
By Assaf Morag, Cybersecurity Researcher
In June 2023, KNP Logistics (Knights of Old), a UK transport company with roughly 700 employees, collapsed after a ransomware attack reportedly triggered by a single weak password and lack of MFA. Systems were encrypted, operations ground to a halt, and the company never recovered.
Incidents like this highlight a hard truth: the most damaging ransomware events often become visible only after companies fail, not because they transparently disclose breaches, but because the consequences spill into layoffs, M&A fallout, or legal disputes.
SafePay ransomware exemplifies this modern extortion economy. Emerging rapidly in late 2024 and scaling aggressively through 2025, SafePay operates a classic double-extortion model – stealing data, encrypting systems, and publishing victims on Tor-based leak sites when negotiations stall. The result is a steady stream of organizations exposed publicly, many of which never reported an incident through official or regulatory channels.
We looked into 500 records related to SafePay ransomware leaks to analyze the data about victims.
Key Takeaways about SafePay Ransomware Victims
- The SafePay ransomware leak records that over 90% of the victims were small or mid-sized businesses, which have the ability to pay the ransom but not absorb the downtime
- Victims cluster in North America and Western Europe, with the United States and Germany standing out, which are regions where strict regulations like GDPR, NIS2, HIPAA, and breach-notification laws dramatically increase the cost of public exposure
- Analyzing leak data is valuable because a lot of this information is never disclosed publicly and can be difficult for security teams to learn from
Analysis of Our Findings
We sampled 500 records related to SafePay ransomware leaks and performed an analysis of recorded data, victims, and more.
SafePay Victims by Sector
Based on domain names, site structure, and business keywords (health, legal, industrial, services, etc.), victims fall into the following sector clusters:
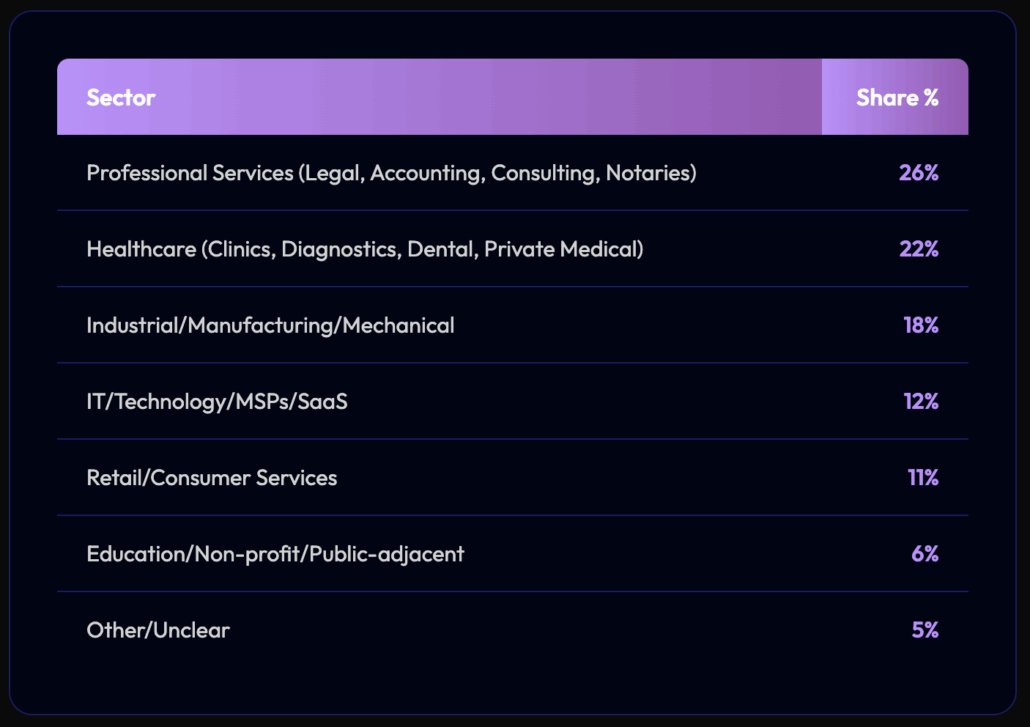
We found that about 66% of victims are service-based organizations. This is a disproportionate number compared to the total percentage of service-based organizations (which is much less than 66%). Therefore, this shows economic targeting of these types of organizations rather than opportunistic scanning.
