
Phishing remains a popular attack method for malicious actors. This attack method is made possible by the wealth of services phishers can purchase on illicit markets: mass mailers, email lists, fake websites etc. Phishing attacks have been on the rise, registering a 250% growth between 2018 and 2019 according to a Microsoft report.
In this blog post, we offer three solutions to prevent phishing attacks. These are separated in two groups: solutions that protect credentials and solutions that proactively target malicious actors.
Protect Credentials with Two-factor Authentication at Login
Two-factor authentication adds a second layer of security at login. Users will still need a username and password, but at each login they will also either enter a one-time code generated by a mobile application or confirm their identity on their phone as shown below.
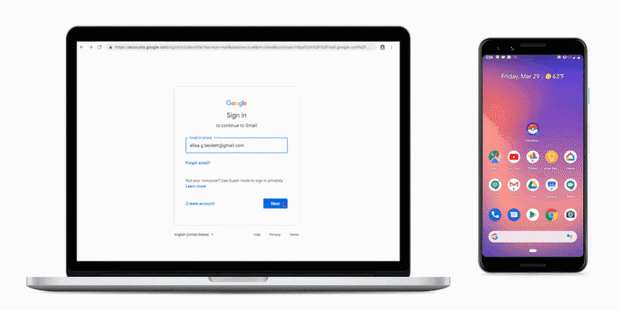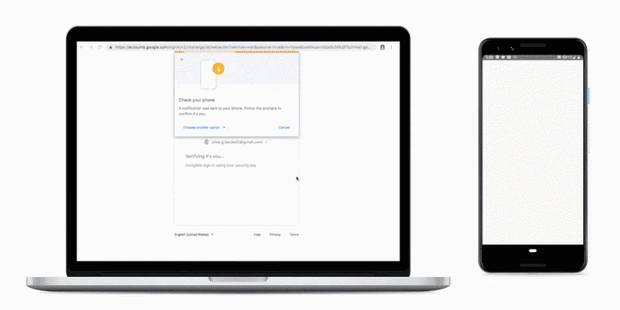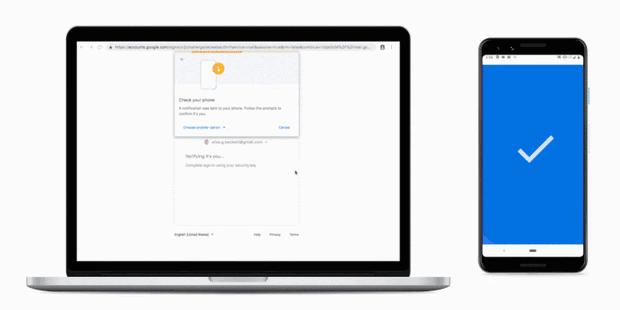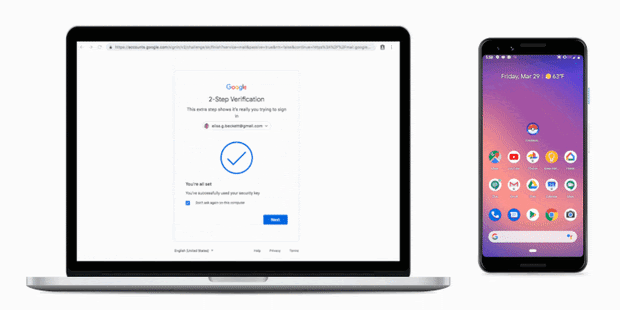
Convincing a user to authorize a malicious actor’s login would be possible, but it would require a laborious social engineering campaign. This strategy would not scale and might instead make a large number of victims. Therefore, two-factor authentication is an interesting solution to prevent phishing.
Its main drawback, however, is the training some users would need to understand how it works, which may ultimately generate an increase in customer calls.
