
Malicious actors often rely on each other to launch attacks. A carding ring that was recently dismantled by Russian authorities, for example, led to the arrest of 25 individuals who were working together.
Browsing through a popular hacker forum, one can come across hundreds, if not thousands, of advertisements for different hacking tools and services. However, extracting intelligence from these advertisements has proven to be of limited use for three reasons:
- If the product is bought, there is no telling whether it actually does what it is advertised to.
- Just because a product is being offered, does not mean it is actually being purchased.
- It is impossible to fully know the nature of every transaction as negotiations between malicious actors happen in private on Discord, XMPP and even Skype (see below).
This does not mean that hacking forum advertisements cannot be used to build intelligence for your company. Indeed, malicious actors leave other traces of their activities that can help us overcome the above limitations and profile the most popular tools malicious actors are using. This intelligence is extremely valuable as it can help your security teams understand how malicious actors will target your company and steer your defenses in the right direction. Building a wall may be helpful to protect against land attacks, but what good does it do against a helicopter attack?
In this blog post, we explore a new source of information that reveals in greater details the three most popular tools bought by malicious actors. We recommend that security teams prioritize their defenses against these threats, as they are likely to be commonly used by malicious actors.
Hacker Contracts as a Source of Intelligence
Just over a year ago, the largest hacking forum on the internet launched a service to reduce friction and uncertainty when malicious actors transact with one another. This service clearly lists the parties involved in the transaction, their obligations, the outcome of the transaction and the date of the transaction (see example below). In other words, the website maintains a register of service contracts.
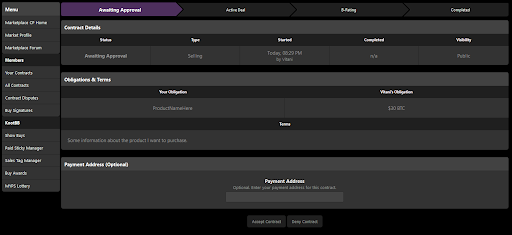
Malicious actors can choose between public and private contracts. In private contracts, only the names of the malicious actors are made public. In a public contract, all of the above information is made public.
Our analyses are based only on the public contracts which represent about 10% of the 125,000 contracts published at the time of data collection. We manually categorized and coded the public contracts’ terms to understand the type of products that were being sold. Of course, private contracts may be used to buy and sell different types of products. However, at the time of writing, there is no method available to investigate these private contracts.
Although it is only a partial overview of malicious actors’ activities, understanding what these tools do and how they work is a first step in improving your firm’s cyber security.
The three most popular tools for sale are:
- Mass mailers
- Social network bots
- Android RAT
Mass Mailers
Some of the more popular tools purchased by malicious actors are known as mass mailers. These specialised programs are specifically designed to deliver hundreds of thousands of emails in an incredibly short amount of time.
The image below presents the very basic interface of a popular mass mailer. The user supplies the software with a server from which to send the emails, a list of recipients, a message and some delay parameters to operate it. A status indicator at the bottom of the screen indicates the status of the mass mailing campaign. No coding skills are required.
Of the contracts analyzed, mass mailers accounted for 12% of tools sold. These tools are usually inexpensive, selling for around USD$10, and sold as a monthly license. This makes them relatively accessible to malicious actors, and are therefore a growing threat. Sending out millions of spam emails is the first step in mounting a successful phishing attack, a common form of malicious activity. In fact, phishing attacks grew by 250% between 2018 and 2019. Phishing is frequently used to spread ransomware.
Social Network Bots
Social media account bots are incredibly popular tools. It is estimated that 53% of all social media account logins today are bots. Unsurprisingly, bots constitute 30% of all tools purchased by malicious actors. These tools allow a malicious actor to set up a multitude of fake accounts on different social media platforms. They can then use the fake accounts to generate hundreds of likes and followers for one main account. This gives the main account an unearned and fraudulent air of legitimacy.
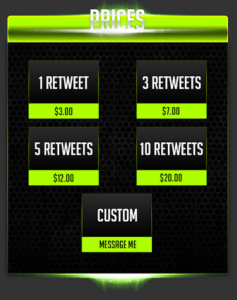
The above example shows that buying a retweet from an established twitter account (over 1 million followers) costs only a few dollars and that malicious actors even offer bulk discounts.
These bots have attracted much popular media attention in the last few years, largely due to their impact on politics and social policy. They likewise pose several threats to firms. First, bots can be used to disseminate spam and phishing links, much like mass mailers.
Second, as social media becomes a growing centre of e-commerce, bots can act as a foil to emerging businesses. Bots can post fake negative reviews or redirect traffic from legitimate businesses. At their worst, bots can be used to launch denial-of-service attacks and take down e-commerce accounts.
Android RAT
Less commonly purchased as a tool with only 3% of transactions but particularly alarming is the prevalence of remote administrative (RAT) tools for Android phones. Using these tools, a malicious actor can gain near-complete access to an unsuspecting victim’s cell phone. This includes accessing SMS messages, emails, and the device’s microphone and camera features. The image below provides an exhaustive list of the capabilities of modern Android RATs.
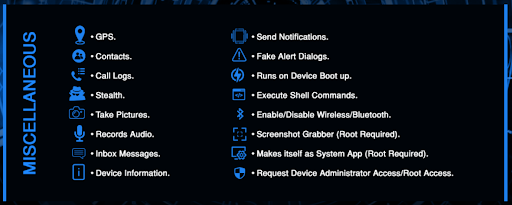
Malicious actors advertise multiple methods to infect Android phones with RATs. Popular methods include clicking on Google Drive links received in a phishing message and having physical access to the victim’s phone. Android RATs are usually rented out on a monthly basis for as low as USD$12 per month or offered on a lifetime basis for USD$150.
