
This article was updated on October 2, 2025 with updated information
As cyber threats continue to evolve in complexity and frequency, staying informed about the latest trends and emerging threats is crucial for cybersecurity professionals. One effective way to do this is by monitoring relevant cybercrime forums, where threat actors often discuss new tactics, techniques, and tools.
We’ve put together the most significant cybercrime forums to monitor in 2025 so security teams can use the information to improve their threat detection and response activities.
What Can Security Teams Gain from Monitoring Forums?
Many cybercrime forums operate on the dark web, using the Tor network to conceal their location and the identities of their participants.
However, some forums are also accessible on the clear web, often requiring registration and approval by the forum’s administrators. To maintain a low profile, these forums may ask for a registration, which can be free, paid, or reputation based.
For closed forums, which are in the minority, there are usually two options: reputation-based registration or paid registration (if a member does not want to provide information about themselves).
Threat actors complement their behavior on cybercrime forums through messaging on illicit channels on Telegram, which is also valuable to monitor. Illicit Telegram channels have become a key tool that complements cybercrime forums, extending discussions beyond static threads into fast, interactive spaces. While forums remain central for reputation building, escrow services, and structured marketplace activity, many threat actors rely heavily and sometimes exclusively on Telegram for real-time coordination, private sales, and closed group operations. This means that both forums and Telegram channels must be monitored to gain a full picture of the threat landscape.
Keeping track of these forums and analyzing the information that cybercriminals share can provide insights into the tactics, techniques, and procedures (TTPs) that threat actors use.
Exploit
Exploit, originally known as Hack-All, is one of the oldest and longest-running Russian-language cybercrime forums. Founded in 2005 by the threat actor “toha,” its transfer to a “trusted member of the community” in 2018 was a surprising event that raised many suspicions within the community, as the administrator’s surrender of the forum was unexpected.
Exploit primarily focuses on:
- Sale of data from breaches and leaks
- Sale of initial accesses (to companies IT infrastructures)
- Malware as a service
- Phishing kits, Spam
- Stolen accounts credentials
Despite some user concerns around law enforcement infiltration, Exploit remains an active threat actor forum.
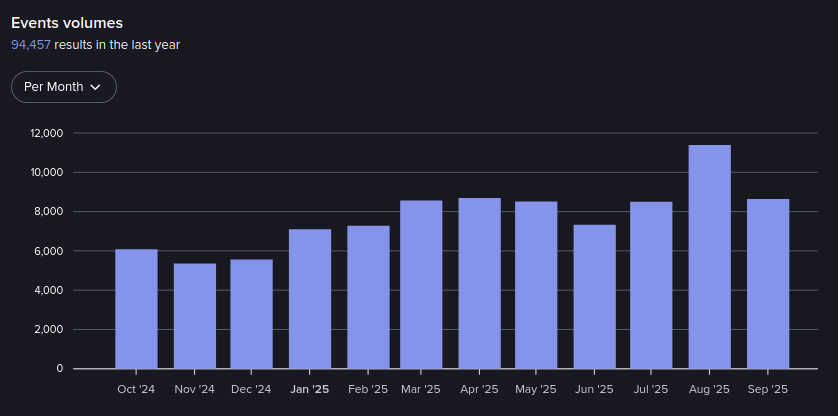
Events in Exploit from October 2024-September 2025 (Source: Flare)
DarkForums
In 2022, the forum launched as “DARK4RMY Forums,” connected to the “D4rk4rmy” (DarkArmy) cybercriminal group. DarkForums appears to have absorbed the BreachForums user base after its April 2025 shutdown, adopting the same design and operational model. As of July 2025, DarkForums activity increased by 600%, indicating its growing prominence in the cybercrime landscape.
Three admins run DarkForums:
- “Lucifer:” Active from the end or 2022 until 2024 resignation, likely based on India, and appearing across multiple underground forums with various emails and handles like “0x1ucif3r,” “iamBOTXD,” and “SamaelX”
- “AnonOne:” Active around the forum’s DarkArmy launch, less active on Telegram, and appearing across multiple forums with various aliases like “Alexa69,” “YourAnonOne,” “HumanError,” “Xolo666,” “LostSec,” and “FlashLethal”
- “Knox:” Active beginning in mid-2023 with a focus on reporting breaches, and taking over admin responsibilities in 2024
Membership operates on a tiered subscription model structure with exclusive access to different areas and content. The forum focuses on the following:
- Sharing and selling compromised databases, including personal identifiable information (PII)
- Trading in malware tools and exploit kits
- Offering various tools for cyberattacks
- Selling access credentials and logs
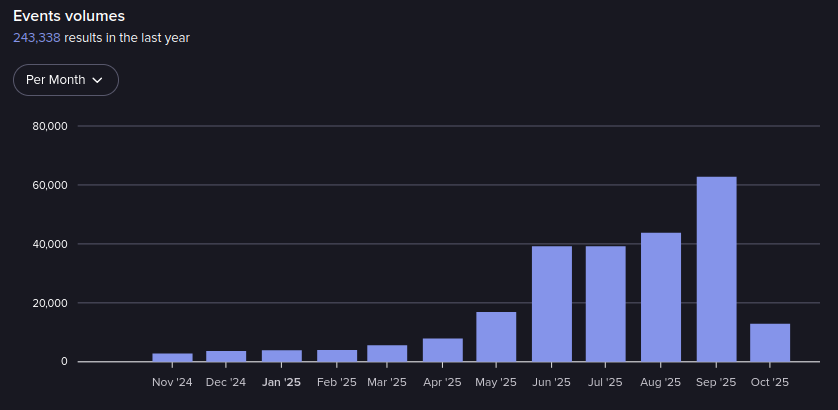
Events in DarkForums from November 2024-October 2025 (Source: Flare)
XSS
XSS’s story begins in 2004 when the forum was a personal project of its first owner called “whost.” Then named DaMaGeLaB the forum was later passed into the hands of the Belarusian threat actor “Ar3s,” who was also the creator of the Andromeda botnet. In 2017, Sergey Yarets aka “Ar3s” was arrested by Belarusian police, leading to DaMaGeLaB’s closure. The forum’s database was then acquired by “toha,” a former administrator of Exploit, in 2018. “Toha” subsequently used this database to launch XSS, a new forum that took over from DaMaGeLaB.
