Table of Contents
- What is Cyber Risk Remediation?
- Sectors Most Prone to Cyberattacks Against Critical Infrastructures
- Why Cyber Risk Remediation is Critical to Your Risk Management Strategy
- 4 Steps to Accelerate Cyber Risk Remediation
- How Flare Helps Accelerate Remediation
- Effective Cyber Risk Remediation in Practice
- AI and the Future of Cyber Risk Resiliency
What is Cyber Risk Remediation?
Cyber risk remediation is the process of proactively identifying, addressing, and minimizing cyber threats that can adversely affect security and expose your organization, network, and customers to data breaches, ransomware attacks, and more. This article addresses the major causes of cyber threats within organizations and explains how a proactive approach to information security significantly lowers your chances of experiencing malicious attacks.
An effective cyber risk remediation strategy requires continuous visibility into your organization’s internal and external cyber vulnerabilities to significantly lower your chances of experiencing a malicious attack. To quickly identify new threats in real-time and mitigate them before they are exploited, companies need a comprehensive cyber risk detection strategy that can:
- Monitor the Dark Web
- Monitor Your Internal Attack Surface
- Monitor Your External Attack Surface
- Accelerate Reconnaissance
- Identify Leaked Credentials
- Prevent Targeted Threats
- Prevent Account Takeover Attacks
- Monitor Github for Source Code and Secrets Leakage
- Detect Technical Data Leakage
- Identify Misconfigured Servers
- Monitor Anonymous Sharing Websites
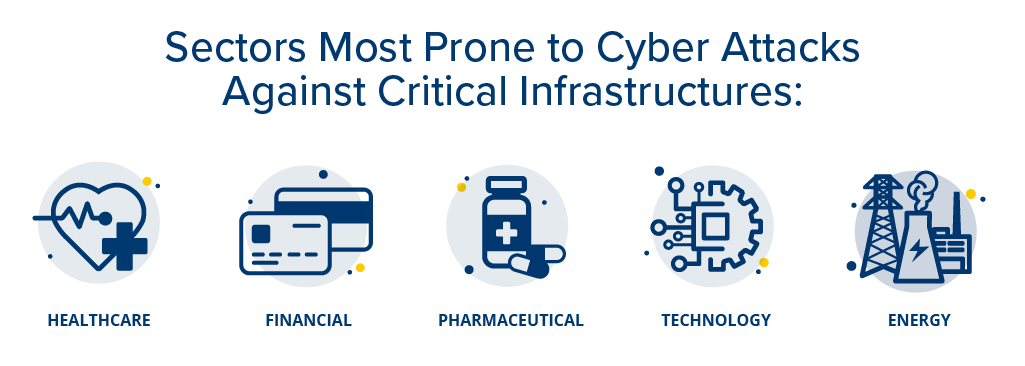
Sectors Most Prone to Cyberattacks Against Critical Infrastructures
Businesses of all sizes are continually susceptible to cyber threats. While every industry is vulnerable, the healthcare, financial, pharmaceutical, technology, and energy sectors are the most frequently targeted by cyber attacks against critical infrastructure.
Organizations in these industries provide target-rich environments for cyber attackers due to the nature of the information they possess, the monetary value of their data, and their importance to national and economic security.
Flare’s cyber threat intelligence solution ensures that businesses of all sizes can significantly reduce time-consuming alerts and efficiently contextualize and prioritize cyber risks to address critical issues rapidly. In addition, clients can secure personal and financial data to protect intellectual property from leaking online.
Why Cyber Risk Remediation is Critical to Your Risk Management Strategy
The worldwide pandemic, a fully remote or hybrid workforce, the rapid acceleration of digital transformation, and the increasing sophistication of cyber attacks have continued to threaten corporate security landscapes on a global scale. Therefore, navigating ever-evolving cyber risk has become more complex and costly than ever.
As it can be challenging to have a holistic view of an enterprise’s entire external attack surface at all times, many organizations are currently reactive when it comes to responding to cyber threats.

Without a proactive threat remediation process, organizations leave their network vulnerable to attacks and the potential for significant legal, financial, and reputational ramifications, often making it challenging to regain customer trust after a breach.

Flare’s solution begins with a transparent and quantifiable examination of your company’s cyber risk profile. Industry-wide, coverage describes the extent to which digital risks are monitored. In most cases, coverage is expressed in terms of the number of sites indexed by DRP to identify cyber risks.
Considering malicious actors cluster on niche websites with peers who originate from the same region or who commit the same form of fraud, this is an extremely valuable metric. Here are several dark web markets that cater to these malicious actors:

Therefore, identifying key sources of leaked information and collecting data when there is a potential risk is key to preventing threat actors from malicious cyber attacks on your organization.
