Organizations are concerned about the proliferation of threats on the dark web. Even as cybersecurity budgets have increased dramatically over the past decade, ransomware, phishing and other cyber threats have grown in intensity and frequency. For example, Flare’s Research team identified a surge in ransomware attacks from 2020 to 2021 – a total increase of 437%. Naturally, the number of victims of ransomware attacks have also been rising rapidly. Clearly, a vast and opaque underground economy has developed that deals in stolen passwords, stolen credit card numbers, ransomware as a service, and other illicit goods and services.
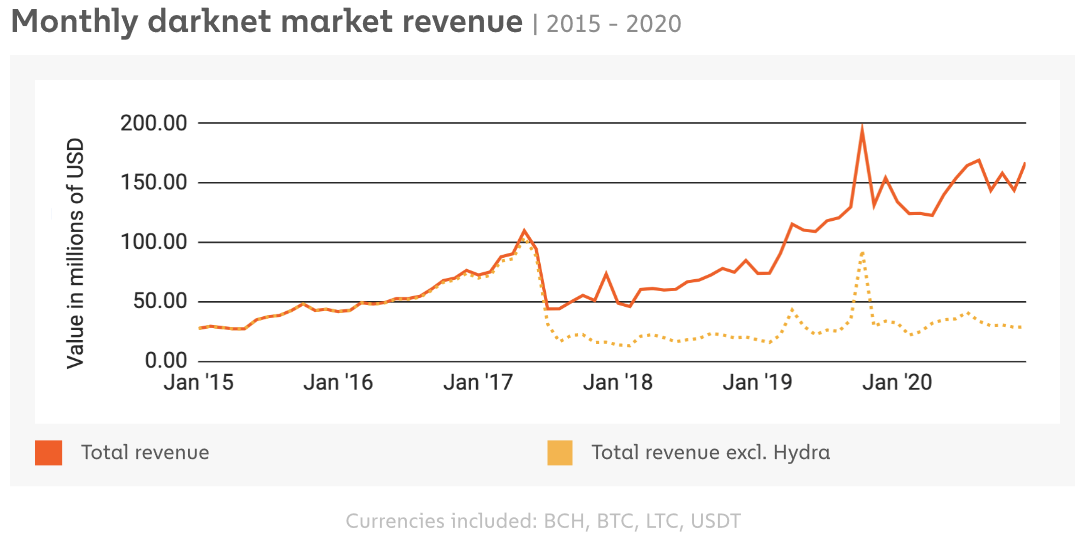
The size of darknet markets has grown exponentially alongside the increase in threat actors. Despite repeated law enforcement victories such as the shutdown of the empire market and the shutdown of Pirate Bay and White House Market, the darknet is larger than ever with an estimated monthly transaction volume of more than $150 million USD. In fact, Forbes has also reported that 2021 is on track for a groundbreaking year for data breaches as we’ve already surpassed last year’s numbers. Even though not all data breaches can be accounted as malicious intent, we still must be mindful. Undoubtedly, visibility into the dark web still lags despite organizations now having increased visibility into their internal networks and security posture.
This article will provide insight into how your organization can monitor the dark web for potential account-takeover schemes and other criminal activities that could impact your company. Dark web monitoring enables you to take a proactive approach to cybersecurity, and actively hunt threats before they become data breaches and ransomware attacks.
What Exactly Is the Dark Web?
The internet can be split into roughly three parts. The first section is what we would call the public web or clear web – essentially all information that is publicly available to an average user. The second is the deep web which comprises all information hidden behind a login wall and not indexed by a search engine. This comprises the vast majority of the internet (Facebook being a prime example). Estimates put this at hundreds of times the size of the clear web. Finally, there is the dark web, which requires a specialized browser such as TOR to access. Learn more about the difference between the dark web vs deep web.
TOR started as a U.S. Navy project to enable hidden communication between naval bases but quickly took on a life of its own. TOR uses a series of relays which make it extremely difficult to track packets as they traverse the internet. While this does not provide for complete anonymity, it does make it far more difficult for law enforcement and other users to identify specific people and servers.