The forums quickly became a central hub for Russian-speaking cybercriminals and attracted global participants. This high level of activity led to a joint police operation in July 2025 involving French, Ukrainian, and Europol authorities. The operation resulted in the arrest of an individual known online as “admin” and “toha.” In August 2025, reports suggested that the admin’s real identity might be 37-year-old Anton Gannadievich Medvedovskiy. Authorities have not yet officially confirmed the cybercriminal’s identity, who is believed to have made at least $7 million from ransomware-related transactions on the forum.
Even today, the forum continues its activities under a new unknown administrator. XSS focuses primarily on the following:
- Credential sales
- Spam
- Phishing
- Malware
- Initial access sale
- Exploit trading
- Data leaks
The forum was linked to high-profile ransomware groups, including REvil, LockBit, and Conti. The admin’s arrest created upheaval and suspicion, leading to traffic and user declines. Recent user bans and disputes over blocked cryptocurrency funds fuel fears that XSS has become a law enforcement honeypot.
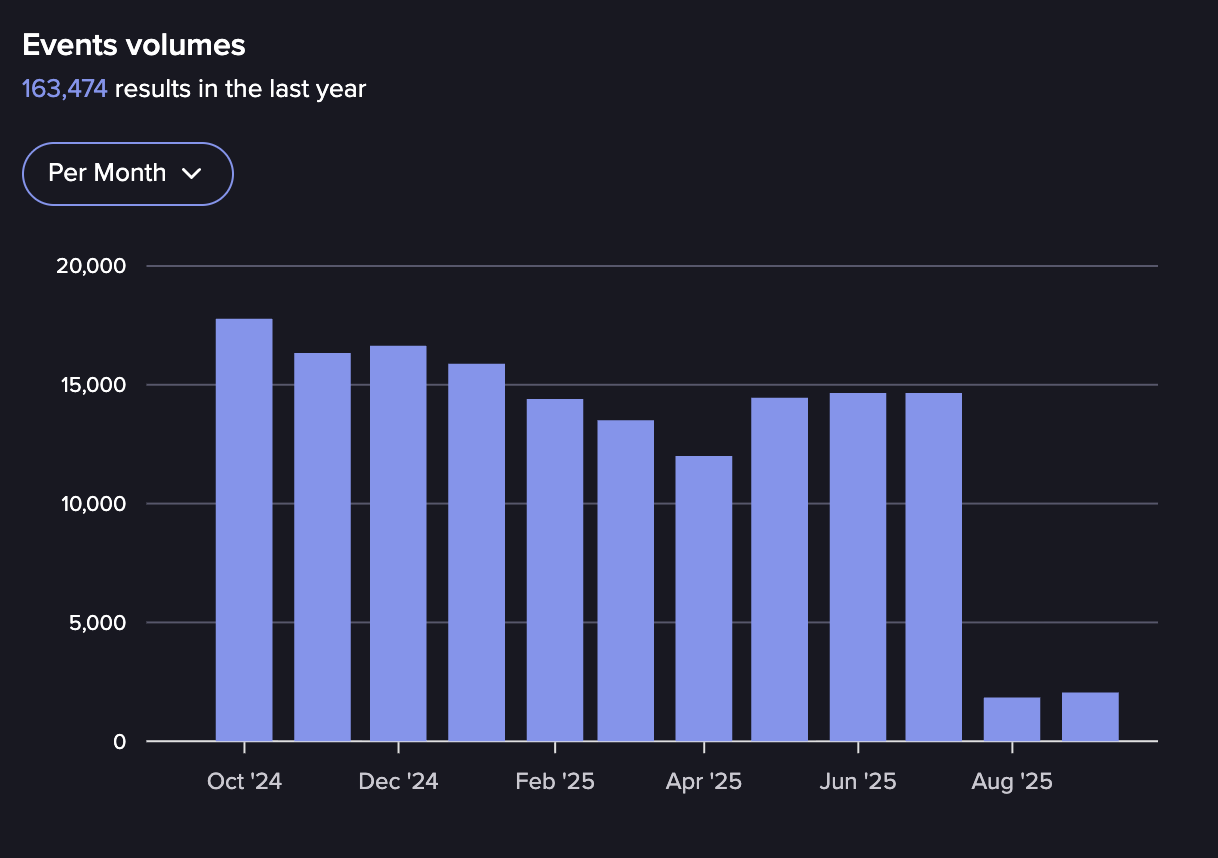
Events in XSS from October 2024-September 2025 (Source: Flare)
DamageLib
DamageLib arose from the ashes of XSS, launching in August 2025. Run by former XSS moderators who distrust the new administrator of XSS, the forum claims that it will not track users, holding itself as a secure, privacy-focused forum as it can be accessed only on Tor network. The new community does not offer a dedicated marketplace and escrow warranty system, which could hinder its future development.