Best Practices That Lead to Better Cyber Resiliency
In the face of escalating cyber attacks and a rise in breach attempts, it is imperative for companies to implement best practices for cyber resiliency. These include:
Minimizing Your Digital Footprint
Carefully select and deploy the right cloud services for your organization, implement effective patch management, and eliminate unnecessary or unused software and devices.
Adopting a Zero Trust Model
Ensure that only the correct people have proper access to essential resources and prevent unauthorized internal and external access to sensitive data.
Segmenting Your Network
Implement firewalls and methods such as microsegmentation to help limit potential damage caused by breaches and streamline your mitigation process.
Executing Secure-by-Design Principles
According to the Open Web Application Security Project (OWASP), one of the critical aspects of reducing an organization’s attack surface is implementing preemptive cybersecurity design decisions. This process is similar to limiting users’ access to specific functions. However, it is implemented at the design stage rather than after the fact when risks are well understood.
Minimizing Third-Party Access
Vendors, contractors, and other suppliers may not have the same level of security measures in place as your organization. Auditing their information security practices, requesting they mitigate risks by adding additional security controls, and shutting down access to third parties with unacceptable levels of risk will lessen your vulnerability.
Training and Educating Employees
Be aware that threat actors have a track record of targeting employees with great success. Educating individuals within your organization on digital, physical, and external threats and security best practices will reduce your attack surface area.
Continuous Monitoring
As threat actors rapidly advance their level of sophistication, continued observation and monitoring of your organization’s digital footprint to proactively identify risks is an essential component to protecting your organization against impending threats.
4 Steps to Accelerate Cyber Risk Remediation
An integrated cybersecurity strategy consists of multiple layers of security to identify, understand, prevent, and mitigate threats posed by cyber risks.
1. Cyber Risk Mapping
The first step in building a comprehensive cybersecurity program is identifying an organization’s vulnerable data, risk profile, existing controls, and security landscape. Extensive mapping of this diverse digital footprint helps security teams better understand their attack surfaces to implement a proactive approach to cyber risk remediation.
An attack surface refers to the total number of possible attack vectors (or points) through which an attacker or unauthorized user can gain access to a system and use that access to extract data or insert malicious code.
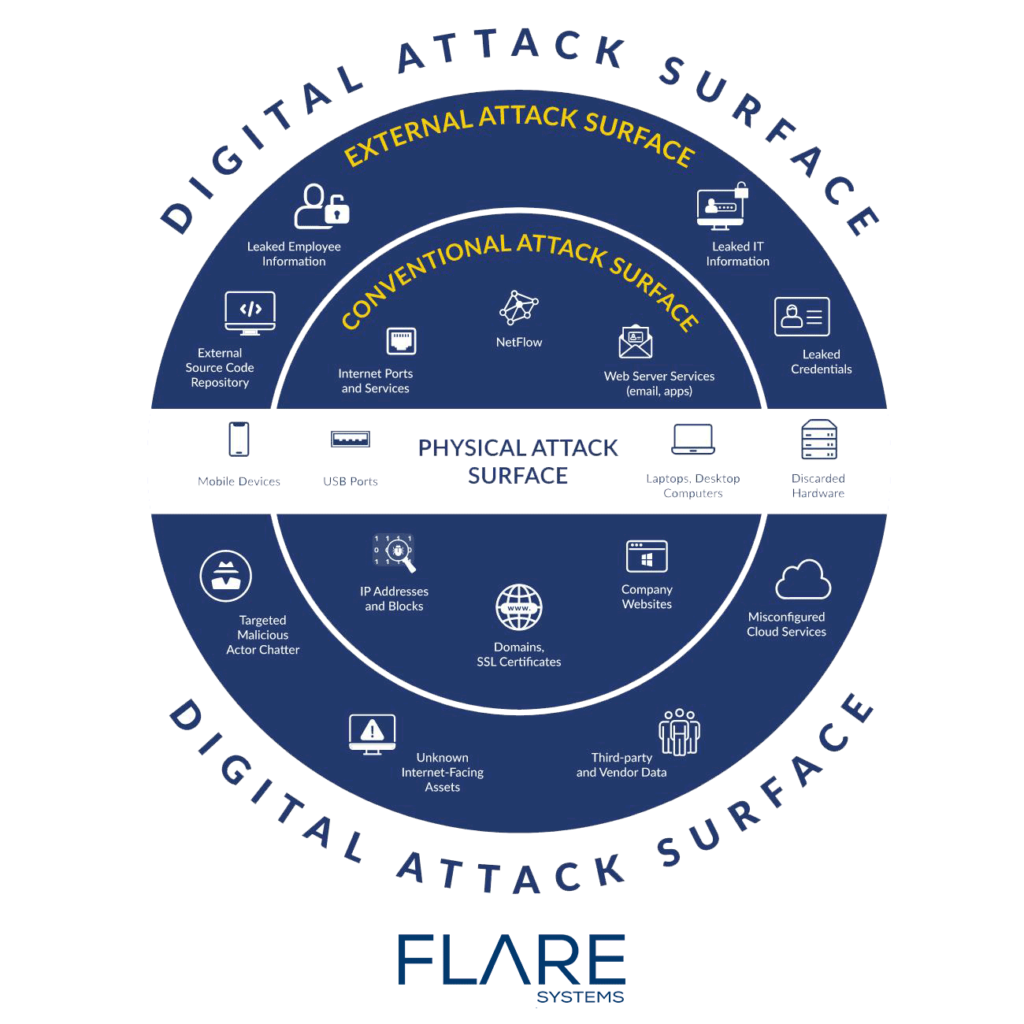
Attack surfaces are divided into two categories:
Physical Attack Surface – Physical attack surfaces include all endpoint devices used by an organization, such as desktops, hard drives, laptops, mobile devices, and USB ports in use (or unsafely discarded).
