The data and visualizations presented on this webpage are based on information collected from January 2024 to January 2025. These graphs are static and do not reflect real-time updates or recent developments. Any trends, insights, or conclusions should be interpreted with this timeframe in mind.

Executive Summary
- Telegram remains the dominant messaging platform in the cybercriminal underground, despite recent events and concerns about security.
- Increased cooperation between Telegram and law enforcement has prompted discussions about alternative platforms, with Signal showing the most significant growth.
- Other messaging apps like Discord, TOX, Matrix, and Session play niche roles, often tied to specific cybercriminal activities or communities.
- Many threat actors use multiple messaging apps to ensure accessibility and redundancy in their communications.
- Flare’s data lake analysis shows a correlation between messaging app choice and cybercriminal user types; for example, Discord is often used by low-level or young threat actors, while TOX is favored by OPSEC-focused and ransomware cybercriminals.
- The collection of contacts shared by threat actors on cybercriminal communities allowed Flare to automatically identify other handles that they may use on different forums by correlating the contacts.
Communicating in the Cybercriminal Underground – A Key Necessity for Threat Actors
Engaging in illegal activities within the cybercriminal ecosystem while maintaining anonymity and operational security presents a significant challenge for threat actors. Regardless of their level of technical expertise or the nature of their actions, one of malicious actors’ primary concerns is securing communications to avoid deanonymization and prevent becoming targets of rival groups or law enforcement.
At the same time, being easily reachable is equally important, as cybercriminals must maintain efficient and reliable channels to coordinate operations, recruit new members, and conduct illicit transactions. As a result, the balance between security and accessibility varies depending on the type of activity and the threat actor’s level of OPSEC awareness, with some prioritizing ease of communication for quick coordination while others emphasize stricter security measures to minimize exposure.
Given these problematics, cybercriminals often resort to exchanging sensitive information outside of forums, relying on messaging platforms such as Telegram, Discord, Signal, Tox, Jabber, Matrix, or Session to evade forum administrators surveillance or mitigate the fallout of potential database leaks [1].
For several years, Telegram has not only served as a communication tool widely praised by threat actors but has also evolved into a cybercriminal ecosystem of its own, emerging as a serious alternative to traditional cybercriminal forums. Telegram is free, valued for its user-friendly interface, API, bot deployment capabilities, support of up to 200,000 members in a group, and the possibility to share files up to 4GB in size. Nevertheless, concerns persist regarding its security. The platform does not enforce automatic encryption for all communications, and its encryption mechanism remains opaque, lacking independent expert review [2]. The rumors about the presence of its key developers in Russia have also raised alarms among the most security-conscious members of the cybercriminal community.
Eventually, the arrest of Telegram’s CEO and founder, Pavel Durov, in France the 25th of August 2024 [3], followed by the platform’s announcement of increased cooperation with law enforcement on September 23, 2024 [4] – along with the practical enforcement of this policy through the disclosure of cybercriminals’ IP addresses and phone numbers in January 2025 [5] – has sparked concern within the cybercriminal ecosystem (see Figure 1). Some threat actors started to discuss the idea of stopping using this platform or at least improving their OPSEC (see Figure 2).
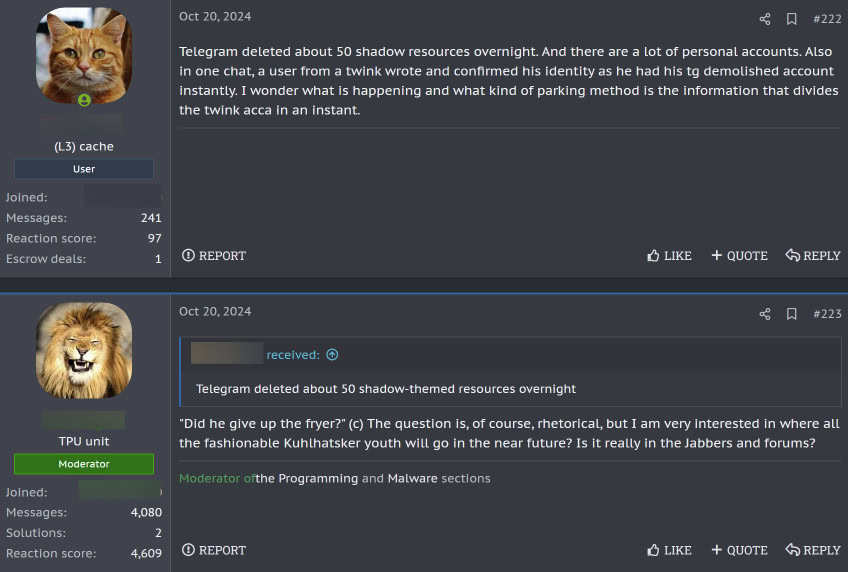
However, old habits die hard. The transition from a tool that is convenient, well-integrated into existing workflows, and broadly used within the cybercriminal ecosystem is not straightforward. Telegram is far from the first messaging service to face turbulence in this sphere, yet history shows that disruptions did not lead to an immediate or complete shift away from an established platform.
