
Stealer logs have quietly become one of the most important drivers of cybercrime today. From ransomware to large-scale data breaches, these stolen digital records are often the first step in an attack.
In part two of our Leaky Weekly (cybercrime current events podcast) mini-series: Use a Stealer Log, Go to Prison, we explore two major arrests tied to threat actors involved with attacking PowerSchool and Snowflake tenants. Tune into Use a Stealer Log, Go to Prison (Part Two) below on Spotify, on Apple Podcasts, on YouTube (below), and/or keep reading this article for the highlights. Check out the first part here.
What Are Stealer Logs?
Stealer logs are the output of infostealer malware, which harvests data when a victim downloads malicious software, often from cracked apps or poisoned ads.
A single log can contain:
- Saved usernames and passwords
- Session cookies that can bypass MFA
- Banking and financial details
- Browser fingerprints and autofill data
- Desktop files and screenshots
Each log is like a “digital master key,” typically zipped and sent to a command-and-control (C2) server for resale or exploitation.
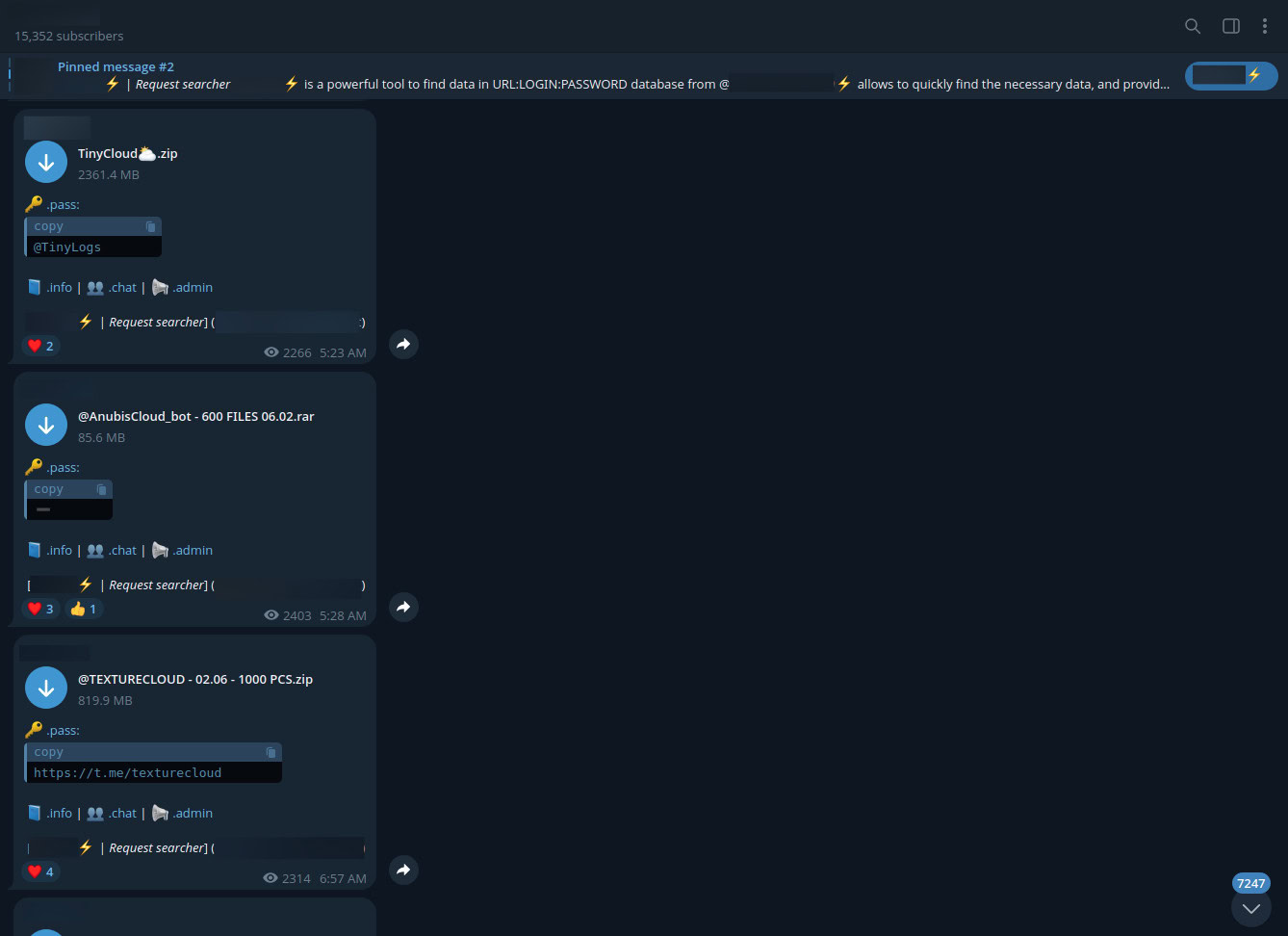
Threat actors post stealer logs in a Telegram channel
Significance of Stealer Logs in 2025
The 2025 Verizon Data Breach Investigations Report (DBIR), with contributions from Flare, found that 88% of web application attacks begin with stolen credentials, which typically are from stealer logs.