DamageLib offers:
- Hacking tutorials
- Malware development tutorials
- Exploits and vulnerabilities related discussions
- Indirect sale of MaaS, databases, etc
Despite porting over the XSS forum content and user base, the forum’s activity engagement remains lower as it continues to suffer from trust issues related to XSS’s demise.
DamageLib’s focus is currently harder to assess because the admins have decided to not create any commercial sections, and there is no marketplace. That is also why engagement remains rather low while the number of registered accounts is at 33,962.
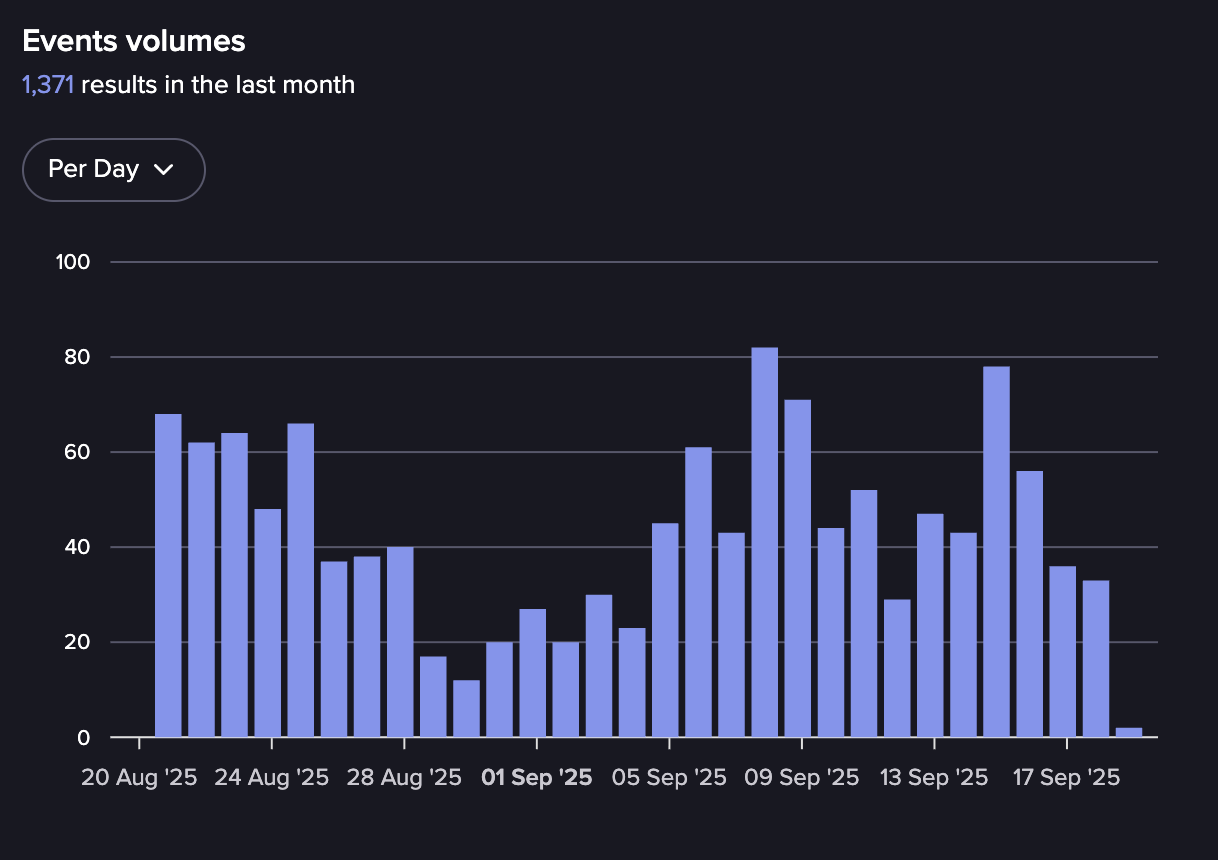
Events in DamageLib from August-September 2025 (Source: Flare)
Leakbase
Administrated by the threat actor “Chucky” since 2021, the forum focuses almost exclusively on sale and distribution of databases, credentials and other leaks. “Chucky” also appears linked to three other usernames, “LeakBase”, “Chuckies”, and “Sqlrip”. The “LeakBase” alias, that was active on BreachForum, is linked to the Swachh City breach impacting approximately 16 million user PII records in September, 2022.
The English-language forum Leakbase uses a subscription model to disseminate content focusing on:
- Sale and sharing of credentials and log, including stolen admin credentials, website back-end logins, and server access
- Database dumps of personally identifiable information (PII), including emails, usernames, hashed passwords, and phone numbers
- General leak information, including breach announcements
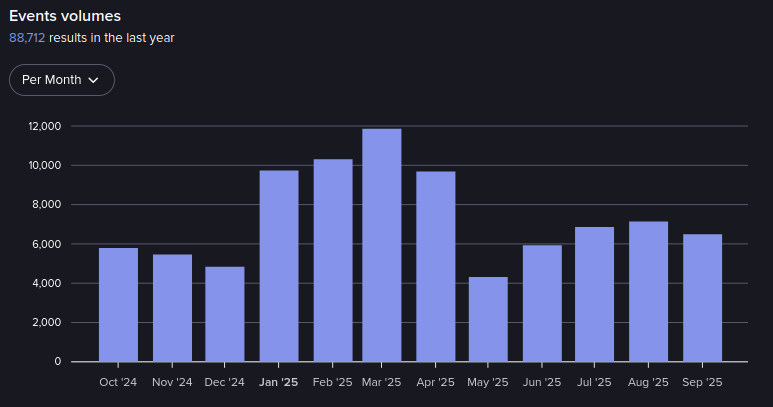
Events in Leakbase from October 2024-September 2025 (Source: Flare)
RAMP
Launched in 2012, RAMP was a long-standing dark web drugs focused marketplaces inspired by Silk Road and run by the threat actor “Darkside”. By 2017 this market attracted the attention of the Russian police who conducted an operation to terminate its existence in July 2017.
