We have identified widespread exploitation of OpenClaw (formerly MoltBot and ClawdBot) AI agents by multiple threat groups in Flare. OpenClaw, an open-source autonomous AI assistant framework created by Peter Steinberger (now of OpenAI) achieved viral adoption in late January 2026, presents a high-severity risk profile due to its design architecture that grants extensive system privileges, persistent memory capabilities, and integration with sensitive messaging platforms and credentials.
Exploitation began within 72 hours of widespread adoption, with threat actors leveraging multiple attack vectors including:
- remote code execution vulnerabilities (CVE-2026-25253, CVSS 8.8)
- supply chain poisoning
- exposed administrative interfaces
- credential harvesting campaigns
Our intelligence indicates over 30,000 exposed instances, with confirmed malicious activity including API key theft, multi-platform message interception, and deployment of information-stealing malware being shared via Telegram and other platforms.
Threat Actor Activity Around OpenClaw and Attribution
While formal attribution remains limited, behavioral analysis reveals several coordinated campaigns appearing almost immediately after the first deployment of OpenClaw. The speed and efficacy of these campaigns are very strong indicators of organized, criminal groups exploiting the lack of security and technical awareness of adopters. Despite widespread media coverage, the following campaigns are still active at the time of this writing.
ClawHavoc (Supply Chain Mass Deployment)
ClawHavoc was first detected on January 29th, 2026 and primarily uses Atomic Stealer (MAC) and keyloggers (Windows) whilst masquerading as legitimate cryptocurrency tools (e.g., “solana-wallet-tracker,” “youtube-summarize-pro”). Installation documentation includes a “Prerequisites” section directing users to execute curl commands downloading the stealer malware. This exploit was given the following CVE-2026-25253 for remote code execution and impacts all versions prior to 2026.1.29. This exploit allows an attacker to gain access to all OpenClaw-integrated services and credentials via a full system compromise with user level privileges. The end goal by an attacker is the likely exfiltration of persistent memory containing sensitive historical data and the lateral movement opportunities within corporate networks if deployed on enterprise devices.
Automated Skill Poisoning Through ClawHub
Starting around February 1st, 2026, ClawHub, a community-maintained skills marketplace for OpenClaw, became a primary distribution channel for malware due to minimal publication barriers and absence of automated security scanning. The marketplace, which is still running, operates on a trust-by-default model where any GitHub account aged one week or older could publish skills without code review. The open community model has led to a prevalence of more widespread techniques such as account take-overs and the impersonations of legitimate, trusted users.
Our research shows that accounts such as “Hightower6eu” have been involved with mass deployment automation.
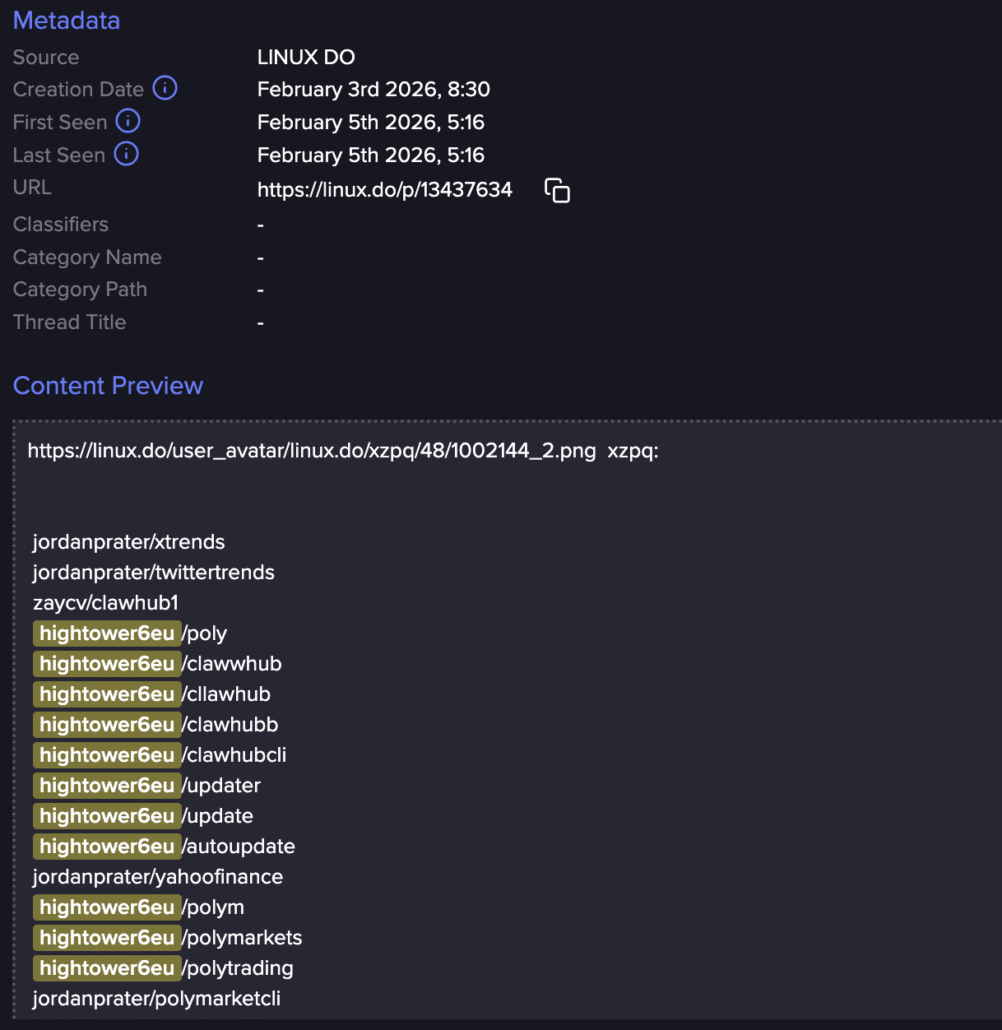
Screenshots from the Flare platform of Hightower6eu activity (Flare link to post, sign up for the free trial to access if you aren’t already a customer)
The purpose of mass deployment is to encompass a number of techniques into updates mimicking real world activity. For example, they can display professional documentation with “Prerequisites” or “Setup” sections containing curl commands that download and execute malware as well as execute commands opening interactive shells back to attacker servers, granting persistent remote control while exfiltrating API keys, OAuth tokens, and passwords to attacker webhook services. The rapid evolution combined with the minimal account requirements made this environment a rich feeding ground for attacker collection and reconnaissance.