Our data shows 46% of stealer logs from personal devices contained corporate credentials, blurring the line between personal risk and enterprise exposure.
Why Threat Actors Use Stealer Logs
- Accessibility: Infostealers malware can cost about $130-170 USD per month on the dark web, which includes C2 infrastructure hosting and may not require technical expertise
- Automation: Infostealer dashboards can highlight credentials deemed as high-value, with corporate credentials, financial accounts, and session cookies.
- Profitability: Stealer logs with high-value credentials can be valuable to sell to other threat actors in cybercrime-oriented communities.
With a low barrier to entry, automated credential prioritization, and potential for financial gain, stealer logs are a prominent tool for cybercrime.
PowerSchool Hack Arrest
PowerSchool, the Student Information System (SIS) provider used by 16,000 schools and over 50 million students, disclosed a data breach in December 2024 (previously covered on Leaky Weekly). Attackers accessed highly sensitive data, including:
- In most school districts:
- Names
- Addresses
- Birth dates
- Emergency contact information (parents, guardians)
- With some school districts, even including:
- Social security numbers
- Medical information
- Grades
- Disciplinary records
Initially, PowerSchool reportedly paid a ransom to have the data deleted, even watching the deletion take place via video. But days later, school employees in North Carolina began receiving threatening emails from someone claiming to still possess the stolen data, opening with: “We are ShinyHunters.”
This was most likely from a different opportunistic threat actor (unrelated to the original attacker). Various attacks have been attributed to ShinyHunters, and this is a well-known name in the cybercrime underground.
Also to note here–unfortunately threat actors promising to delete stolen data may not be a guarantee.
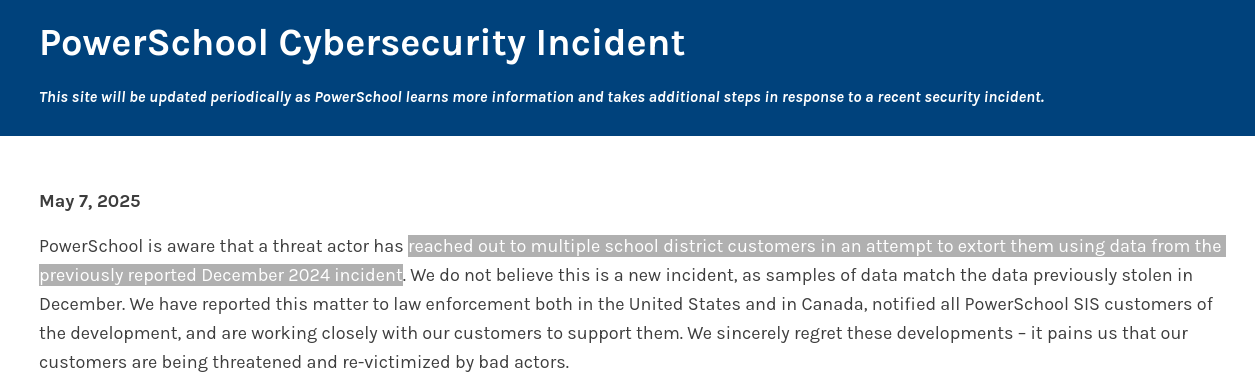
Follow up from Powerschool about the second extortion (Source: PowerSchool)
In May 2025, U.S. prosecutors revealed the arrest of Matthew Lane in connection to the PowerSchool hack.