The RAMP forum emerged in July 2021 as RAMP 2.0 and was launched on the same domain previously utilized by the Babuk ransomware data leak site and subsequently the Payload.bin data leak site. The forum was founded as a response to the ban on discussions and advertisement related to ransomware on other major Russian-language forums after the Colonial Pipeline attacks.
The first owner, linked to Babuk RaaS, was the threat actor Wazawaka (Mikhail Matveev), who later passed the ownership to Kajit. Kajit eventually had to give away the forum to the threat actor Stallman, who is the administrator up to this day. RAMP 2.0 functions as a cybercriminal membership forum, offering services such as the advertisement of RaaS groups and initial access to corporate environments. It attracts a diverse user base, including Russian, English and Chinese speaking threat actors.
RAMP 2.0 focuses on:
- Ransomware
- Initial access broker (IAB) services
- Exploits
- Malware
- Sharing information
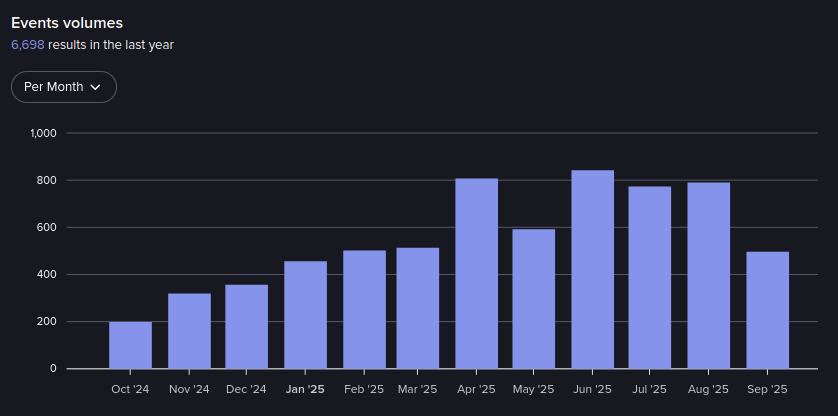
Events in RAMP from October 2024-September 2025 (Source: Flare)
Duty Free
In late March 2025, the IT Army of Russia began using Duty Free’s forums and its DutyNews Telegram channel to broadcast operations. The DutyNews Telegram channel appears to replicate content posts from the forum. Currently, no public and credible reports or datasets provide insight into forum admin, founders, owners, or activity.
Duty Free primarily focuses on:
- Recruiting cybercriminals to target Ukrainian infrastructure and telecommunications
- Conducting Distributed Denial of Service (DDoS) attacks
- Publishing leaked data
- Openly authorizing ransomware related discussions and RaaS advertisement
Currently, Duty Free appears to be a location filling in the cybercrime forum gap left after the arrest of XSS’s admin. The forum is a copy of the structure of XSS, and they openly accept RaaS groups (which is bold).
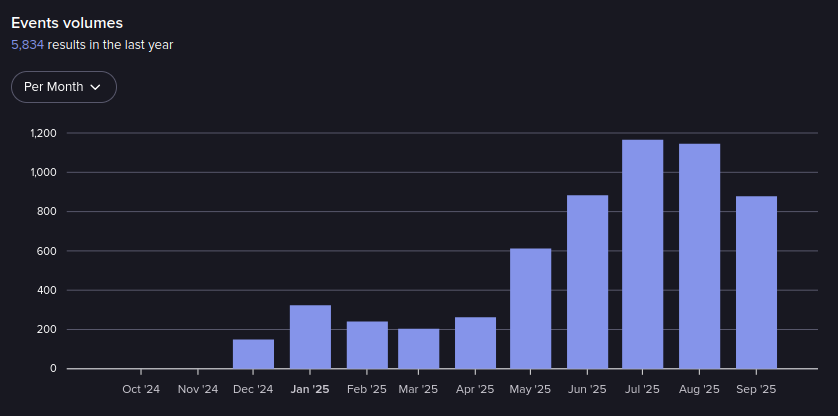
Events in Duty Free from October 2024-September 2025 (Source: Flare)
Best Hack Forum (BHF)
Active since 2012, BHF is one of the more established Russian-language forums mainly focusing on credentials sale, spam and dataleaks.
BHF primarily focuses on:
- Software cracking
- Exploits
- Combolists
- Stealers logs
- Spam tools
- Tutorials
The presence of bots, Telegram integrations, and escrow services highlights that BHF offers sophisticated operations and higher-value transactions.
