The nebulous part of the internet: the dark web, which traditional search engines don’t index, serves as a hub for cybercriminal activity, ranging from illicit trade in stolen data to planning sophisticated cyberattacks.
Dark web analytics can help organizations detect potential threats and enable them to proactively protect their digital ecosystem. There are a number of threats on the dark web, some that have been around for many years and some that are entirely novel. To name a few:
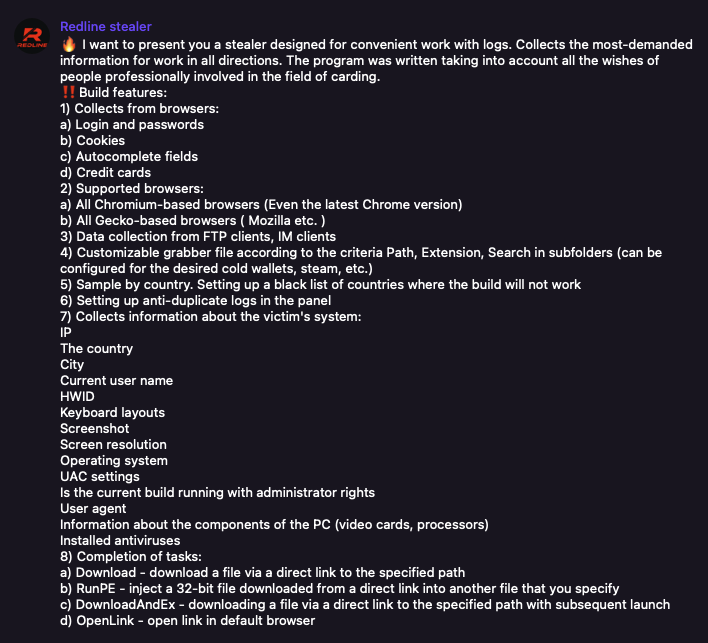
- Stealer logs containing corporate credentials and cookies
- “Traditional” leaked credentials
- Threat actors selling corporate data
- Threat actors selling access to corporate IT environments
- Threat actors targeting companies for political reasons
Understanding the Dark Web: A (not so) Hidden Hotbed for Cyber Threats
What are the Parts of the Internet: Clear, Deep, and Dark Web?
What we see and use daily – news websites, online shopping – is commonly referred to as the clear web. Beneath this visible layer lies the deep web, encompassing unindexed pages like academic databases and password-protected accounts.
The dark web is a part of the internet that people cannot access through standard web browsers. It is a haven for privacy advocates, political dissidents, and unfortunately, an array of cybercriminals. Accessible only through specialized software like Tor or I2P, the dark web anonymizes user traffic, making it ideal for activities wanting to stay off the radar, including the trade of illegal goods, discussion of malicious tactics, and sale of stolen data.
To be clear, most of what occurs on the dark web is not cybercrime. The most common use of the dark web is to sell drugs, guns, and other illicit goods. However, significant sections of the dark web do contain cybercrime, and many sections contain information related to fraud and other cybercrime related activities.
What Happens on the Dark Web
While the dark web is vast and diverse, cybercriminal forums and marketplaces pose a significant threat to businesses. Here, threat actors buy and sell anything from credit card information, intellectual property, to hacking tools and ransomware-as-a-service offerings. These secretive activities offer a trove of insights into potential threats to an organization’s cybersecurity.
Cybercriminals on the dark web often:
- Plan and discuss potential attacks
- Exploit vulnerabilities
- Exchange attack methodologies
They can sell access to compromised systems, trade in stolen credentials, and much more. Being able to tap into these conversations, transactions, and threat actor behaviors equips businesses with valuable intelligence to fortify their defense systems.
Therefore, businesses and cybersecurity professionals are increasingly realizing the importance of monitoring and understanding the dark web. By leveraging dark web analytics, they can:
- Identify emerging threats
- Detect breaches early
- Potentially prevent cyber attacks before they happen
This proactive cybersecurity approach can make the difference between a well-guarded system and a devastating data breach.
However, the dark web is expanding. Telegram has popped up as another significant source of cybercrime, with thousands of channels specializing in bank fraud, stealer logs, stolen credentials, DDoSing, ransomware, and other illicit activities.
Unlike the “traditional” dark web, Telegram channels are easy to create and easy to delete, account creation takes only a few seconds and messaging is encrypted. Telegram now serves as both an alternative to the dark web and as a backup system, with many major dark web marketplaces and forums having corresponding Telegram channels.
The Importance of Dark Web Analytics in Today’s Cybersecurity Landscape
As the cyber threat landscape grows increasingly complex, the need for businesses to go above and beyond traditional defense methods has never been more critical. Dark web analytics represents a potent weapon in the arsenal of any robust cybersecurity strategy.
By monitoring and analyzing dark web activities, organizations can gain actionable insights to stay ahead of cyber threats.
Here’s why dark web analytics plays such a pivotal role in today’s cybersecurity landscape.
