
The past few months have shown how social engineering, misconfigurations, and rushed development can lead to unfortunate outcomes for organizations, and the people who trust them with their personal data.
In this Leaky Weekly recap, we break down three major stories:
- The Salesforce tenant breaches
- Back-to-back breaches of the Tea app
- Rise and collapse of Tea’s male-oriented clone, TeaOnHer
Tune in as host and security researcher Nick Ascoli covers these stories below on Spotify, on Apple Podcasts, on YouTube (below), and/or keep reading this article for the highlights.
Salesforce Tenant Breaches: Attack that Started with a Phone Call
Salesforce is a customer engagement tool for thousands of global enterprises, powering sales, service, marketing, and more. Unfortunately from June through August 2025, multiple Salesforce instances were breached—not through vulnerabilities in Salesforce itself, but through compromised customer environments.
This sounds similar to the Snowflake tenant breaches (covered on Leaky Weekly) in which threat actors logged into the accounts of Snowflake customers. However, this case does involve hacking.
How the Attack Worked
Attribution points to UNC6040, better known as ShinyHunters, a threat group notorious for extortion and voice phishing (vishing). Attackers called employees and convinced them to authorize a malicious connected app to their Salesforce portal. This linked an attacker-controlled Data Loader app to the victim’s tenant, enabling bulk data exfiltration.
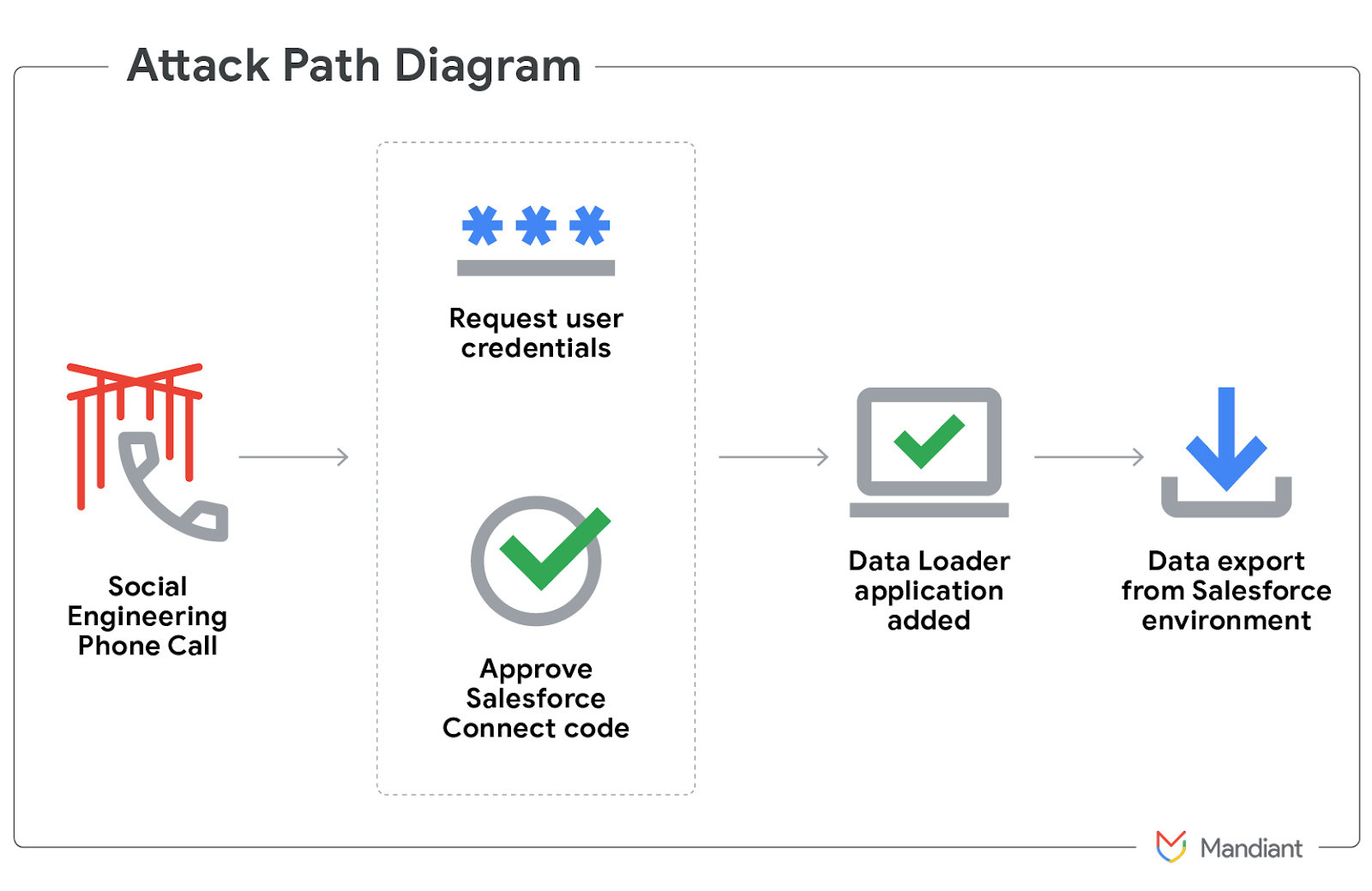
Mandiant outlined the attack path
Who Was Affected
Reports name a roster of household brands across industries: airlines, luxury brands, tech giants, and more. Stolen information often included customer service records: emails, names, countries of residence, and more.
