By Assaf Morag, Cybersecurity Researcher
The SessionReaper vulnerability (CVE-2025-54236), recently added to the CISA Known Exploitable Vulnerabilities (KEV) index, has rapidly become a dangerous threat facing Adobe Commerce and Magento merchants worldwide. While many publications focus on the technical flaw and its surface-level exploitation, we’ll take a different approach and dive into the cybercrime ecosystem surrounding this vulnerability:
- the exploit kits circulating in low-visibility channels
- the chatter within criminal communities
- the emerging patterns that reveal how threat actors are operationalizing SessionReaper in real attacks
By examining the underground activity, we provide a different view into threats and outline how defenders can mitigate them.
Key Takeaways
- The vulnerability is capable of leading to a full-system takeover if unaddressed: The exploit runs inside Magento’s application context, far beyond a simple front-end compromise
- Threat actors have been discussing this vulnerability and ways to abuse it: since Adobe published its advisory for CVE-2025-54236, we’ve been tracking references to it in Flare, where daily mentions have increased
- Recommendations to reduce risk from CVE-2025-54236 and prevent post-exploitation damage include applying the official Adobe/Magento patch immediately, and if your architecture allows it, disable file-based session storage (read our full recommendations below)
What are Adobe Commerce and Magento?
Adobe Commerce (formerly Magento) is a robust e-commerce platform used by businesses to build and manage online stores, offering features for product catalog management, shopping cart functionality, checkout, payment integrations, and customer experience optimization. Magento originated as an open-source solution known for its flexibility and developer-friendly customization, allowing brands to build highly tailored shopping experiences.
Adobe Commerce is the enterprise, paid version that includes advanced capabilities such as AI-driven product recommendations, Adobe-level analytics, scalable cloud hosting, and integrated marketing tools for larger operations.
What is SessionReaper (CVE-2025-54236)?
This vulnerability (CVSS 9.1) is caused by improper input validation (CWE-20) inside Magento’s session handling and REST API logic. The root issue is that Magento fails to fully verify the integrity of session data. Attackers can submit a forged session token that triggers Magento to deserialize untrusted session objects. The nested deserialization bug allows attackers to inject crafted objects into the session storage, which Magento later executes.
When Magento stores sessions as files (instead of Redis or a database), the attacker’s malicious serialized payload ends up as a physical file on disk. During subsequent operations, Magento deserializes the manipulated session file, leading to remote code execution (RCE) under the web server permission context. A more technical explanation of the vulnerability by the researchers who analyzed the patch and retraced the vulnerable API calls is available here (they also created a Proof of Concept and published it in their blog).
Why Do We Care About SessionReaper?
Magento is still one of the most popular e-commerce solutions in use on the internet, estimated to be running on more than 130,000 websites.
By poisoning the session and triggering unsafe deserialization, the attacker gains RCE within Magento’s PHP runtime. This allows them to execute arbitrary code under the web server user (www-data, apache, or nginx).
Once achieved, the attacker can:
- Upload PHP backdoors or webshells
- Add or modify Magento modules to ensure persistence
- Read and exfiltrate customer data (orders, addresses, emails)
- Access stored payment tokens or gateway credentials
- Create new admin accounts or escalate privileges
- Modify templates to inject malicious JavaScript into storefront pages
- Redirect customers to phishing or fraudulent payment portals
- Tamper with pricing, inventory, checkout logic
- Deploy malware, cryptominers, or spam scripts
- Pivot laterally to other internal systems reachable from the host
Because the exploit runs inside Magento’s application context, it provides deep and trusted access – far beyond a simple front-end compromise. This makes the vulnerability extremely dangerous and capable of leading to full-system takeover if left unpatched.
SessionReaper: Mentions on the Dark Web and Telegram
Since Adobe published its advisory for CVE-2025-54236 on September 9th, 2025, we immediately began tracking references in Flare, where daily mentions steadily accumulated. Initially, these were mentions of legitimate security research and media coverage, but also with a parallel current of increasingly darker and more operational discussions.
On October 24th, 2025, CISA formally announced that the vulnerability was being exploited in the wild, at which point we observed a shift from passive news-mirroring to active exploitation interest, including references to trading exploits and requests for PoC acquisition.
Notably, on Telegram in the “☠️☠️Suboxone 👹👹hackers 👺👺” group, we saw the publication of an open-source GitHub repo and later, on October 31st, a short tutorial teaching how to identify vulnerable Magento instances in the field.