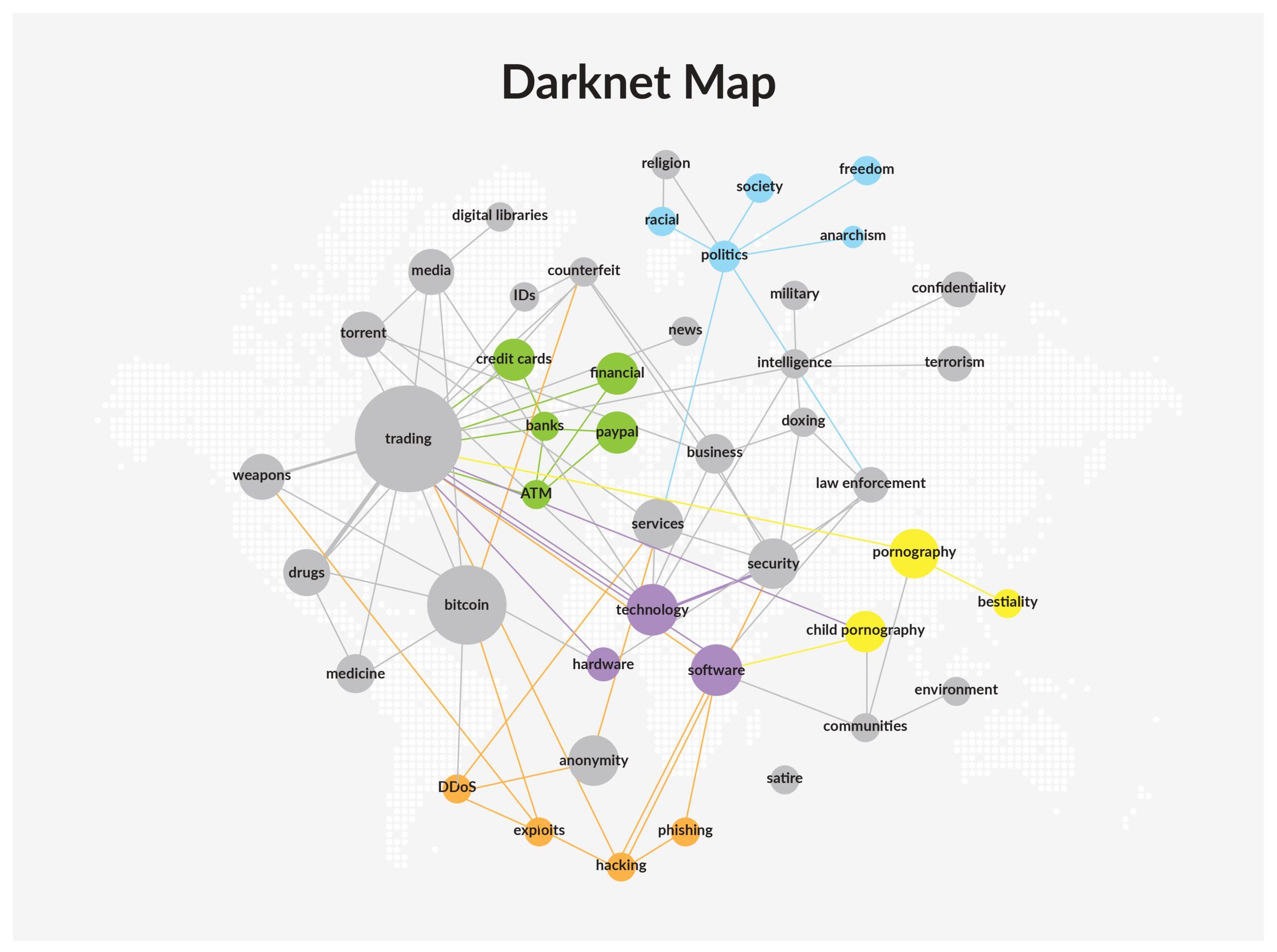
For this reason, the dark web exploded in popularity as it enables criminals and other users who require a high degree of anonymity to transact business and communicate with far less risk. The dark web is a common place for criminal actors to meet and barter although it is not exclusively used for criminal enterprises. In 2018, we took the time to map the darknet. You’ll notice that not all of the dark web is malicious – many individuals and organizations use it for legitimate purposes as well. You can see the results below:
What Types of Information Are Sold on the Dark Web?
