
This article was updated on September 5th, 2025.
Pulling off sophisticated cybercrime can be shockingly simple compared to a few years ago. With the emphasis on “logging in” rather than “hacking in,” threat actors, there’s less barriers today than before.
The notorious Exploit dark web forum is a hotspot for malicious actors in the Russian language cybercrime ecosystem. On this forum, they can share various hacking techniques, malware samples, and proof of concept for exploits.
Some threat actors on Exploit are initial access brokers (IAB), who sell information about accessing organizations’ environments such as with administrative powers or through VPNs. Others can bid on this information for sale through the auction system, private messages, or directly in the thread.
Is Your Access for Sale on Exploit?
Initial access brokers list corporate network access on forums like Exploit, XSS, and RAMP every day. Flare monitors these communities 24/7 so you know when your organization is being targeted before an attack begins.
What are Initial Access Brokers?
Initial Access Brokers (IABs) are specialized threat actors who focus on one thing: breaking into corporate networks and selling that access to other criminals. Rather than conducting ransomware attacks or data theft themselves, IABs invest their time compromising organizations through methods like exploiting vulnerable VPNs, leveraging stolen credentials from stealer logs, or running targeted phishing campaigns against employees with privileged access.
Once they establish a foothold—often with domain admin privileges—they list the access for sale on dark web forums like Exploit, XSS, and RAMP. Their listings typically include details buyers care about: the victim’s country, industry, annual revenue, number of endpoints, and the type of access obtained. Prices range from a few hundred dollars for small targets to $50,000 or more for Fortune 500 companies with high-privilege access.
What Do IABs Do?
The rise of IABs further complicates the cybersecurity landscape. They specialize in breaching systems, cleaning up the stolen information, and then selling that access to the highest bidder, who can then carry out more extensive cyber attacks. This type of threat actor essentially offers a ‘shortcut’ for cybercriminals, lowering the entry barrier for conducting sophisticated cyberattacks.
The impact of the dark web on cybersecurity is significant and growing. As cyber threats continue to evolve in complexity and scale, the importance of comprehensive cyber threat intelligence cannot be overstated.
A Brief History of IABs
Threat actors have been helping each other break into systems and bypass security controls dating back to the 1980s when they first began congregating on the early internet. Over time, as cybercrime became less about experimentation and rebellion and more financially motivated, people began to sell rather than share their initial access. Exploit kits developed in the 2000s gave buyers an “off-the-shelf” way to attack common vulnerabilities.
As these gained popularity and additional products and services emerged to facilitate cyber crime, it attracted more attention from both criminal elements and law enforcement. Forums that used to operate in the obscure corners of the “clear web” migrated to the dark web to evade scrutiny starting in the 2010s.
That move gave initial access brokers everything they needed to evolve once again. The anonymity of the dark web led directly to the rise of marketplaces like Exploit that closely imitate the look and feel of legitimate ecommerce sites. IABs now have an easy way to reach buyers, conduct transactions, and market their services, which in turn increases both supply and demand.
IABs may be nothing new, but they have never before been as accessible or numerous as they are now, and all signs suggest that their role in cybercrime, and their presence on the dark web, will only continue growing.
Delving Into Exploit: The Threat Actor’s Marketplace
Among the encrypted corners of the dark web, Exploit stands out as a veritable hub for cybercriminal activity. This Russian language forum has earned an infamous reputation as an online marketplace where threat actors buy and sell illicit goods and services related to cybercrime.
