
A 0-day is a software vulnerability that is unknown to its software maker. 0-days are perhaps the most valuable type of exploits out there simply because they can be used with an incredibly high chance of success, and often for an extended period of time. With no knowledge of a flaw, a software maker is unlikely to publish a fix, and the actions of the attackers can probably go undetected for quite some time.
The Market for 0-Day Vulnerabilities
0-days were once associated with Nation States that had the necessary resources to probe software and find unknown vulnerabilities. Over the past two decades however, private researchers and malicious actors have also been hunting and finding their own 0-days.
For the former, there is likely to be a high payday for reporting the vulnerability through a bug bounty program. There are also conferences dedicated to the identification of 0-days such as Pwn2Own, but not the publication of the details of the vulnerability. For the latter, 0-days represent a valuable tool to stealthily launch attacks that can generate up to millions of dollars in profit.
Private companies now also operate as brokers, buying 0-days from researchers, and selling them to intelligence and law enforcement agencies. These brokers offer hundreds of thousands of dollars for each 0-day, and appear to be turning quite a healthy profit from reselling the 0-days.
No matter how 0-days come to be known and shared, in all of the above examples, 0-days remain private and shared among a small circle of people. They in essence keep a veil of secrecy and mystery that has enshrined them since the first days of the computer age.
0-Days Moving Into the Spotlight
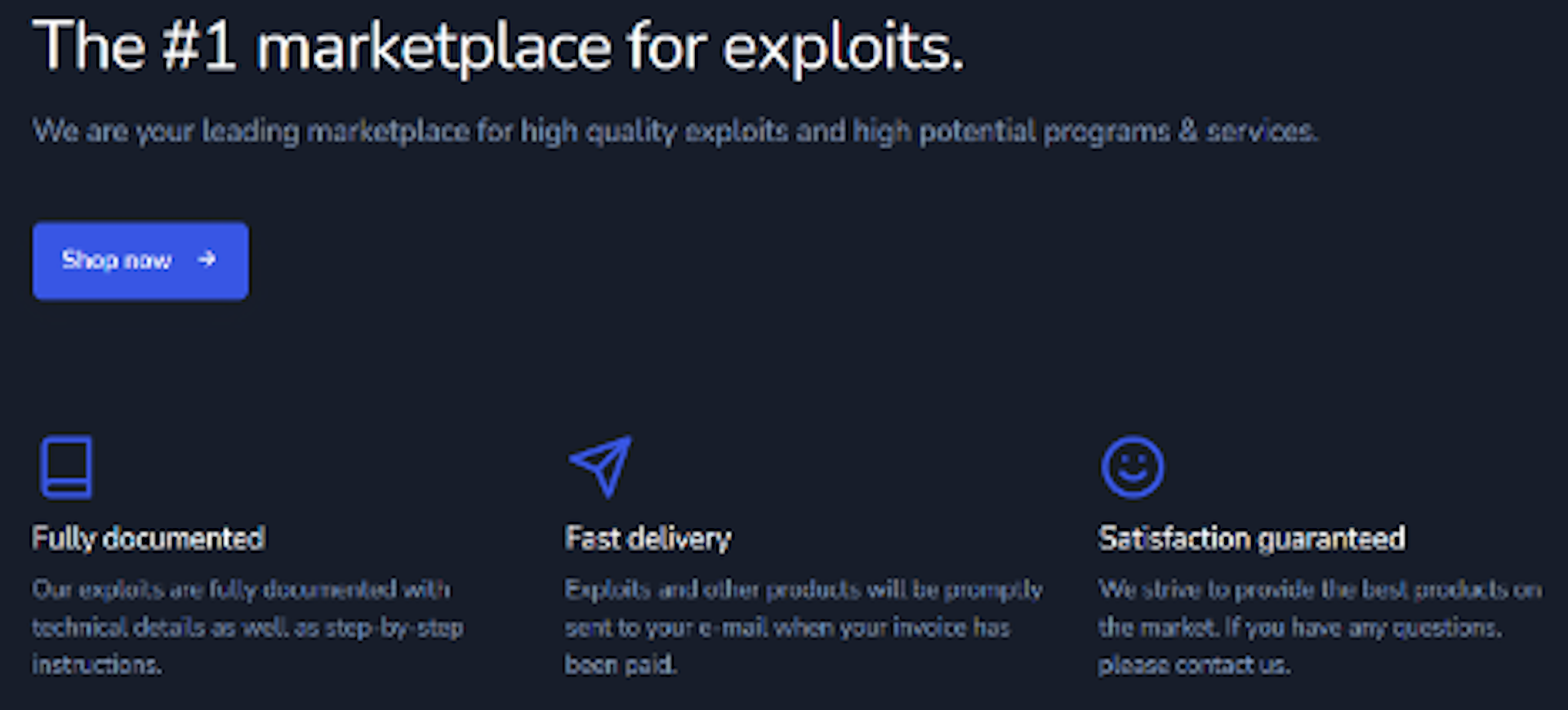
The secrecy that surrounds 0-days explains why the launch of a very public 0-day marketplace is so surprising. Our intelligence team has found that the dark web is now the host to a very active marketplace where 0-days can be bought. As shown in the image below, the m marketplace promises:
- Fully document 0-days that can be exploited quickly
- Fast delivery
- Satisfaction guaranteed, though no refunds are promised
Another surprise comes from the high profile 0-days that are advertised on the website. These include SMS interception, SIM card exploitation, mobile phone takeovers and social media account takeovers. These are all incredibly valuable 0-days that could be leveraged for damaging attacks against individuals and organizations. Their price, from a few hundred to a few thousands US dollars appears to be much smaller than what we have seen in other public displays of 0-day pricing where the most valuable are worth hundreds of thousands of dollars.
The marketplace appears lastly to be selling the same exploit to multiple individuals. The website indeed presents ratings which appear to represent past sales, with a 5-star rating associated with it. The most popular 0-days have apparently been sold hundreds of times, suggesting that the marketplace is already incredibly active.
A Public and Visible Presence
The popularity of the platform could be explained by its marketing campaigns on social media like Instagram and YouTube. The market has its own account with hundreds of subscribers. There, it publishes information and videos of the 0-days, as well as explanations on how to use the site. The whole customer journey is presented and potential customers can see what to expect when they purchase a 0-day account. It shows how payments in cryptocurrencies can be sent, and that bit.ly is used to deliver the files once the purchase is complete.
Threats Only Get Better, Not Worse
Bruce Schneier famously said that threats only get better, and not worse. This new marketplace is a good example of this mantra, and a lesson to be learned for security professionals. It represents yet another example of the democratization of the most sophisticated attacks down to malicious actors who need no technical knowledge. 0-days that target large communication networks and communication software are significant threats and must be detected as quickly as possible. This is why we have added this marketplace as a source of information that we monitor on a daily basis to identify quickly any new significant 0-day.
Using this information, security teams can better understand the risks associated with using specific tools and networks. They can also better understand the security posture of companies. Indeed, some appear to be more targeted than others by malicious actors, and to be taken over more easily. These may represent unnecessary risks for your organizations and could perhaps be replaced by more secure software that does not fall to malicious actors as easily.
What makes the success of platforms possible is the visibility of the marketplaces and it will also be interesting moving forward to monitor how malicious actors are allowed to operate on social media. Their presence there represents an advantage of terms of visibility for the malicious actors, but also an investigation opportunity for law enforcement to gather intelligence on the individuals that operate these platforms. We look forward to better understanding just how law enforcement will react to this shift towards visibility, and if those brazen enough to go there will be the first ones to be shut down in the end.





