This article was updated on July 24th, 2025.
Infected device markets continue to grow on both the clear and dark web. Essentially these markets sell access to infected computers & browser fingerprints that can be used by threat actors to compromise online accounts. Even unsophisticated threat actors can purchase browser fingerprints for as little as $10, and gain access to hundreds of unique logins stored in the browser, and the potential to bypass corporate 2FA Controls
Monitoring for these listings manually is almost impossible, traditional approaches to dark web monitoring are often ineffective for finding IOCs related to infected device markets. We expect infected device markets to continue to scale and become an increasingly important reason to conduct extensive monitoring of the dark & clear web.
A Look at Infected Device Marketplaces
Monitoring illicit communities is not a new concept for information security teams. Most organizations with a mature information security program already monitor dark web markets and forums to identify third-party exposure, stolen corporate credentials, and malicious actor TTPs. However the increasing popularity of infected device marketplaces pose an entirely new challenge and set of opportunities for security professionals.
Launched in late 2018, Genesis Market showed great potential, as it was the very first marketplace focused on digital identities. At a basic level, Genesis Market sold access to browser fingerprints of computers that had been infected with malware. This service enabled the purchaser to mimic the fingerprint of the victim’s browser, gaining access to dozens, or even hundreds of credentials stored in the browser, and in many cases the ability to bypass 2FA controls.
Authorities shut down Genesis Marketplace in 2023 (in an operation aptly called Operation Cookie Monster), but as with most illicit marketplaces, it was quickly replaced. The so-called “Russian Market” has been around for years but has recently seen a surge in users and become the go-to place for bad actors to purchase stolen credentials of all kinds. And while an estimated 85% of the listings of Russian Market are recycled from elsewhere, the scale of what’s on sale and the low prices—logs as low as $2—have attracted a massive following.
The Russian Market will eventually be taken down, too. But, as before, something will quickly replace it, and it will probably be worse than the previous version. To that point, the administrators behind Genesis Market were never caught, and many takedowns aren’t accompanied by arrests, leading bad actors to get discouraged but not defeated.
What’s clear is that infostealer malware isn’t going away anytime soon. That means marketplaces will continue to pop up to sell massive amounts of sensitive corporate credentials, the literal keys to the kingdom, to whoever wants to buy.
The Challenge