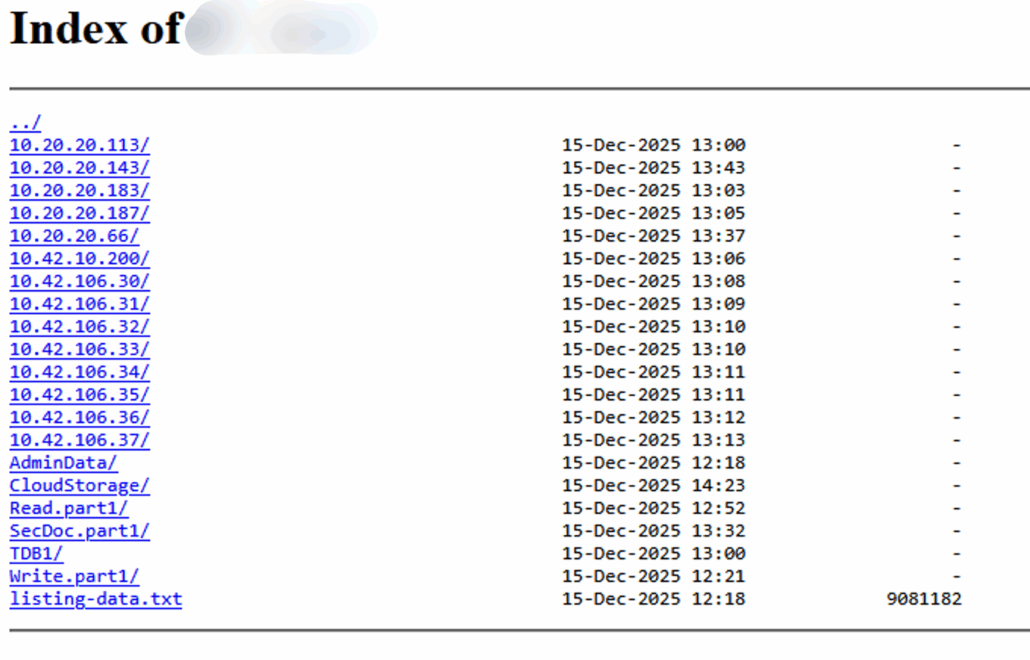
A screenshot from the Tor site leakage, you can see an internal network endpoint that leaked
SafePay Victims by Organization Size (Employees)
We analyzed the size distribution of the victim organizations:
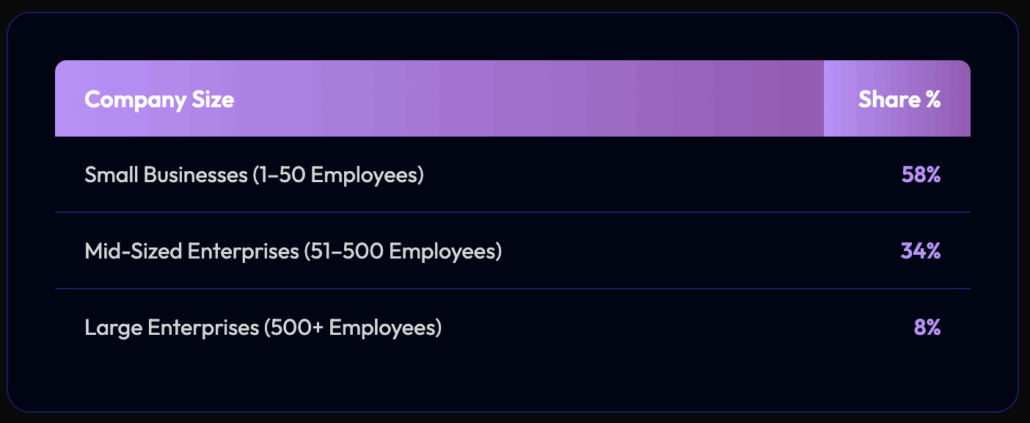
Over 90% of the victim organizations are SMBs. This implies that the main target profile is an organization that can pay, but can’t absorb the downtime.
Ransomware groups are not hunting Fortune 500 companies, even if they have a greater capability to pay. Perhaps with less internal bureaucracy, there’s also less legal escalation, and SMBs can pay ransoms faster.
SafePay Victims by Organization Size (Revenue)
Based on public-facing posture and service scope, the majority of businesses are local or regional providers at 64%, there are 28% national-level companies, and only 8% multinational enterprises.
