
One-time password (OTP) bots have rapidly gained notoriety for their capabilities to compromise the strongest systems.
These advanced malware programs are designed to bypass security measures that rely on OTP systems. These systems are commonly used in two-factor authentication (2FA), which is widely seen as a robust method for securing digital identities and information.
Even though OTP systems add an additional layer of security beyond passwords, as with any security measure, there is some level of risk. Read more to learn about OTP bots, their impact, and mitigation methods.
Understanding OTP Bots: Their Function and Operation
How Do One-Time Passwords Work?
To fully grasp the potency of OTP bots, it’s essential first to understand how the one-time password system functions. A typical OTP system generates a unique, temporary code that the user must input, along with their regular password, to gain access to an account. This code can be delivered via different mediums, such as text messages, emails, or specialized apps. The idea is to add an extra layer of security; even if a malicious party gets hold of the user’s main password, they still need the OTP to access the account.
What is an OTP Bot?
These crafty malware programs exploit various tactics to bypass this additional security layer. Some OTP bots employ sophisticated phishing methods to trick users into revealing their OTPs. Others may infect the user’s device to intercept OTPs directly, essentially beating the system at its own game.
The operation of OTP bots largely depends on their design and the specific vulnerabilities they are built to exploit. For instance, some OTP bots target vulnerabilities in the software used to generate or transmit the OTPs, while others focus on user behavior, leveraging social engineering techniques to trick users into unwittingly providing their OTPs.
Threat actors sell OTP bots on platforms such as illicit Telegram groups like in this screenshot below.
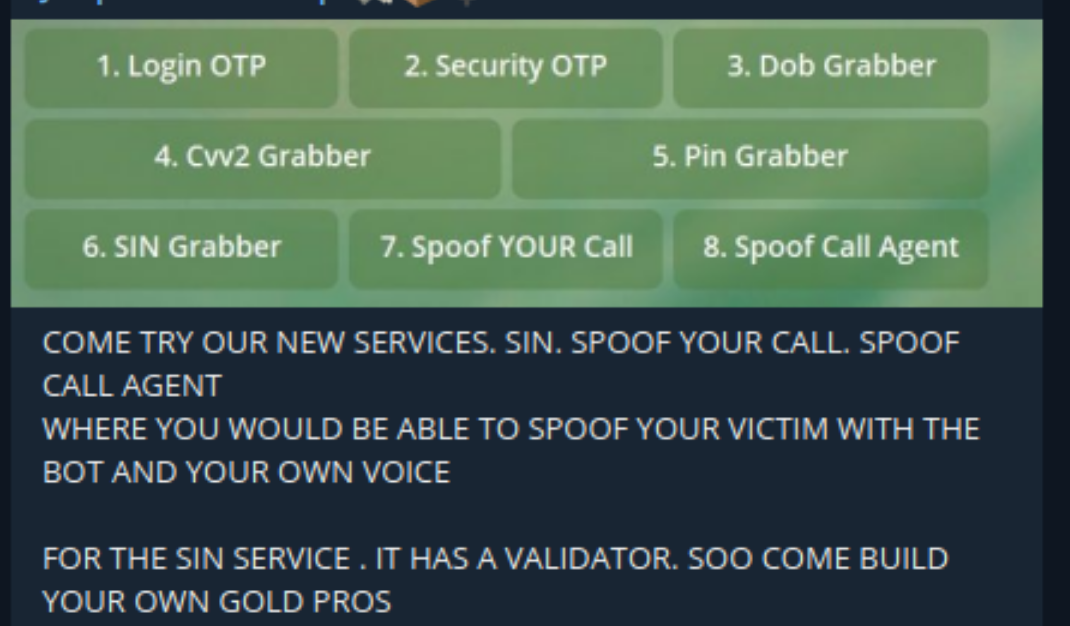
Screenshot from Telegram of a threat actor post advertising phone-related fraud items including OTP bots.
Recognizing the function and operation of OTP bots is the first step towards comprehending the scale of the threat they pose.
