
This article was updated on September 29th, 2025.
Threat actors who traditionally bought and sold malware, login credentials, and sensitive information on markets found on Tor (The Onion Router) are increasingly moving off the dark web and setting up shop on instant messaging platforms, such as Telegram. There, they can freely buy and sell illicit malware like OTP bots, which may endanger your organization’s security.
Why Are Threat Actors Leaving the Dark Web?
To understand why threat actors are moving away from the dark web, it helps to understand why they originally chose to use Tor. Tor allows for nearly completely anonymized browsing and website hosting with URLs ending in .onion. Traffic is routed through nodes hosted globally, usually jumping between multiple nodes before arriving at the intended destination, with traffic never leaving the network.
This provides for a high degree of anonymity, which is a benefit for threat actors, but also results in incredibly slow speeds, with .onion pages often taking in excess of a minute to load. In addition, large file uploads and downloads can take days or even weeks, depending on the size of the file. Information published to dark web markets and forums is also essentially permanent, given that government agencies and security companies continuously monitor and archive the dark web.
Social media messaging channels carry almost none of these drawbacks. They are made to be consumable, fast, and when a channel is infiltrated by law enforcement or security organizations, a new one can be created quickly. Although data is archived on messaging channels, it can feel more anonymous and less permanent than publishing files or information to the dark web, particularly since data can be set to automatically delete after a period of time.
While threat actors often use a collection of social messaging applications, Discord, Signal, TOX, Matrix, and Session are some favorites. Our research shows that as of January 2025, the most popular app for illegal activity is Telegram.
What is Telegram?
Telegram is a messaging app that offers its users both ease of use and anonymity. It’s popular among threat actors for several reasons: Telegram is free, user-friendly, offers encryption, and supports up to 200,000 members in a group as well as the ability to share files up to 4GB in size.
Over the years, Telegram has evolved into a cybercriminal ecosystem in its own right, rivaling traditional Tor-based cybercrime forums and marketplaces. The platform allows users to communicate with large groups of people, either by creating groups or through channels capable of broadcasting and sharing files with an unlimited audience. The channels are specialized and searchable.
What Malicious Content Can Be Found on Telegram?
Almost anything that can be found on a traditional dark web marketplace can also be found on illicit instant messaging channels.
Bank accounts, stolen credentials, one-time password bots, forged checks, and even infected devices can be easily purchased through Telegram, with many marketplaces focused on making the transactions and use of stolen information as easy as possible.
OTP bots, which are used to bypass 2FA and MFA controls, are an example of the sorts of malware sold on illicit Telegram channels.
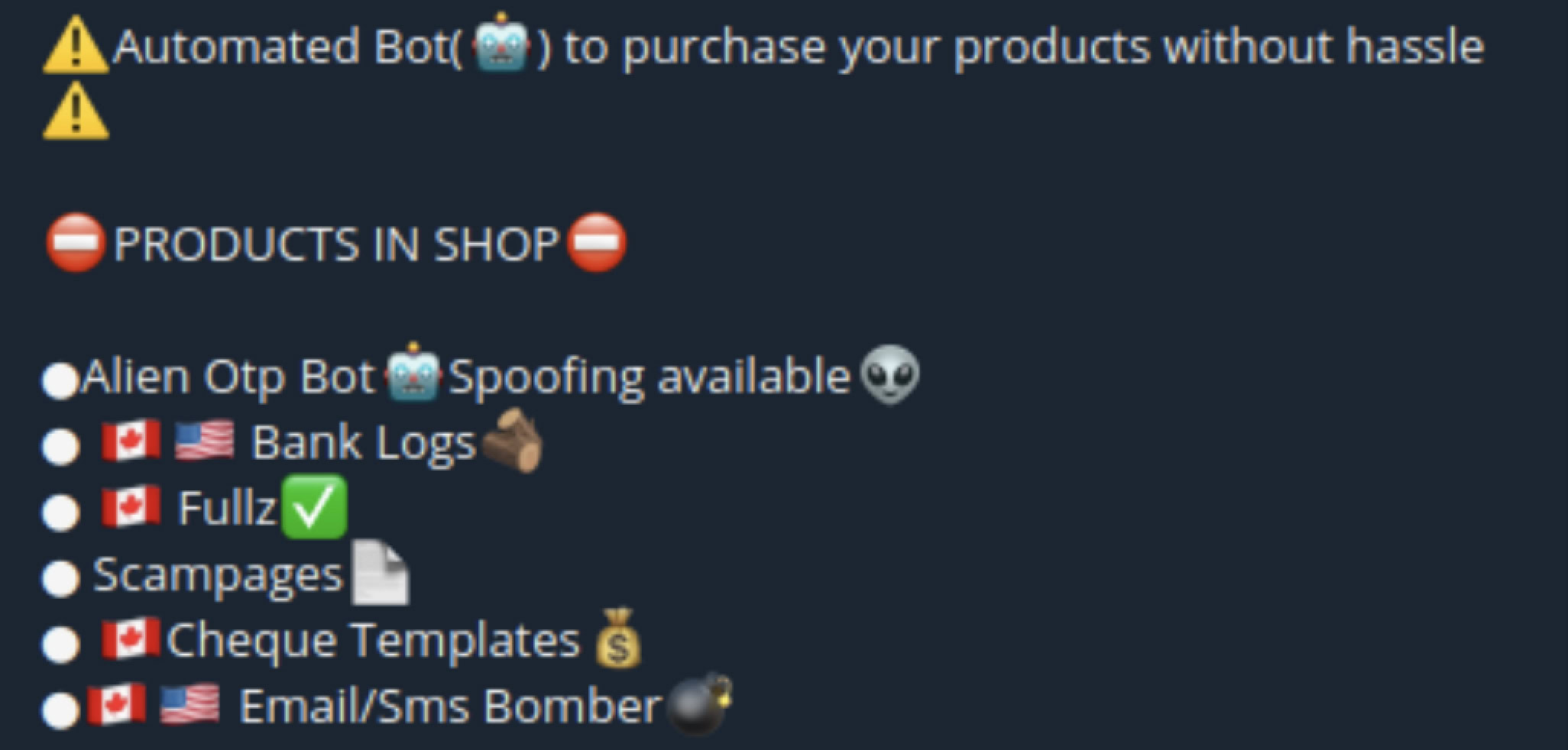
What Are OTP Bots?
