By Flare Research
React2Shell is a newly disclosed vulnerability (CVE-2025-55182) that has exposed a critical flaw at the core of React Server Components (RSC), enabling unauthenticated remote code execution (RCE) in applications using React 19 and frameworks built on top of RSC, most notably Next.js. Current telemetry suggests that more than 1.4 million publicly accessible instances worldwide are running vulnerable versions, creating a massive attack surface for opportunistic and targeted exploitation alike.
This critical 10.0 severity vulnerability was discovered by Lachlan Davidson and explained in detail here.
Key Takeaways:
- React2Shell is deemed critical because the vulnerability allows for unauthenticated RCE, increasing the chances of exploitation
- Flare’s platform has uncovered threat actors seeking and publishing PoCs to exploit React2Shell and how to find potential victims
- Active underground discourse among Russian, Chinese, English, and Arabic-speaking threat actors, all actively discussing and circulating methods for exploiting the vulnerability
- Recommendations to mitigate risks associated with React2Shell are:
- Upgrade React and react-dompackages to the latest version:
- Upgrade React and react-dompackages to the latest version
- Upgrade Next.js
- Redeploy your application fully
- Audit transitive dependencies
What Causes the React2Shell Vulnerability?
CVE-2025-55182 is mainly caused by insecure deserialization, in which attacker-controlled inputs are parsed and expanded without sufficient validation or sanitization. This is a critical vulnerability with 10.0 severity because it does not require authentication; instead, a single crafted HTTP request is enough to trigger RCE, which makes it trivial and easier to exploit. Additionally, React is widely used.
