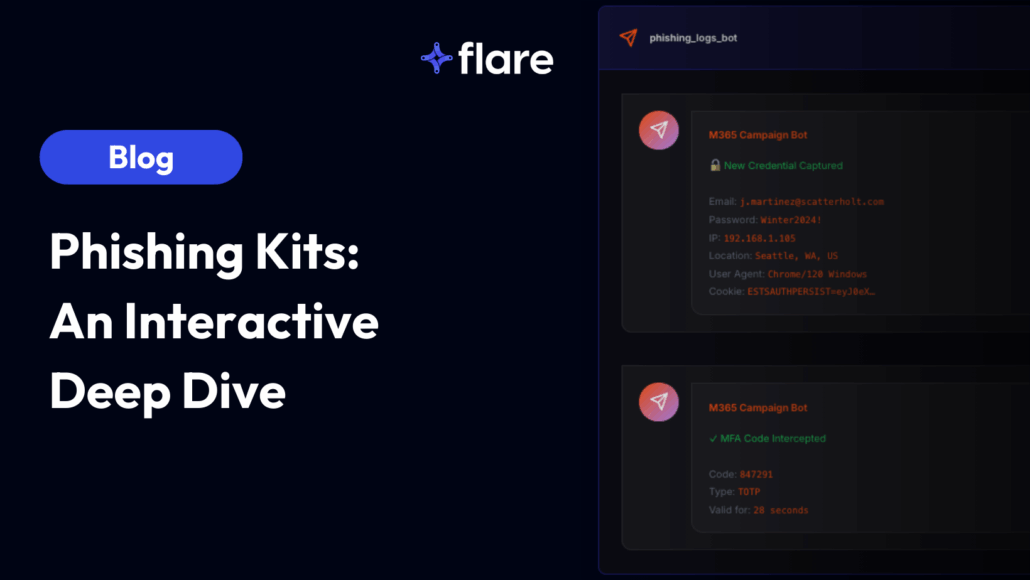
Credential capture and exfiltration handles the core function of harvesting submitted data. When a victim enters their username and password, the kit logs the credentials along with metadata: IP address, user agent, timestamp, and geographic location. Credentials are typically exfiltrated through multiple channels simultaneously. Most kits send real-time notifications to a Telegram bot while also logging to a web-based admin panel and optionally forwarding to an email address or webhook.
Evasion and antibot systems protect the phishing infrastructure from detection. Kits implement multiple layers of filtering: IP reputation checks block known VPN and datacenter ranges, geographic restrictions limit access to target regions, browser fingerprinting identifies automated scanners, and referrer validation ensures visitors arrived from a phishing email rather than a direct link. Visitors who fail these checks are redirected to the legitimate service or a benign page, making the kit invisible to security researchers and automated takedown systems.
Admin panels give operators visibility into campaign performance. The panel displays total visits, successful credential captures, conversion rates, and geographic distribution. Operators can manage multiple campaigns, export harvested credentials, and configure kit settings. Some panels include built-in credential validation that automatically tests captured passwords against the target service.
Telegram as a Back End for Phishing Kits
Telegram has become one of the primary hubs for threat actors in recent years, and also the backend for a great deal of cybercrime infrastructure. Telegrams API is easy to use, and the ability to rapidly spin up private groups and channels has made it an attractive platform for threat actors to utilize as backend infrastructure.
Adversary-in-the-Middle Attacks: How Modern Phishing Defeats MFA
For years, multi-factor authentication was considered the definitive answer to credential phishing. If an attacker captured a password, they still couldn’t access the account without the second factor. That assumption no longer holds. Adversary-in-the-middle (AiTM) phishing has fundamentally changed the equation by capturing not just credentials, but the authenticated session itself.
Technical Implementation: Evilginx and Similar Tools
Evilginx is the most well-known open-source tool for conducting AiTM attacks. Originally released in 2017 and significantly updated in subsequent versions, it provides a framework for creating reverse proxy phishing infrastructure.
Evilginx operates as a man-in-the-middle proxy that intercepts TLS connections. When a victim connects to the phishing domain, Evilginx terminates the TLS session and establishes a new TLS connection to the legitimate target server. It then relays HTTP requests and responses between the victim and the target while inspecting and modifying the traffic as needed.
The tool uses “phishlets,” which are YAML configuration files that define how to proxy a specific target service. A phishlet specifies the legitimate domain to proxy, which subdomains to handle, what cookies to capture, and how to identify when authentication has succeeded. The community has developed phishlets for most major services including Microsoft 365, Google Workspace, Okta, and numerous others.
When Evilginx detects that the victim has successfully authenticated (typically by observing the presence of specific session cookies), it logs the captured credentials and cookies. The attacker can then export these cookies and import them into a browser using developer tools or browser extensions designed for cookie management.
