The largest repackage and re-post of an old leak
In November 2024, a hacker known as “Nam3L3ss” allegedly released previously undisclosed data from the MOVEit breach in May 2023. This leak consisted of millions of records, including sensitive employee and big brand corporate information, significantly escalating the breach’s impact. Digging into this story reveals that Nam3L3ss claims to be an hacktivist freeing information from many previous breaches, not just MOVEit.
MOVEit History
MOVEit is a managed file transfer software produced by Ipswitch. Inc., now a subsidiary of Progress Software. MOVEit encrypts files and uses the FTP (file transfer protocol) to transfer data. On May 31st 2023, Progress disclosed a pre-authentication SQL Injection vulnerability in MOVEit Transfer and Cloud, later assigned CVE-2023-34362. This vulnerability turned out to be a 0-day actively exploited in the wild.
Attackers exploited this vulnerability on public-facing servers, allowing them to deploy a web shell called “LemurLoot,” disguised as legitimate ASP.NET files. This enabled the exfiltration of sensitive data from affected organizations.
In May 2023, the ransomware group Cl0p exploited the 0-day vulnerability to gain access to MOVEit instances worldwide. Cl0p published a blog post about the breach, warning affected organizations that they had until June 14th to pay a ransom or risk having their data made public. Organizations disclosed in June 2023 included the Government of Nova Scotia, BBC, British Airways, and the United States Department of Energy amongst hundreds of others.
Cl0p extorted victims over the course of June, July and August, posting batches of victims and leaking their data via Bittorrent. Then we didn’t hear from them.
The Rise of Nam3L3ss
Over a year later, Nam3L3ss claimed to have MOVEit related data from prominent companies. These leaks were not previously claimed by Cl0p and sparked theories as to the origins of this data. While these leaks appear new, they, in fact, are repacked data Cl0p’s breach. This is the largest repackaging of old information to ever happen.
The repackaged data was extracted, for now, from four compromised companies’ files from the Cl0p MOVEit breach. Nam3L3ss strategically reorganized and repackaged data from companies impacted by the MOVEit breach, presenting it in a way that emphasized high-profile clients. For example, Company A, a contractor for Company B, had its compromised files containing a directory labeled “Company B.” Nam3L3ss extracted and leaked this directory separately, branding the leak as “Company B” to amplify its significance.
This approach transformed a voluminous and unstructured leak into a targeted release, naming and organizing the leaks based on the recognizable clients rather than the original contractors. This repackaging tactic, likely aimed to maximize public attention, has the consequence of increasing pressure on the implicated companies.
Nam3L3ss is a hacktivist claiming to liberate data. He posted a manifesto on Breach forums and operates a blog at nam3l3ss.bearblog[.]dev. Here’s an excerpt from his blog:
Data I post is NOT a secret, everything I post the Criminal already have it!