The dark web is surprisingly small by the standards of the clear and deep web, with only about 60,000 pages at any given time. However, on these pages, vast amounts of information are sold for cryptocurrencies such as Monero and Bitcoin. Here are some common types of data you might find on the dark web:
- Personal Health Records (PHI)
- Social Security Numbers
- Exposed Technical Data & Source Codes
- Names, Birthdays, and Security Question Answers
- Email Address Credentials
- Other Compromised Credentials
- Personally Identifiable Information (PII) such as home addresses
- Financial data, bank accounts, and credit cards
- Software Source Code
- Company Proprietary information
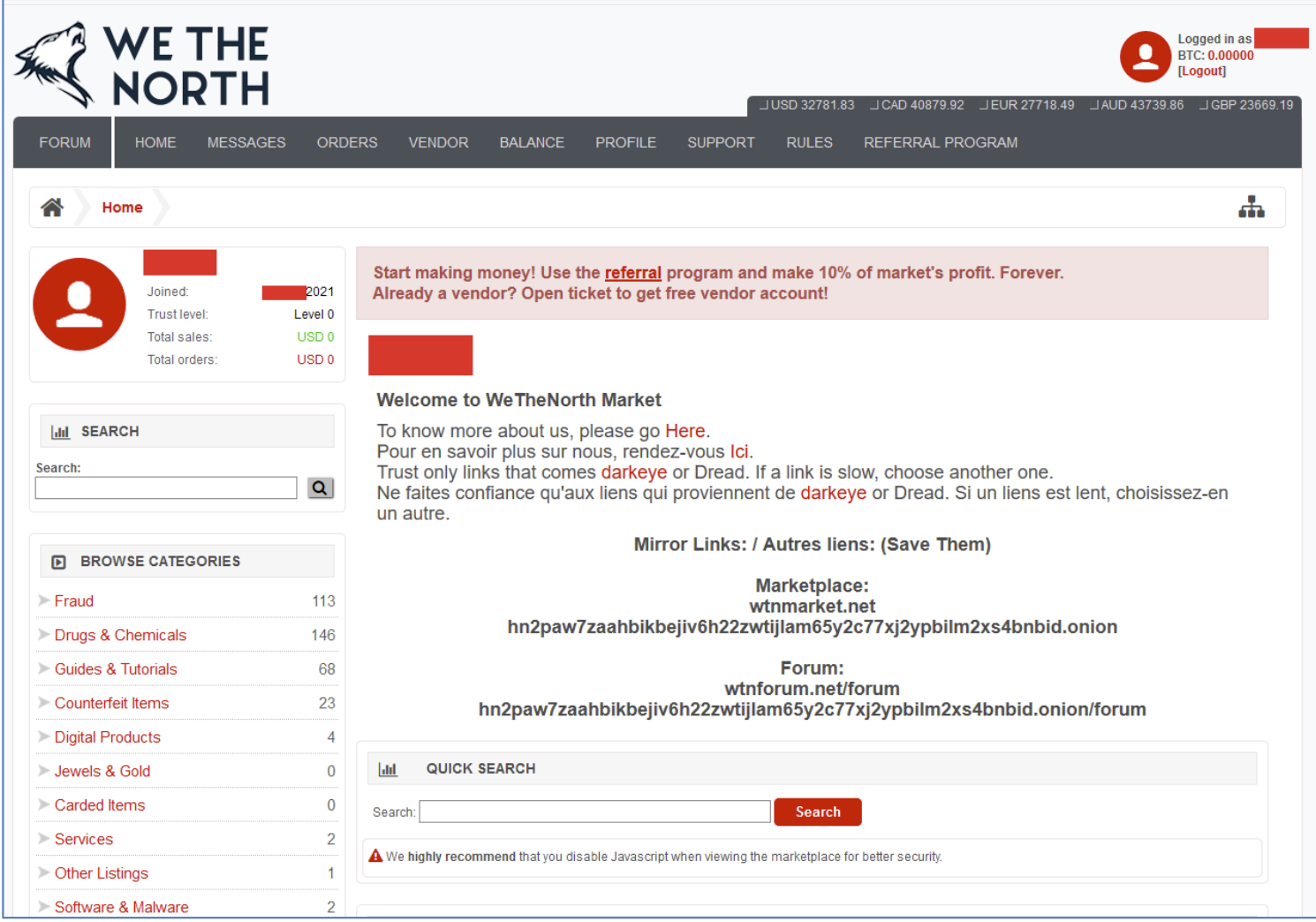
Here’s a look at ‘We The North’ dark web marketplace. On the left hand side, you’ll see the numerous categories of illicit content and materials users can purchase. Including 113 items under ‘fraud,’ where stolen data is sold.
How Can You Prevent Your Information Being Sold on the Dark Web?
