
This article was updated on October 3rd, 2025.
Cybercrime forums provide an outlet for threat actors to coordinate, expose sensitive data, and conduct illicit trades. These forums are often accessible on the clear web, though registration is typically required. Some have a presence on both the clear and dark web, with a smaller number of exclusive communities existing only on the dark web.
The typical structure of a cybercrime forum sees a dedicated marketplace section that facilitates the sale of stolen credentials, databases, CVE exploits, 0-days/1-days, malware as a service, initial access brokers, carding, phishing kits, spam, bullet proof hosting, crypto laundering, and more.
Russian-language cybercrime forums remain a space for illicit activities including for-profit cybercrime and state-sponsored cyber warfare. For example, as of May 2025, at least 44 crypto-focused money laundering services are active on top Russian-language forums, offering crypto swaps, mixing, and cash deliveries.
Monitoring cybercrime forums to see if malicious actors mention an organization’s name can provide insight into an impending attack or reveal credentials for sale that include the organization’s domain.
We’ve put together the top Russian-speaking cybercrime forums to monitor.
Top Russian-Language Cybercrime Forums
As threat actors continue to create new cybercrime forums, monitoring the entirety of the dark web can be overwhelming and time-consuming. To focus monitoring activities, security teams can start with the following Russian-language cybercrime forums.
Exploit
Exploit, originally known as Hack-All, is one of the oldest and longest-running Russian-language cybercrime forums. Founded in 2005 by the threat actor “toha,” its transfer to a “trusted member of the community” in 2018 was a surprising event that raised many suspicions within the community, as the administrator’s surrender of the forum was unexpected.
Exploit primarily focuses on:
- Sale of data from breaches and leaks
- Sale of initial accesses (to companies IT infrastructures)
- Malware as a service
- Phishing kits
- Spam
- Stolen accounts credentials
Despite some user concerns around law enforcement infiltration, Exploit remains an active threat actor forum.
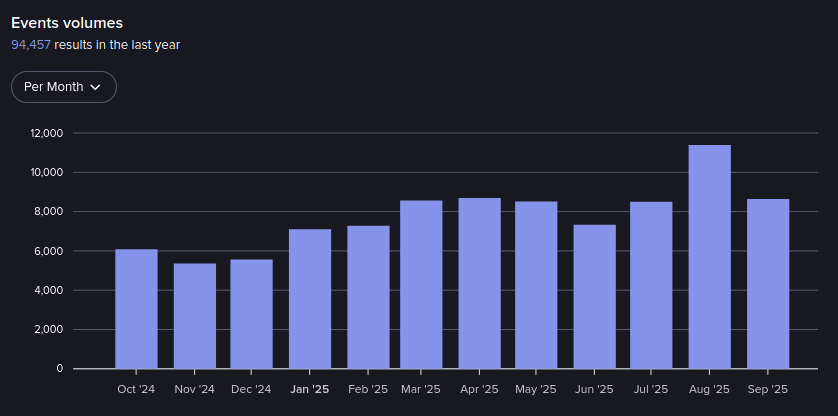
Events in Exploit.in from October 2024 – September 2025 (Source: Flare)
XSS
XSS’s story begins in 2004 when the forum was a personal project of its first owner called “whost.” Then named DaMaGeLaB, the forum was later passed into the hands of the Belarusian threat actor “Ar3s”, who was also the creator of the Andromeda botnet. In 2017, Sergey Yarets a.k.a. “Ar3s” was arrested by Belarusian police, leading to DaMaGeLaB’s closure. The forum’s database was then acquired by “toha,” a former administrator of Exploit, in 2018. “toha” subsequently used this database to launch XSS, a new forum that took over from DaMaGeLaB.
The forums quickly became a central hub for Russian-speaking threat actors and attracted global participants. This high level of activity led to a joint police operation in July 2025 involving French, Ukrainian, and Europol authorities. The operation resulted in the arrest of an individual known online as “admin” and “toha.” In August 2025, reports suggested the admin’s real identity. The authorities have not yet officially confirmed the threat actor’s identity, who is believed to have made at least $7 million from ransomware-related transactions on the forum.