It's only the Politicians, Government Agencies, and sorry to say the Public in general who have their heads buried in the sand about just how much information is floating around the internet on them, and extremely Personal information!
I am tired of Governments allowing Companies to SELL data on people and Data Brokers with terrible security or protections on their data.
Who really owns the Data on you? IS it YOUR data or do Companies OWN your private data and have a right to SELL it to anyone they desire?
Think about that for a minute, Companies treat YOU and your information as something they OWN! It does NOT belong to you they say, so they are FREE to SELL your data to whoever they want whenever they want and YOU have NO SAY!
Nam3L3ss insists he is not affiliated with Cl0p ransomware
Although he insists, see forum post screenshot below for details, we have so far confirmed that all of the repackaged breaches we looked at came from the MOVEit breach of 2023.
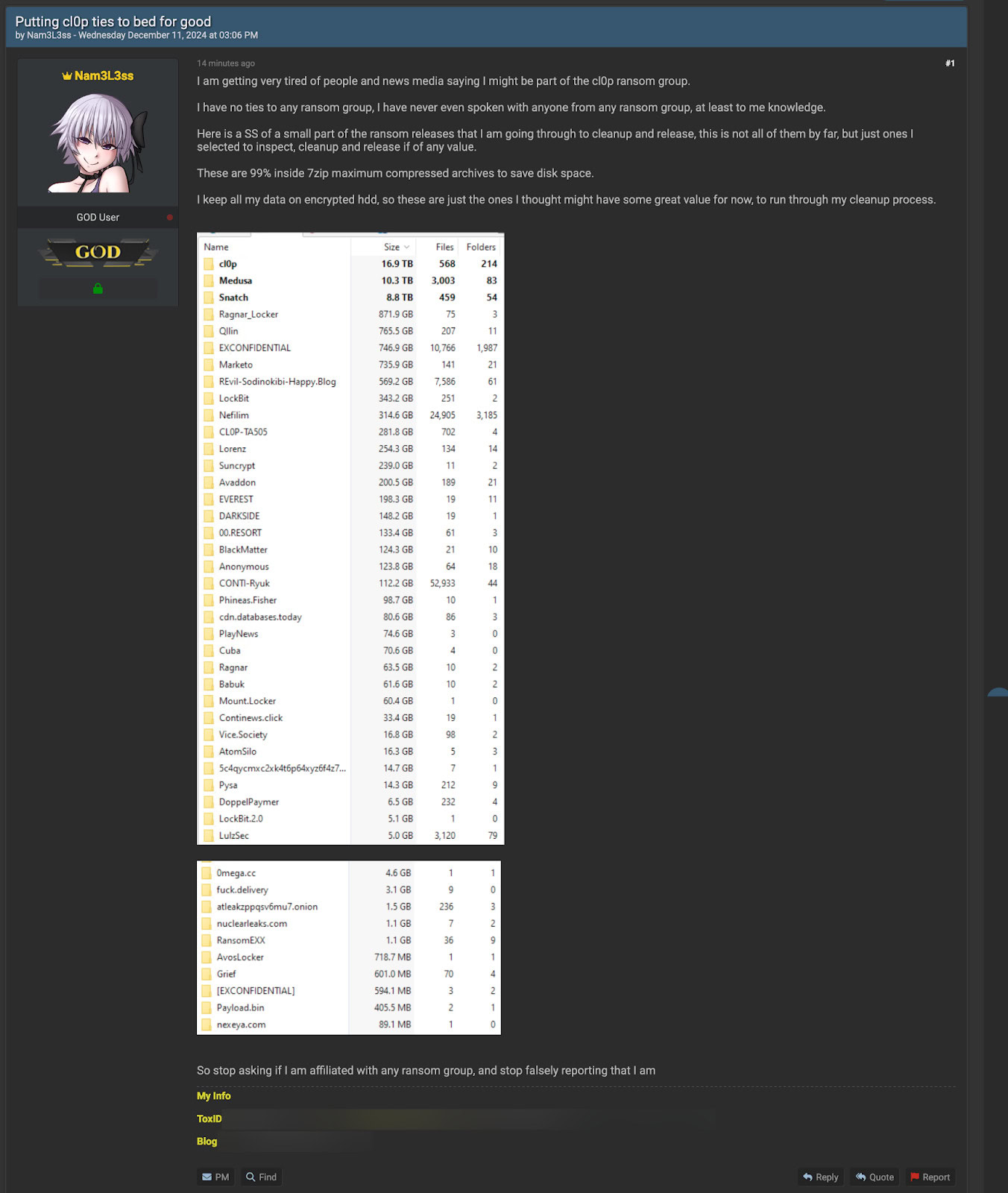
Here is the list of breaches he allegedly possess:
- Cl0p: 16.9TB
- Medusa: 10.3TB
- Snatch: 8.8TB
- Ragnar_Locker: 871.9GB
- Qilin: 765.5GB
- EXConfidential: 746.9GB
- Marketo: 735.9GB
- Revil-Sodinokibi-Happy[.]Blog: 569.2GB
- Lockbit: 343.2GB
- Nefilim: 314.6GB
- CL0P-TA505: 281.8GB
- Lorenz: 254.3GB
- Suncrypt: 239.0GB
- Avaddon: 200.5GB
- EVEREST: 198.3GB
- DARKSiDE: 148.2GB
- 00[.]Resort: 133.4GB
- Blackmatter: 124.3GB
- Anonymous: 123.8GB
- Conti-Ryuk: 112.2GB
- Phineas[.]Fisher: 98.7GB
- cdn.databases[.]today: 80.6GB
- PlayNews: 74.6GB
- Cuba: 70.6GB
- Ragnar: 63.5GB
- Babuk: 61.6GB
- Mount[.]Locker: 60.4GB
- ContiNews: 33.4GB
- Vice[.]Society: 16.8GB
- AtomSilo: 16.3GB
- 5c4qycmxc2xk4t6p64xyz6f4z7: 14.7GB
- Pysa: 14.3 GB
- DoppelPaymer: 6.5GB
- Lockbit2.0: 5.1GB
- Lulzsec: 5.0GB
- 0mega: 4.6GB
- f[u]ck[.]delivery: 3.1 GB
- atlaszppqsv6mu7[.]onion: 1.5GB
- nuclearleaks[.]com: 1.1GB
- RansomEXX: 1.1GB
- AvosLocker: 718.7MB
- Grief: 601.0MB
- [EXCONFIDENTIAL]: 594.1MB
- Payload[.]bin: 405.5MB
- nexeya[.]com: 89.1 MB
Repackaging Enabled by Supply Chains
These four entities were contractors for larger corporations, providing services that integrate into their operations. While a company may invest heavily in its own security infrastructure, its overall security posture is only as strong as its weakest link. Supply chain monitoring is not just a precaution but a necessity to mitigate the risk of security failures from third-party contractors and suppliers.
Flare customers can access a TLP:Amber article in our research center covering the breach victims as disclosed by Nam3L3ss as of December 6th 2024.
We would like to thank Estelle Ruellan, Olivier Bilodeau, Tammy Harper, and Mathieu Lavoie for their help on this article.
Dark Web Investigations and Flare
The Flare Threat Exposure Management (TEM) solution empowers organizations to proactively detect, prioritize, and mitigate the types of exposures commonly exploited by threat actors. Our platform automatically scans the clear & dark web and prominent threat actor communities 24/7 to discover unknown events, prioritize risks, and deliver actionable intelligence you can use instantly to improve security.
Flare integrates into your security program in 30 minutes and often replaces several SaaS and open source tools. Learn more by signing up for our free trial.