In vulnerable versions, this deserializer trusts client-provided metadata, allowing a threat actor to craft a malicious payload that:
- Injects unexpected object types into the server
- Tricks React’s internals into executing attacker-controlled code
- Results in full server compromise
| Vulnerable | Patched | |
| React | react-server-dom-webpack, react-server-dom-parcel, react-server-dom-turbopack Versions 19.0.0 – 19.2.0 | 19.0.1, 19.1.2, 19.2.1 |
| Next.js | Because Next.js heavily integrates React Server Components, it inherited the vulnerability | 15.0.5, 15.1.9, 15.2.6, 15.3.6, 15.4.8, 15.5.7, 16.0.7 |
The following are conversations we are tracking on the dark web and Telegram with Flare:
Given this is a 10.0 CVE, there is naturally interest from the cybercrime underground. Some attackers are looking for PoCs, and some are publishing links to PoCs.
In this Telegram “Pwn3rzs Chat” channel, there’s a discussion about the wide circulation of the PoC, but claiming that most of them don’t work and were “developed” by AI.
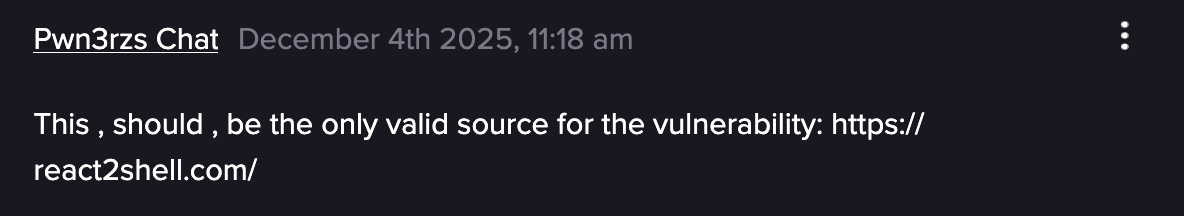
Message in the Telegram channel about the vulnerability (Flare link to post, sign up for free trial to access if you aren’t already a customer)
On the above-mentioned thread and similar, there are many links to PoCs on GitHub, and even a Nuclei template. Most of them are fake or invalid:
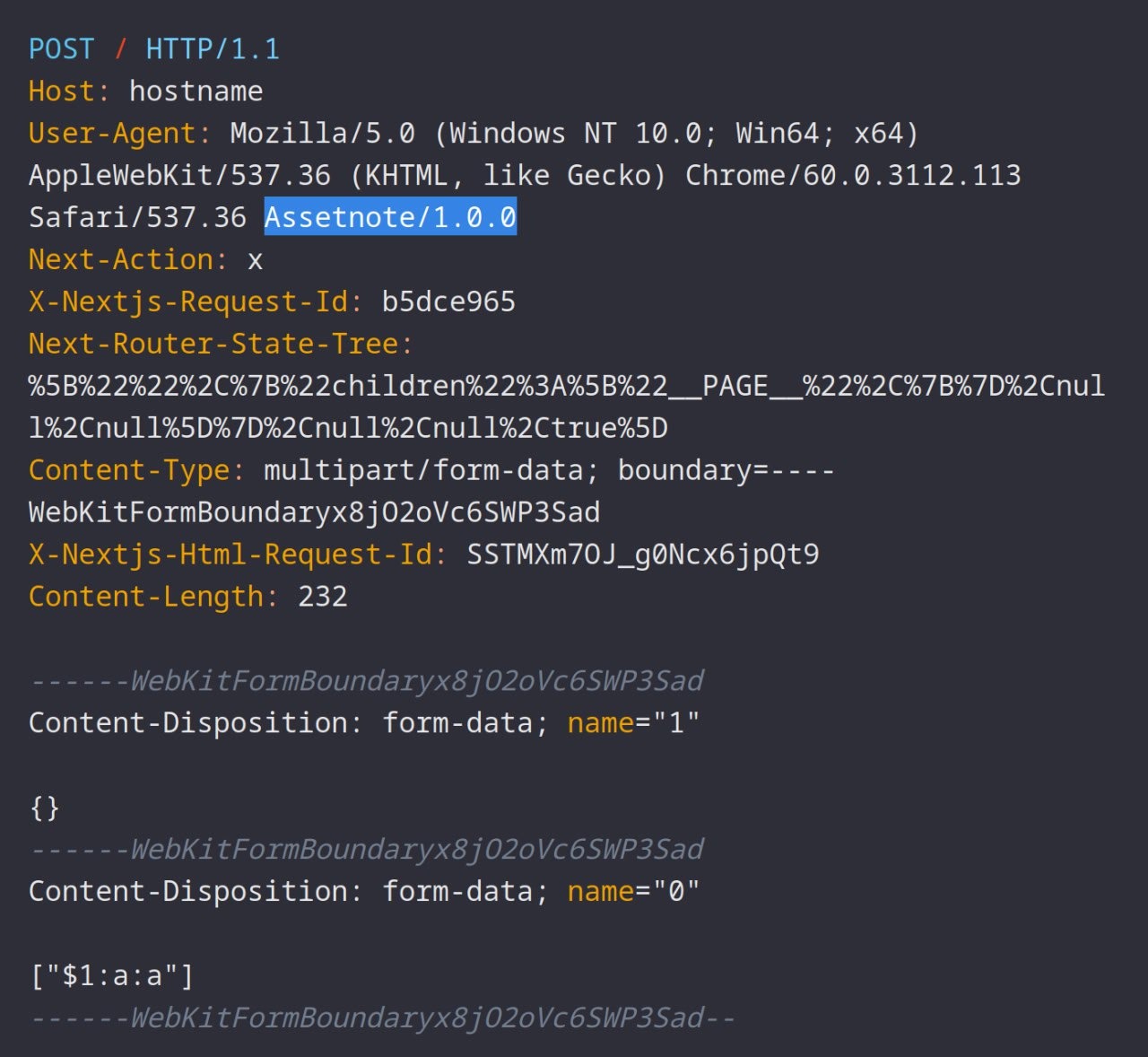
In another Telegram group, “WebPwnChat,” we observe an active discussion surrounding the vulnerability and the circulating proof-of-concept exploits. The conversation is driven primarily by several Russian-speaking threat actors. Notably, one message stands out, suggesting a potentially successful exploitation attempt.