Even today, the forum continues its activities under a new unknown administrator. XSS focuses primarily on the following:
- Credential sales
- Spam
- Phishing
- Malware
- Initial access sale
- Exploit trading
- Data leaks
The forum was linked to high-profile ransomware groups, including REvil, LockBit, and Conti. The admin’s arrest created upheaval and suspicion, leading to traffic and user declines. Recent user bans and disputes over blocked cryptocurrency funds fuel fears that XSS has become a law enforcement honeypot.
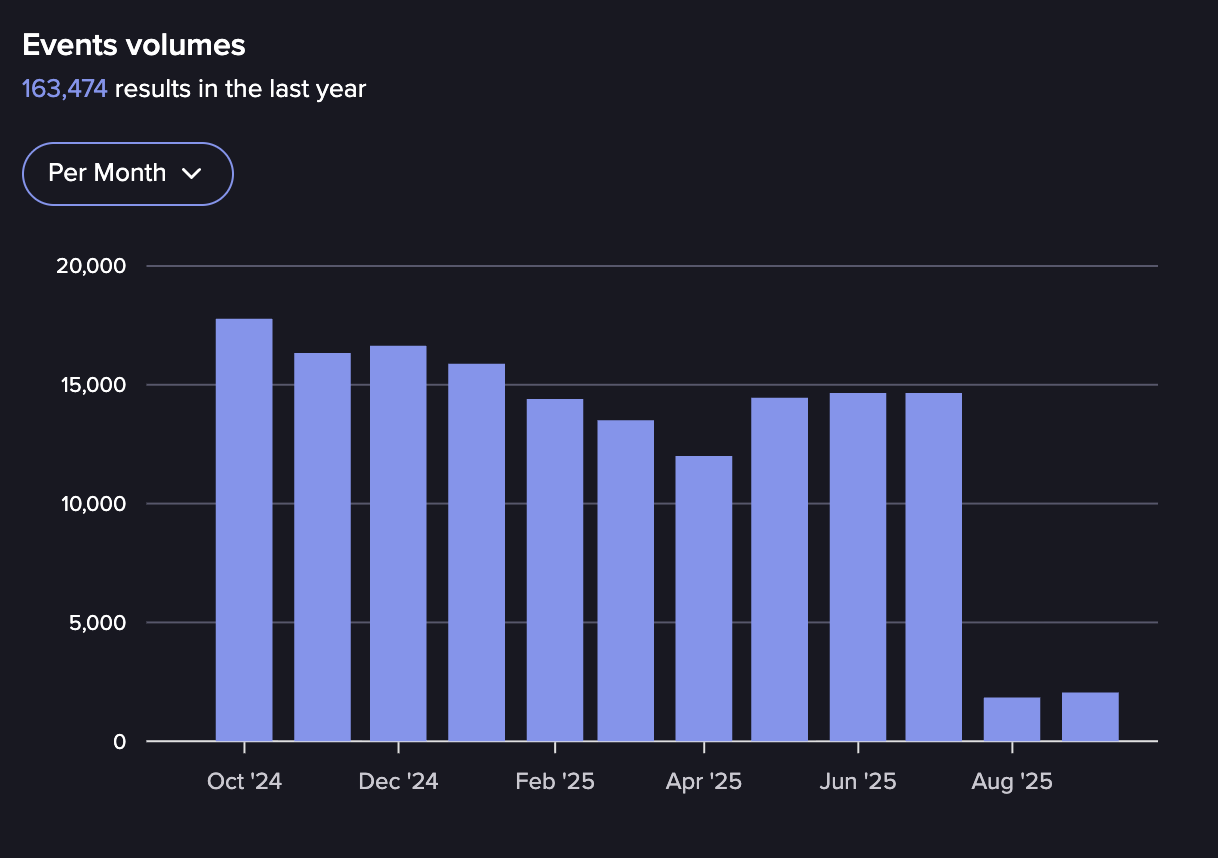
Events in XSS per month October 2024-September 2025 (Source: Flare)
DamageLib
DamageLib arose from the ashes of XSS, launching in August 2025. Run by former XSS moderators who do not trust the new administrator of XSS, the forum claims that it will not track users, holding itself as a secure, privacy-focused forum as it can be accessed only on Tor network. The new community does not offer a dedicated marketplace and escrow warranty system, which could hinder its future development.
