
This article was updated on December 13th, 2025.
The dark web is often a mysterious and misunderstood corner of cyberspace. Dark web forums are accessible through Tor (although some do have clear web mirrors) and serve as a congregation point for cybercriminals. Some sites such as Dread mimic clear web services like Reddit, while others such as XSS and Exploit serve as hubs for Russian-language threat actors.
The Onion Router (Tor) encrypts and routes connections through multiple relay nodes, providing strong anonymity by obscuring the user’s IP address and location. This makes it an excellent service for threat actors to use as it creates significant challenges for law enforcement to attribute specific markets, forums, listings, and posts to individuals.
Forums serve a critical role in the cybercrime ecosystem. Threat actors use forums to communicate, to transact, to settle disputes, and to recruit other threat actors to specific groups or projects. Reputation systems, escrow services, and moderator enforcement give these communities a level of trust and structure that enable large-scale criminal collaboration. The static nature of forums combined with the value of the content makes them an excellent source for threat intelligence monitoring.
Automate Dark Web Forum Monitoring
Flare monitors hundreds of dark web forums including XSS, Leakbase, Dread, and emerging marketplaces. Search across 8 years of archived data and get real-time alerts when your organization, credentials, or data appear in threat actor discussions.
Are Dark Web Forums Worth Monitoring?
While countless cybercriminals will often operate their illegal activities outside the dark web (such as in illicit Telegram channels), many dark web forums are still extensively valuable to monitor regularly. Dark web monitoring provides organizations a view of threat actor activity, the most recent data breaches, and discussion of critical exploits.
In some cases threat actors will discuss targeting specific organizations, or sell data or access to organizations by name. Rapidly detecting and alerting on these posts can provide your organization advanced notice that there may be a significant security event, or even a third-party data breach that could contain your data.
Dark Web Forums to Watch
XSS
XSS is a hub for Russian-language threat actors, and primarily focuses on: credential sales, spam, phishing, malware, initial access sale, exploit trading, and data leaks. This forum was linked to ransomware groups such as REvil, LockBit, and Conti. In July 2025, Europol, French, and Ukrainian authorities arrested a threat actor alleged to be the administrator of XSS. The forum continues to remain active under a new unknown administrator, but the former admin’s arrest has sowed suspicion, leading to declines in user count and traffic. Some believe that XSS is a law enforcement honeypot, due to recent bans and blocked cryptocurrency funds.
Screenshot from XSS
DamageLib
After the arrest of who is believed to be XSS’s admin, former XSS moderators started DamageLib, as they didn’t trust the new XSS admin. The forum claims it does not track users. DamageLib focuses on hacking tutorials, malware development tutorials, exploits and vulnerabilities-related discussions, and indirect sales of MaaS, databases, and more. The forum’s activity remains on the low end as it is impacted by credibility lost over XSS’s fall.
Dread
Dread is a dark web forum that was designed to mimic the look of the legitimate forum website Reddit. After its creation in 2018, this dark web forum now sees over hundreds of posts per day currently. This forum was essentially created to host many sub-communities to help threat actors connect and find the information they want more quickly. The majority of the illicit information shared on Dread is in relation to data leaks and selling data freely.
Screenshot from Dread
Leakbase
One of the more sophisticated forums on the dark web, both in terms of the amount of sensitive data available and the mature approach to discovery and commerce, Leakbase gives hackers a place to sell stolen data, combolists, leaked credentials and to discuss future attacks, often in conjunction. Discussions are conducted in English and, notably, there’s a ban on Russian-data, presumably to avoid geopolitical tensions inviting extra scrutiny. The forum remains active despite at least one domain change and appears poised for longevity and growth given the administrator’s track record.
Exploit
Comparable in many ways to XSS, Russian hackers also congregate on Exploit, which has a presence on both the dark and clear web. From stolen credentials and malware to advice, intelligence, and collaborators, this forum offers everything a cyber criminal would need to launch attacks and pick targets at will. Exploit.In stands out from others by consisting largely of established cyber criminals rather than opportunistic beginners, making it one of the most dangerous forums on the dark web, responsible for facilitating countless cyber attacks over the years.
Initial Access Brokers on Exploit
Initial access brokers commonly operate on Exploit. These threat actors can gain initial access to enterprise environments, then sell the access to ransomware groups, affiliates, and other threat actors to make a profit from it. Typically IABs will offer a start price, step, and a blitz, which serves as a “buy it now” option for threat actors.