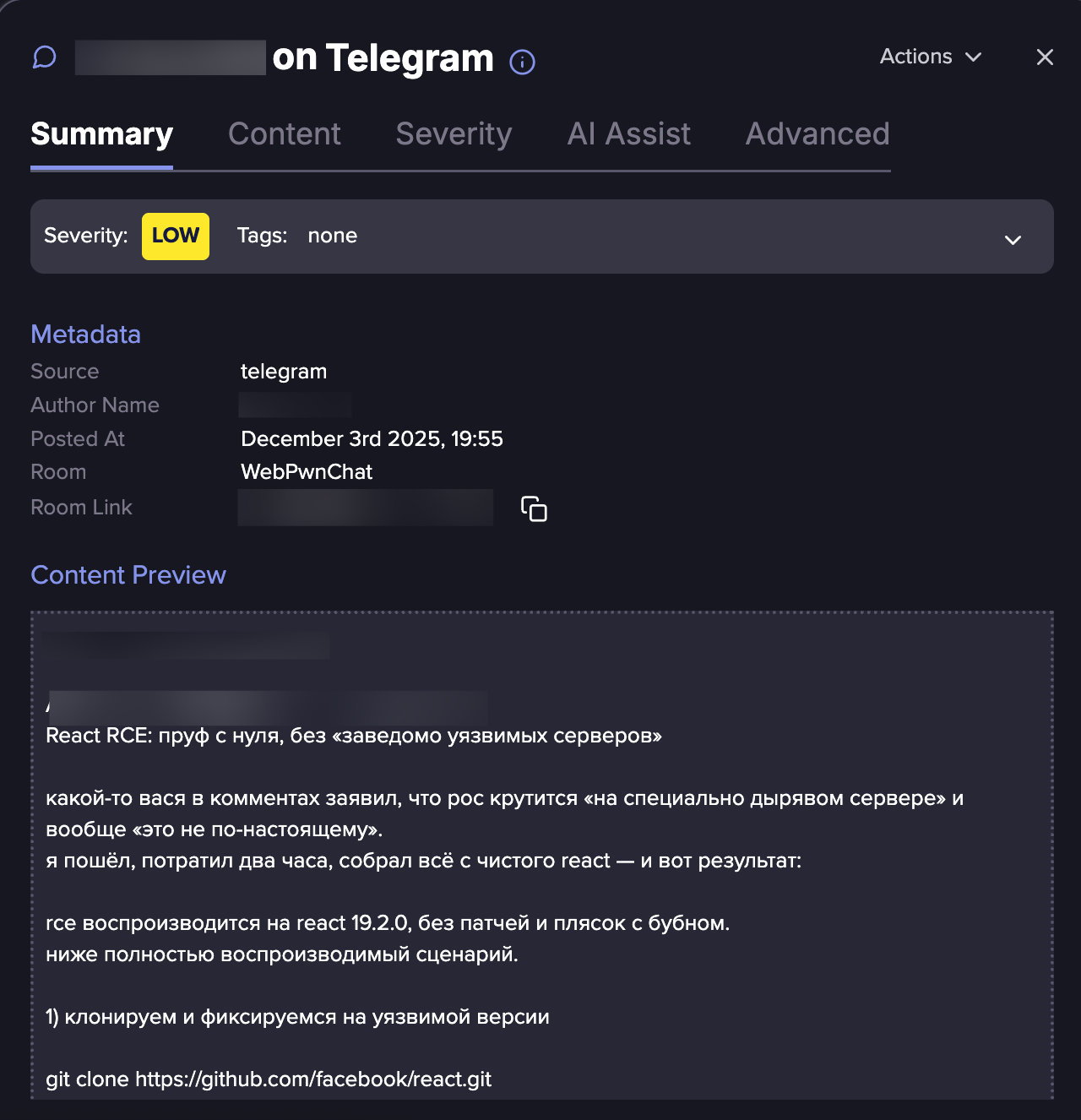
Telegram message of potentially successful exploitation attempt (Flare link to post, sign up for free trial to access if you aren’t already a customer)
This points to another Telegram channel where you can find a complete guide to the PoC.
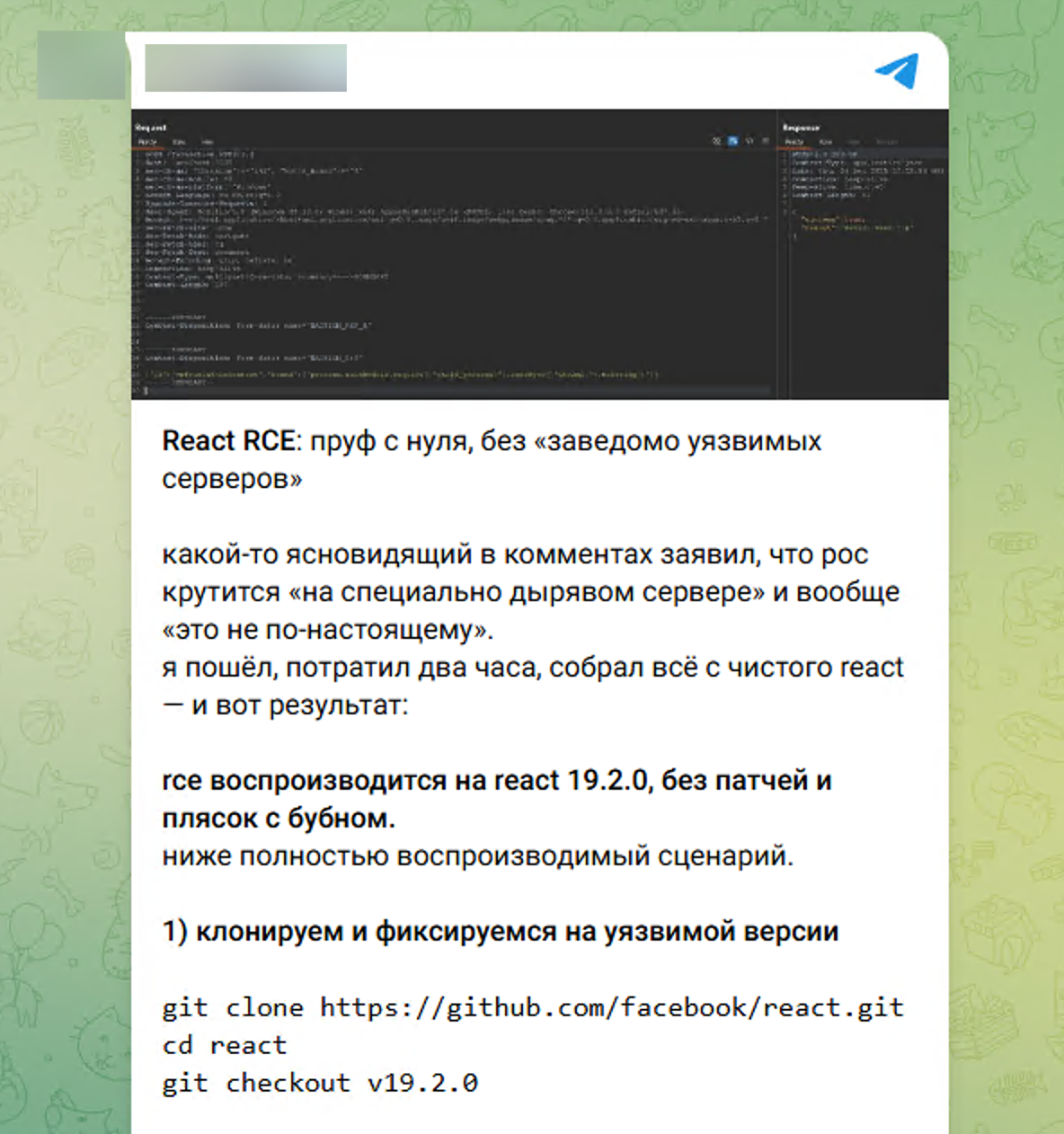
Telegram message with complete guide to the PoC
Without reproducing it, it’s hard to say if it works or not, but based on the discussion and the screenshot, it looks like it can actually cause RCE.
Related to the topic, Lachlan Davidson claimed:
“Many of these “PoCs” have been referenced in publications, and even some vulnerability aggregators. We are concerned that these may lead to false negatives when evaluating if a service is vulnerable, or lead to unpreparedness if or when a genuine PoC surfaces.”
To successfully exploit newly discovered vulnerabilities, two elements are required: a working exploit (such as the one identified above) and servers that remain unpatched. In the Telegram channel “Netlas.io”, a user under the same name (possibly affiliated with the platform, though not confirmed) often shares links and search queries for locating vulnerable targets.
In the case of this React vulnerability, the scale of exposure is significant. Current telemetry suggests that more than 1.4 million publicly accessible instances worldwide are running vulnerable versions, creating a massive attack surface for opportunistic and targeted exploitation alike.
Telegram message of researcher spreading awareness (Flare link to post, sign up for free trial to access if you aren’t already a customer)