DamageLib offers:
- Hacking tutorials
- Malware development tutorials
- Exploits and vulnerabilities related discussions
- Indirect sale of MaaS, data bases, etc
Despite porting over the XSS forum content and user base, the forum’s activity engagement remains lower as it continues to suffer from trust issues related to XSS’s demise.
DamageLib’s focus is currently harder to assess because the admins have decided to not create any commercial sections, and there is no marketplace. That is also why engagement remains rather low while the number of registered accounts is at 33,962.
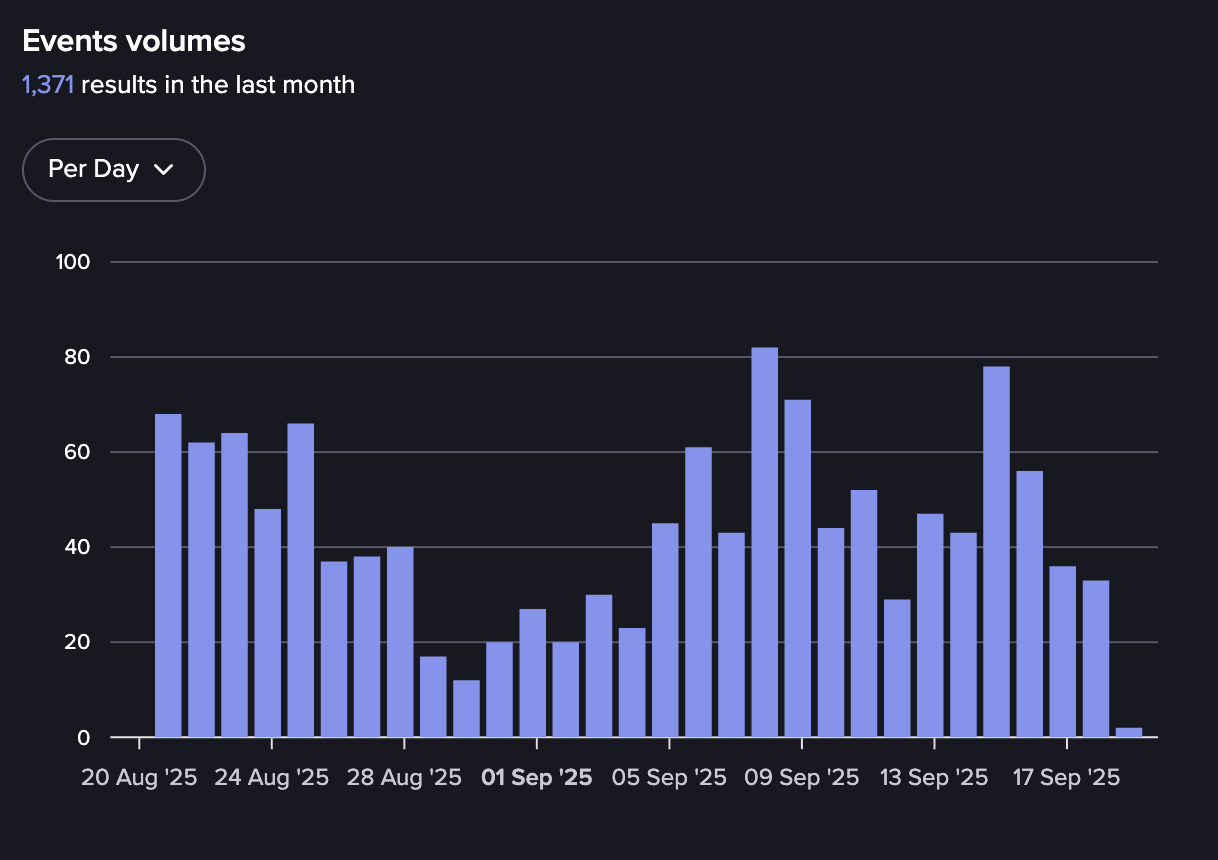
Events in DamageLib from August-September 2025 (Source: Flare)
Duty Free
In late March 2025, the IT Army of Russia began using Duty Free’s forums and its DutyNews Telegram channel to broadcast operations. The DutyNews Telegram channel appears to replicate content posts from the forum. Currently, no public and credible reports or datasets provide insight into forum admin, founders, owners, or activity.
