
This article was updated on July 25th, 2025.
Ransomware has always been about extorting money from victims. But why get paid once when you could get paid three times? Not content with single extortion attacks, ransomware gangs have escalated to double and even triple extortion.
With the commodification of cybercrime, adversaries have significantly increased the sophistication levels of their operations, and therefore also the potential devastating impacts of a ransomware attack.
In our webinar, Triple Extortion Ransomware & Dark Web File Dumps, Flare Director of Marketing Eric Clay and CTO & Co-Founder Mathieu Lavoie discussed trends in ransomware attacks including:
- double/triple extortion
- different types of ransomware
- methods for stealing sensitive data
and more. Check out the webinar, or keep reading for more insights into ransomware trends.
How are Ransomware Groups Changing?
Ransomware attacks began as a simple transaction — a cybercriminal would infect a device, encrypt the victim’s data, and demand a ransom. However, ransomware groups are constantly changing their tactics, techniques, and procedures (TTPs). One alarming trend that we’ve seen recently is ransomware groups resorting to double and triple extortion tactics.
What is a triple extortion ransomware attack?
In a triple extortion attack, a threat actor goes beyond simply encrypting a victim’s data. Instead they add layers of pressure to coerce victims into paying one or more ransoms. Attacks follow the following pattern:
- Attackers encrypt files and demand payment for a decryption key, rendering systems and data unusable, and interrupting businesses.
- Having stolen sensitive data before encrypting it, the attackers then threaten to leak or sell the data if a ransom isn’t paid.
- The third layer of extortion varies, although the goal is always the same: another paid ransom. The bad actors may threaten to:
- Launch DDoS attacks
- Harass customers or other stakeholders
- Contact the media
- Or they may simply demand more payments after a ransom is paid
Some of the more sophisticated ransomware groups are even moving away from encryption all together, choosing to focus on data exfiltration and ransom. This creates an additional opportunity for threat actors to monetize ransomware since, even if the ransom isn’t paid, actors are able to sell access to the data.
This doesn’t mean every ransomware group is abandoning encryption. Encryption still creates chaos and loss for companies. It is an effective method of creating pressure and causing operational impact that can lead to financial loss. Therefore, encryption is likely here to stay for many groups, and we will likely continue to see groups finding additional ways to gain leverage and force companies to pay.
The Growing Impact of Infostealers on Ransomware Attacks
Ransomware and infostealers are increasingly interconnected in the modern cybercrime ecosystem. Infostealers, remote access Trojans (RATs) that infect computers, exfiltrating sensitive data and compiling it into stealer logs, which are distributed online.
The ransomware economy runs on stealer logs, which include massive amounts of user data, such as credentials, session cookies and tokens, browser data, cryptocurrency wallets and more. Ransomware operators buy or harvest this information to launch their attacks — and they tend to look for stealer logs or variants that contain specific information, or target certain industries.
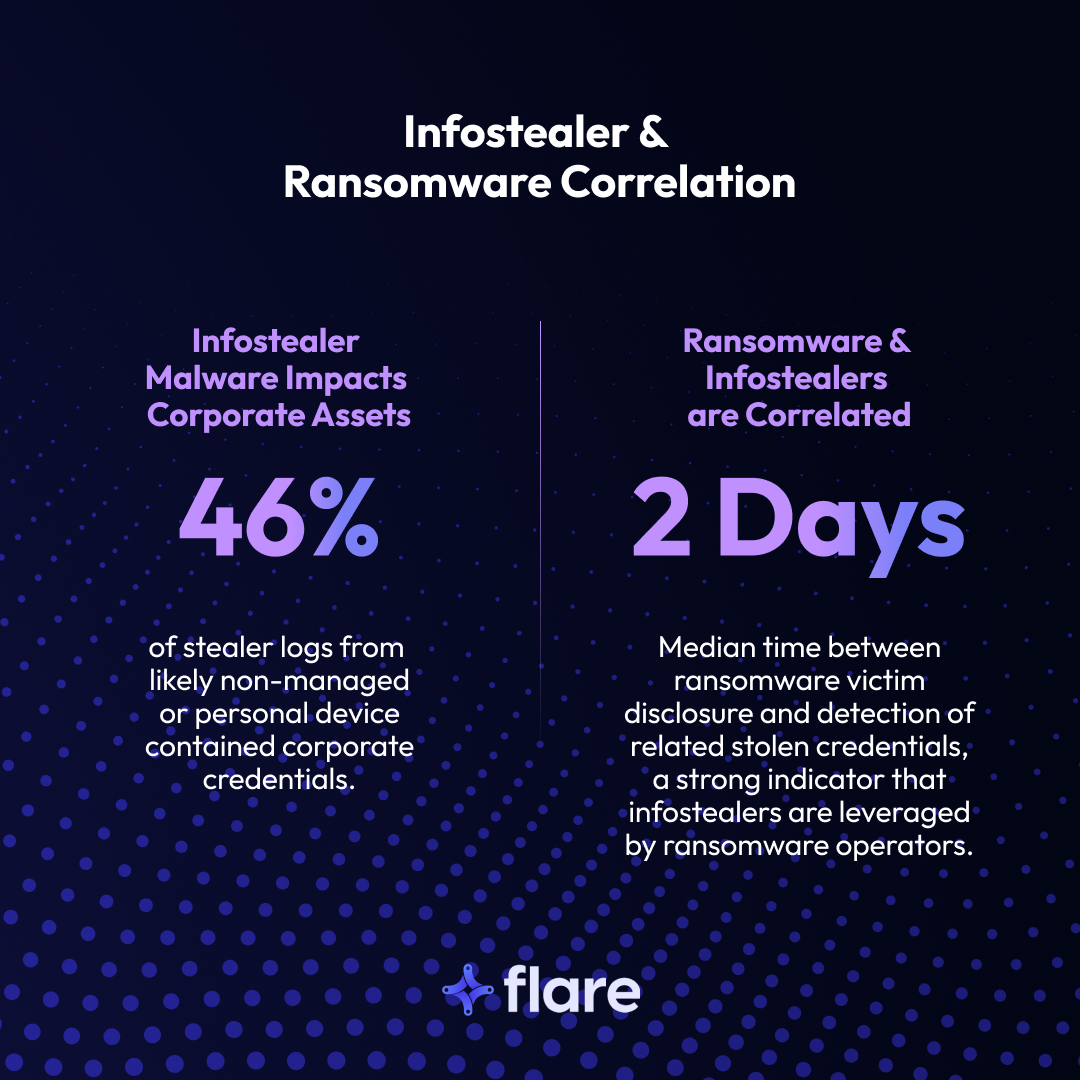
The 2025 Verizon Data Breach Investigations Report (DBIR) states that 46% of stealer logs likely from personal devices contained corporate credentials. In addition, the median time between ransomware victim disclosure and detection of related stolen credentials is two days, which shows a strong indicator that ransomware operators leverage stealer malware.
Take the example of Active Directory credentials. Active Directory (AD) is Microsoft’s directory service for Windows domain networks. Because AD validates user credentials and determines their access rights to network resources, it’s particularly dangerous for AD credentials to be compromised — attackers can potentially gain full control over an organization’s entire IT infrastructure.