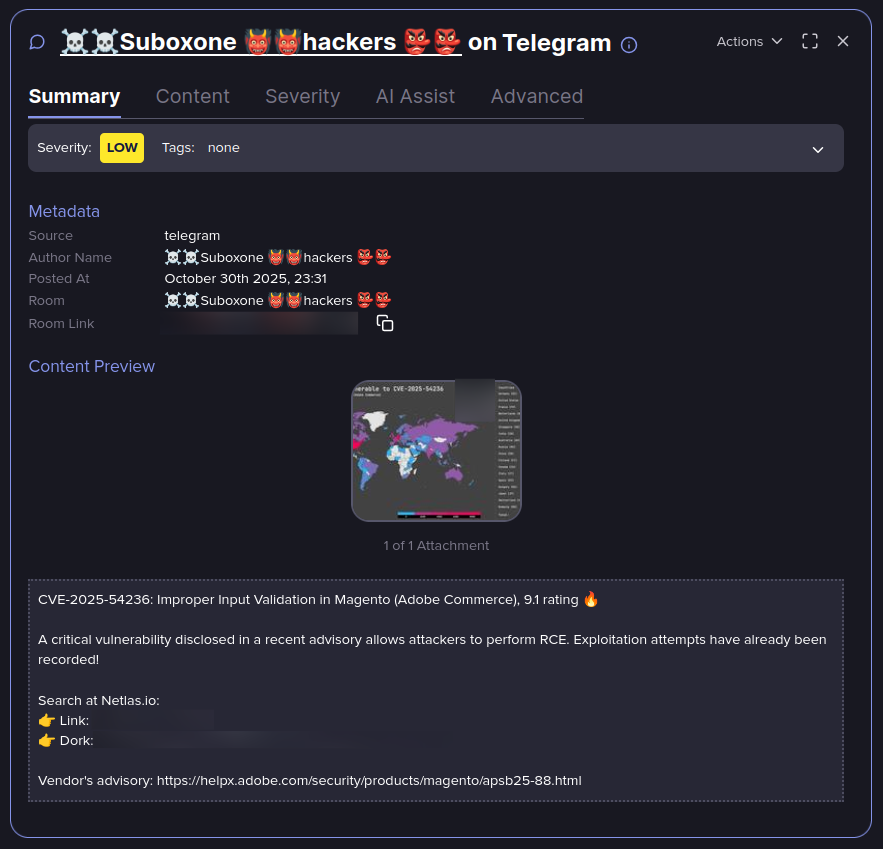
Short tutorial in exploiting CVE-2025-54236 (Source: Flare)
By November 3rd, discussions on carder.market revealed how cybercriminals are actively commodifying this CVE across Magento, WooCommerce, and Shopify to escalate from credential theft to full RCE-enabled financial extraction campaigns via backend compromise, payment token exfiltration, and residential proxy identity spoofing.