Indeed, in May 2023 a small tremor shook the Russian language cybercriminal forum XSS, when the threat actor “nightly” announced that he was selling a remote code execution vulnerability and an exploit affecting the qTOX 1.17.6 messenger for 20 Bitcoins (around $550,000 at the moment of the offer). The threat actor shared a proof of concept video (see Figure 3) where he claimed being able to retrieve a user’s IP upon acceptance of a new contact [6]. The vulnerability was allegedly sold in less than a day and caused many fears among qTOX users on XSS – predominantly malicious actors involved in ransomware activities. The alleged sale of this exploit deeply worried the Russian-speaking cybercriminal community and even pushed the administrator of XSS to abandon qTOX as an official communication tool.
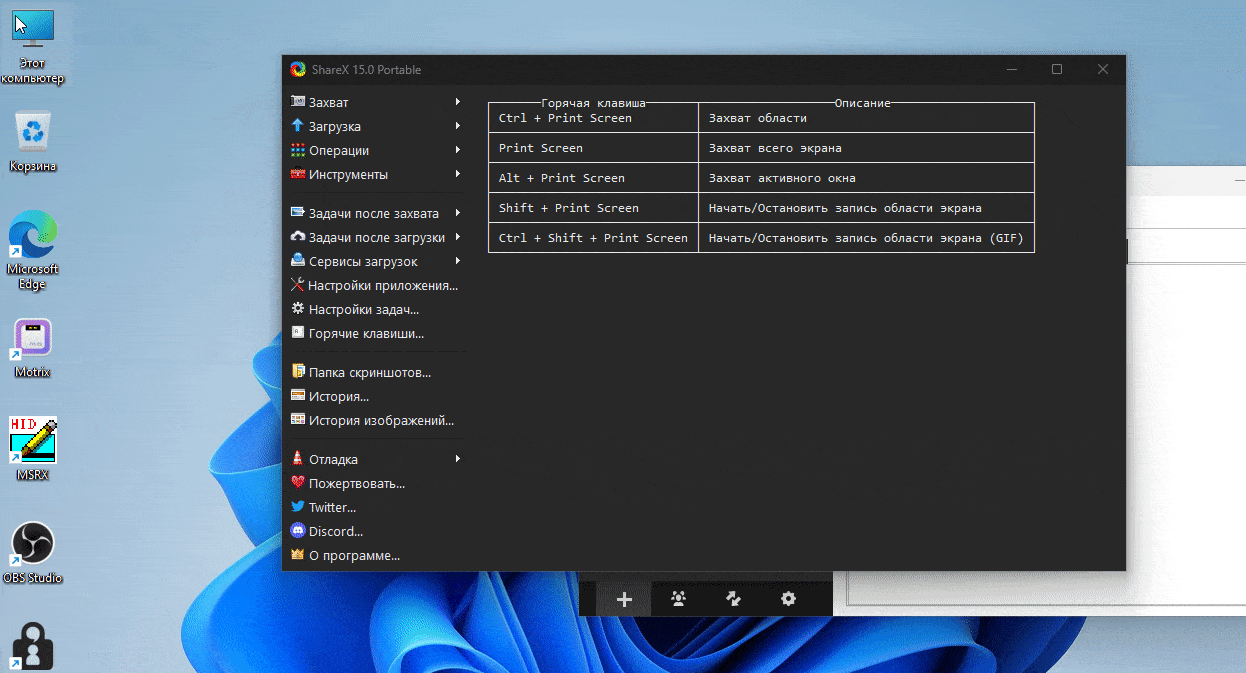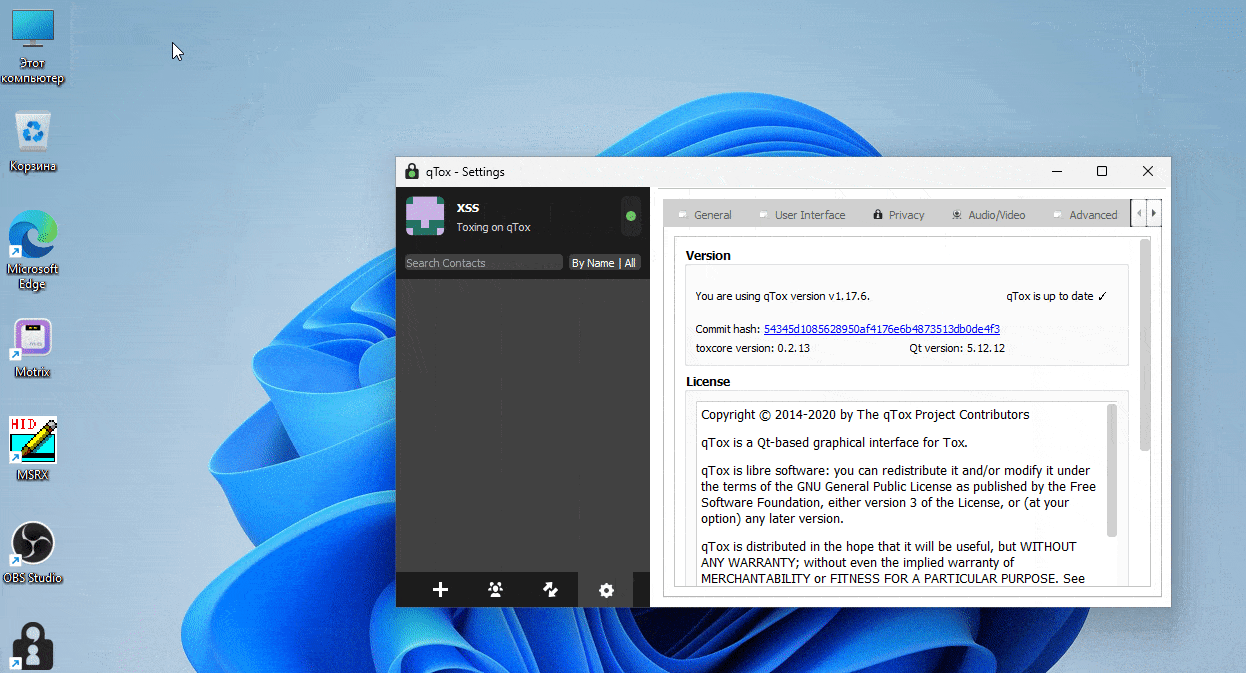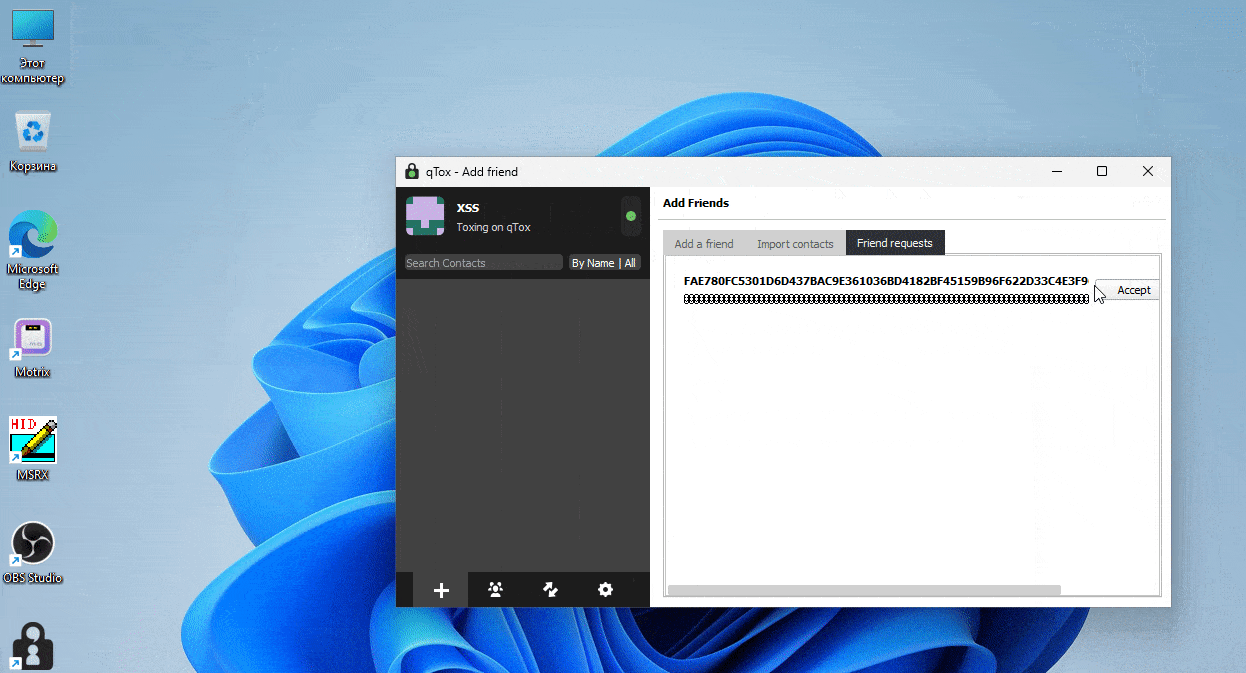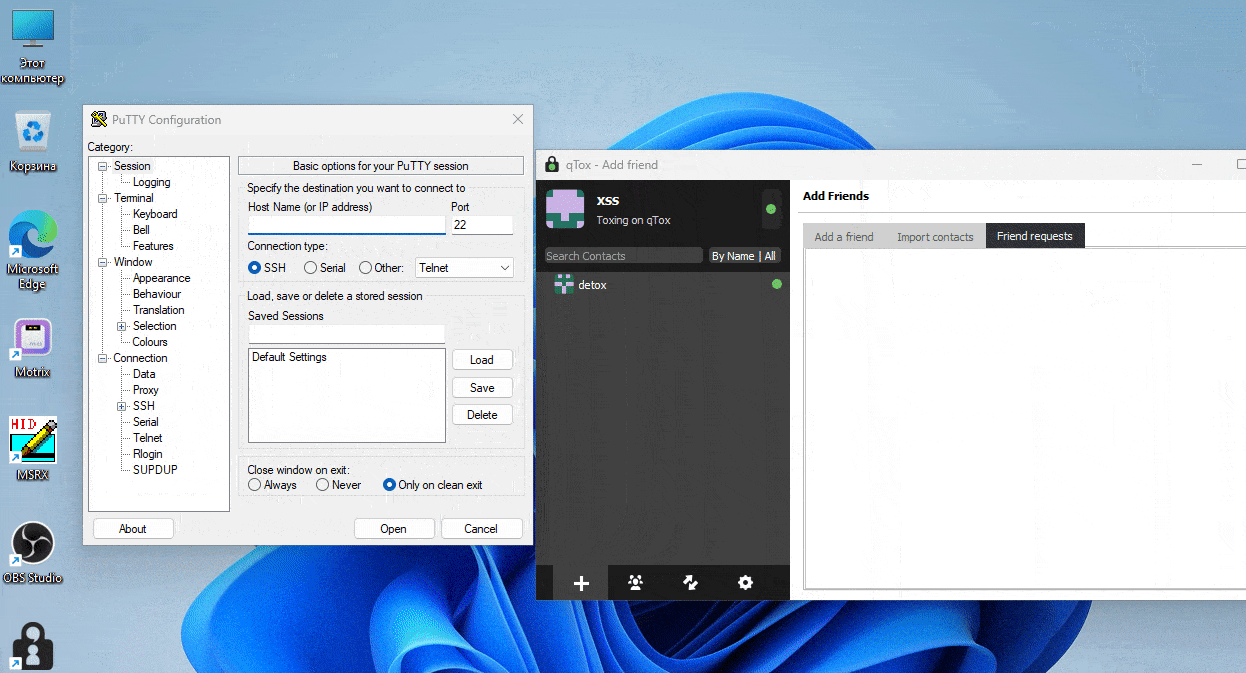
Both of these cases have sparked heated discussions about the right communication tool in the cybercriminal ecosystem (see Figure 4). However, several months later, it appears that things have not changed much; qTOX continues to be a niche messenger popular among a minority of threat actors and was recently updated [7], while Telegram seemingly continues to dominate as the preferred platform for cybercriminals, especially those involved in infostealer operations, carding, refund fraud, and hacktivism.