Duty Free primarily focuses on:
- Recruiting threat actors to target Ukrainian infrastructure and telecommunications
- Conducting Distributed Denial of Service (DDoS) attacks
- Publishing leaked data
- Openly authorizing ransomware related discussions and RaaS advertisement
Currently, Duty Free appears to be a location filling in the cybercrime forum gap left after the arrest of XSS’s admin. The forum is a copy of the structure of XSS, and they openly accept RaaS groups (which is bold).
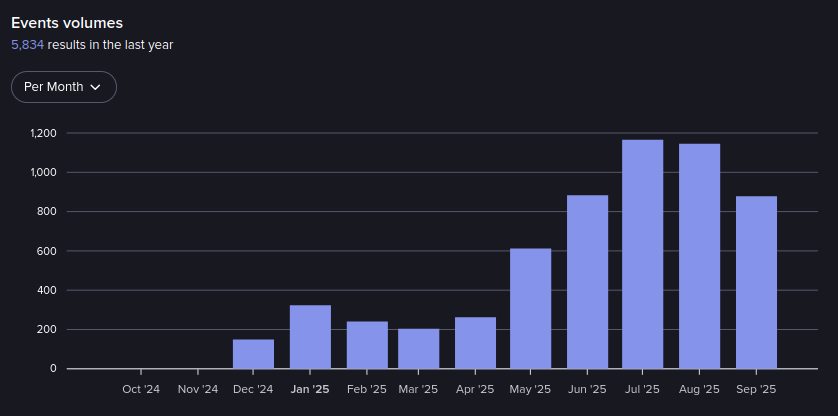
Events in Duty Free from October 2024-September 2025 (Source: Flare)
Best Hack Forum (BHF)
Active since 2012, BHF is one of the more established Russian-language forums mainly focusing on credentials sale, spam and dataleaks.
BHF primarily focuses on:
- Software cracking
- Exploits
- Combolists
- Stealers logs
- Spam tools
- Tutorials
The presence of bots, Telegram integrations, and escrow services highlights that BHF offers sophisticated operations and higher-value transactions.
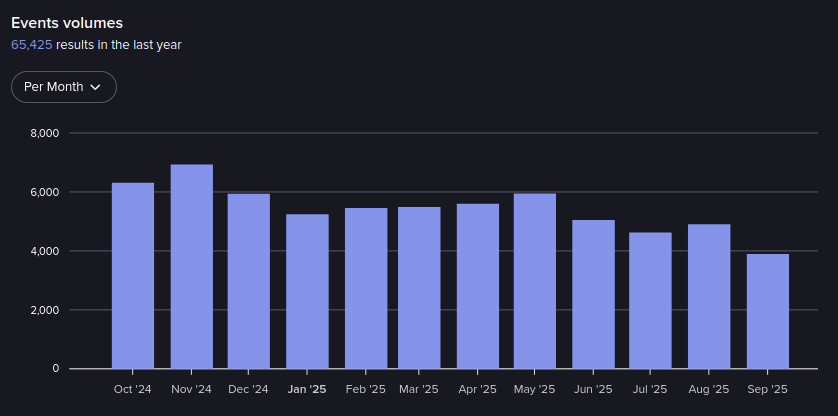
Events in BHF from October 2024 – September 2025 (Source: Flare)
Russian Anonymous Market Place (RAMP)
Launched in 2012, RAMP was a long-standing dark web drugs focused marketplaces inspired by Silk Road and run by the threat actor “Darkside.” By 2017 this market attracted the attention of the Russian police who conducted a takedown operation in July 2017.
