
A phishing attack is any communication (email, SMS, instant messaging) campaign launched by a malicious actor to steal personal data and credentials. Phishing attacks are one of the biggest threats to data security. According to a Microsoft report, the frequency of phishing attacks grew by 250% between 2018 and 2019. Phishing has now supplanted malware as the preferred method used by malicious actors to steal data and credentials. It is estimated that 45% of all emails sent globally are spam messages.
Although there is no one way to successfully launch a phishing campaign, we set out to investigate what techniques Canadian fraudsters specifically use. To do so, we analyzed the phishing-related advertisements on Canadian illicit markets and chat rooms and engaged in discussions with over 10 malicious actors. In this first blog post, we present the 5-stage process that we identified:
- Collecting leads
- Designing the letters
- Sending spam emails
- Setting up scam pages
- Setting up a bulletproof (BP) hosting and domain registration
This process is most probably not used to launch all phishing attacks in Canada, but still provides valuable intelligence into the tactics and methods of Canadian malicious actors.
Stage 1: Collecting leads
The first stage of a phishing attack is to secure a list of potential victims’ emails. Because of the low response rate to spam emails (sometimes as low as 0.003%), phishers need mailing lists that count in the hundreds of thousands — if not millions — of emails to generate a profit. These emails are called leads in the criminal underground.
Email lists are publicly available on the internet for free (see Hunt’s The 773 Million Record “Collection #1” Data Breach for an example). These lists, however, often include many duplicates and inactive emails which reduce the effectiveness of phishing campaigns.
Phishers find more value in the email lists that are sold on illicit markets. For the right price, vendors offer tailor-made email lists from a specific geographic area, and stolen from a particular service or industry. These lists increase the likelihood of a successful phishing attack. The example below was taken from an illicit market where leads are sold by the tens of thousands and are classified based on the status of the victims, as well as their online activity.
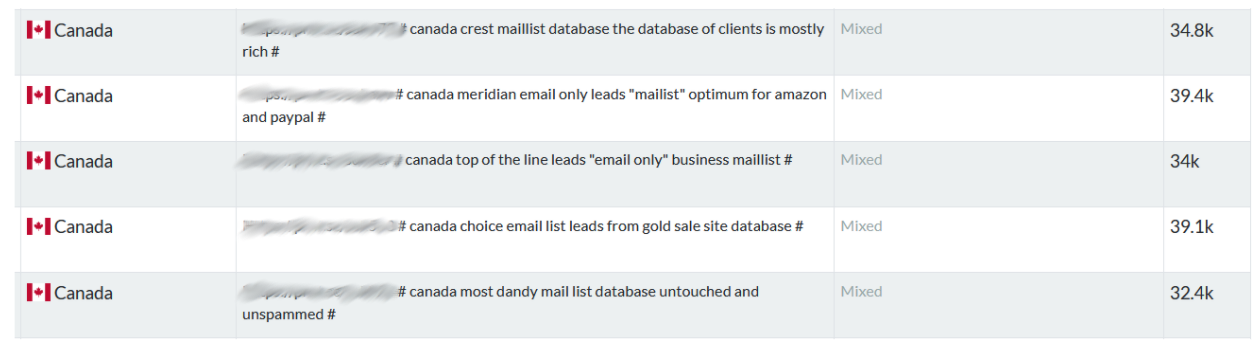
Our team conversed with a phisher to learn how email lists are built and priced. In the example below, the phisher offers a list of 100,000 Canadian emails for $150. This is in-line with the average pricing seen online for this product.
FLARE: You got an email list from canada?
MALICIOUS ACTOR: I don’t know yet. Let me check. I think i do though.
MALICIOUS ACTOR: You need .ca email addresses right?
MALICIOUS ACTOR: Those are straight from Canada.
FLARE: Yeah.
MALICIOUS ACTOR: I have 1 dump from a Canadian site.
MALICIOUS ACTOR: It’s fresh, depending on what you want to use it for. It’s from three months ago.
MALICIOUS ACTOR: The dump has 12,319 mixed emails and 4,492 emails ending in .ca.
MALICIOUS ACTOR: It’s small, sorry. I would give 1,000 for about $5. Is that a fair price?
FLARE: Do you have other .ca or Canadian emails from other dumps?
MALICIOUS ACTOR: Yo man. I had left a dump completely untouched from January. I think you’re gonna love it.
MALICIOUS ACTOR: All .ca I got from 2020.
MALICIOUS ACTOR: All dumped from Canadian/US sites. I would bump the price down to $1.50 per 1,000 since it’s almost 100,000 emails.
FLARE: Emails from merchant sites or forums?
MALICIOUS ACTOR: Mostly shops. 1 was a forum but i got only 88 .ca from it.
