The dark web operates outside the reach of Google, Bing, and standard browsers. Accessible only through specialized tools like Tor, it serves as both a privacy haven and a thriving marketplace for stolen credentials, corporate data, and attack infrastructure. For security teams, visibility into this hidden layer of the internet isn’t optional—it’s where threat actors buy initial access, trade stealer logs, and sell corporate data.
Monitor the Dark Web Without Searching It Yourself
Flare continuously monitors the dark web, I2P, and thousands of Telegram channels to detect stolen credentials and threat actor activity targeting your organization.
Understanding Dark Web Search Engines
What are Dark Web Search Engines?
Dark web monitoring platforms for business are specialized SaaS platforms that allow you to browse the dark web and data from the cybercrime ecosystem that isn’t indexed by traditional search engines. The dark web is hidden from regular browsers and search engines thanks to its registry operator, which differs from the infrastructure used by the clear web. The most well known browser is Tor, which stands for The Onion Router.
Understanding Tor & .onion Sites
The internet has three distinct layers. Dark web search engines help you navigate the deepest layer—accessible only through specialized tools like Tor.
The Onion Router (Tor)
Originally developed by the U.S. Naval Research LaboratoryHow It Works
Traffic is encrypted in multiple layers and routed through a series of volunteer-operated nodes (relays), making it extremely difficult to trace the origin or destination.
.onion Addresses
Instead of traditional domains (.com, .org), dark web sites use .onion addresses—56-character strings that can only be resolved within the Tor network.
Who Uses It
Journalists, activists, privacy advocates—but also threat actors operating marketplaces, forums, and data leak sites outside law enforcement reach.
Security Threat
Infostealers exfiltrate credentials to dark web marketplaces. Ransomware gangs host leak sites on .onion domains to pressure victims and sell stolen data.
http://3g2upl4pq6kufc4m.onion
What Search Engines Can Access the Dark Web?
There are a variety of search engines available that will allow you and your team to access the dark web. These include tools like:
- Torch
- Ahmia
- Haystack
- Candle
- Not Evil
- Dark Search
- Onion Search
Is the Dark Web Available on Google?
Unlike the deep web, which is accessible on regular browsers if you have the correct web address, you can’t access the dark web from standard browsers like Google or Bing. To gain access, you need a special browser such as Tor, and a search engine designed specifically for the dark web.
Why Do You Need to Understand Dark Web Search Engines?
Why Should Security Teams Consider Dark Web Monitoring?
The dark web isn’t all bad; Onion sites are often used by dissidents, privacy focused researchers, and even legitimate businesses. However, the anonymity provided by the dark web also means serves as a hub and a marketplace for threat actors. Stolen and leaked data is bought and sold in parts of the dark web, as is malware as a service that can be used to attack your networks. By searching and monitoring the dark web, you can catch threats and stolen data before your assets are exploited by attackers.
What is the Impact of Criminal Activity on the Dark Web?
Threat actors refine their techniques on the dark web, form gangs, and sell each other tools that help them steal enterprise data. The impact of this activity is evident in the numbers: in 2023, there were 3,205 publicly reported data breaches, a 72% increase over 2021 which held the previous record for the highest number of publicly reported data breaches on record.
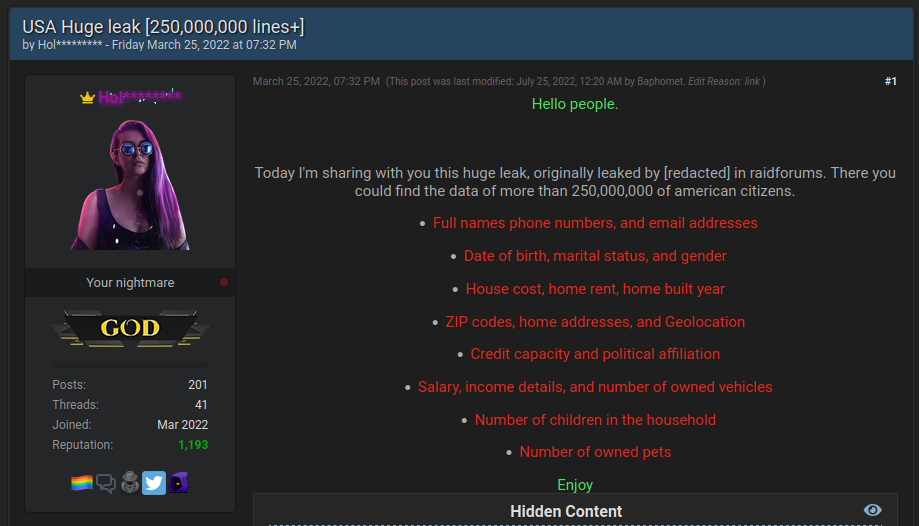
A post on BreachForums giving away breached consumer data
When a breach occurs, stolen data rarely stays in one place. It follows a predictable lifecycle across dark web infrastructure:
- Initial access brokers sell entry points to compromised networks—often harvested from infostealer logs containing valid credentials, session cookies, and VPN tokens.