Given the significant developments affecting Telegram in 2024, we sought to examine the current state of cybercriminal communications. By analyzing Flare’s data lake, we aim to address the following questions:
- Have threat actors migrated en masse to alternative platforms since August 2024?
- Does the nature of a cybercriminal’s activity influence their choice of messaging platform?
In the following sections, we will explore these questions in depth, supported by data-driven insights.
I. Analysis of the Popularity of Messengers of the Underground: Making Sense of Raw Data
To answer aforementioned questions, we used Flare’s robust dataset. Flare has an extensive data lake of sources (i.e., market, forums, Telegram channels) focused on cybercriminal activities such as data leaks, initial access, malware, infostealers, carding, fraud, ransomware and marginally drugs. We use a subset of data consisting of 1 year (2024) of activities. These precisions are important because the data lake from which you pull information can heavily influence the output and we wanted to be as transparent as possible with our readers by explaining what our bias is.
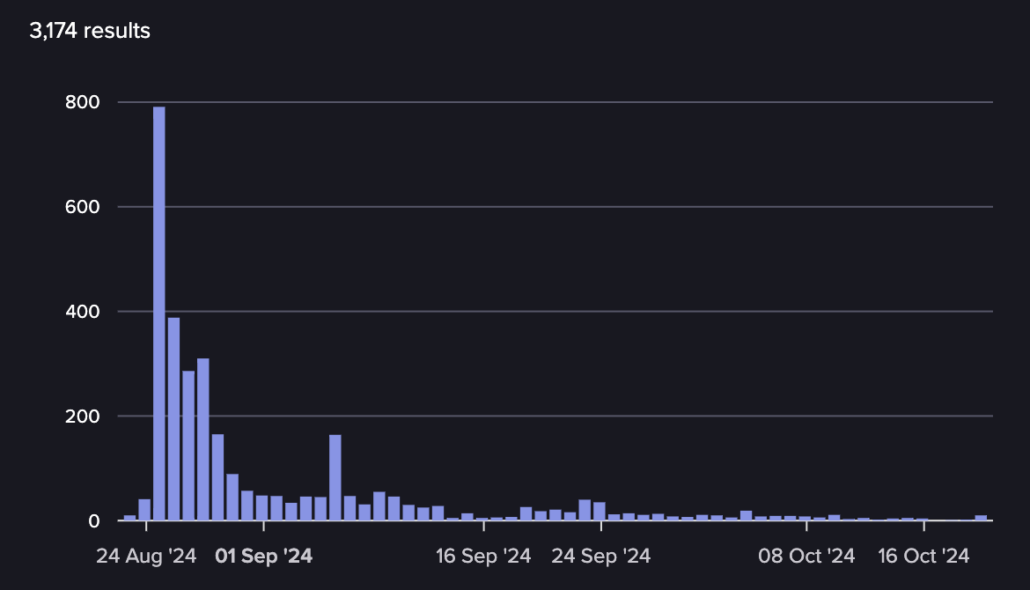
Let’s start by adopting a funnel approach, first looking at the raw data, then refining and analyzing it. In 2024, Flare observed that over 80 millions IDs and links to six different messaging apps were shared by individuals active on cybercriminal forums and Telegram channels (see Figures 5 and 6). While this number may seem impressive, it does not accurately reflect the reality of the cybercriminal ecosystem or the popularity of a messaging application. It is, for instance, quite natural that Telegram links are predominant on Telegram itself as they constitute links between different channels and groups on this platform. Moreover, this data contains many duplicates (i.e. links or IDs shared multiple times by the same or different threat actors).
Figure 5: This is a precise yet conservative estimate of the number of published links/IDs for various messaging apps on cybercrime forums in 2024, meaning the actual number could be slightly higher. Source: Flare.io
Figure 6: Pavel Durov was arrested on the 25th of August 2024, Telegram announced that it will increase cooperation with law enforcement on the 23rd of September 2024. No substantial impact can be observed.