Relying on the FBI and others to remove infostealer marketplaces isn’t a sustainable strategy. Security teams can be more effective by being proactive about identifying what’s been stolen and using that threat intelligence to help prevent identity attacks and account takeover fraud. Monitoring infected device marketplaces isn’t always simple, though, since there is very little identifiable information listed that can be used to automatically detect corporate accounts that could be potentially listed. An average listing contains:
- The country where the bot is located
- The number of resources attached to the bot
- The number of browsers from which information was stolen (Fingerprints)
- The date on which the bot was installed, and last updated
- A partial IP address
- The operating system of the bot
- A list of all resources available
Even more concerning is that these markets have commoditized and simplified their offerings to enable even unsophisticated threat actors to utilize fingerprints. As can be seen in the image below, downloading a fingerprint is similar to online shopping. Marketplaces even provide detailed guides and tutorials on how to use the bots to successfully execute attacks.
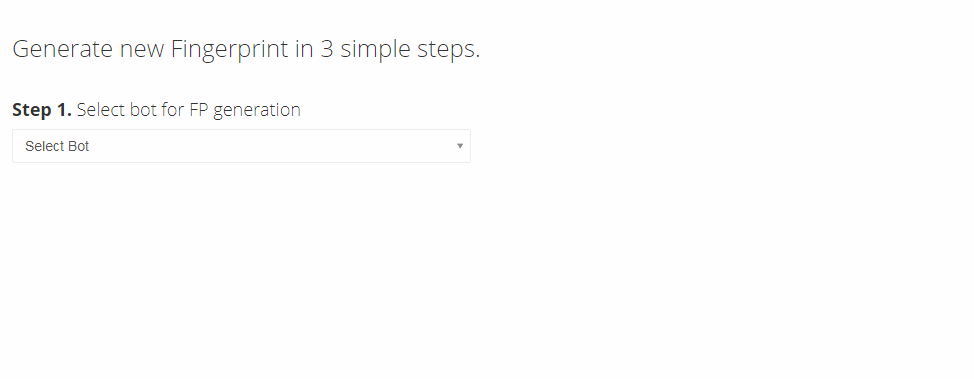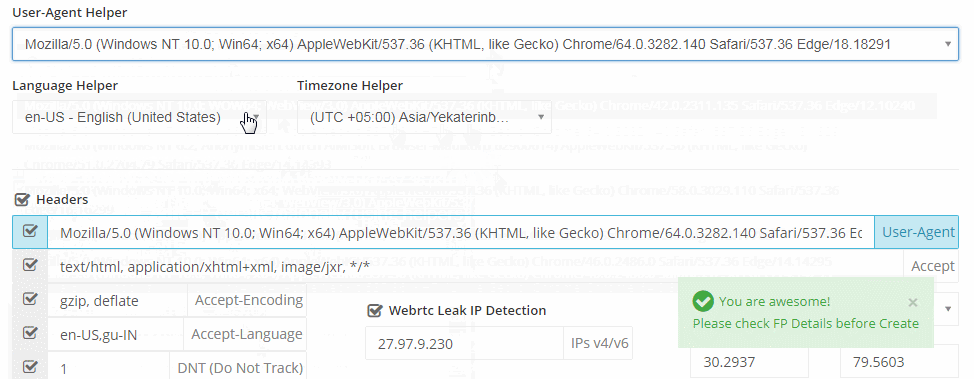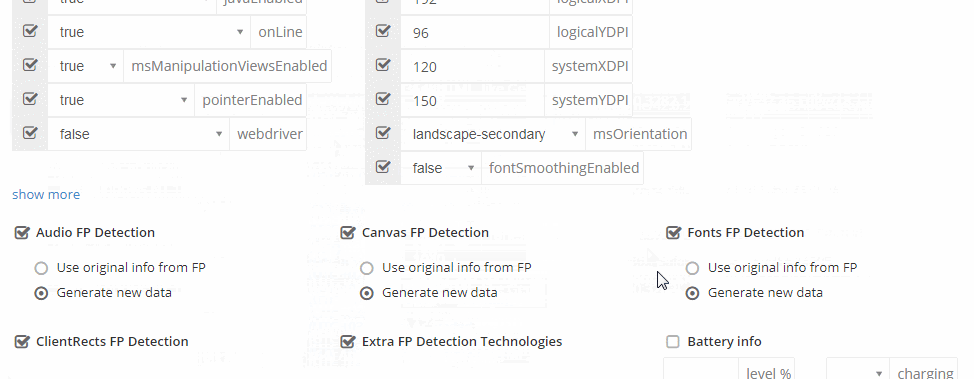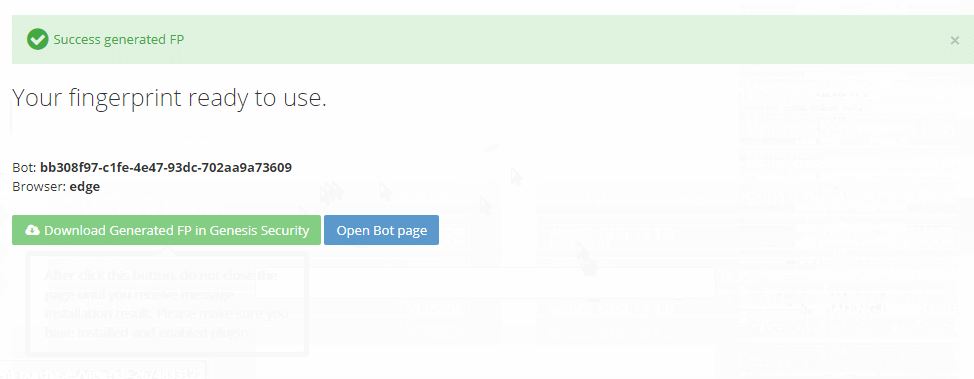
Previously, on Genesis Market, most listings were focused on individuals with access to banking and financial services accounts that threat actors could exploit. However, a significant portion of the listings on Russian Market and others are Windows 10 Enterprise devices, indicating that a substantial number of offerings are likely to be corporate computers that could hold logins to high-value internal corporate accounts and environments. By one estimate, more than 60% of the listings on Russian Market contain SaaS credentials for common business apps, and as many as 77% include single-sign-on (SSO) credentials that give entry to multiple systems and data sources. Regardless of whether infostealer attackers intended to target corporate credentials, they’re alarmingly successful at capturing them, leading to a robust and fast-growing trade for this data on illicit corners of the internet.
Monitoring for Stealer Logs with Flare
The Flare threat intelligence solution empowers organizations to proactively detect, prioritize, and mitigate the types of exposures commonly exploited by threat actors. Our platform automatically and constantly scans the clear & dark web and prominent threat actor communities to discover unknown events, automatically prioritize risks, and deliver actionable intelligence you can use instantly to remediate risks from stealer logs and beyond.
Flare integrates into your security program in 30 minutes and often replaces several SaaS and open source tools. See stealer logs relevant to your organization by signing up for our free trial.