Securing a list of leads with a high degree of relevance is a crucial component in any profitable phishing campaign.This crucial first step completed, malicious actors can move on to designing the more complicated aspects of their campaigns.
Stage 2: Designing the letters
Phishers call the spam emails they send out letters. The role of letters is to convince the victims to click on a link that will redirect them to a phishing site. This is achieved through social engineering and by playing with the victims’ emotions of fear, curiosity and emergency. A common technique appears to include legitimate-looking attachments like receipts and service contracts to the emails and asking the victim to connect to their account as soon as possible. These documents can be auto-generated on websites and available for purchase for as low as $10.
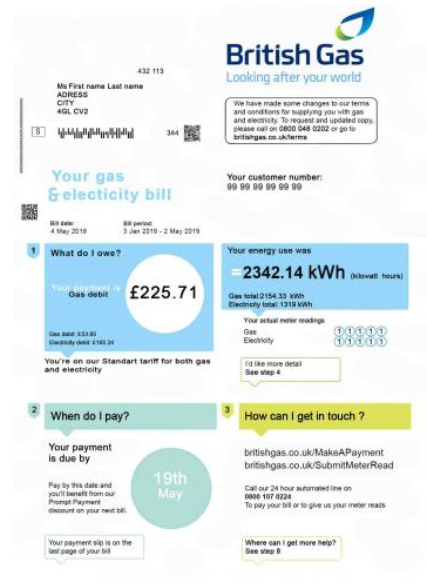
Image caption: fake invoice attached to a spam email to entice the victim to click on a link to look at their bill
Reaching a victim’s inbox in the first place is easier said than done. Filters have become so effective that few if any spam emails make it to the victims’ inbox. To increase their odds of success, phishers never use a direct link to their phishing site in their spam. Instead, phishers use programs that create unique links that redirect the victim through dozens of websites before they ever reach the phishing sites. This technique makes it difficult for automated and AI-powered tools to identify the true destination of the link found in the spam mail.
Spam filters also filter emails based on their content. Phishers therefore create unique letters that randomize their content and the underlying HTML code. This confuses even the most modern spam filters, and ensures that phishing emails reach their intended targets. The price chart below presents the costs phishers pay to add unique links (redirects) and randomization to their letters.
HTML letter without randomization: $50 – $60
HTML letter with randomization of a text part: $60 – $70
HTML letter with high randomization of a text part: $70 – $80
HTML letter with high randomization of a text part + randomization of a CSS code: $80 – $110
HTML letter with high randomization of a text part + high randomization of a CSS code: $110 – $120
—
500 redirects: $109
1,000 redirects: $169
—
Your letter will be done after 6 hours. If not, I will give you a 20% discount.
These features can add substantially to the costs of a phishing campaign. But without them, it would likely be more difficult to turn a profit on a phishing campaign.
Stage 3: Sending spam emails
Sending spam is a tedious process which requires a mass mailer, a specialized software designed to send a letter to tens of thousands of emails in the blink of an eye. Sales of these kinds of programs account for a small but significant share of all software sold on hacking forums.
The screenshot below shows the interface of a mass mailer software. Its very basic design makes it incredibly easy to use once the required information is provided.
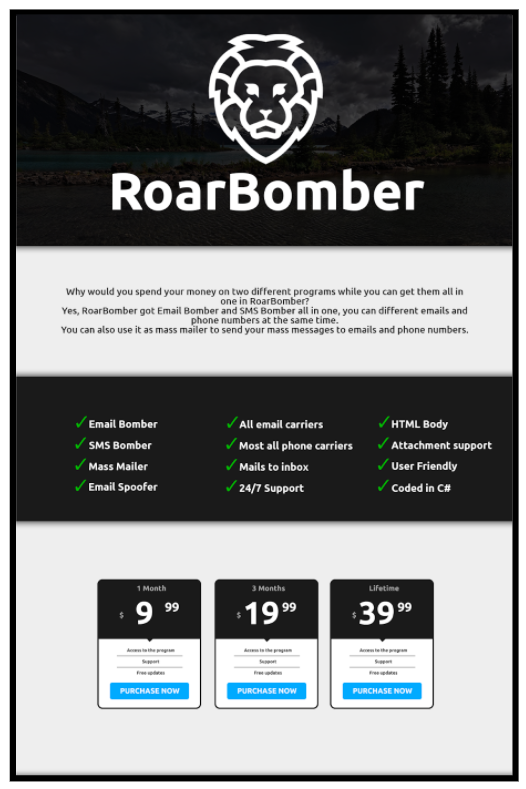
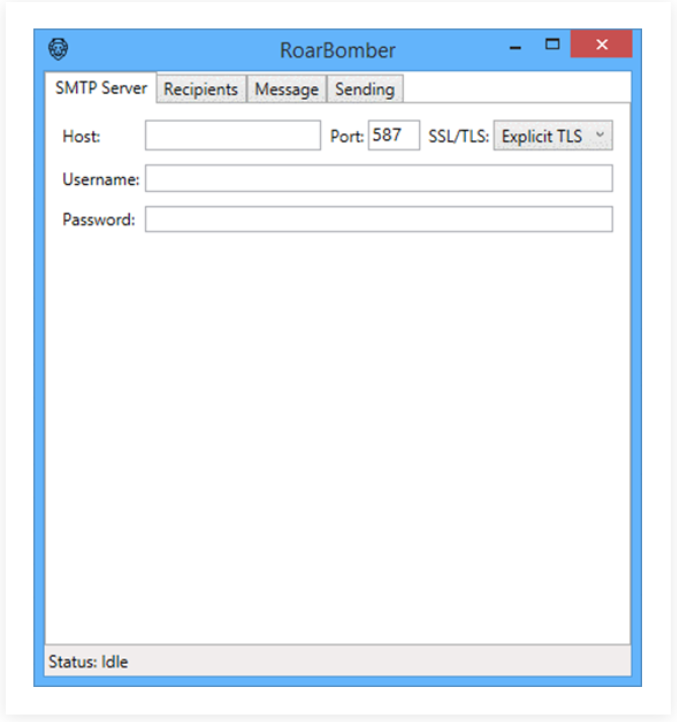
Image caption: An advertisement for a popular mass-mailer. For a relatively low cost, a scammer can use RoarBomber to send email and SMS spam.
Malicious actors must instruct their mass mailers what server to use to send the spam. Some manage to buy access to or hack into legitimate servers that have a good reputation for sending emails. This increases the odds of success of the spam campaign. Others buy access to or hack personal and corporate computers and install mail sending software on them.