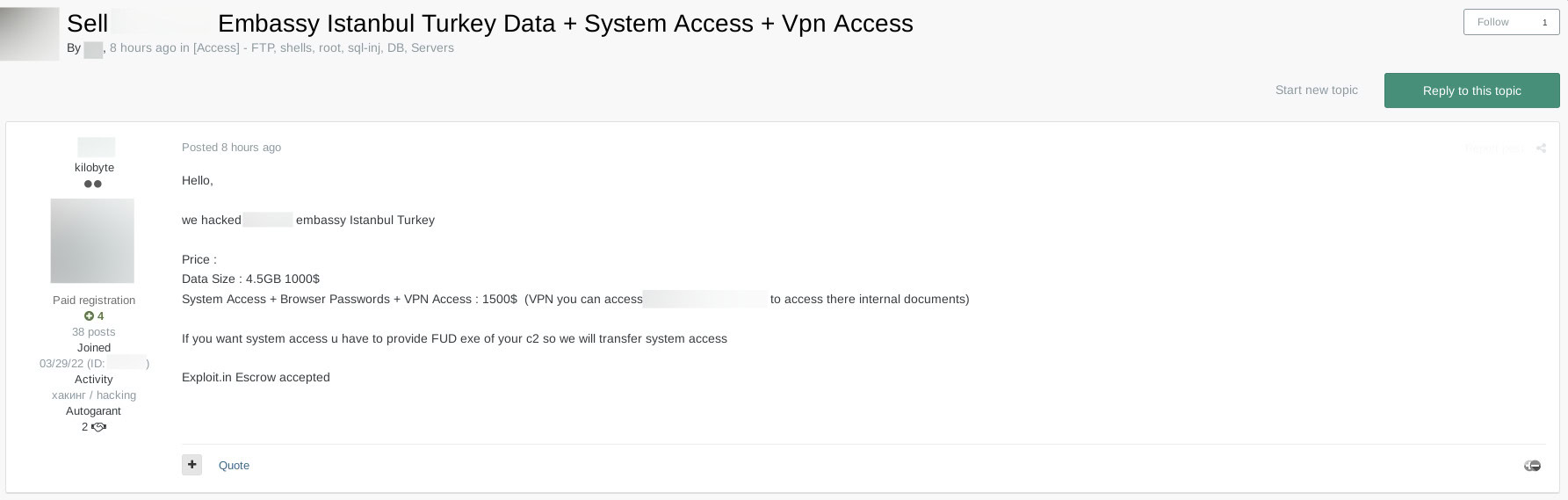
What’s Sold on Exploit?
Exploit provides a meeting place for cyber threat actors. The anonymity provided by this platform fuels a thriving underground economy centered around:
- Stolen personal data
- Credit card information
- Stolen credentials
- Ransomware
- Botnets
- Phishing kits
What makes Exploit particularly concerning is its accessibility. By enabling malicious actors of all skill levels to procure cybercrime tools and services, it significantly broadens the potential pool of cybercriminals. Furthermore, it fosters a community of collaboration, allowing cyber threat actors to share tactics, techniques, and procedures, thereby continually evolving their threat methodologies.
Exploit and IABs
The forum also acts as a platform for IABs. These brokers hack into business networks and sell the access they’ve gained, along with additional relevant information, to other threat actors. This “cybercrime-as-a-service” model creates a significant threat, as it allows threat actors of all levels to launch sophisticated attacks.
For businesses and organizations, understanding the workings of platforms like Exploit is vital in anticipating potential threats. Cyber threat intelligence plays a crucial role in this regard, providing insights into potential vulnerabilities, current threat actor techniques, and the latest trends in the cybercriminal underworld.
A Closer Look at a Black Market
Our own research into Exploit and the IABs who operate there emphasizes how they lower the barrier to entry for cybercrime. In the posts we studied, the average “blitz” price, which functions like “buy it now” in an online auction, was $4,699.31. But with the outliers removed, the average dropped to just $1,328.23. We saw listings as low as $150, and a few as high as $120,000.
As people who streamline and simplify cyber attacks for others, it comes as no surprise that IABs work hard to accommodate their clientele. They can sell access to high-value targets to elite hackers for top dollar. Most of the listings, however, targeted smaller companies and sold for prices any criminal could afford.
Just like someone selling on Amazon or Ebay, initial access brokers work hard to attract, acquire, and retain customers in an increasingly crowded and competitive market. The result for everyone else, unfortunately, is more stolen credentials, worse cyber attacks, and larger financial losses.
Seeing Beyond Exploit
Exploit may be one of the best-known marketplaces for initial access brokers, but it’s hardly the only place on (or off) the dark web where they operate. Some of the leading alternatives include:
- XSS: Many of the threat actors on Exploit also have a presence of XSS, a similar dark web site that auctions initial access and other illicit resources. It’s free and relatively easy to create a new account, making this forum attractive for people new to cyber crime and the IABs who want to sell to them.
- RAMP: Though similar in many ways to Exploit and XSS, Ramp distinguishes itself by allowing discussion of ransomware and allowing people to use Chinese and other languages rather than Russian and English exclusively. In that way, RAMP is extending access to IABs to cyber criminals in any country, no matter their motives.
- Telegram: This messaging app, which has lax moderation and a commitment to privacy, has become a hotbed for cyber crime, with thousands of channels connecting hackers with collaborators and resources. Telegram has taken a stronger stance against illegal activity since its founder’s arrest in 2024. Regardless, it remains as popular as ever with IABs and others helping to make cyber crimes more successful.
The Rise of Initial Access Brokers: A New Threat in Cybercrime
Once IABs have successfully breached the organizations’ defenses, instead of exploiting the access themselves, they sell it on platforms like Exploit. This access is then bought by other threat actors who conduct more targeted and potentially damaging attacks, such as ransomware attacks or data exfiltration.
Why is the Rise of IABs Concerning?