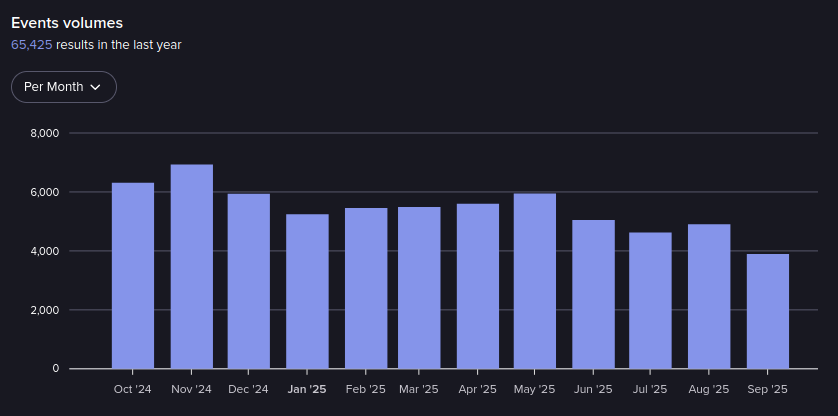
Events in BHF from October 2024-September 2025 (Source: Flare)
Lolzteam
Around 2013, a user known as both Grisha Sutchkov and Zelenka appeared to have founded Lolzteam, also referred to as LolzTeam. Initially, the forum focused on gaming, video game cheating, and in-game items. Over time, activities took on a criminal element, including theft and fraud. Lolzteam serves as a common entry point for young individuals venturing consciously or unconsciously into cybercrime. Its low barrier to entry makes it a de facto starting point for those engaging in low-level scams and frauds to earn small sums of money.
The Lolzteam marketplace remains active, focusing on gaming and social media logins. In 2025, the market is one of the larger platforms for buying and selling these accounts, providing account validation and guarantees. The current membership appears to be hundreds of thousands of daily users, with most between the ages of 16 and 25.
Lolzteam focuses on the following:
- Account and credential sales, typically for social and gaming platforms
- “Traffers,” malicious actors who distribute malicious content by using compromised accounts
- Infostealer malware
- Social engineering tutorials
- Game cheating, including game cheating tools, in-game items, and loot
Finally, the forum’s dedicated market includes the following features that indicate a high maturity level:
- Verified or vetted sellers
- Guarantees for accounts
Reputation systems - Escrow
Lolzteam has experienced two significant breaches:
- December 2014: Exposing approximately 25,000 users’ data, including usernames, emails, and genders
- May 2018: Exposing 398,000-400,000 accounts whose data was later released on another cybercriminal forum, including usernames and email addresses
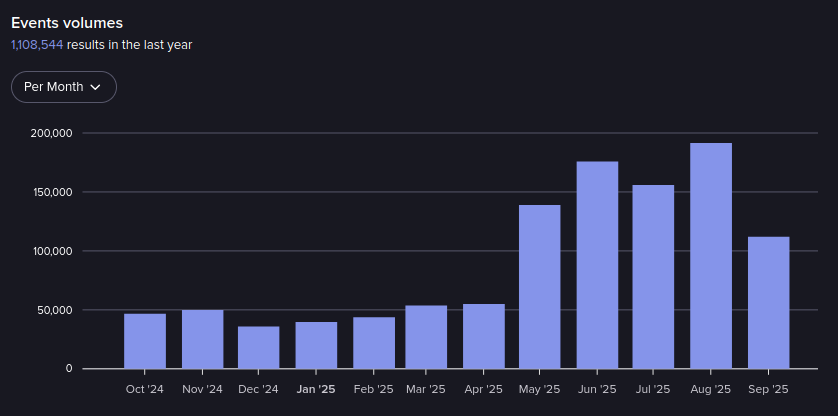
Events in Lolzteam from October 2024-September 2025 (Source: Flare)
Altenen
Originally established as an Arabic-language platform in 2008, Altenen transitioned to English, likely to broaden its reach. In May 2018, law enforcement arrested the forum’s founder but released little information about the person’s identity. This arrest led to a brief shut down until new admins revived it in June 2018.
As part of account activation, Altenen requires users to share the forum’s domains on social media. The forum uses a tiered membership model, providing different levels of access to content. The forum primarily focuses on the following:
- Sharing techniques and tools for carding and financial fraud
- Discussions on software cracking, methods for gaining unauthorized access, and related tools
- Exchanging information on various online scams and fraudulent activities
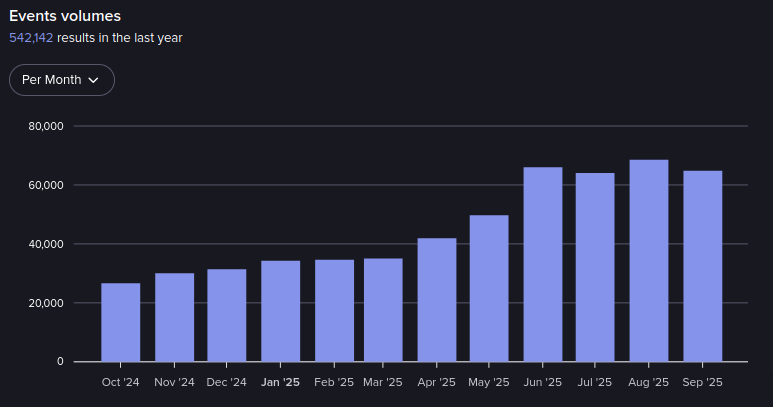
Events in Altenen from October 2024-September 2025 (Source: Flare)
WWH Club
WWH-Club is a carding and financial fraud focused community that has operated since 2014. In 2024 two of its moderators, Alex Khodyrev and Pavel Kublitskii, were arrested in the United States. According to the Department of Justice they have also participated in several other dark web marketplaces, forums, and training centers.