The RAMP forum emerged in July 2021 as RAMP 2.0 and was launched on the same domain previously utilized by the Babuk ransomware data leak site and subsequently the Payload.bin data leak site. The forum was founded as a response to the ban on discussions and advertisement related to ransomware on other major Russian-language forums after the Colonial Pipeline attacks.
The first owner, linked to Babuk RaaS, was the threat actor “Wazawaka” (Mikhail Matveev), who later passed the ownership to “Kajit.” “Kajit” eventually had to give away the forum to the threat actor “Stallman,” who is the administrator up to this day. RAMP 2.0 functions as a threat actor membership forum, offering services such as the advertisement of RaaS groups and initial access to corporate environments. It attracts a diverse user base, including Russian, English and Chinese speaking threat actors.
RAMP 2.0 focuses on:
- Ransomware
- Initial access broker (IAB) services
- Exploits
- Malware
- Sharing information
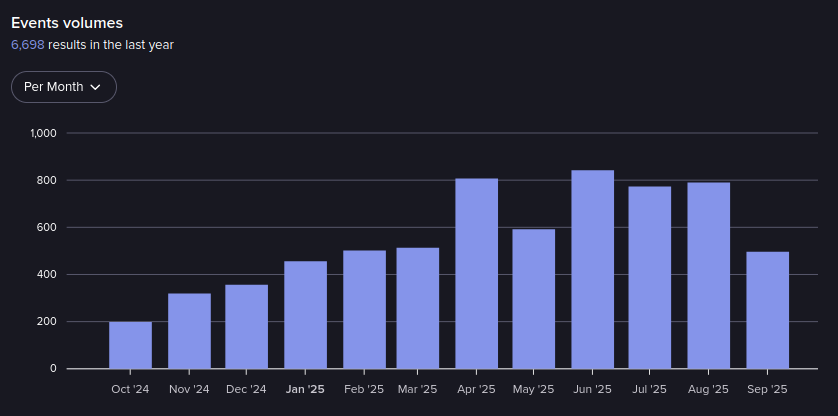
Events in RAMP from October 2024 – September 2025 (Source: Flare)
Lolzteam
Around 2013, a user known as both “Grisha Sutchkov” and “Zelenka” appeared to have founded Lolzteam, also referred to as LolzTeam. Initially, the forum focused on gaming, video game cheating, and in-game items. Over time, activities took on a criminal element, including theft and fraud. Lolzteam serves as a common entry point for young individuals venturing consciously or unconsciously into cybercrime. Its low barrier to entry makes it a de facto starting point for those engaging in low-level scams and frauds to earn small sums of money.
The Lolzteam marketplace remains active, focusing on gaming and social media logins. In 2025, the market is one of the larger platforms for buying and selling these accounts, providing account validation and guarantees. The current membership appears to be hundreds of thousands of daily users, with most between the ages of 16 and 25.