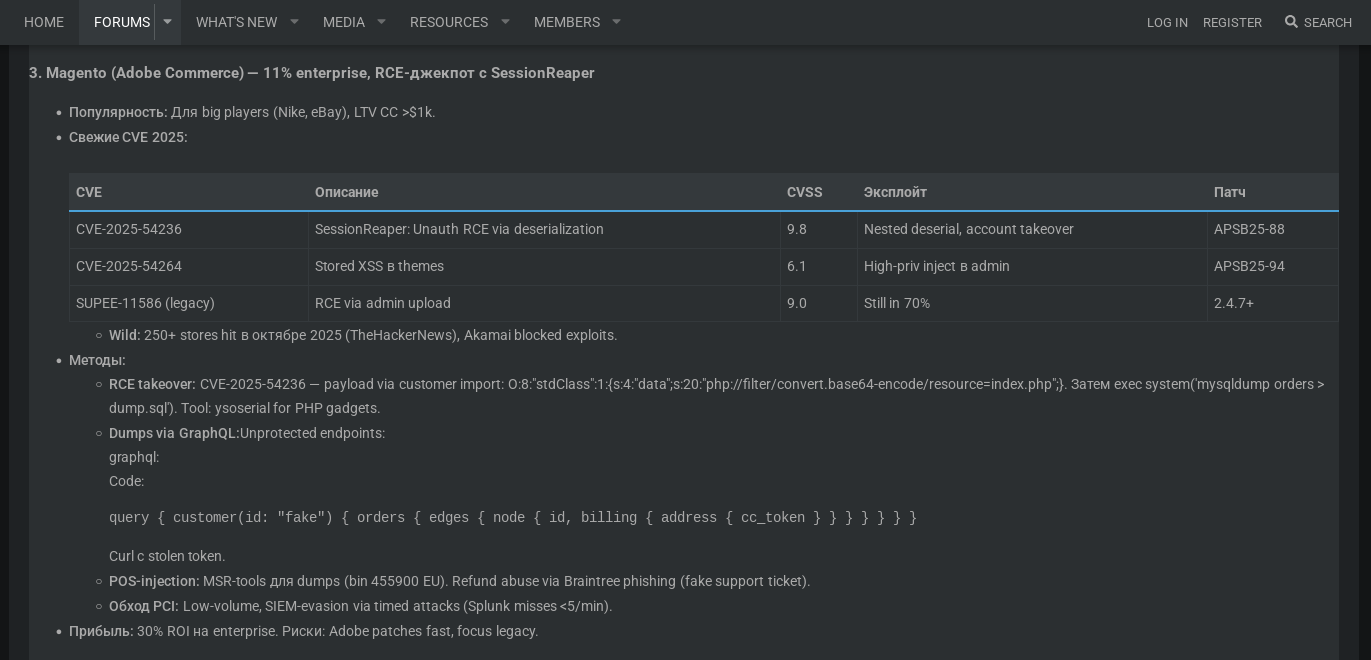
Threat actors discuss CVE-2025-54236 in Carder Market (Source: Flare)
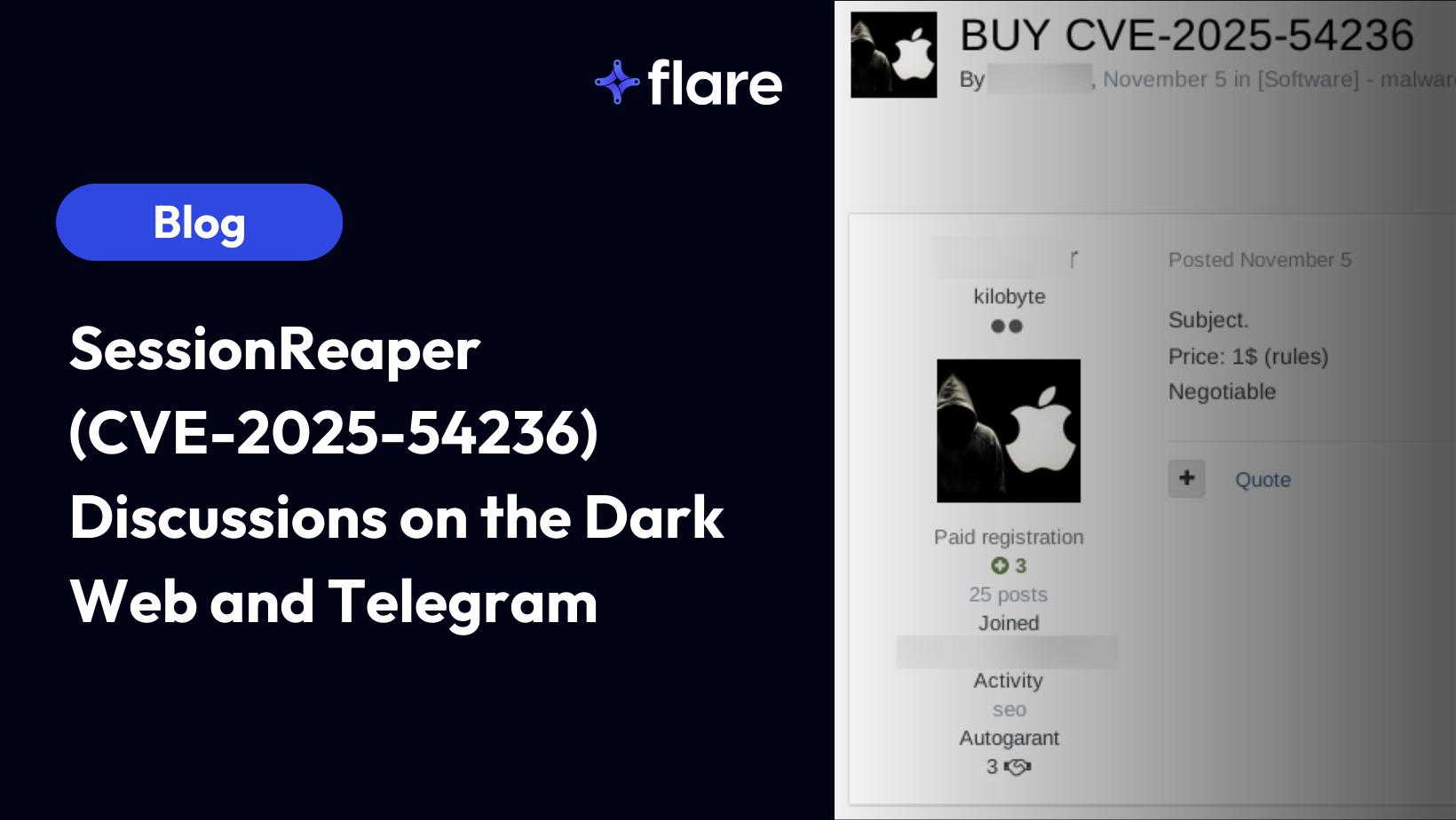
Finally, by November 5th, on Exploit, we began seeing explicit advertisements offering to buy or sell working exploits for this vulnerability – confirming its progression from newly-announced bug to fully weaponized underground asset.
