Today we’re covering two cybercrime research stories:
- React2Shell (CVE-2025-55182) vulnerability and chatter about it in cybercrime communities
- Gamers are a major target for threat actors through infostealer malware
Tune in to this story on Spotify, Apple Podcasts, YouTube (below), and/or keep reading this article for the highlights. We also have instructions for a giveaway in the video episode for CTF players who would like another shot at unlocking a shirt from a past challenge…
React2Shell (CVE-2025-55182) Vulnerability Chatter on the Dark Web
React2Shell is a newly disclosed vulnerability as of December 3rd (CVE-2025-55182) that has exposed a critical flaw at the core of React Server Components (RSC). This enables unauthenticated remote code execution (RCE) in applications using React 19 and frameworks that implement RSC, most notably Next.js. Researcher Lachlan Davidson disclosed the React2Shell vulnerability and wrote a detailed report.

Screenshot of Lachlan Davidson’s website React2Shell.com detailing the vulnerability (Source: React2Shell.com)
There may be more than 1.4 million publicly accessible instances worldwide that are running vulnerable versions, which creates a massive attack surface for exploitation.
We’ve been monitoring threat actors speaking English, Arabic, Chinese, and Russian, who are seeking and publishing code to find potential victims and exploit React2Shell. Learn more about the cybercrime conversations we’ve come across with screenshots.
For example, in this Telegram channel, there are discussions about the PoC circulating along with the claims that most don’t work and were possibly “developed” by AI.
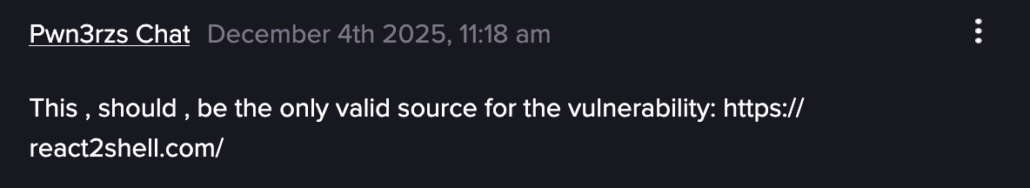
Message in the Telegram channel about the vulnerability (Flare link to post, sign up for free trial to access if you aren’t already a customer)
Recommendations to mitigate risks associated with React2Shell include:
1. Upgrade React RSC packages
Install patched versions immediately or whichever version line your project uses:
npm install [email protected]
2. Upgrade Next.js
Update to the nearest patched release (e.g., 15.3.6 or 16.0.7).
3. Redeploy your application fully
The vulnerability exists on the server, not in static output.
4. Audit transitive dependencies
Some bundlers and frameworks embed RSC internally – upgrading React alone may not be enough.
41% of Infostealer Victims Come from Video Game Files
We found that gamers are a major target of threat actors through fake games like Roblox, GTA, Fortnite, etc.
After studying 50,000 infostealer infections, these were our main findings:
- 41.47% of people (or about 2 in 5 people) in our study were infected through a gaming-related file of some kind.
- In addition, across all infections, 17.65% involved the victim downloading a “crack”/”cracked” version of the game, which made “crack” the most common claimed functionality in the study
People who play video games have long been a target for various types of malware distributed on file sharing or torrent sites, and the current “flavor” of malware is infostealers.
These infections can result in:
- Identity theft
- Financial loss (if credentials for a financial institution are stolen)
- Breached privacy (passwords, files, and personal habits can be exposed)
Legitimate software is expensive, but an infostealer log infection can be more costly. Always download from official sources when possible. Learn more about this analysis with Estelle Ruellan, Threat Intelligence Researcher:
Leaky Weekly and Flare Academy
Leaky Weekly is brought to you by Flare, Threat Exposure Management solution and industry-leading dataset on cybercrime that integrates into your security program in 30 minutes. Check out what’s on the dark web (and more) about your organization with a free trial.
Check out Flare Academy:
- Our free training series led by experts on critical topics such as threat intelligence, operational security, and advanced investigation techniques (earn CPE credits towards cybersecurity certifications)
- Our Discord community is a space to learn from and with cybersecurity professionals and students, check out previous training resources, and keep up with upcoming training