WWH Club focused primarily on the following:
- Stolen PII, including social security numbers and credit report data
- Payment card dumps
- Login credentials
- Tutorials and training for committing fraud
- Tools for carding
Finally the market included the following features that indicated a high maturity level:
- Membership fees
- Charges for training or tuition
- Vendor marketplaces
As a cybercrime forum providing educational opportunities, it became an onboarding channel for new threat actors.
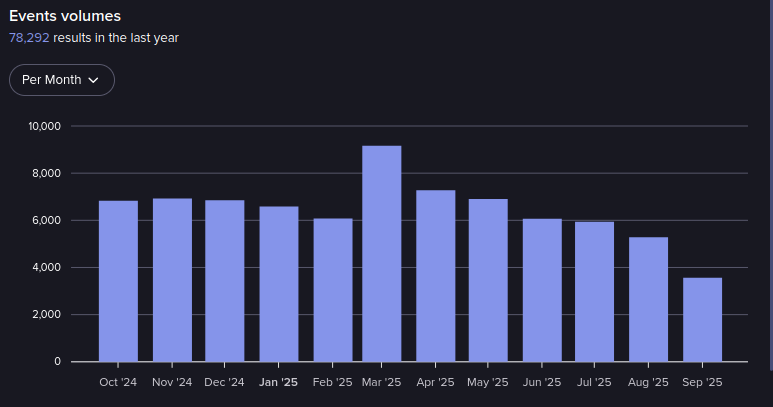
Events in WWH Club from October 2024-September 2025 (Source: Flare)
DarkNetArmy
In 2022, the forum launched publicly as DarkNetArmy Forums, linked to the broader “DarkNetArmy” (DNA) cybercriminal community previously operating across Telegram and smaller boards. The site established both a clearnet domain, darknetarmy.io, and a Tor mirror, darknetarmy.onion. DarkNetArmy has grown in visibility due to its active vendor threads and multilingual user base. By mid-2025, DarkNetArmy displayed a marked increase in postings around commodity malware and cracked RAT builds, suggesting its consolidation as a mid-tier underground market.
DarkNetArmy’s membership model combines free access with tiered vendor privileges based on reputation and feedback. Typically, transactions occur outside of the forum, across Telegram, PGP-encrypted email, and cryptocurrency wallets.
The forum focuses on the following:
- Malware distribution, like RATs such as 888 RAT, cracked malware builders, and loaders
- Bulk combo lists and validated account credentials across gaming, social, and financial platforms
- Proof-of-concept exploits, OpenBullet configs, and access brokers offering compromised admin panels
- DDoS rentals, phishing kits, and bulletproof hosting options
- Guides and “how-to” threads enabling entry-level cybercrime participation
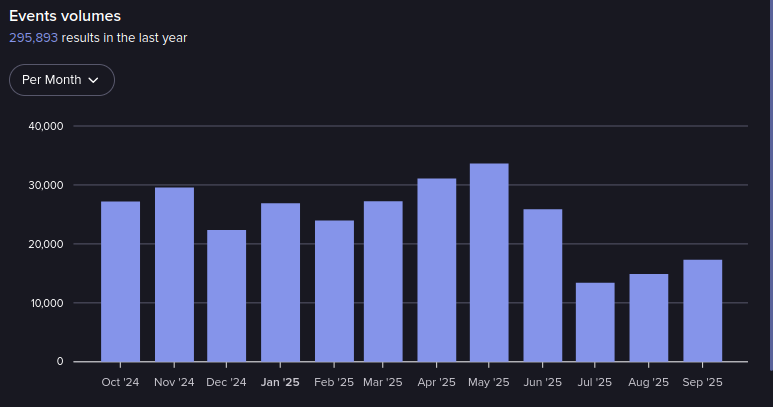
Events in DarkNet Army from October 2024-September 2025 (Source: Flare)
Dread
In 2018, administrators with usernames HugBunter and Paris launched Dread with a Reddit-like structure and community-based approach. In May 2019, a Wall Street Market moderator posted a hidden IP address to Dread, implicating the forum in what would be an exit scam and seizure. A few months later in September 2019, the forum experienced a service outage that staff indicated might have been related to HugBunter’s health or equipment malfunctions triggered the security system.
In November, the site went live again with a new user interface. Dread hosts a variety of sub-forums, known as “subdreads,” focusing on the following:
- Trading of stolen usernames, passwords, and other sensitive information
- Discussions and coordination of ransomware operations
- Sharing and distribution of malicious software tools
- Information and updates on the status of various darknet markets
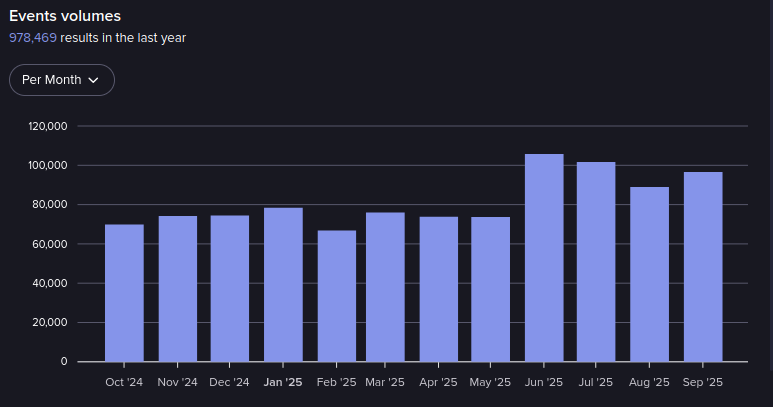
Events in Dread Army from October 2024-September 2025 (Source: Flare)
Hackforums (HF)
In 2007, an admin with the alias “Omniscient” launched Hackforums using a traditional forums structure that dedicated various sections to different topics.