Source: Flare.io
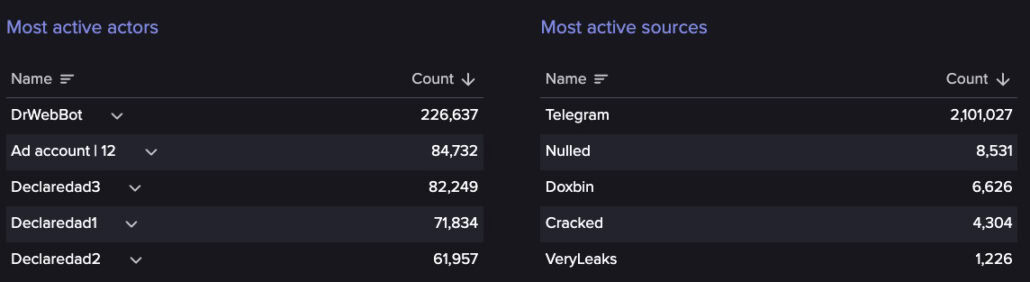
For instance, in 2024, 10 threat actors in Flare’s data were responsible for the vast majority of published Discord links (see Figure 7). Removing these top 10 actors from the dataset caused the number of shared Discord invite links in our database to drop from 2.8 million to just 91,000 over the past year. Moreover, among these links numerous duplicates were present. Interestingly, the absolute majority of Discord links was published on Telegram, highlighting a clear interest for this messaging app among Telegram users.
II. Telegram Reign Continues: More Than a Messenger – The Social Network of Cybercrime
To better assess the popularity of messaging apps, let’s refine the data by focusing only on unique links and messenger IDs shared on cybercrime forums. As shown on Figure 8 below, the amount of unique links and Telegram usernames published on cybercrime forums in 2024 is incomparably higher than one of any other massaging apps. Far behind, the second and third most popular apps, Discord and Session have seemingly not clearly benefited from Telegram’s setbacks or the concerns raised by its increased cooperation with law enforcement. As of January 2025, Telegram still reigns supreme, and its usage in the cybercriminal community has not substantially dropped.
As shown in the interactive Figure 8, when only selecting Signal, this messenger seems to be the only one that has gained traction following Pavel Durov’s arrest and Telegram’s policy changes. The rise in newly shared Signal invite links between September and December 2024 strongly suggests a correlation between the timing of these events. Nevertheless, the popularity of Signal remains marginal.
Figure 8: Pavel Durov was arrested on the 25th of August 2024, Telegram announced that it will increase cooperation with law enforcement on the 23rd of September 2024.
No substantial impact of these events can be observed except for Signal. Source: Flare.io
III. Correlation Between the Type of Threat Actor’s Activity and Choice of Messaging App
To answer our second question regarding the influence of threat actors cybercriminal activities over their choice of a specific messaging app, Flare has observed on which forums the majority of messaging apps links and IDs were published and what was the nature of criminal activity of threat actors that published them.
- Discord invite links were primarily found on forums like Nulled and Cracked – both recently seized by law enforcement [8] – as well as VeryLeaks and DemonForums. They were mostly published by younger individuals often present in gaming-focused communities and sometimes involved in low-level cybercrime.
- Matrix and Element protocol based IDs were mainly found on drugs focused forums like RuTOR, RCclub, BigBro and marginally on the fraud focused Probiv Russian-language forum. In Flare’s data lake Matrix and Element were predominately used by threat actors buying and selling drugs or those involved in fraud schemes.
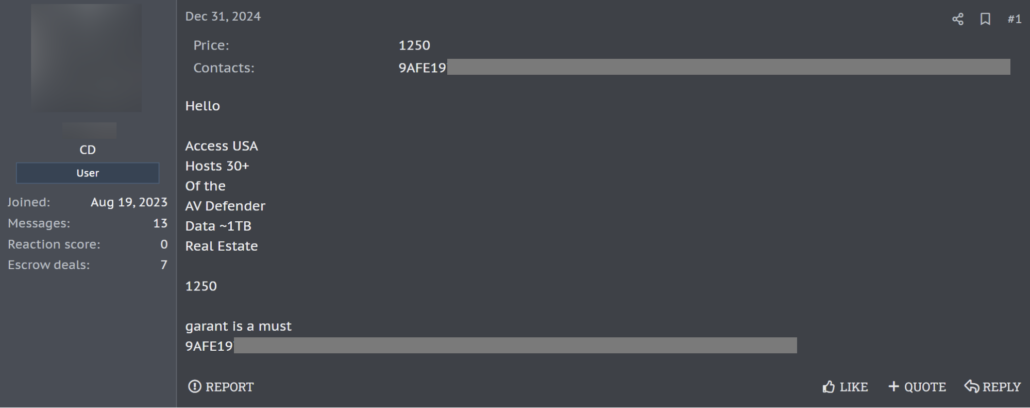
- TOX and Jabber IDs were predominantly shared on XSS, CrdPro, BreachForums, and Exploit forums, by cybercriminals often involved in the sale of corporate accesses, ransomware, or corporate databases (see an example in Figure 9).