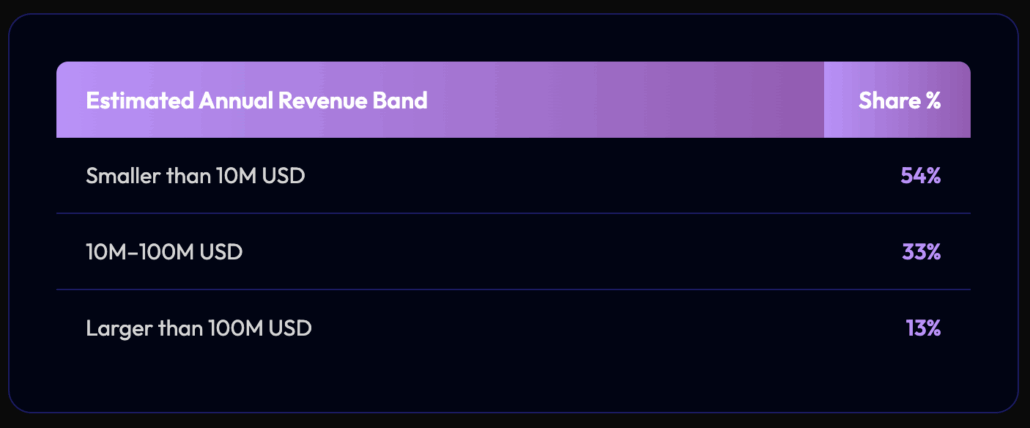
This draws a picture of meticulously targeted companies that are large enough to pay, but small enough to panic.
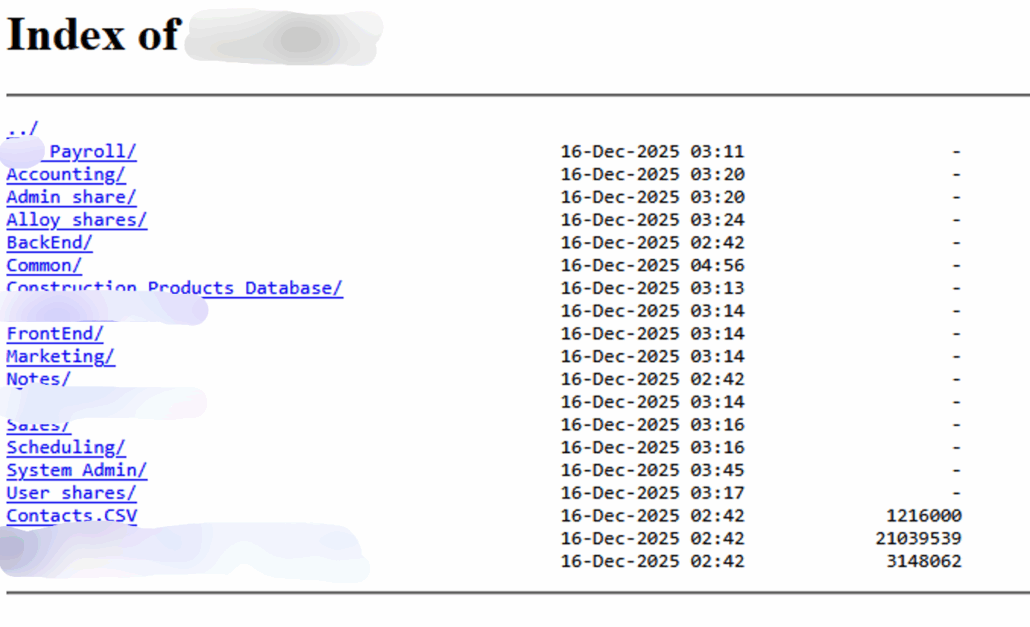
A screenshot from the Tor site leakage, with invaluable business operational data
SafePay Victims by Geographic Distribution
We analyzed the geo-location distribution of the victim organizations:
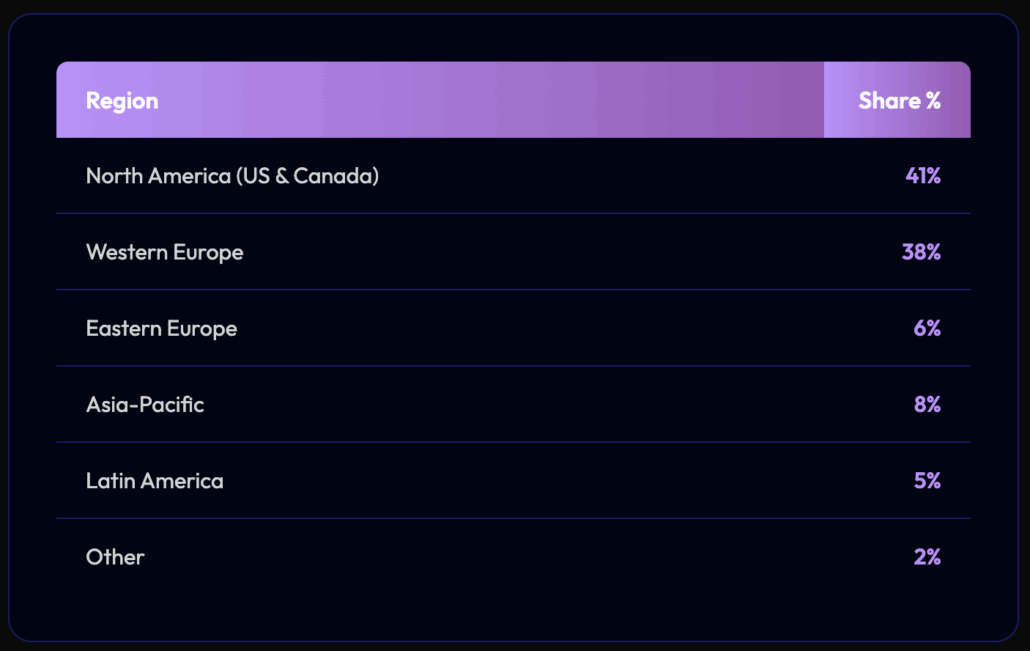
We found that 158 of the organizations were from the US and 76 were from Germany. This means that the victims cluster in high-GDP, high-regulation economies. GDPR-heavy regions are explicitly attractive extortion targets, and our analysis did not show a meaningful presence of low-income regions.
Ransomware groups don’t pick victims at random, but rather pick pressure points. Across this data set, the most common victims are organizations whose business operations depend entirely on IT availability, handle highly sensitive data (PII, PHI, legal or financial records), and operate with limited internal security resources.
When systems go down, revenue stops immediately; when data is stolen, the damage doesn’t end with recovery. This combination creates ideal extortion conditions, especially for small and mid-sized companies that lack the resilience of large enterprises but still carry significant legal and contractual obligations.
What makes EU and North American companies especially attractive is regulation-driven leverage. Laws like GDPR and NIS2 in the EU, and HIPAA, state breach-notification laws, and disclosure requirements in North America, dramatically raise the cost of public incidents. Attackers understand this and weaponize it: even a partial data leak can trigger regulatory scrutiny, lawsuits, reputational collapse, or insurance fallout.