The forum operates on a structure that defines members levels or access based on user activity, reputation, or occasional invite-only sections. The forum offers free registration with open access to most areas, though certain boards or features may require higher trust levels gained through forum participation or manual moderator approvals.
Hackforums has been linked to the following:
- Limitless Logger Pro (2013): Keylogger for stealing sensitive information
- SSH brute-force (2013): Targeting Linux system with weak passwords
- Blackshades RAT (2014): Remote administration tool created and sold on the forum
- MegalodonHTTP Botnet (2016): Malware including features like binary downloading and executing, DDoS, remote shell, antivirus disabling, cryptomining
- Mirai malware (2016): Malware targeting Internet of Things (IoT) devices published as open-source on the forum
- NanoCore RAT and Net Seal (2018): Exclusively marketed by Avalanche cybercrime organizer Gennady Kapkanov
- LuminosityLink (2018): FBI identifying user data linked to the malware
Hackforums focuses on the following:
- Discussions on various hacking techniques and tools
- Topics related to securing systems and networks
- Sale of malware, stolen credentials, and other illegal services
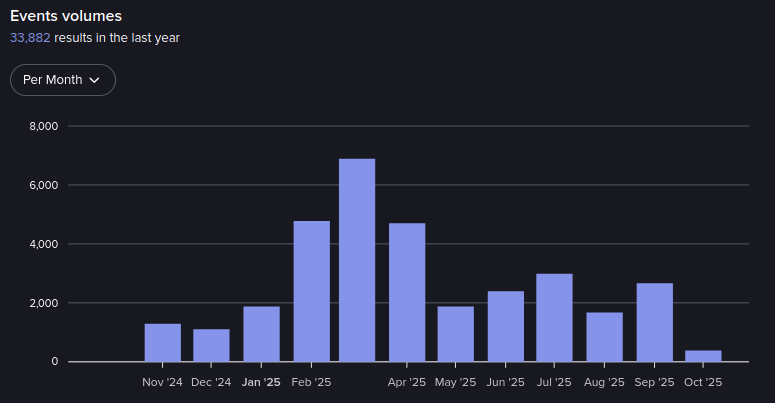
Events in Hack Forums from November 2024-October 2025 (Source: Flare)
Cracking[.]org
In the mid-2010, a user with the alias “Jacob” established Cracking[.]org using a traditional forum structure that dedicated various sections to different topics. In March 2018, Cracked[.]org began focusing on cybercrime and fraud, ultimately gaining up to over four million users across 28 million posts. The forums generated approximately $4 million in revenue and impacted at least 17 million victims.
Cracking[.]org may have ties to other forums, Cracked[.]to and Nulled, based on shared users and administrative cooperations. In early 2025, the coordinated FBI and Europol takesdown of Cracked.[]org and Nulled led many users to migrate to other forums, Telegrams, or Discord channels.
Most discussions and marketplace access on Cracking[.]org seem to rely on user reputation, activity, and invitation. Cracked[.]org focuses on the following:
- Sharing news about recent data breaches and security vulnerabilities
- Discussions and tools related to breaking into online accounts
- Sharing and distribution of malicious software tools
- Sale and exchange of compromised information
Generally, it functions as a hub for low to medium-tier threat actors looking to buy affordable tools and stolen data or learn hacking skills.
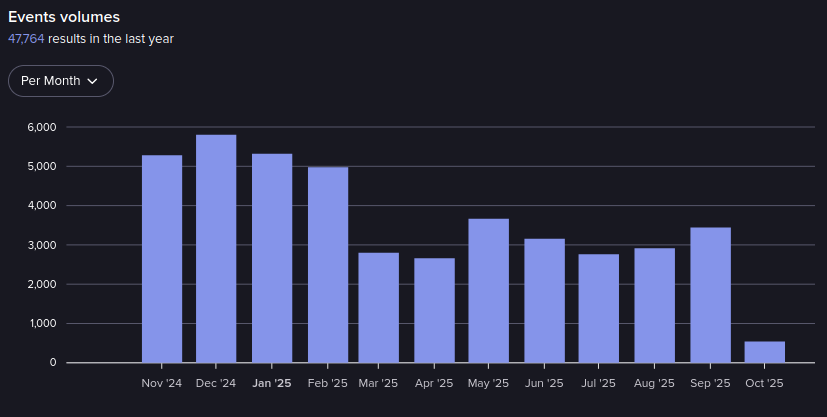
Events in Cracking[.]org from November 2024-October 2025 (Source: Flare)
HydraForums
HydraForums describes itself as a database sharing and marketplace forum. The name likely derives from Hydra Market, a major Russian darknet market that shut down in 2022 following international law enforcement operations.
The site has multiple sections, including:
- VIP area: Public and private database leaks, logs, combolists, credit card information, cracked accounts, tutorial and guides
- Free leaks: Database, log, combolists, leaked documents and passports, free software source code, credit card information
- Hacking and security: Web hacking, phone hacking, social media hacking, vulnerabilities and exploits
- Cracking: Combolist tools, cracked accounts, configurations for tools, like OpenBullet.