Digital Attack Surface – All of the hardware and software connected to an organization’s network constitute their digital attack surface. Applications, code, ports, servers, shadow IT, web applications, and company websites can all potentially contain multiple points of vulnerability, such as weak passwords, poorly maintained software, and default operating system settings.
External Attack Surface – To gain a complete picture of their cyber risk it is essential for companies to go beyond the conventional attack surfaces noted above and proactively monitor anonymous sharing sites and source code repositories for external attack surfaces, including:
- Leaked IT Information
- Leaked Employee Information
- Leaked Credentials
- Misconfigured Cloud Services
- Third-Party Vendor Data
- Unknown Internet-Facing Assets
- Targeted Malicious Actor Chatter
By leveraging a rigorously developed scientific methodology combined with an AI-driven data collection system, Flare’s solution monitors your digital footprint and alerts you to risk events in real-time. This allows organizations to identify weaknesses, assess vulnerabilities, and determine the next steps through visualizations. After the overall mapping is complete, organizations can then categorize these findings and reduce the time required to triage.
2. Threat Contextualization and Prioritization
Once you have a succinct categorized and prioritized list, a process to automate dissemination of this information to the appropriate security team members is integral to quickly securing your data and shoring up your organization.
At a high level, an effective threat contextualization process will assist in:
- Building a comprehensive list of the actors involved in the event
- Determining the intent of the parties (malicious or accidental)
- Understanding the sensitivity of the exposed data
- Identifying where the threat has occurred
- Connecting malicious actor behavior across various platforms
This tailored approach to cyber threat intelligence, outlined in our recent whitepaper, helps SOCs become more efficient in immediately detecting, prioritizing, and remediating internal and external threats and digital risks.
3. Cyber Risk Awareness and Communication
As threat actors typically post malicious services on multiple platforms, security teams are likely to receive numerous alerts per day. Excess noise creates inefficiencies as it could take up to several hours to thoroughly investigate a single warning.
Flare’s solution actively collects data from illicit platforms malicious actors use and provides your team with real-time alerts and intelligence reports, allowing you to filter out the noise and immediately focus on remediating the true threats while continuing to monitor the situation.
Download our whitepaper to learn more about how the management of these alerts via risk scoring provides rapid threat detection and increases your organization’s security posture while creating time and cost efficiencies.
4. Taking Action Against Cyber Risks
The last stage involves taking action against the risks identified in the aforementioned steps. While these steps vary by industry, size of your company, and risk profile, there are a number of measures you can take, including removing dangerous content from public sources, replacing leaked credentials, and introducing new security measures to prevent future data breach attacks.
How Flare Helps Accelerate Remediation
Since 2017, Flare Systems has been developing AI-driven technologies to protect your companies against malicious actors and human errors. Our solution analyzes and prioritizes billions of data points to deliver actionable intelligence through its intuitive yet straightforward platform to automate your dark, deep and clear web monitoring to provide you with real-time actionable intelligence.
Effective Cyber Risk Remediation in Practice
Malicious actors are continuously seeking ways to leverage human error, careless actions, and security vulnerabilities to infiltrate your organization’s systems.

Discover how Flare’s detection of leaked credentials on GitHub and a proactive response to preventing malicious actors helped a large Telecommunications provider save millions of dollars in incident response costs and fines in our latest white paper.
In a recent case, the Flare platform detected sensitive data that had been posted by a previous employee at a large financial institution. The CTI team promptly identified and notified the former employee’s superior, who contacted the individual in question and asked for the content to be removed. Less than 30 minutes after the alert, the content was removed from GitHub and the incident was contained. Read more about how proactive remediation, internal process security improvements, and improved protection streamlined this organization’s process and cut incident response times by 95%.
AI and the Future of Cyber Risk Resiliency
The use of artificial intelligence technologies such as machine learning and natural language processing can drastically reduce response times by cutting through the noise of daily alerts. Our AI-driven system provides your security team with sophisticated analyses to prioritize threats and take action to protect your organization’s sensitive data and brand reputation.