Conclusion
Understanding the market dynamics of the criminal underground is crucial to understanding what threats may be presently targeting your firm. As certain tools and techniques have fallen out of favour, largely as a result of improved cyber security, others have risen in popularity to take their place. Looking at the activity of malicious actors in a major illicit market, we can see that spamming, social network manipulation and Android RATs remain very popular. Recognizing these dynamics can help your security teams best allocate their resources where needed.
To address the three threats described above, we recommend that companies:
- Offer mandatory training to enhance employees’ ability to detect spam messages. IT departments should also recommend to employees that they flag any suspicious communication to help detect any new threat.
- Monitor brand mentions on social networks to detect fake messages and phishing websites. Companies should also use professional services to identify accounts of their partners that may be buying fake followers.
- Install antivirus software on Android phones and keep their software up to date to prevent and detect RAT activity.
With a robust set of tools developed in-house, Flare Systems is prepared to help you understand the latest tools that can be found in the criminal underground and monitor your digital footprint on social media. For a demonstration of our services and products, contact [email protected].
Appendix: Virtual Private Servers and Remote Desktop Access
While not linked to a specific threat, an essential tool for malicious actors are virtual private servers. Virtual private servers are used for various reasons including hosting a fraudulent website. The advertisement below clearly states that the hosting allows for “everything except child porn and terrorism.” Bulletproof means that the owner of the virtual private servers for rent will not be shut down if a complaint is lodged against them.
The other highlighted potential use cases for the virtual private servers are launching denial of service attacks (ddos booter), attacking login pages (bruteforcing) and spamming (bulk email).
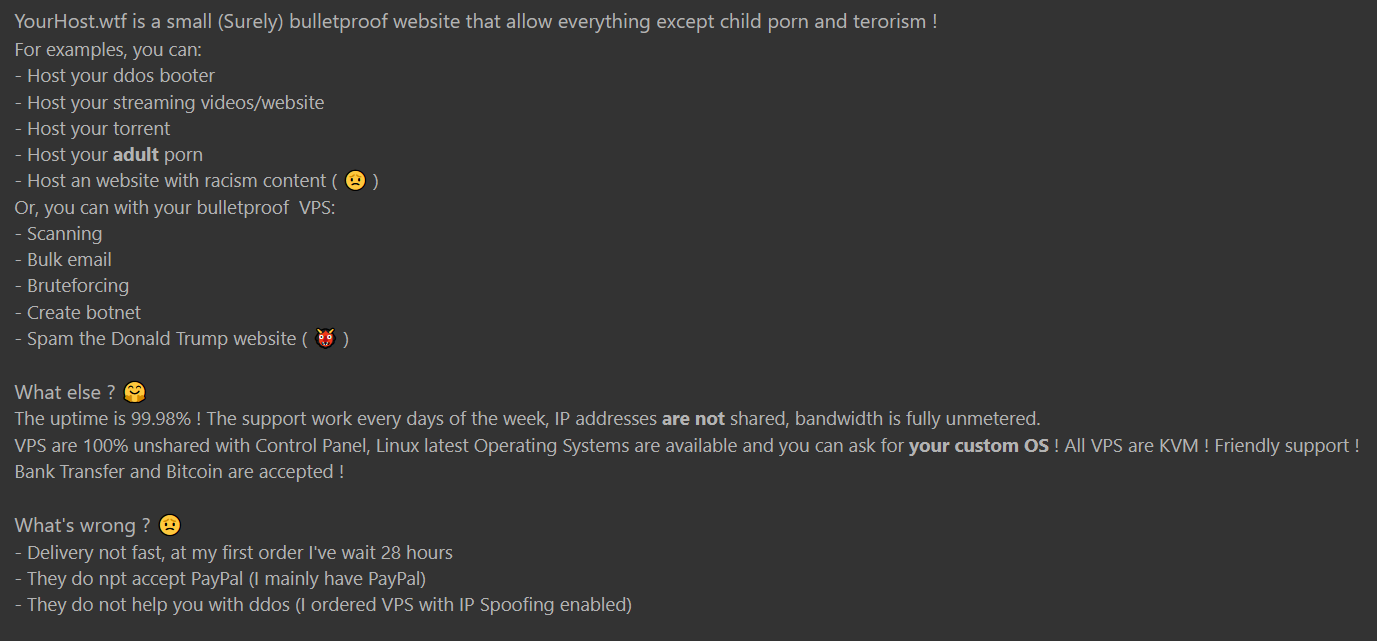
Purchasing a web hosting service from another malicious actor also promises a degree of privacy and security. There are indeed no credit card payments that can be traced to a malicious actor and the hosting provider is likely to ensure the servers remain online as long as possible.
A closely connected threat is the sale of remote desktop access credentials. These allow malicious actors to log into personal and corporate computers from afar. These kinds of attacks, according to the US Federal Bureau of Investigations (FBI) have seen a dramatic increase since 2016. Once a malicious actor is into a desktop on your corporate network, they can have unfettered access to any file or other networks the end-user had access to.
With an increasing amount of employees working from home and accessing corporate networks remotely in light of the global pandemic, the use of these tools will likely only increase. Considering that these remote networks have been rolled out quickly, security oversights are also more likely to occur. Enforcing good security practices such as using Google BeyondCorp and multifactor authentication can significantly strengthen your company against remote desktop system abuse.