That’s why many victims never publicly report attacks, and why ransomware leak data offers rare, unfiltered insight into real-world cyber risk that questionnaires, disclosures, and annual reports often miss.
SafePay Ransomware History, Growth, and Modus Operandi
Emergence and Rapid Scale (2024 – 2025)
Multiple trackers and vendors place SafePay’s first appearance in late 2024, followed by a sharp rise in 2025 to the point it’s repeatedly described as one of the most active groups during parts of 2025. Ecosystem tracking sites also show SafePay reaching hundreds of claimed victims with activity continuing into December 2025.
Core Business Model: Double Extortion + Leak Operations
SafePay is consistently described as running double extortion:
- Access + data theft (exfiltration)
- Encryption for downtime leverage
- Leak-site publication and pressure tactics if negotiation fails
Their infrastructure footprint includes multiple Tor endpoints and Tor leak sites.
Why your SafePay Leak Data Set is Invaluable
Not all companies report ransomware, and there is often little documentation in public.
- The European Union Agency for Cybersecurity (ENISA) has explicitly warned that publicly reported incidents are “only the tip of the iceberg.”
- ENISA’s threat landscape work also notes that operational impact is rarely documented and that under-reporting contributes to an intelligence gap.
- The UK has moved toward mandatory incident reporting proposals specifically because visibility is lacking.
- The FBI has long urged victims to report ransomware because authorities otherwise lack a comprehensive view.