The rise of IABs is especially concerning due to several reasons:
- Their existence amplifies the potential damage caused by initial breaches, as access can be sold to the highest bidder, often more advanced threat actors.
- They have effectively made sophisticated cyber attacks more accessible, since now threat actors of various levels can purchase network access and launch their own attacks.
- This model also increases the overall efficiency of cybercrime, as it allows different actors to specialize and then collaborate, thereby escalating the overall threat.
The emergence of IABs underscores the constant evolution of cyber threats and the necessity for businesses to remain aware and adaptable. As part of a comprehensive Threat Exposure Management strategy, organizations would benefit from considering the risks posed by these brokers and ensure their defenses can counter this evolving threat. Understanding and monitoring these shifts in the cybercriminal world is essential to staying one step ahead and securing your digital assets effectively.
A Profile of One IAB
IABs can make it easier and more economical to keep launching ransomware attacks even if fewer and fewer victims pay.
Consider one IAB, ominously named “Toymaker” because they took the unique step of coding their own infostealer malware. It can steal credentials from any system where it’s deployed, or go further to create reverse shells and execute commands. More than just gaining initial access, the Toymaker takes steps to control a system before handing it off to another threat actor.
Unlike IABs that sell on auction sites like Exploit, the Toymaker works exclusively with a ransomware gang called Cactus. Essentially, the Toymaker gets the door open, then hackers seasoned in finding and encrypting sensitive assets handle the rest of the attack. This enables both sides to become experts in their respective domain, initial access and ransomware,yet still work together to maximize the potency (and profits) of attacks. It’s a win-win for both sides.
The Evolution of IABs
If IABs continue to evolve on their current trajectory, we can expect two results:
- More IABs overall.
Every year the cyber criminal ecosystem grows—more threat actors, more attacks, more losses, etc. IABs play an important role in helping cybercrime scale by making it easier for beginners to launch their first attack, while also making it easier for established hackers to launch more attacks. As demand for access grows, along with the supply of exposed credentials, expect to see more IABs in total, more posts selling access, and probably more marketplaces like Exploit, as well.
- Lowered the prices.
Many of their customers can’t or won’t pay high prices. What’s more, they don’t want to target high-value enterprises because of the higher risk. Just like any merchant eager to keep customers happy, IABs may lower the price of access over time. More credentials getting exposed combined with cheaper prices for initial access will likely lead to more companies, especially small and midsized companies, seeing damages as a result of cybercrime.
Strengthening Cyber Defense: Responding to the Threats from the Dark Web
In the face of an ever-evolving cyber threat landscape, punctuated by the proliferation of platforms like Exploit and the rise of IABs, fortifying cyber defenses has never been more crucial. There are several strategic steps that organizations can take to effectively respond to these threats originating from the dark web.
Prioritize Threat Intelligence
Forewarned is forearmed. Investing in comprehensive cyber threat intelligence is a critical first step. This involves proactively monitoring and analyzing information about potential attacks, threat actors, and their evolving tactics, techniques, and procedures (TTPs). It’s essential to understand not just your industry’s threat landscape, but also the broader digital underworld where these threats are conceived and traded.
Implement Robust Cyber Hygiene
This includes regular patch management to address software vulnerabilities, multifactor authentication, stringent access controls, and employee awareness training. Many breaches are the result of successful phishing attacks, making human error a significant vulnerability. Regular training can ensure your team is aware of the latest phishing techniques and other threats.
Adopt a Zero-Trust Approach
In a zero-trust model, every user, device, and network flow is considered potentially compromised and must be verified. This model minimizes the potential damage IABs can inflict, as access to critical resources remains restricted even if a network perimeter is breached.
Engage a Dark Web Monitoring Solution
Specialized solutions or services that monitor dark and deep web sources for stolen corporate data or threats against your organization can provide early warning of an impending attack.
Regular Incident Response Drills
Regularly testing your security team’s response to different types of cyber attacks can help identify areas for improvement and ensure your team is ready to respond effectively when a real incident occurs.
The dark web presents a substantial and evolving threat. By understanding its intricacies and the nature of threat actors like IABs, organizations can build robust defenses, effectively neutralizing these threats and securing their critical digital assets.
Monitoring Dark Web Cybercrime with Flare
The Flare Threat Exposure Management (TEM) solution empowers organizations to proactively detect, prioritize, and mitigate the types of exposures commonly exploited by threat actors. Our platform automatically scans the clear & dark web and prominent threat actor communities 24/7 to discover unknown events, prioritize risks, and deliver actionable intelligence you can use instantly to improve security.
Flare integrates into your security program in 30 minutes and often replaces several SaaS and open source tools. Learn more by signing up for our free trial.





