
Technical data leakage strikes again, this time affecting a major manufacturer in the automotive industry. Bleeping Computer reported this week that a misconfigured Git server has leaked source code from Nissan North America.
The server had been secured with a default username and password, respectively admin:admin. It contained 20GB of data including code for mobile apps, diagnostics software, backend tools, the company’s internal core mobile library, and client-related tools.
The Bitbucket instance was taken offline shortly after the data started being disseminated through a torrent link on multiple chat channels and hacking forums. The dump was discovered by Swiss software engineer Tillie Kottmann after receiving a tip.
Limited interest displayed on the criminal underground
A quick investigation on the criminal underground revealed an interesting narrative around the Nissan source code leak. For example, a discussion thread on a popular hacking forum has revealed malicious actors have different opinions on its value. A user says the leak contains “nothing of critical importance,” as he was hoping for a tool or method “to take remote control of a car and crash it into traffic.”
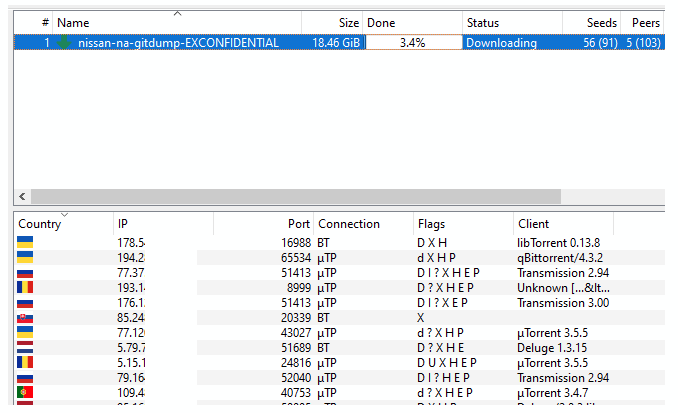
At the time of writing, the torrent link to download the public repository has been seeded by 91 users and downloaded by another 103.
So far, there is no mention of the incident on the Russian hacking forums we analyzed. The only mention detected was of the December 2017 incident when hackers breached the computer network of the same company’s finance department in Canada. As a reminder, at that time hackers stole the personal data of 1.13 million customers, including names, addresses, vehicle makes and models, vehicle identification numbers, credit scores, loan amounts and monthly payments.
Additionally, though unrelated to the recent leak, our team has detected numerous shells for sale and a code grabber to scan AM FM bands for OEM systems in vehicles developed by popular automotive manufacturers. The latter was found on a popular Russian website. This type of gadget can intercept security codes in vehicles equipped with wireless keys. Criminals can use it to open garages and cars that use wireless access systems.
What is the bigger problem?
There are many lessons to be learned from this security incident, yet the most important is quite obvious: never secure a critical corporate server with default or weak credentials. Considering a company this size has publicly exposed the Git server with such a faulty combination, it only leaves us wondering how they may have approached security for other critical components.
Looking at the high number of mixed applications whose code was kept on one, common server, again we cannot help but wonder what other security mishaps may be hiding, ready to jeopardize corporate security. If the stakes are high, malicious actors can leverage the leaked code to infiltrate corporate networks and steal critical information. Ensuring that projects and initiatives are kept on different virtual servers and repositories can help mitigate the impact of data breaches.
Technical data leaks can turn into a major headache. Source code, API keys and other critical technical data leaks can go undetected for months before your security team is aware of the incident. In some cases, it is journalists or independent security researchers who identify the digital risk, therefore exposing your company to possibly unpleasant conversations with the media and customers.
While many rush into casting the blame on development teams for using various cloud-based solutions or free open-source software, it is important to understand that technical leaks are often unintentional. Naturally, the larger a development team gets, the higher the chances for technical data leakage to occur, due to the difficulty in implementing secure coding practices. This is why having good visibility over your digital footprint is essential to detect any data breach in minutes, instead of weeks.