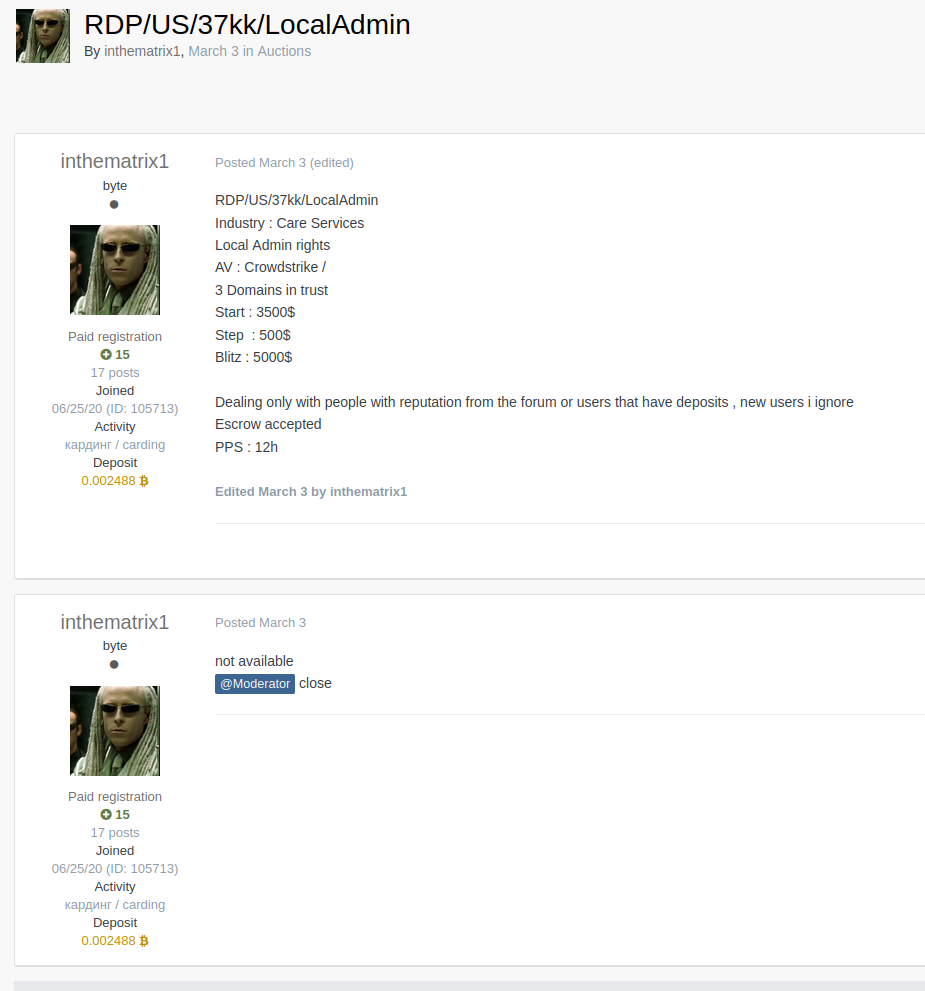
Post from initial access broker
DarkForums
When another prominent dark web forum called BreachForums was taken down by authorities, many former members migrated to DarkForums, which had a relatively small presence to that point. That quickly changed with the influx of experienced and engaged users who have the option to subscribe to three paid ranks: VIP, MVP, and GOD. Paid subscribers gain access to exclusive Telegram channels and data leak feeds—a sign of forums using mature engagement tactics to attract and retain users.
RAMP
The Russian Anonymous Marketplace (RAMP) has undergone several incarnations since it first appeared over a decade ago, evolving from a marketplace for illicit drugs to one largely focused on cybercrime. RAMP resembles many other dark web forums with one crucial exception: Sites that sell stolen data often prohibit listing involving ransomware attacks following the Colonial Pipeline ransomware attacks in 2021, but RAMP does not have this prohibition. That makes it an invaluable source of information about past and future ransomware attacks, as well as a potent resource for past and future attackers.
The Key Characteristics of Dark Web Forums
In many ways the dark web represents the vanguard of the cybercrime world, where the most aggressive and ambitious attackers go to plan new attacks and devise innovative methods. As such, the dark web changes constantly, whether that means old forums evolving or new forums emerging. Rather than focusing search efforts on too few forums or missing the newest threats to appear on the dark web, operate instead with a more expansive understanding of what higher-risk dark web communities look like. They all share these features:
- Accessible: Despite the fact the dark web forums are less accessible than anything on the surface or clear web, and many enact barriers like rigorous vetting procedures and high membership fees, these forums still need to be accessible to users. That means even if a source is “closed” it’s not necessarily inaccessible to new members or even security researchers.
- Organized: Just like other forums, and related to the previous point, dark web forums are organized around rules, hierarchies, systems, and norms. It’s what makes these forums attractive and keeps them running as intended. However, it’s also what makes these forums identifiable and traceable, giving security teams clues to help anticipate attacks and neutralize threats.
- Finite: Vast as the dark web may be, with people around the world logging on in large numbers, it’s still a finite space that’s not as big as it may seem. There may be large numbers of forums, but many are small or defunct, and many of the users on the larger, more-established forums are not active. Understanding that the dark web isn’t as “unknowable” as it seems helps security teams better utilize this valuable resource.