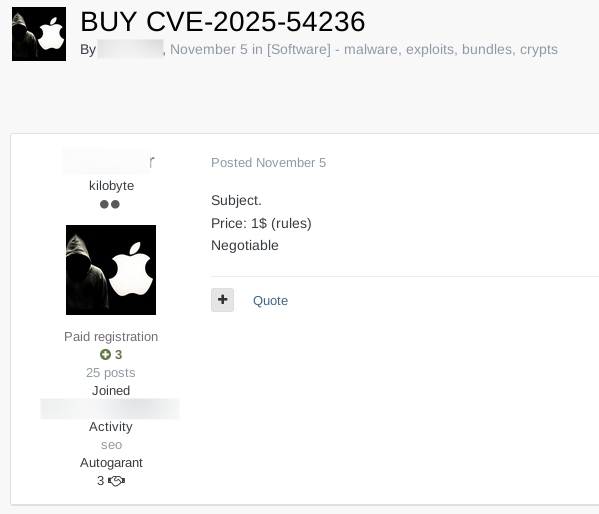
Threat actor sells a working exploit for CVE-2025-54236 for “$1 negotiable” (Source: Flare)
Monitoring these discussions and their escalation over time provides a strong indicator of how seriously attackers began treating this vulnerability and how rapidly it gained operational significance in the underground ecosystem.
Monitoring for Vulnerability Mentions in Flare
In Flare, you can easily look for vulnerabilities by:
- placing the CVE yourself in the search bar or any affiliated nickname the vulnerability carries
- using the search filter
Mapping the SessionReaper Campaign to the MITRE ATT&CK Framework
Our investigation showed that the attackers have been using common techniques to exploit this vulnerability. Here we map each component of the attack to the corresponding techniques of the MITRE ATT&CK framework:
| Initial Access | Execution | Persistence | Collection | Credential Access | Impact |
| Exploit Public-Facing Application (T1190) | Command and scripting interpreter: Unix Shell (T1059.004) | Server Software Component: Web Shell (T1505.003) | Data from Local System (T1005) | Unsecured Credentials: Credentials In Files (T1552.001) | Financial Theft (T1657) |
From a MITRE perspective, the attacker’s activity aligns with Exploiting a Public-Facing Application (T1190) to gain initial access, executing arbitrary commands inside Magento via Command/Scripting Interpreter (T1059.004) and establishing persistence using Web Shells (T1505.003).
Once inside, they extract sensitive transactional and customer-profile data using Data from Local System (T1005) and Application Credential Theft (T1552.001), ultimately monetizing this access through Financial Theft (T1657).
Mitigation Recommendations for Security Teams
To reduce risk from CVE-2025-54236 and prevent post-exploitation damage, we recommend:
- Apply the official Adobe/Magento patch immediately. If you haven’t already, and ensure all custom modules are compatible with the new type of validation changes.
- If your architecture allows it, disable file-based session storage. Use Redis or database-backed sessions to eliminate the attack surface created by file-based serialized session objects.
- Scan your server for malicious session artifacts and PHP shells, especially in /var/session/, /pub/media/, /pub/static/, and custom plugin directories.
- Review administrative user accounts for unexpected additions or role changes introduced after the advisory date.
- Monitor outbound traffic and API calls for indicators of payment token exfiltration or abnormal large data exports.
- Increase logging and enable alerting on deserialization errors, failed session conversions, and unexpected REST API input types, as these may indicate probing.
- Harden file upload behaviors, disable execution in upload directories, and ensure .php cannot be interpreted outside approved paths.
Monitor for Emerging Threats with Flare
The Flare Threat Exposure Management solution empowers organizations to proactively detect, prioritize, and mitigate the types of exposures commonly exploited by threat actors. Our platform automatically scans the clear and dark web and prominent threat actor communities 24/7 to discover unknown events, prioritize risks, and deliver actionable intelligence you can use instantly to improve security.
Flare integrates into your security program in 30 minutes and often replaces several SaaS and open source tools. See what external threats are exposed for your organization by signing up for our free trial.