Court documents allege that Lane:
- Accessed PowerSchool using leaked employee credentials
- Exfiltrated data via a server leased in Ukraine
- Demanded 30 Bitcoin ($2.85M) in ransom
- Conducted a separate $200K extortion attempt against a telecommunications company with a co-conspirator in Illinois
Nothing suggests that stealer logs were used in this attack, however, based on the cybercrime communities the threat actor accessed, it is likely they were the attack vector.
Lane pled guilty to:
- Cyber extortion conspiracy
- Cyber extortion
- Unauthorized access to protected computers
- Aggravated identity theft
He now faces five years in prison, three years of supervised release, and must forfeit $160,981.
Associated Arrests of Snowflake Tenant Hacks
In mid-2024, attackers compromised over 160 Snowflake customer cloud environments by exploiting stolen credentials from stealer logs. Victims spanned industries including entertainment, finance, telecom, and healthcare. Data stolen included:
- Personally Identifiable Information (PII)
- Medical prescriber DEA numbers
- Digital event tickets
The investigation culminated in a series of arrests:
- Connor Moucka (a.k.a. Waifu, Judische, Catist), arrested in Ontario, Canada, in October 2025
- John Erin Binns (a.k.a. IRDev), incarcerated in Turkey
- Cameron John Wagenius (a.k.a. Kiberphant0m), arrested in Texas in December 2024 near Fort Cavazos
Moucka was identified through links between his Apple iCloud account, Discord handle, and cryptocurrency wallets. After his arrest, Wagenius/Kiberphant0m posted on BreachForums with the hashtag “#FREEWAIFU” (referring to Moucka):
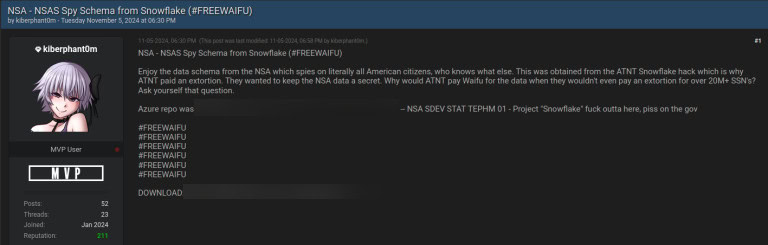
kiberphant0m posted about the Snowflake tenant breaches with the hashtag “#FREEWAIFU”
Wagenius was identified through his post history across Discord, Telegram, and various dark web forums, through posts that tipped off investigators to suspecting he could be military personnel:
- Mentioning “military base contracted Wi-Fi” in online arguments
- Posting photos in uniform
- Conducting Google searches such as:
- “where can i defect the u.s government military which country will not hand me over”
- “U.S. military personnel defecting to Russia”
- “Embassy of Russia – Washington, D.C.”
On July 15, 2025, Wagenius pled guilty to:
- Conspiracy to commit wire fraud
- Extortion in relation to computer fraud
- Aggravated identity theft
He faces up to 20 years in prison when sentenced this October.
These attacks have been said to be perpetrated by various threat actors and groups, such as ShinyHunters (because of the extortion notes), Scattered Spider, and more. Regardless of the threat actor attributed, these attacks used stealer logs as the attack vector against Snowflake tenants.
Stealer Logs are Central to Modern Cybercrime
Credentials stolen via stealer logs can lead to large-scale breaches across industries. Threat actors are drawn to their accessibility, but there are legal consequences for them.
For security teams, proactive monitoring of stolen credentials is critical to stopping attacks before they escalate.
Leaky Weekly and Flare Academy
For a deeper dive into these trends, check out more episodes at YouTube, Spotify, or Apple Podcasts.
Join us at Flare Academy, which can elevate your cybersecurity career. Our (free!) training series are led by experts that cover critical topics such as threat intelligence, operational security, and advanced investigation techniques. You can also earn CPE credits toward your cybersecurity certifications.
Join the Flare Academy Community Discord to keep up with upcoming training, check out previous training resources, chat with cybersecurity professionals (including Nick and Tammy!), and more.