Early Threat Detection
On the dark web, cybercriminals discuss and plan their strategies, including:
- Potential targets
- New malware developments
- Exploitable vulnerabilities
By analyzing this data, organizations can detect threats before they manifest into full-blown attacks.
Early threat detection allows for timely countermeasures, mitigating potential damage significantly.
Data Breach Detection & Response
In the unfortunate event of a data breach, the dark web is usually the first place stolen data appears for sale. Monitoring the dark web allows organizations to quickly identify their stolen data, helping them gauge the extent of a breach and respond effectively. Data often appears on dark web forums such as Breachforums, which threat actors give away for free or sell.
In addition, many ransomware groups now work under a model called “data extortion ransomware” in which they threaten to leak a company’s data if the organization doesn’t pay the ransom.
Swift detection of breached data can minimize the damage, allowing the organization to alert affected customers or stakeholders and take remedial actions.
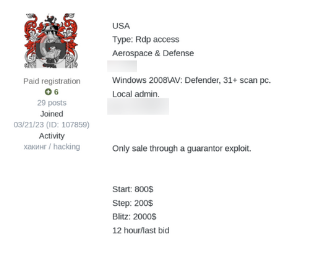
IABs will sometimes name the specific company they have hacked, but in other cases may obscure critical details. Monitoring IAB forums can provide an excellent opportunity to identify if your company has been compromised, or if one of your third-parties may have been.
Insight Into Cyber Criminal Behavior
Dark web analytics also provide valuable insights into the behavior, tactics, techniques, and procedures (TTPs) of cyber threat actors. Understanding how these individuals or groups operate is vital for crafting effective defensive strategies. It empowers organizations to anticipate and prepare for evolving threats, enhancing their overall cybersecurity posture.
Cybercriminals routinely sell exploits, vulnerabilities, and even malware on dedicated dark web forums and Telegram channels. In some cases an exploit may target a particular company’s application or service, while in others an exploit may affect a commonly used open source library.
Regulatory Compliance
Several industries, particularly finance and healthcare, are under regulatory obligations to protect sensitive data. Proactive monitoring of the dark web forms an integral part of demonstrating due diligence in data protection efforts, helping meet compliance requirements.
Strengthening Cybersecurity Infrastructure
The intelligence derived from dark web analytics can help organizations identify the weaknesses in their cybersecurity infrastructure. By understanding what cybercriminals are after and how they may achieve their goals, businesses can prioritize strengthening their defenses accordingly. For example, research shows that many organization’s fail to prioritize even basic cybersecurity recommendations.
Cyber threats are continually evolving and the cost of data breaches is steadily rising. Dark web analytics offers businesses a proactive approach to cybersecurity. By shedding light on the shadowy corners of the cyber threat landscape, it empowers organizations to stay one step ahead of cybercriminals.
Key Techniques and Tools in Dark Web Analytics
Delving into the dark web to extract valuable intelligence is a complex task that requires a combination of advanced techniques and specialized tools.
Here are some of the most important methods utilized in dark web analytics, which allow cybersecurity experts to convert raw data into actionable insights.
Web Crawling and Scraping
One of the primary techniques used to gather data from the dark web is web crawling and scraping. Unlike the clear web, search engines don’t index dark web sites, making them hard to locate. Advanced web crawlers are used to automate the process of discovering and collecting data from these hidden sites.
These tools can gather a wealth of information, including forum posts, marketplace listings, and more, providing a foundation for further analysis.
Natural Language Processing (NLP)
After gathering data, the next step is cleaning and structuring it.
Natural language processing, a branch of artificial intelligence, aids in understanding and organizing the vast amount of text-based data gathered from the Dark Web. NLP can help detect languages, identify relevant topics, and even understand sentiment, providing a richer context to the data.
Threat Intelligence Platforms
Organizations often use threat intelligence platforms to aggregate and analyze data from various sources, including the dark web. These platforms can:
- Automate data collection
- Integrate with existing security systems
- Provide real-time alerts
making it easier for cybersecurity teams to stay on top of potential threats.
User Profiling and Link Analysis
Tools that can profile users and analyze their relationships are vital in understanding criminal networks operating on the dark web. User profiling can reveal repeated behavior, while link analysis can demonstrate relationships between different entities, be it individuals, websites, or transactions.
Implementing dark web analytics requires a combination of these advanced techniques and tools. However, the benefits it provides in identifying potential threats and bolstering security measures make it a crucial component of any forward-thinking cybersecurity strategy. The goal is not just to react to cyber threats but to proactively understand and anticipate them, staying one step ahead of cybercriminals at all times.
Dark Web Analytics with Flare
The Flare Threat Exposure Management (TEM) solution empowers organizations to proactively detect, prioritize, and mitigate the types of exposures commonly exploited by threat actors. Our platform automatically scans the clear & dark web and prominent threat actor communities 24/7 to discover unknown events, prioritize risks, and deliver actionable intelligence you can use instantly to improve security.
Flare integrates into your security program in 30 minutes and often replaces several SaaS and open source tools. Learn more by signing up for our free trial.