
A little over a year ago, malicious actors hacked the MyFitnessPal service. With 143 million users, this was one of the largest hack of credentials ever reported. Now, as Flare Systems is launching its leaked passwords check service, we present the three lessons we learned from analyzing this massive throve of passwords.
Getting acquainted with the leaked data
Of the 143M accounts that were hacked, only 46M passwords were released publicly. Researchers have suggested that the leak actually included passwords encrypted with state-of-the-art cryptography (bcrypt) and easy to crack cryptography (SHA-1). MyFitnessPal updated the cryptography when users logged in starting a few years ago. Therefore, the 43M leaked passwords are likely for users that have not logged in for a few years.
Most common passwords
Many users used the same passwords. As a result, we found 22M unique passwords among the 46M leaked passwords. We present below the Top 10 most common passwords.
- 123456 (0.21%)
- password (0.20%)
- fitness (0.11%)
- qwerty (0.07%)
- skinny (0.07%)
- sunshine (0.06%)
- myfitnesspal (0.06%)
- charlie (0.05%)
- princess (0.05%)
- loseweight (0.05%)
We did not expect users to have very strong passwords for their fitness app. This is confirmed by the exclusive use of lowercase alphabetic characters. Interestingly, the word monkey is in 17th place. That word has been consistently listed as one of the most common passwords and many are still puzzled as to why.
Password length
The Figure below shows the length of cracked passwords. The most common length is 8 characters. Over 90% of passwords are between 6 and 10 characters long making them very easy to crack.
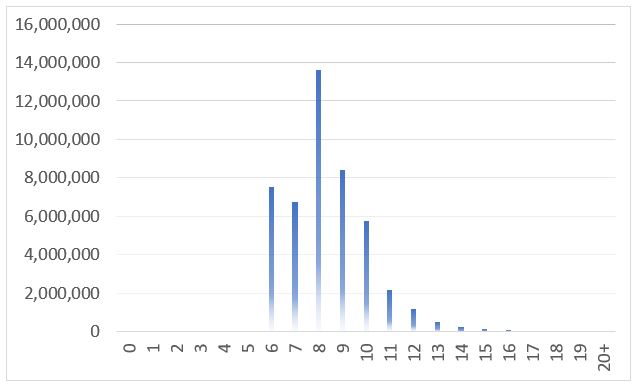
Almost all of the passwords start with a lowercase letter (87%) and the remainders started with either 1 digit (11%) or 2 digits (1%). Half of the passwords ended with 2 digits. 10% more ended with 1 digit. Around 2% of the passwords ended with a single special character. 65% of all characters are alphas and 25% are digits.
The Zxcvbn Algorithm
We at Flare Systems like the Zxcvbn algorithm to measure the strength of passwords. Dropbox designed this algorithm that rates passwords on a scale from 0 (very weak) to 4 (very strong). It addition to detecting the use of common words, the algorithm also looks at how close characters are on an English keyboard. !@#$%?&*() may look like a very strong password; in reality, it is a common password as it includes all the special characters above the letters.
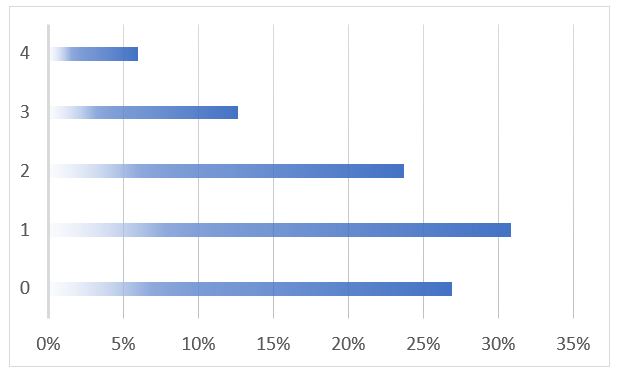
The Figure confirms that over half the passwords from MyFitnessPal were very weak. It also shows that incredibly complex passwords (rating of 4) were still cracked as the encryption algorithm used was itself weak and easily cracked.
Lessons learned
The first lesson we learned is that people are getting better at choosing their passwords. Yes, the most common passwords found in the dump are very week (monkey?). The top 10 most common passwords however represent less than 1% of all passwords. This suggests that fewer and fewer users are choosing weak passwords.
The second lesson is that strong passwords are useless if they are not encrypted properly. The leak data contains very complex passwords that could not have been cracked if not for the very basic encryption scheme MyFitnessPal used. Security departments therefore need to educate their users on the importance of strong passwords. They also need to make sure that they are internally using strong encryption to protect those passwords.
Finally, this leak reminds us of the dangers of password stuffing (see this article on how hackers are using the technique on a fast-food restaurant app). The size of the leak puts millions of users who reused their passwords on other websites at risk of victimization. When choosing a password on a smartphone application, many users will not take the time to generate a strong secure password as is commonly the norm on desktops. These weak passwords may lead to the leak of more private information such as credit credit data.
Flare Systems’s new password check service can help you protect against password stuffing and the consequences of leaked passwords. Contact us to learn how.