Because of the tedious nature of sending spam, many phishers prefer to outsource the actual delivery of letters to professionals. The professionals have the infrastructure to send out hundreds of thousands of emails per hour and often charge between $50 and $250 per 100,000 emails sent. Significant discounts are also offered for bulk orders.
Phishers track if these subcontractors have sent the letters through referral links. Each of their subcontractors receives a different letter with a different phishing link. The phisher can use this to see which professional generated the traffic to their phishing site. This allows scammers to keep their subcontractors accountable.
Stage 4: Setting up scam pages
Hacking forums are abound with willing and capable web designers-for-hire, skilled in HTML and JavaScript. These individuals work in tandem with graphic designers to create look-alikes of commercial websites also called scam pages. In a survey yet to be published by our research team, of all the completed contracts on a popular hacking forum, graphic and web design agreements accounted for over half of all “non-criminal” transactions.
Phishers can also purchase premade template websites, painstakingly designed to mirror even the most minute details of a well-known site. Graphics, logos, and even interactive elements are recreated with a high degree of fidelity. It is also possible for phishing sites to link to the real images on legitimate sites. This may leave traces in logs that can help identify phishing sites, however. For scam pages targeting the Canadian market, web designers have even gone so far as to include bilingual elements. Mobile and desktop versions of these websites are equally available for phishers to purchase. We present below 9 examples of scam pages. Click on each to open them in a larger format and watch malicious actors test out the features of their pages.
Step 5: Setting up a bulletproof (BP) hosting and domain registration
Legitimate web hosts cooperate with companies when they detect a phishing site on their servers, and take down the scam pages. Phishers therefore use alternative web hosting services to host their scam pages. These services are either offered by registered companies in countries with little or no police enforcement, or by malicious actors who have hijacked servers all over the world and rent them out. The advertisement below taken from a hacking forum describes the costs to rent out a “bulletproof” hosting server.
Servers do not answer to (Digital Millennium Copyright Act) takedowns and are bulletproof.
Domains will be truly yours, not even FBI can steal them from you
Normal Virtual Private Server: $30 a year
Hosting unlimited scam pages: $3,600 a year
Private dedicated server, any task: $6,000 a year
Hosting services commonly also offer domain registration. In the past, phishers would buy domain names that looked like official ones (ex. Banofamerica.com to phish customers of bankofamerica.com). Best practices among phishers now suggest that subdomains may be more effective; the domain name would not matter as much to victims who struggle to differentiate between domains and subdomains (ex. bankofamerica.usbanking.com).
What can be done?
With so many individual actors working together and building on each other’s work, it is no surprise once again that the frequency of phishing attacks nearly tripled between 2018 and 2019.
Understanding the black market that fuels the phishing industry can provide an explanation for this rapid growth. With potentially thousands of malicious actors active in the phishing market, there is money to be made participating in these scams. A long supply chain with dozens of individual actors working together also means it will be near-impossible to ever fully eliminate the threat of phishing.
Understanding one of the biggest threats to your firm’s cybersecurity then is the best way to reduce the risk of being targeted by a phishing attack.