So the unique data set on Flare functions like a shadow disclosure layer: it captures “claims” and “evidence artifacts” that may never appear in press releases, annual reports, or breach notifications.
How can you leverage this dataset?
Taking Advantage of Flare’s Data Set on Leaks to Build Your Defenses
Third-Party Hygiene (Vendor Risk/Supply-Chain Risk)
Leak-site victim data is extremely practical for third-party risk programs because it answers:
- Which vendors have a history of ransomware exposure? (even if they never told customers)
- Which sectors in your supply chain are repeatedly hit?
- Which vendors show repeat victimization across time? (high signal for weak controls)
When conducting your third-party risk program, you often send endless questionnaires, or use a third-party monitoring vendor. Flare’s dataset can complement these practices and provide actual invaluable intelligence on your third-party service provider.
M&A and Due Diligence
In M&A, ransomware history matters because it can alter:
- Valuation (downtime, remediation cost, lost customers)
- Representations and warranties risk
- Data integrity (“What else is missing?”)
- Post-merger integration risk (latent persistence, identity compromise, incomplete rebuilds)
Leaked data helps you understand if the organization in question had ever been listed by SafePay, or any other group in Flare (such as Lockbit, Cactus, Satana, etc).
Cyber Insurance Underwriting and Claims Intelligence
From an insurer’s perspective, ransomware leak data sets can support:
- Risk scoring beyond self-reported controls
- Adverse selection mitigation (companies hiding prior events)
- Portfolio analytics (which industries are repeatedly published by specific groups)
- Claims validation context (timeline sanity checks; evidence of data theft vs encryption-only)
And because SafePay’s ecosystem is high-volume, this is particularly useful for “baseline frequency” and “severity distribution” modeling, especially given the well-documented underreporting problem.
Setting Up a Third-Party Monitoring Program with Flare
As part of our analysis, we will demonstrate how you can set up your own third-party monitoring practice with the Flare.
Our first step was to limit our search to “ransom leaks.”
Ransom leaks filter
Below you can see how we started our search with the Top Level Domain of “onion.”
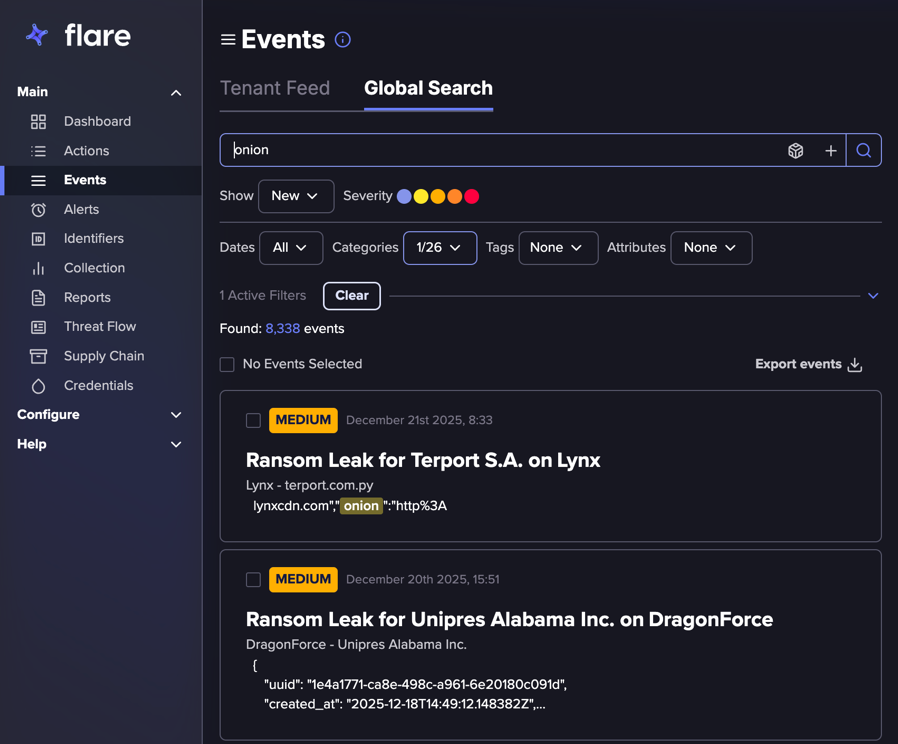
We searched for the Top Level Domain of “onion”
Thus far we just tested the volume and explored what can be found on the platform. Now we can continue with defining identifiers that will enable automated monitoring.