Protect Credentials by Removing Passwords Altogether
Removing user account passwords altogether could be an alternative to two-factor authentication. In this scenario, users enter their email address or phone number to log in. They then receive a one-time code that logs them directly into a website as shown below.
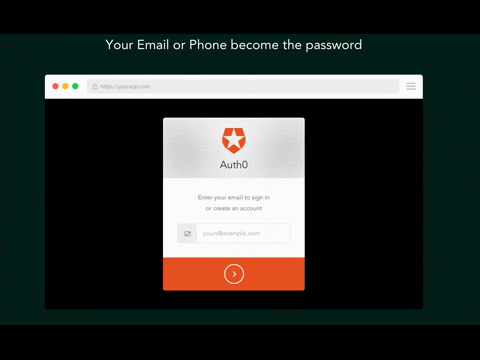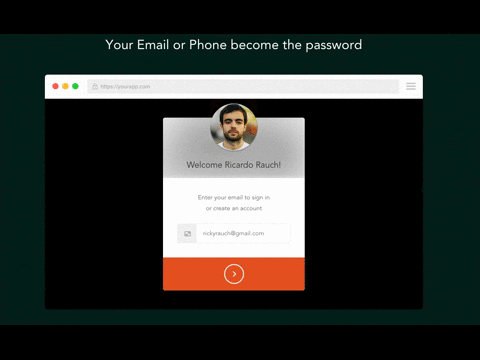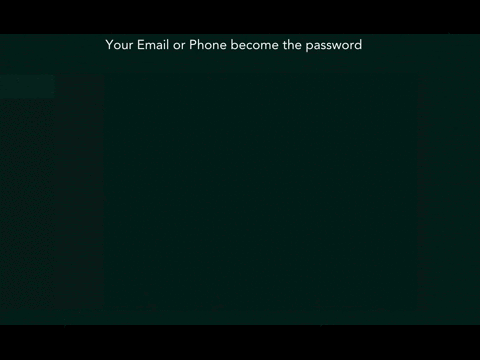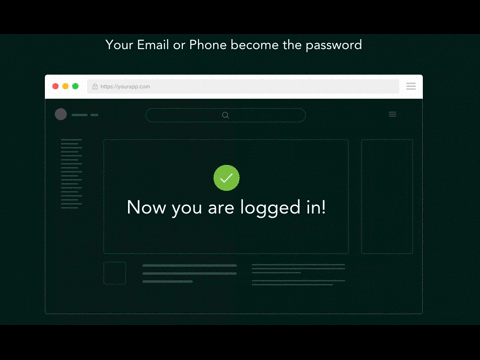
Because there are no passwords left to steal, malicious actors are unable to phish the customers of passwordless authentication services. This solution is simple and straightforward for users. Moreover, if there are no passwords to steal, then phishing the credentials from a user becomes impossible. The main drawback of this solution is that emails and SMS are often delayed because of internet connectivity issues. Users must therefore be patient while they wait for their one-time link.
Proactively Targeting Malicious Actors
An alternative to login solutions is to stop phishing attacks right at the source. An effective phishing attack needs to be believable, and recreate every detail of a firm’s website. This includes its domain name and a digital (SSL) certificate that matches that domain name. The registration of the domain name can be the Achilles’ heel of phishing attacks.
Each new domain name and SSL certificate registration is indexed and published in public feeds. This feed can be parsed for URLs that resemble those of firms. Importantly, the feeds include both domain names (ex. bankofamerica.com) as well as subdomain names (ex. bankofamerica.phishingwebsite.com).
Subdomains are a popular tool to build phishing campaigns.
- Subdomains make it easier to include the victim’s full name to add a layer of authenticity to phishing sites.
- Subdomains can be appended to reputable domains. Security tools are unlikely to flag a popular news website (ex. cnn.com) even if it has a phishing subdomain appended to it (bankofamerica.cnn.com). Malicious actors are therefore particularly interested in vulnerable legitimate sites that can be taken over to add a phishing subdomain.