What’s Next?
ShinyHunters has a history of waiting before launching extortion campaigns, so organizations may see delayed ransom demands or targeted phishing attacks leveraging stolen data. Reports also suggest the group may launch its own Data Leak Site (DLS), mirroring ransomware groups that publicly “name and shame” victims to increase pressure.
The Tea App: From Viral Sensation to Back-to-Back Breaches
Launched in 2023, the Tea app was designed as a safety tool for women to share “red” and “green” flags about men they dated. With viral traction on TikTok and Instagram, Tea soared to #1 on the App Store in July 2025. But days later, it suffered two severe data breaches.
Breach 1: ID Photos Exposed
On July 26, 2025, a 4chan user posted proof of an exposed Firebase storage bucket containing 72,000 verification photos with images of women holding driver’s licenses. This data should have been “immediately deleted,” per Tea’s privacy policy, but was left publicly accessible.
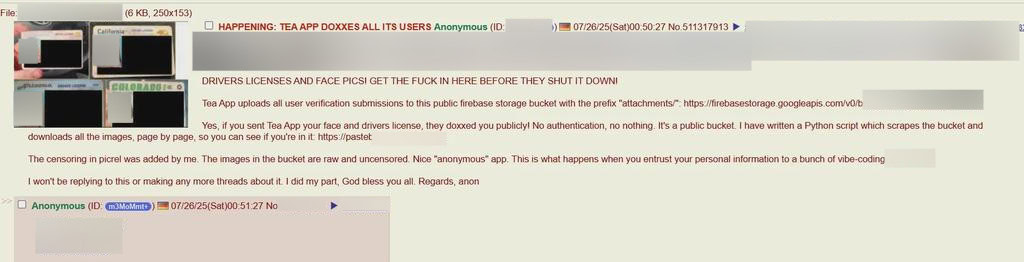
The threat actor posted on 4chan about the information from Tea that they accessed
Breach 2: Private Chats Leaked
Just days later, Tea had another exposure. Improper access controls exposed 1.1 million private chat messages, including deeply personal exchanges about abusive partners and infidelity. Users trusted Tea with sensitive conversations, which later became available online.
Both breaches trace back to basic misconfigurations and weak access controls, underscoring how a lack of security fundamentals can sink even the fastest-growing apps.
TeaOnHer: Tea’s Male-Oriented Clone
TeaOnHer, a male-oriented clone of Tea marketed as a platform where men could post about women, launched in August. It quickly reached #3 on the App Store with 165,000 downloads. But then it was discovered to have security flaws that were leaking:
- Names and email addresses
- Selfies and government ID photos
- Driver’s license data
- Location information
In total, about 53,000 users were affected.
The developer’s personal email and admin panel password (“Password1!”) were hardcoded into the site’s JavaScript, leaving them visible on the homepage.
Like Tea, TeaOnHer is already facing legal scrutiny and possible class-action lawsuits. Cybersecurity experts attribute rushed development and nonexistent access controls as the cause of these vulnerabilities. This may be a cautionary tale for startups racing to capitalize on viral momentum without building security in from the start.
Misconfigurations and Manipulation Fuel Modern Breaches
From Fortune 500 companies to viral apps, threat actors are exploiting the simplest gaps, whether it’s a convincing phone call or an exposed storage bucket. Extortion tactics are evolving to apply even more pressure on victims.
For security teams, the path forward is clear: reinforce strong access controls, employee training, and continuous monitoring.
Leaky Weekly and Flare Academy
For a deeper dive into these trends, check out more episodes at YouTube, Spotify, or Apple Podcasts.
Join us at Flare Academy, which can elevate your cybersecurity career. Our (free!) training series are led by experts that cover critical topics such as threat intelligence, operational security, and advanced investigation techniques. You can also earn CPE credits toward your cybersecurity certifications.
Join the Flare Academy Community Discord to keep up with upcoming training, check out previous training resources, chat with cybersecurity professionals (including Nick!), and more.