You can list the domains of the companies you wish to monitor.
Identifiers page
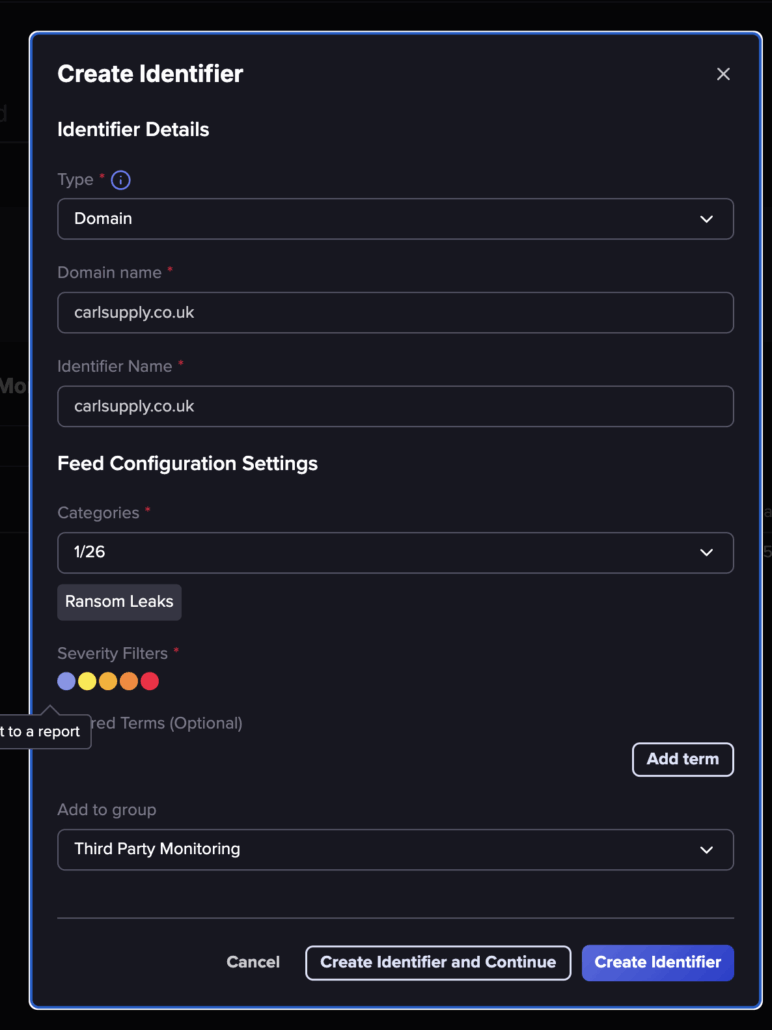
For instance, we search for “Carl supply” in the UK
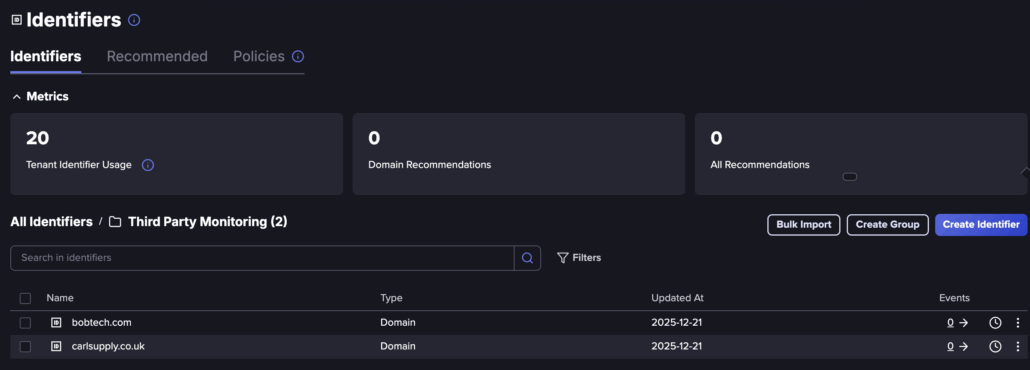
You can see we set a couple of identifiers
Next, we can set up an alert that will send us a notification, in case these domains appear in Flare’s ransom leak data corpus.