- Private sales and auctions happen first. High-value datasets (financial records, healthcare data, corporate credentials) are sold to a small group of buyers before wider distribution.
- Leak sites and forums come next. Ransomware groups publish victim data on .onion leak sites to pressure payment. Other actors dump breaches on forums like BreachForums or via Telegram channels to build reputation.
- Commoditization follows. Within weeks or months, breach data gets repackaged, combined with other leaks, and sold in bulk—or released for free to maximize damage.
- Credential stuffing and fraud are the endgame. Exposed credentials get tested against banking portals, corporate SSO systems, and SaaS applications at scale.
Why Dark Web Monitoring Matters
By the time a breach hits the news, threat actors have often had weeks of access to the data. Continuous dark web monitoring compresses your detection window—surfacing exposed credentials, leaked documents, or mentions of your organization while there’s still time to act: forcing password resets, revoking sessions, or notifying affected customers before attackers weaponize the data.
What is the Impact of an Attack?
Cyber attacks cause many problems, from lack of trust in your brand to the interruption of business operations. The consequences are also financial: the average cost of a data breach peaked in 2023 at $4.45 million. Such costs include legal fees, regulatory sanctions, the cost of finding and remediating vulnerabilities, and other related costs.
Dark Web Search Engines and Flare
Do You Need Dark Web Search Engines to Monitor the Dark Web?
Security teams should absolutely be monitoring the dark web, but this doesn’t mean they need to be searching it themselves. Tools like Flare empower your team to conduct reconnaissance on the dark web, scanning for stolen data and other information that might jeopardize your systems and networks.
Flare has an eight year archive of the dark web and does real time monitoring for more than 50,000 cybercrime Telegram channels, enabling security teams to pivot across data sources in the cybercrime system without any concerns over compromising operational security.
How Does Flare Monitor the Dark Web?
Flare monitors and continuously ingests data from thousands of channels across sources as diverse as Telegram, the dark web and I2P. Our platform continuously scrapes dark web forums, ransom blogs, autoshops, and dark web marketplaces. Flare automatically collects, analyzes, and contextualizes dark web data to provide your team with information relevant to your organization.
What are the Key Features of Flare’s Dark Web Monitoring Solution?
- Automation: Your analysts can’t manually search the dark web constantly. Flare automates the process to give you 24/7 coverage, freeing up your team for higher order tasks.
- Dark Web Archive: Flare continuously archives and indexes data, making it searchable and preventing threat actors from taking down or deleting data that may be harmful.
- A proactive security stance: By actively seeking stolen data out, you can catch a breach early and take steps to protect your data.
- Visibility into threats: Flare’s data theft monitoring solution scans the dark and clear web, as well as illicit Telegram channels, to find leaks before an attack happens.
- Immediate alerts: Flare cuts through the noise, sending only relevant alerts to your team, so you will know as soon as information appears on the dark web or a paste and dump site.
Dark Web Search Engines and Flare
Flare provides the leading Threat Exposure Management (TEM) solution for organizations. Our technology constantly scans the online world, including the clear & dark web, to discover unknown events, automatically prioritize risks, and deliver actionable intelligence you can use instantly to improve security. By monitoring dark web activity, you can keep your organization’s data and networks safe from attackers.
Our solution integrates into your security program in 30 minutes to provide your team with actionable intelligence and automated remediation for high-risk exposure. See it yourself with our free trial.