EvilProxy operates on similar principles but is offered as a commercial phishing-as-a-service platform. Rather than requiring attackers to deploy and configure their own infrastructure, EvilProxy provides a managed service with a web interface for creating campaigns, selecting targets, and retrieving captured sessions. This has significantly lowered the barrier to entry for AiTM attacks.
Other tools in this category include Modlishka, Muraena, and various commercial platforms that offer similar functionality with different feature sets and pricing models.
Phishing Kits by the Numbers
According to IBM X-Force’s analysis of phishing kit deployments, the median lifespan of a phishing kit deployment dropped to 3.2 days in 2023, down from 3.7 days the year before—suggesting that detection and takedown capabilities are improving. However, attackers are compensating with volume: they simply redeploy the same kit on fresh infrastructure when one deployment is burned. More striking is the increase in victims per deployment. The median number of potential victims per phishing kit deployment rose to 160 in 2023, up from 93 in 2022 and just 75 in 2021. This suggests that phishing operators are becoming more effective at driving traffic to their pages before takedown occurs, likely through better targeting, more convincing lures, or improved evasion techniques that extend the window before security tools flag the page. The same report found that phishing remained one of the top initial access vectors, tied with abuse of valid accounts at 30% of all incidents—a reminder that despite years of awareness training and email filtering, credential phishing remains a reliably effective attack technique.
The Phishing Kit Economy
Phishing kits exist within a mature underground economy with established market dynamics, distribution channels, and business models. Understanding this economy helps explain why phishing has scaled so dramatically and why it continues to evolve rapidly.
Phishing Kit Market Structure
The phishing kit market operates on multiple tiers. At the top are sophisticated developers who create and maintain advanced platforms like EvilProxy, Caffeine, and similar commercial offerings. These operations function as legitimate software businesses, complete with development teams, customer support, and regular feature updates. They invest in research and development, monitor their targets for changes that might break their kits, and compete for market share through feature differentiation and pricing.
Below this tier are independent developers who create and sell individual kits or smaller-scale PhaaS offerings. These operators typically focus on specific targets or niches, such as banking kits for particular regions or templates for cryptocurrency exchanges. They often sell through Telegram channels or dark web forums, building reputation through successful sales and positive reviews from buyers.
At the bottom are resellers and redistributors who acquire kits through purchase, theft, or leaks and resell them at lower prices. This tier is rife with scams, backdoored kits, and outdated products. Buyers at this level often lack the technical sophistication to evaluate what they’re purchasing, making them vulnerable to exploitation by the very criminals they’re trying to emulate.
Phishing Kit Pricing Models
Phishing kit vendors have adopted pricing models familiar from legitimate software:
Subscription access is the dominant model for sophisticated platforms. Monthly fees typically range from $150 to $1,500 depending on features, with premium tiers offering AiTM capabilities, dedicated infrastructure, and priority support. Subscriptions include ongoing updates, new templates, and access to the operator panel.
Lifetime licenses appeal to operators who want to self-host and avoid recurring costs. These typically run $2,000 to $5,000 and include the kit source code, allowing buyers to deploy on their own infrastructure. The trade-off is that updates and support may be limited or require additional payment.
Per-template pricing is common for simpler kits. A single phishing template might sell for $50 to $200, with buyers assembling their own collection of templates for different targets. This model suits operators who only need to target specific services.
Revenue sharing arrangements exist where kit developers take a percentage of successfully monetized credentials. This model aligns incentives between developer and operator but requires trust and transparency that is difficult to establish in criminal markets.
Phishing Kit Distribution Channels
Telegram has become the primary marketplace for phishing kits. Vendors operate channels where they advertise their offerings, post demonstration videos, and share testimonials from satisfied customers. Private groups handle sales transactions and customer support. The platform’s combination of accessibility, perceived anonymity, and rich media support makes it ideal for this purpose.
Dark web forums remain important for reputation building and reaching more sophisticated buyers. Established forums like XSS, Exploit, and others host vendor threads where developers showcase their products, respond to questions, and build credibility through transaction histories and community vouches.
Direct sales through personal networks account for a significant portion of high-end kit distribution. Established developers cultivate relationships with prolific operators, offering preferential pricing, early access to new features, and dedicated support in exchange for loyalty and discretion.
Mitigate Threats from Phishing Kits with Flare
The Flare Threat Exposure Management solution empowers organizations to proactively detect, prioritize, and mitigate the types of exposures commonly exploited by threat actors. Our platform automatically scans the clear & dark web and prominent threat actor communities 24/7 to discover unknown events, prioritize risks, and deliver actionable intelligence you can use instantly to improve security.
Flare integrates into your security program in 30 minutes and often replaces several SaaS and open source tools. See what external threats are exposed for your organization by signing up for our free trial.