A mature cyber security program can dramatically reduce the risk of your information being stolen and sold, however, no program is perfect. We recommend most companies conduct regular dark web scans or engage in real-time dark web monitoring to identify stolen credentials. Both of these methods play an important role in data leak prevention and detection, which are always best practices for organizations and should always be a priority. Here are a few quick tips that can help prevent your corporate information from exposure on the dark web.
Manage Your Passwords Well
You’ve probably heard this before, but you should avoid reusing passwords and you should change passwords regularly. Many people have accounts on dozens or even hundreds of different sites. When one of these sites suffers a data breach, the email and associated password will likely end up being sold on the dark web. If the site that is breached has additional information such as phone numbers or home addresses, the information may be sold together to facilitate identity theft.
Our employees recommend investing a small amount in a password manager, either for yourself, your team or organization. Then, employees can easily save randomly generated passwords and access them seamlessly. Some examples include 1Password, KeePass, and Bitwarden.
Be Careful With BYOD Policies
In many cases companies allow employees to bring and use their own desktops, laptops, and cell phones for business. While this can reduce upfront costs and allow employees to work on machines they have a level of comfort with, it can also open them up to a range of attacks that could bypass your organizational cybersecurity program. Oftentimes users who bring their own computer may forget to patch systems, fail to update anti-malware, or may have other security lapses.
Although these are great tips to start with, this is only the tip of the iceberg when it comes to data leak monitoring. To protect your organization’s information, we must also consider how to prevent S3 bucket leaks, GitHub repo leaks, and centralize key and secrets storage. All of which have been broken down in our Information Leakage: What You Need to Know Guide.
What Are The Benefits of Actively Monitoring the Dark Web?
Dark web monitoring has traditionally been seen as a function of a threat intelligence program. Unfortunately, aside from a few large organizations, most companies don’t have the resources or personnel to make use of a full-fledged threat intelligence operation. However, that doesn’t mean that dark web monitoring provides no value. Instead, it can be used by companies to find out whether criminal actors have compromised employee accounts, as part of account takeover schemes, or discover if your organization’s financial information is for sale.
Prevent Security Incidents from Becoming Data Breaches
Finding out whether your organization’s account credentials have been exposed or are for sale on the dark web can provide innumerable benefits. First, it provides you with a valuable first warning sign that a security incident may have occurred. SIEM Solutions, anti-malware, and anti-phishing can be valuable, but even the best cybersecurity programs have flaws. Actively monitoring the dark web can alert you to an incident that other tools missed, and by doing so help you prevent a larger data breach or ransomware attack.
Get Visibility Into External Threats
The first step for many fledgling cybersecurity programs is to get visibility into the types of data they collect, the amounts of data collected, and the security measures on their network. However, many organizations fail to consider the information that may be living outside of their internal network. Beginning to actively monitor the dark web can provide invaluable insights into your organization’s risk profile, and whether you are a target, or have been targeted by malicious dark web actors.
Prioritize Your Efforts
Once you have visibility into your organization’s digital footprint and level of risk, it’s time to prioritize your risk mitigation efforts. In many cases, you can apply a risk matrix to understand risk severity. Using DRP software can make risk prioritization easy through risk scoring using machine learning and automated remediation. Assign each instance of exposed data a score, based on the formula threat times likelihood. This can lend clarity to your risk mitigation efforts as you can systematically work to reduce the most unacceptable risks.
Discover Technical Information for Sale
Stolen credentials and personal information isn’t all that is for sale on the dark web. Malicious actors will also at times steal proprietary corporate technical data such as source code, API keys, and other confidential technical data. Actively monitoring the dark web can help you identify whether proprietary corporate data is for sale.
How to Get Started with Dark Web Monitoring?
Getting started with your own dark web monitoring program may seem overwhelming. Even though the dark web is comparatively small when compared with the clear web, there are dozens of markets spanning thousands of pages. Many large enterprises fund entire threat intelligence programs designed to identify ATO schemes and other threats to their organization. Small and mid-size organizations may have difficulty funding a fully-fledged threat intelligence program.
Fortunately, Digital Risk Protection (DRP) software can help them get visibility on threats both in and out of their organization. A DRP Solution can enable your organization to scan the dark, deep, and clear web and quickly identify exposed credentials, account takeover schemes, technical data leaks, and other critical external security threats.
If you’re interested in learning more about how Digital Risk Protection software can enable your security team to actively hunt threats and reduce your overall risk profile, set up and try out our free trial in less than 15 minutes.