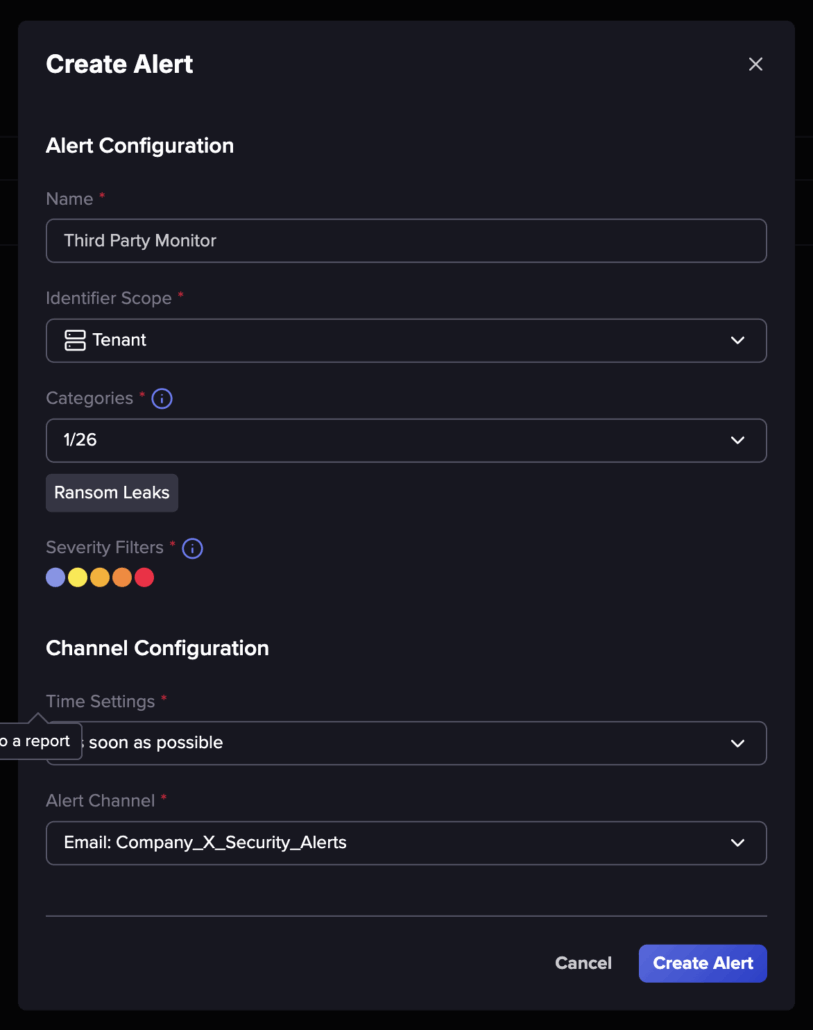
Configuring an alert with our company’s email, tenant scope, and ransom leak as a source
What Security Practitioners Can Learn from the SafePay Attack Analysis
Analyzing 500 SafePay ransomware leak records reveals a highly consistent victim profile. Roughly two-thirds of victims are service-based organizations (such as professional services, healthcare, retail, and industrial SMEs) with over 90% classified as small or mid-sized businesses.
These are companies that are operationally dependent on IT, handle sensitive data, and lack the resilience to absorb prolonged downtime. Geographically, victims cluster heavily in North America and Western Europe, with the United States and Germany standing out. Regions where strict regulations like GDPR, NIS2, HIPAA, and breach-notification laws dramatically increase the cost of public exposure.
This is what makes SafePay leak data so valuable. Because many organizations never disclose ransomware incidents, leak-site intelligence acts as a shadow transparency layer, exposing real-world risk that questionnaires, self-attestations, and annual reports routinely miss. For third-party risk management, M&A due diligence, and cyber insurance underwriting, this data provides rare, evidence-based insight into which companies, sectors, and regions are repeatedly hit, and where hidden cyber risk is most likely accumulating.
Ransomware Readiness with Flare
The Flare Threat Exposure Management solution empowers organizations to proactively detect, prioritize, and mitigate the types of exposures commonly exploited by threat actors. Our platform automatically scans the clear & dark web and prominent threat actor communities 24/7 to discover unknown events, prioritize risks, and deliver actionable intelligence you can use instantly to improve security.
Flare integrates into your security program in 30 minutes and often replaces several SaaS and open source tools. See what external threats are exposed for your organization by signing up for our free trial.