- Exposable: Since dark web forums are run by real people, they are not as perfectly secure as they appear, even when they have rigorous security and privacy controls in place. Plenty of forums and hacker communities have crashed and burned—to the benefit of defenders—due to mistakes made by their administrators or because of in-fighting among threat actors. The evasive maneuvers used on the dark web are not immune to human errors, which is why no forum is immune to exposure and infiltration.
Best Practices for Dark Web Forum Monitoring
When implementing dark web monitoring as part of your cybersecurity strategy, it may seem challenging to implement successfully. However, the benefit to implement dark web monitoring as part of your overall security posture can help your organization stay on top of ongoing threats to industries and provide valuable threat intelligence insights for your company. There are several best practices companies can follow to strengthen their monitoring efforts. Here are four best practices to ensure your dark web monitoring is done effectively:
1. Define the goals of conducting dark web monitoring.
Dark web monitoring should always be done with the goal of passive intelligence gathering only without consulting law enforcement or legal counsel. Organizations should aim to set an established baseline of goals, key areas to monitor, and rules of engagement. They should also ensure that they are gathering the necessary information to help aid identifying and tracking of exploits and actions taken by malicious actors.
2. Employ the use of staff, tools, and/or automation to support dark web monitoring.
There are numerous tools and automation capabilities that can help support companies with regular dark web monitoring. These tools can include dark web crawling while also providing alerts regarding any notable exploits, specific keywords or phrases to watch, and any relevant information that can be detrimental to your brand. Also, it is important to provide your staff the training and defined objectives of what to look for regarding their monitoring efforts.
3. Implement an escalation policy or procedures regarding dark web monitoring.
If a credible threat is detected, businesses should have a predefined escalation strategy to follow accordingly. This plan should also include outlining how the information will be shared with the relevant internal and external stakeholders within the company. It may also be important to take the measure to implement a remediation process if exploits have been found during the dark web monitoring.
4. Ensure regulatory compliance is retained and review measures regularly.
Businesses often need to ensure that their monitoring activities comply and adhere to the necessary laws and regulations for conducting dark web monitoring. This can include regulatory compliance measures such as data protection laws and cyber best practices to ensure the monitoring is done for ethical and threat intelligence purposes only. Additionally, given that the threat landscape is constantly changing it will be valuable to ensure the policies and practices of dark web monitoring for your organization are reviewed and updated regularly.
The dark web has become a breeding ground for cybercrime and other illegal activities, thus making it a significant threat to countless consumers and companies. Implementing dark web monitoring is a crucial step for many companies to identify potential cyber risks, data breaches, and other illegal activities. By effectively monitoring the dark web, businesses can stay ahead of the curve and respond quickly to emerging threats, while protecting themselves and their customers successfully.
Context: The Key Ingredient for Dark Web Monitoring
Dark web monitoring creates two closely related challenges for security teams. First, even with a list of the most prominent dark web forums, someone has to first gain access and then manually search through the content looking for relevant threat intelligence. It can take a massive amounts of time and labor to uncover just a small amount of the intelligence that teams want and need. Which then leads to the second issue: gaps in visibility and intelligence gathering result in a surface-level understanding of threats with little security value.
For example: A security analyst finds infostealer logs for sale on the dark web that contain company credentials and secrets. That’s an important find, but teams still need to ascertain what risks that stolen information creates, what damages could result from those risks, and what it would take to remediate them. Plus, they potentially have to repeat this process multiple times as they discover more information on the dark web. They may have found threat intelligence, but it hasn’t translated into stronger, simpler, or more streamlined security, which is the ultimate purpose of dark web monitoring.
Context is what gives dark web threat intelligence meaningful value as a security resource. It’s what helps teams prioritize the risks they find, accurately assess the right response, and orchestrate an efficient remediation, all while dealing with limited resources. Unfortunately, getting context only multiplies the amount of monitoring and intelligence collection for teams, which explains why it’s often lacking. There’s simply not enough hours available to scour the dark web for all it can reveal.
Technology can bridge this gap and supplement threat intelligence with the context necessary to understand threat actors and anticipate future attacks. The dark web used to be a place for hackers to hide. Now, thanks to more context and more threat intelligence, it’s a place where defenders can gain the edge.
Monitor the Dark Web with Flare
The Flare Threat Exposure Management solution empowers organizations to proactively detect, prioritize, and mitigate the types of exposures commonly exploited by threat actors. Our platform automatically scans the clear & dark web and prominent threat actor communities 24/7 to discover unknown events, prioritize risks, and deliver actionable intelligence you can use instantly to improve security.
Flare integrates into your security program in 30 minutes and often replaces several SaaS and open source tools. See what external threats are exposed for your organization by signing up for our free trial.