- Legitimate websites may have a wildcard digital certificate that allows them to create new subdomains without having to list them in public feeds. This prevents monitoring services from issuing warnings when new subdomains are created.
Algorithms that can eliminate false positives are important as hundreds of thousands of domain names are registered every single day. False positives create unnecessary alerts that reduce the vigilance of security teams. DNSTWIST has become an industry-relevant algorithm to detect domain names that may look like yours and used for phishing campaigns. Its website offers a live tool to detect phishing sites.
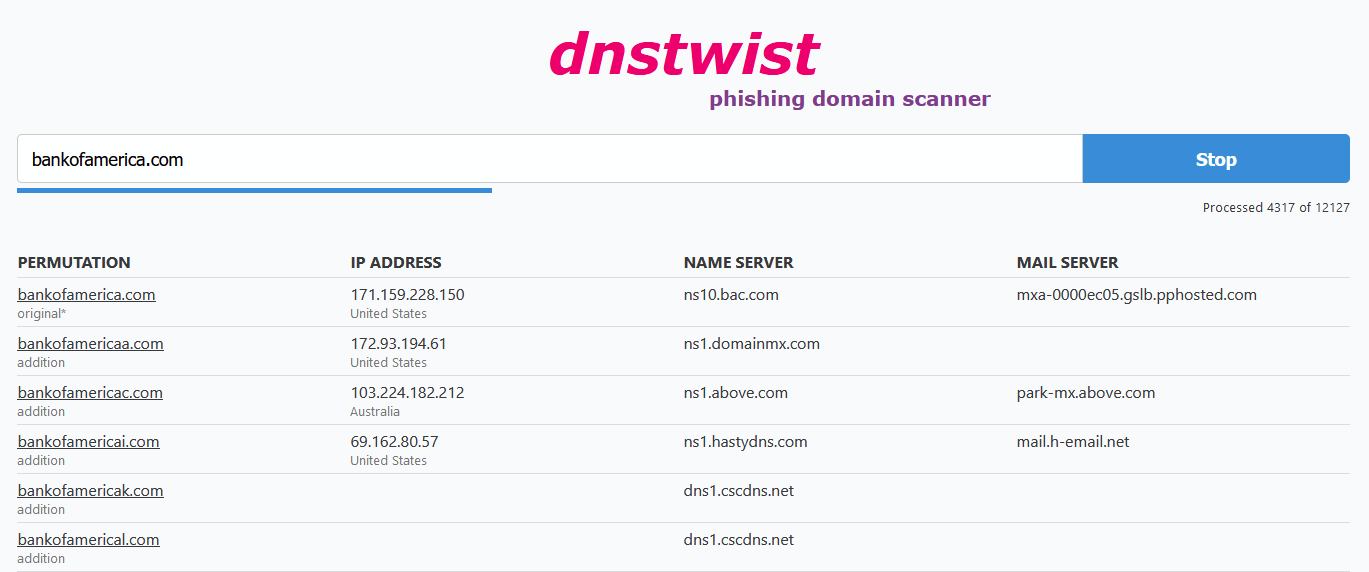
Identifying phishing domain names and SSL certificates is a first step to prevent phishing attacks. This information should indeed be shared with security companies, integrated into spam filters and be used to file a takedown request with the issuer of the domain name, or the company hosting the website.
To be effective, domain name registration detection must be fast. In 2016, a phishing domain name would only be used for around 24 hours. Today, these websites likely remain accessible for under an hour. Since users will typically begin clicking on the shared link within 4 minutes, this gives malicious actors ample time to collect user data through their phishing websites while avoiding detection.
Conclusion
By offering extensive coverage of clear and darknet sources, Flare Systems is well positioned to detect the registration of new domain names similar to your own. By offering quick response times and automated alerts, Flare Systems products can help manage the risks of a phishing attack. To see if Flare Systems is right for you, request a demo at [email protected].