Why CVE-2025-55182 is a Serious Threat
This vulnerability poses a serious threat because:
- It is unauthenticated, and anyone on the internet can exploit it
- Default installations are vulnerable
- RCE leads to full takeover: data exfiltration, credential theft, lateral movement, OS-level compromise
- There’s a huge ecosystem footprint: millions of React/Next.js deployments rely on RSC
This is why maintainers, cloud vendors, and security providers are treating CVE-2025-55182 as a critical infrastructure risk, not just another library bug.
CVE-2025-55182 Mitigation Recommendations for Security Teams
1. Upgrade React RSC packages
Install patched versions immediately or whichever version line your project uses:
npm install [email protected]
2. Upgrade Next.js
Update to the nearest patched release (e.g., 15.3.6 or 16.0.7).
3. Redeploy your application fully
The vulnerability exists on the server, not in static output.
4. Audit transitive dependencies
Some bundlers and frameworks embed RSC internally – upgrading React alone may not be enough.
Monitor for Emerging Threats with Flare
Flare helps security practitioners stay ahead of newly disclosed CVEs like React2Shell by continuously monitoring the clear and dark web and threat actor communities for early signals of exploitation. Flare’s collection includes more than 50,000 cybercrime Telegram channels, hundreds of cybercrime forums, ransomware leak sites, and dark web marketplaces, in addition to one of the most comprehensive sets of breached identity data in the industry.
See what external threats are exposed for your organization by signing up for our free trial.