It is important to note that a substantial number of threat actors use multiple messaging apps simultaneously (see Figure 10). This is especially true for those offering services to other cybercriminals. Maintaining easy accessibility is essential for any commercial activity; therefore, threat actors selling services such as cryptocurrency exchange and money laundering, hosting, malware obfuscation, or development often provide multiple communication channels. The interactive Figure 11 below, highlights this reality and allows you to explore different combinations of messenger apps links and IDs found in a single forum post in 2024. Telegram in combination with other messaging apps remains the most popular combination among all others highlighting once more the resilience of this communication tool.
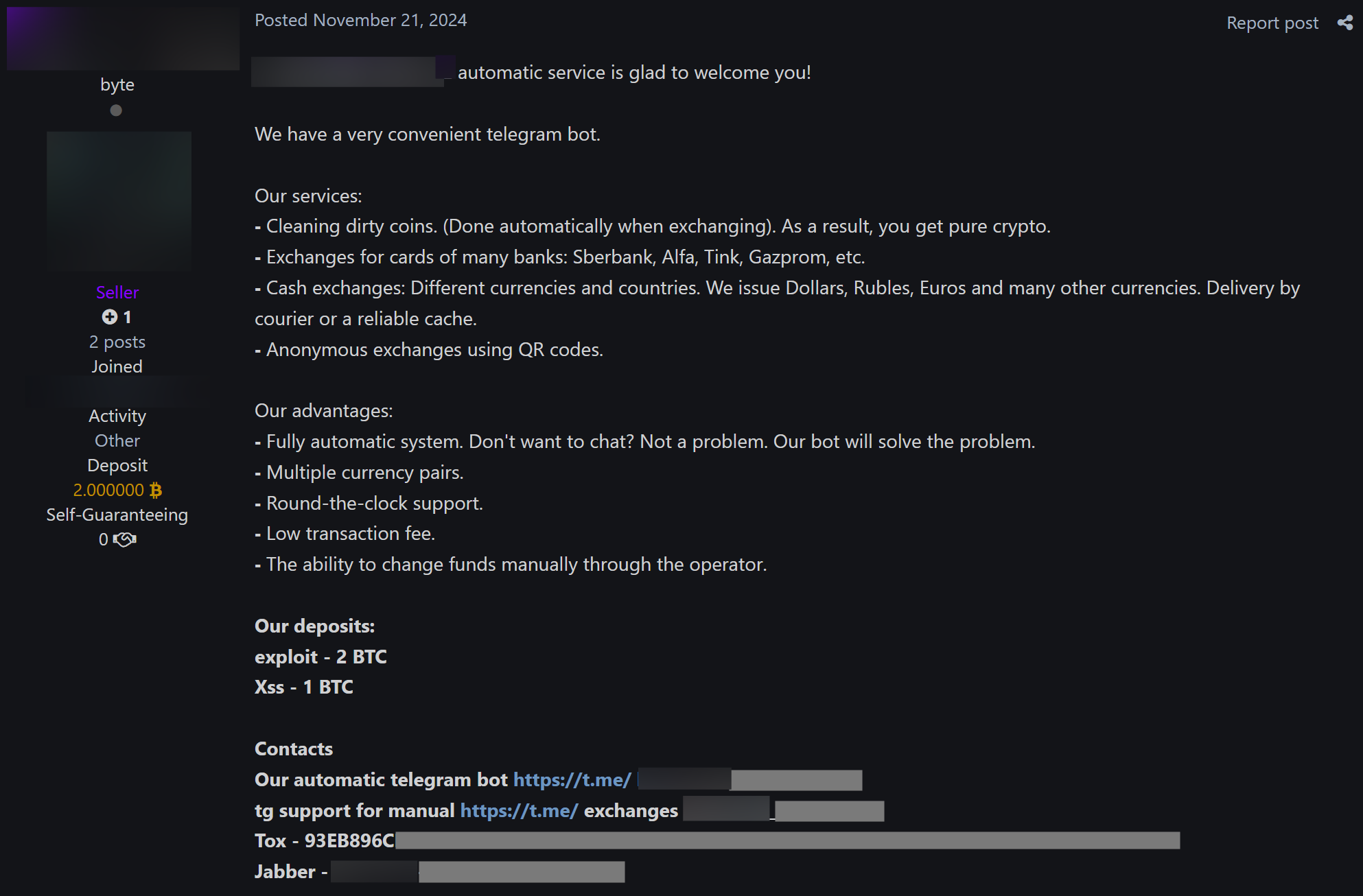
Figure 11: Source: Flare.io
Final Thoughts and Potential Future Research
The collection of this data has also allowed us to identify links between different messenger IDs and correlate them. As shown in Figures 12 and 13, it is possible to determine which threat actor uses which