The Impact of OTP Bots on Cybersecurity Landscape
OTP bots have significantly reshaped the cybersecurity landscape, prompting businesses and security experts to reassess the reliability of one-time password systems. These sophisticated cyber threats have demonstrated the ability to exploit even the most robust security protocols, necessitating a proactive and informed approach to cybersecurity.
Weaknesses within OTP Systems
Previously regarded as one of the safest methods of securing digital information, the effectiveness of OTPs is under intense scrutiny. These bots highlight that no security measure is completely invincible, and a layered, multifaceted approach to cybersecurity is of utmost importance.
OTP Bots and Brand Reputation
OTP bots have intensified the already high stakes in the realm of data privacy. With the capacity to bypass OTP systems, they can gain unauthorized access to personal, financial, and business-critical information. This compromises not only the security but also the reputation of organizations, leading to potential loss of customer trust and legal implications. Protecting organizations against OTP bots is crucial to brand protection.
Need for Advanced Threat Detection for OTP Bots
Conventional security measures may not suffice against such sophisticated threats, necessitating investment in more robust and dynamic security technologies. For example, cyber analysts increasingly leverage AI and machine learning to detect and neutralize such threats.
Social Engineering and OTP Bots
Finally, OTP bots have underlined the importance of user awareness and education. Many OTP bot attacks succeed due to social engineering tactics, capitalizing on user behavior and lack of knowledge about potential threats. Therefore, businesses must emphasize comprehensive security training for all users, thereby enhancing their first line of defense.
OTP bots have shaken the cybersecurity landscape, necessitating a reassessment of current security protocols. By understanding their impact, organizations can implement more comprehensive, informed strategies to defend against these potent threats.
Strategies for Detecting and Mitigating OTP Bots Threats
With the ever-present threat of OTP bots, it’s imperative to develop effective strategies for detection and mitigation. As technology evolves, so does the sophistication of these bots, making it crucial for businesses to stay one step ahead. Here, we provide some strategic steps that can significantly reduce the risk posed by OTP bots.
Deploy Advanced Threat Detection Systems
Conventional antivirus software may not be equipped to detect sophisticated OTP bots. Therefore, businesses should invest in advanced threat detection systems that leverage artificial intelligence (AI) and machine learning (ML). These systems can analyze patterns, detect anomalies, and raise alerts when potential threats are identified, ensuring a quicker response to any security breach.
Regular Security Audits
Regular security audits can help identify vulnerabilities that OTP bots could exploit. These audits should encompass all aspects of your cybersecurity infrastructure, including:
- Software
- Hardware
- Network protocols
- User behavior
When CTI teams find weaknesses, they should address them promptly to prevent possible attacks.
Secure OTP Transmission Channels
Given that some OTP bots intercept OTPs during transmission, securing these channels is essential. This could involve encryption of communication channels or shifting to more secure methods of delivering OTPs, like hardware tokens or dedicated authenticator apps.
User Education and Awareness
A significant proportion of OTP bot attacks succeed due to user ignorance or negligence. Conduct regular training sessions for users to help them understand the threats posed by OTP bots and the importance of security protocols. Users should be educated about:
- phishing attempts
- the dangers of downloading unverified apps
- the importance of regularly updating and patching their software
Implement a Multi-Layered Security Approach
Relying on OTPs as the sole line of defense is risky. Implement a multi-layered security approach that combines OTPs with other security measures, such as biometric authentication, encrypted communication, secure firewalls, and advanced intrusion detection systems.
By understanding the risks posed by OTP bots and implementing robust strategies for their detection and mitigation, businesses can significantly enhance their cybersecurity posture. It’s a continual process that demands vigilance, adaptability, and proactive action—but the security and integrity of your digital assets are well worth the effort.
Mitigating OTP Bot Risks with Flare
OTP bots are complex and their ability to exploit weaknesses in OTP systems necessitate a robust, dynamic approach to security.
Flare automatically monitors illicit Telegram channels including ones in which threat actors buy and sell OTP bots. In addition, Flare monitors for other external threats including stolen credentials, leaked GitHub secrets, infected devices, and more. Request a demo to learn more about how we can help protect your organization.