Unfortunately, AD credentials have found their way into stealer logs. In 2024, Flare discovered 569,892 stealer logs containing at least one AD access credential, compromising more than 13,000 unique organizations.
Certain infostealer families appear to target Active Directory Federated Services (ADFS) credentials. In 2024, Flare found that Lumma, StealC, and Redline accounted for 82.5% of all recorded logs with ADFS, although Risepro, Vidar, and Bradmax were also responsible for some of the ADFS logs.
The commodification of ransomware groups
Ransomware groups are growing in sophistication and operating more like legitimate companies. For example, many groups employ:
- A mission-oriented approache
- Recruitment practices to seek new hires
- Specialization
- Affiliate vetting and recruiting
For example, the Karakurt group, after operating privately for a year, published a recruitment post to attract new members. They pride themselves on their mission to hold companies accountable for existing vulnerabilities in their cybersecurity and for the negligence of their IT staff. These groups can be driven by both financial and political motives, often influenced by the shifting landscape of geopolitics, and they’re open about their reasoning — many groups release press-style Q&As explaining their missions and engage in other public relations or marketing.
In general, there are two distinct types of specialization within such groups. Similar to a company with various departments, a group may have internal specialization. For instance, within a ransomware group, some members might excel in negotiating the ransom, while others primarily focus on developing malware. Another form of specialization involves individual groups having their own areas of expertise, akin to specialized agencies within a larger company. One group might concentrate on distributing ransomware, collaborating with another group that specializes in extortion.
This organized and specialized collaboration among groups can lead to more intricate and scalable operations compared to individual threat actors.
Concrete Recommendations to Protect Against Ransomware
Ransomware is on the rise; according to Verizon’s latest Data Breach Investigation Report (DBIR), ransomware was present in 44% of breaches up from 32% the year before. However, there are ransomware readiness steps you can take to protect your organization:
- Detection: Ensure that users have MFA, and utilize endpoint detection & response (EDR) to detect any type of attack internally and externally.
- Third party monitoring: Conduct an assessment before beginning a new relationship with a business, and also continuously monitor the third party’s security posturing.
- Ransomware group monitoring: Keeping an eye on ransomware groups and any file listings that seem relevant can be useful to find out earlier about any risks instead of waiting to be notified by the third party. For example, we’ve seen a success story of a company that had been monitoring ransomware groups and knew three weeks in advance that one of their third party partners had been compromised by ransomware before they received a legal disclosure notice from said partner. This can provide more time for affected organizations to review the data they were sending to the breached third party and start addressing the data leak.
- Monitor the dark web: Ensure that you monitor dark web markets and forums for stolen credentials and other relevant threats that could lead to a breach.
Monitor for External Threats with Flare
The Flare threat intelligence solution empowers organizations to proactively detect, prioritize, and mitigate the types of exposures commonly exploited by threat actors. Our platform automatically scans the clear & dark web and prominent threat actor communities 24/7 to discover unknown events, prioritize risks, and deliver actionable intelligence you can use instantly to improve security.
Flare integrates into your security program in 30 minutes and often replaces several SaaS and open source tools. See what external threats are exposed for your organization by signing up for our free trial. Check out ransomware risks across your supply chain with a demo.