- Penetration and attack area: Web application exploits, botnets, DDoS attacks, and vulnerabilities like SQL, cross-site scripting (XSS), and cross-site request forgery (CSRF)
- Trader Area and Buy-Sell: Advice on contacting an admin for security transactions or escrow
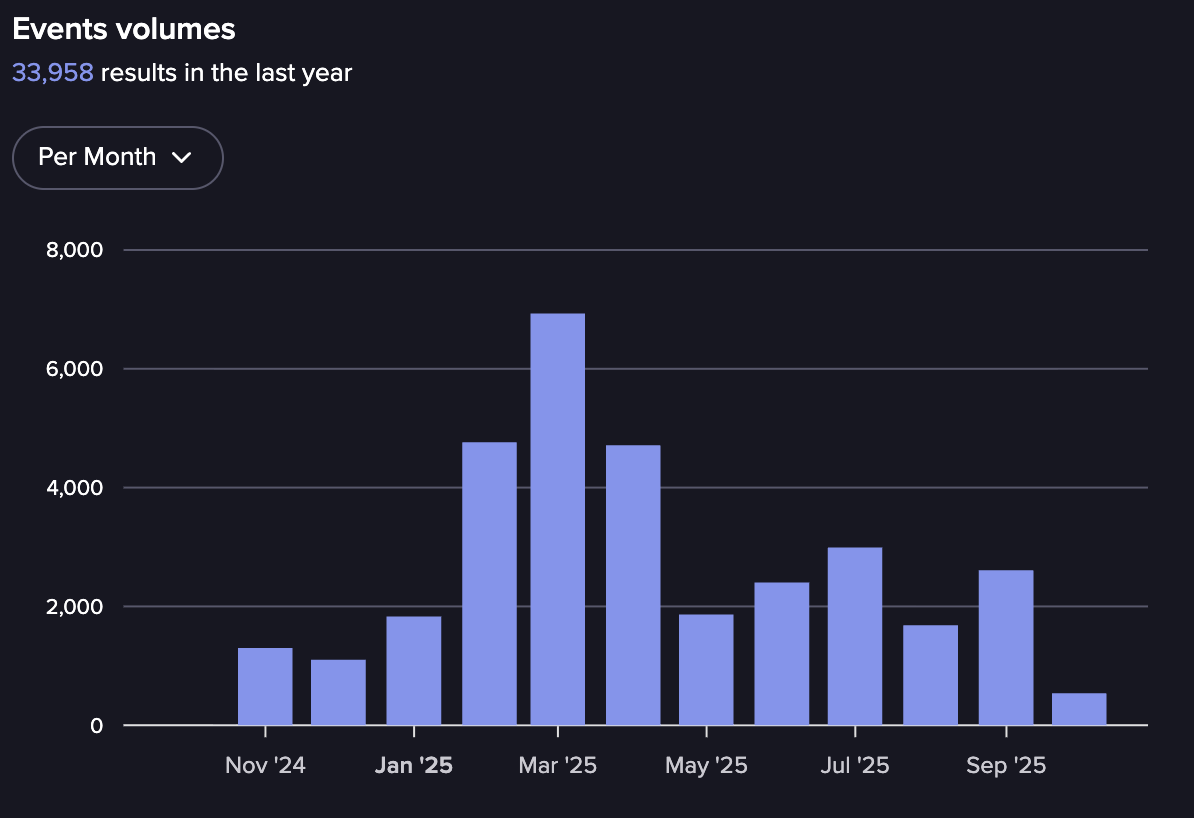
Events in HydraForums from November 2024-October 2025 (Source: Flare)
Best Practices for Monitoring and Analyzing Cybercrime Forums
Effectively monitoring and analyzing cybercrime forums is essential for gaining valuable insights into threat actor TTPs. By following some best practices, security analysts maximize the benefits of this intelligence-gathering process.
Prioritize Targeted Cybercrime Forums
Focus your efforts on monitoring forums that are most relevant to your organization’s industry, geographical location, and specific threat landscape. This will enable you to gather the most pertinent intelligence and better allocate your resources.
Use a Systematic Approach
Developing a structured approach for monitoring and analyzing forum content may include:
- Setting up regular intervals for checking forums
- Categorizing information based on specific criteria
- Using automated tools to assist with data collection and analysis.
Preserve Anonymity and Security
When accessing cybercrime forums, maintain your anonymity and security by using technologies like:
- A VPN
- Tor network
- Anonymizing tools to protect your IP address and identity.
Additionally, ensure that your device is up-to-date with the latest security patches and that you’re using a secure, isolated environment to access potentially malicious content.
Collaborate with Peers and Share Intelligence
Cyber threat intelligence is most effective when shared among professionals and organizations so you can consider:
- Engaging with industry peers
- Participating in threat intelligence sharing platforms
- Sharing findings and insights with the broader community
Continuously Refine Your Monitoring Strategy
A monitoring strategy should evolve parallel to the cyber threat landscape evolves which means:
- Regularly reviewing and updating the approach
- Incorporating new forums and threat actors
- Identifying trends as they emerge
This will help you stay ahead of the curve and maintain a comprehensive understanding of the cybercrime ecosystem.
Integrate Intelligence into Your Cybersecurity Strategy
Integrating intelligence into the cybersecurity strategy enables you to take action on it, including using it for
- Informing proactive defense measures
- Threat hunting
- Improving incident response processes
- Augmenting risk management processes
Monitoring Cybercrime Forums with Flare
The Flare Threat Exposure Management solution empowers organizations to proactively detect, prioritize, and mitigate the types of exposures commonly exploited by threat actors. Our platform automatically scans the clear & dark web and prominent threat actor communities 24/7 to discover unknown events, prioritize risks, and deliver actionable intelligence you can use instantly to improve security.
Flare integrates into your security program in 30 minutes and often replaces several SaaS and open source tools. See what external threats are exposed for your organization by signing up for our free trial.