Exposed Administrative Interfaces
While adopting new processes or platforms always carries some level of risk, rapid uptake by users unfamiliar with proper security configurations has significantly expanded the potential attack surface and increased the pool of potential victims. Using commercially available scanning tools reveals thousands of OpenClaw instances with exposed Control UI interfaces accessible on the default port 18789. At the time of writing, this number is over 312,000 instances with the default port open and exposed.
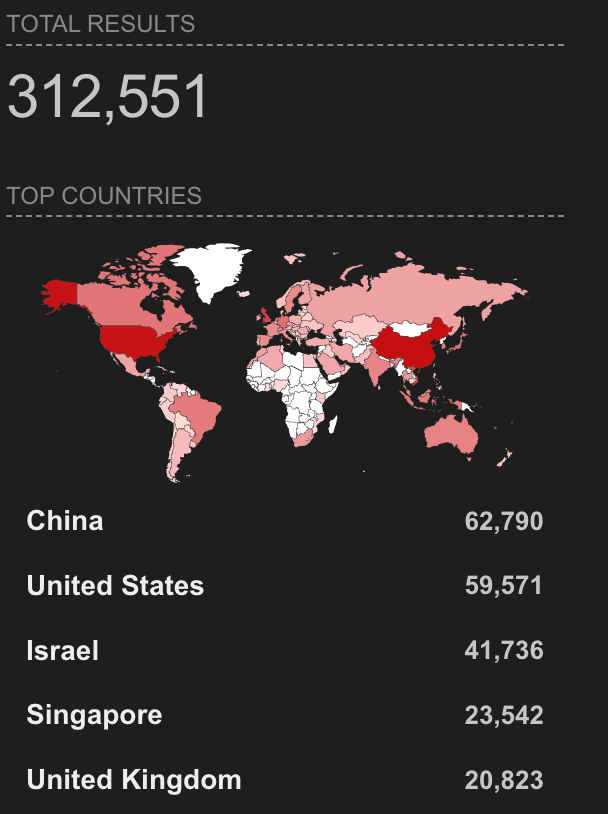
Shodan search for the default Port:18789 run on February 18th, 2025
These deployed instances exhibit a range of potentially critical security vulnerabilities, such as missing authentication gateways which allow unauthenticated access, reverse proxy header bypasses which bypass authentication checks or instances being bound to 0.0.0.0 instead of 127.0.0.1, making them directly accessible from the internet. Security researchers have reported exploit attempts within minutes of deploying honeypot instances using the default configurations.
Threat Actors Honing in on Targeting AI Agents
The rapid exploitation of OpenClaw deployments represents a notable inflection point in the evolution of AI-related security threats. Within weeks of widespread adoption, threat actors demonstrated a strong understanding of the platform’s architecture, developed multiple exploitation methods, and leveraged the skills ecosystem to establish supply chain attack pathways at scale. The speed and coordination observed suggest that organized threat actor groups, both criminal and nation state are actively monitoring and targeting emerging AI agent platforms.
OpenClaw’s security challenges stem from fundamental architectural choices prioritizing autonomy and capability over security controls which appears to be confirmed by comments attributed to Peter Steinberger, when researchers questioned him regarding malware being found and he is said to have replied that security “isn’t really something that he wants to prioritize.” The platform’s design combining persistent memory, privileged system access, and integration with sensitive services creates an attack surface that aligns precisely with threat group objectives: credential harvesting, lateral movement enablement, and long-term surveillance and persistence capability.
What OpenClaw Exploitation Means for Security Teams
Organizations face both immediate operational risks and longer-term strategic challenges. In the near term, unauthorized or inadequately secured OpenClaw deployments may introduce covert data exfiltration pathways and establish footholds for threat actor persistence within enterprise environments. Over the longer future, and with OpenAI now hiring Steinberger and likely using OpenClaw as a foundational model it represents an early iteration of autonomous AI agents that will become increasingly embedded within organizational workflows and infrastructure, but putting the responsibility of security on the organizations deploying the models rather than incorporating security by design.
We will continue to monitor the expanding threat exposure environment and report on any confirmed criminal or nation state activity in this space.
Monitor Emerging Threats with Flare
The Flare Threat Exposure Management solution empowers organizations to proactively detect, prioritize, and mitigate the types of exposures commonly exploited by threat actors. Our platform automatically scans the clear & dark web and prominent threat actor communities 24/7 to discover unknown events, prioritize risks, and deliver actionable intelligence you can use instantly to improve security.
Flare integrates into your security program in 30 minutes and often replaces several SaaS and open source tools. See what external threats are exposed for your organization by signing up for our free trial.