Lolzteam focuses on the following:
- Account and credential sales, typically for social and gaming platforms
- “Traffers,” malicious actors who distribute malicious content by using compromised accounts
- Infostealer malware
- Social engineering tutorials
- Game cheating, including game cheating tools, in-game items, and loot
Finally, the forum’s dedicated market includes the following features that indicate a high maturity level:
- Verified or vetted sellers
- Guarantees for accounts
Reputation systems - Escrow
Lolzteam has experienced two significant breaches:
- December 2014: Exposing approximately 25,000 users’ data, including usernames, emails, and genders
- May 2018: Exposing 398,000-400,000 accounts whose data was later released on another cybercrime forum, including usernames and email addresses
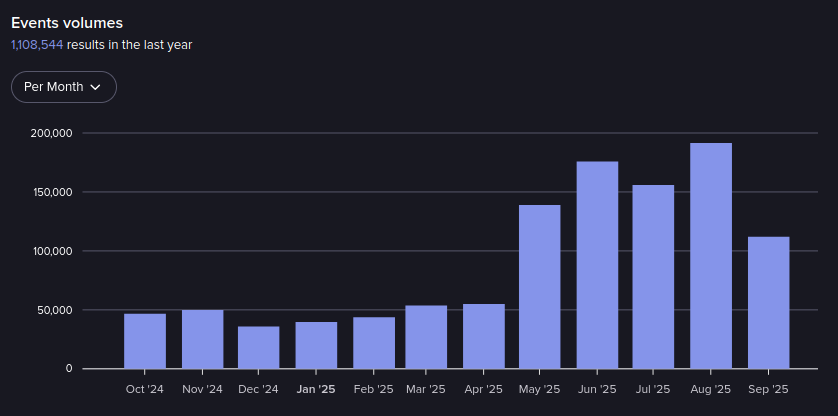
Events in Lolzteam from October 2024 – September 2025 (Source: Flare)
WWH-Club
WWH-Club is a carding and financial fraud focused community that has operated since 2014. In 2024 two of its moderators, Alex Khodyrev and Pavel Kublitskii, were arrested in the United States. According to the Department of Justice they have also participated in several other dark web marketplaces, forums, and training centers.
WWH Club focused primarily on the following:
- Stolen PII, including social security numbers and credit report data
- Payment card dumps
- Login credentials
- Tutorials and training for committing fraud
- Tools for carding
Finally the market included the following features that indicated a high maturity level:
- Membership fees
- Charges for training or tuition
- Vendor marketplaces
This cybercrime forum provides educational opportunities, which serves to onboard new threat actors.
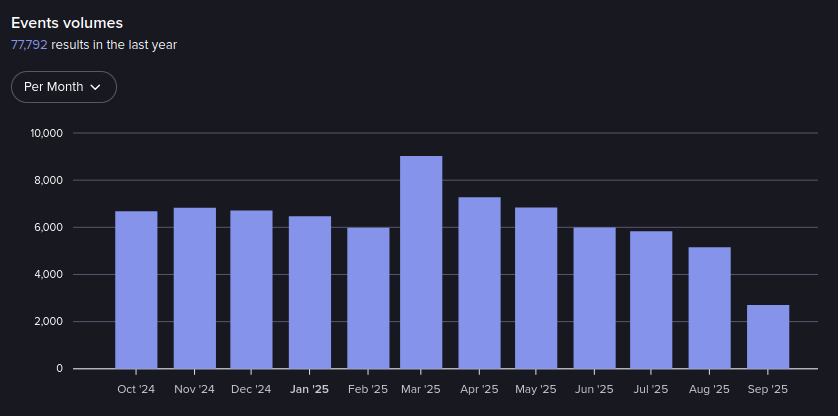
Events in WWH Club from October 2024 – September 2025 (Source: Flare)
Automate Cybercrime Monitoring with Flare
The Flare Threat Exposure Management solution empowers organizations to proactively detect, prioritize, and mitigate the types of exposures commonly exploited by threat actors. Our platform automatically scans the clear & dark web and prominent threat actor communities 24/7 to discover unknown events, prioritize risks, and deliver actionable intelligence you can use instantly to improve security.
Flare integrates into your security program in 30 minutes and often replaces several SaaS and open source tools. See what external threats are exposed for your organization by signing up for our free trial.