One-time Password Bots (OTP bots) are essentially a method for threat actors to attempt to gather 2FA (two factor authentication) codes from victims at scale.
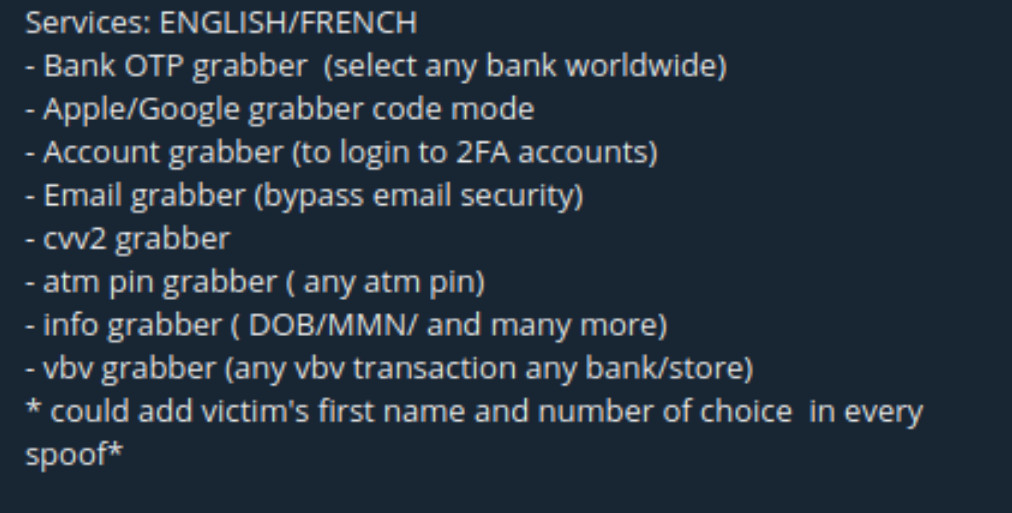
OTPs, or one-time passwords, are unique and temporary codes used in 2FA. A user inputs their regular password and an OTP, which is sent to their email or phone number, to gain access to their account. OTP bots were created to circumvent this additional security layer. They usually work like this:
- Threat actors purchase stolen login credentials on the dark web or use other methods to discover passwords.
- If an account has 2FA enabled, threat actors deploy OTP bots to steal the temporary code. Depending on the account targeted, the bot might send a text asking for a code, a robocall, or repeated push notifications on the user’s phone.
- The victim may fall victim to the scam and mistakenly grant access to threat actors.
Part of the reason for their popularity is that OTP bots don’t require technical skills. Threat actors can purchase them and deploy them against their chosen targets.
Defending Against OTP Bots
OTP bots are often used to facilitate personal financial fraud, but threat actors also use OTP bots to attack corporations.
It is not difficult to envision a scenario in which a data breach exposes hundreds of corporate logins. A threat actor can then find victims’ phone numbers using OSINT and leverage them to solicit one-time passwords and bypass two-factor authentication controls.
Tactics for Mitigating OTP Bot Attacks
Fortunately, there are many strategies that can help defend your organization against OTP bot attacks:
- Use compromised password detection: OTP bots don’t work if the threat actor can’t get the correct password. Your organization can greatly benefit from a strong password policy in place.
- Deploy advanced threat detection: Threat detection systems provide real-time alerts to potential threats to your organization. Advanced threat detection ensures a quicker and more effective response to any security breach.
- Conduct security audits: Regular security audits can help identify vulnerabilities that OTP bots might exploit.
- Secure OTP transmission channels: Some bots intercept one-time passwords during transmission. Encrypting communication channels or moving to more secure OTP delivery methods, such as hardware tokens or dedicated authenticator apps, can help.
Monitor for External Threats with Flare
The Flare Threat Exposure Management solution empowers organizations to proactively detect, prioritize, and mitigate the types of exposures commonly exploited by threat actors. Our platform automatically scans the clear & dark web and prominent threat actor communities 24/7 to discover unknown events, prioritize risks, and deliver actionable intelligence you can use instantly to improve security.
Flare integrates into your security program in 30 minutes and often replaces several SaaS and open source tools. See what external threats are exposed for your organization by signing up for our free trial.