messaging app. The next step will be to include usernames, making it easier to study malicious actors and automate the discovery of their handles and communication channels—but that’s a story for another time. ;)
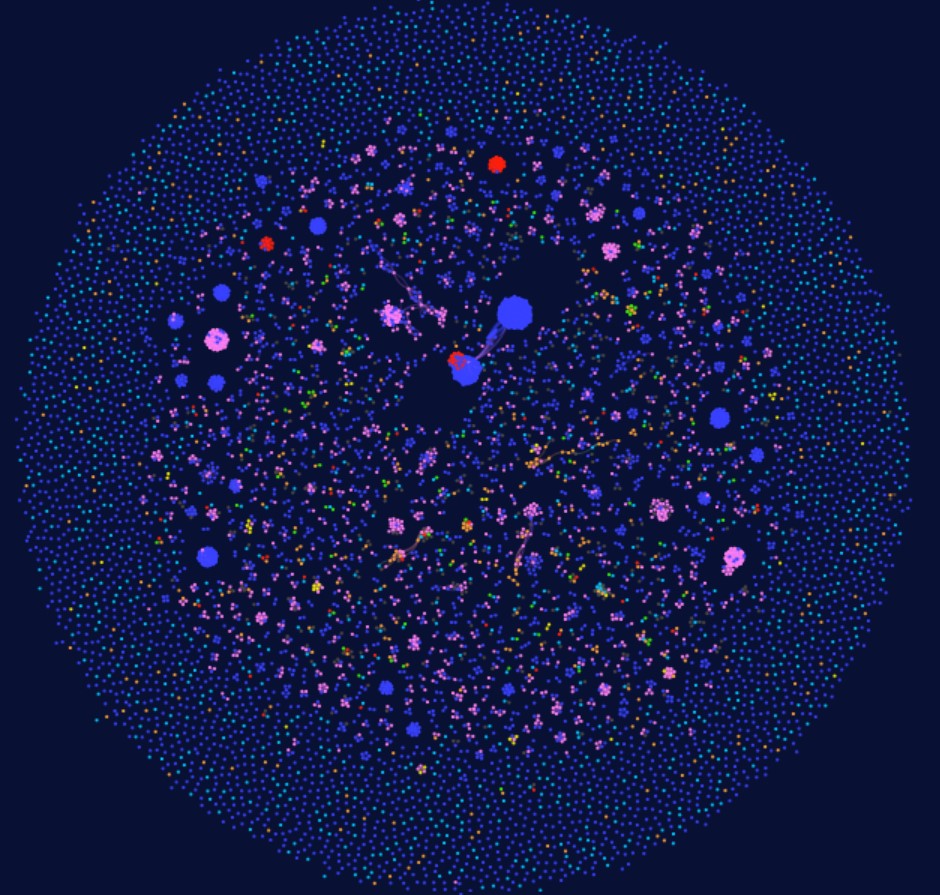
Figure 13: Example of a cluster of messenger IDs belonging to the same threat actor but found on different posts on forums and Telegram channels.
Dig Further into Cybercrime with Flare Academy
Interested in following more cybercrime research? Check out Flare Academy’s training sessions, which are led by cybersecurity researchers. Check out the upcoming sessions here.
We also offer the Flare Academy Discord Community, where you can connect with peers and access training resources from the Flare Academy training.
Can’t wait to see you there!
Sources
[4] Sergiu Gatlan, “Telegram Now Shares Users’ IP and Phone Number on Legal Requests.” BleepingComputer, September 23, 2024. https://www.bleepingcomputer.com/news/security/telegram-now-shares-users-ip-and-phone-number-on-legal-requests/.
[6] XSS.is (ex DaMaGeLaB). “Tox 1.17.6 / RCE,” May 25, 2023. https://xss.is/threads/88898/.