
Cloud services, especially those related to communications, have massively been adopted by corporations, as they have shifted to a remote workforce this year. The poster child for this trend, Zoom, now has over 300 million daily participants, up a dizzying 3,000% from the previous year. Global spending on public cloud services is expected to grow by 18% in 2021, an increase of USD$50 billion!
Despite this, employees are still seeking and registering for cloud services that are not under the control of their IT departments. Quite often, employees are not satisfied with the cloud services they are required to use for official communications, and feel discouraged by the long delays to get approval to use a new service. This leads to shadow IT, where communication and documents are exchanged in secret without the knowledge of IT departments.
Shadow IT represents a significant risk for your company. Employees are often unaware of the security risks posed by the services they register on, and are likely to adopt a deficient rights management process. This is one of the top five human errors that leads to data breaches. Unauthorized cloud services may also not be compliant with industry regulations. Their use could lead to costly investigations, fines and brand damage.
How regular users react to a data breach
While it is one thing for your employees to launch a shadow IT environment behind the IT department’s back, it is another to keep it up when there’s evidence of compromise. Let’s take a closer look at the aftermath of a major data breach that affected an Android SMS application with over 100 million users.
A cybersecurity company has revealed that the application kept on its servers a copy of all the media its users shared. This information could be accessed without any authentication, and was hosted on sequential URLs. Using a basic script, it was possible to generate the URLs of all media hosted on the application’s server, and spy on its users. The report mentioned that the data breach was significant, and included identity papers and very personal pictures, among others.
To understand user satisfaction, we collected the last 5,000 reviews posted about the application on the Google Play Store. In the graph below, you can see the distribution of reviews from low-rating one star (S1) to high-rating 5 stars (S5). Our data shows that users were overwhelmingly satisfied with the application in the months prior to the data breach. The 5-star rating represents at least 66% of all reviews on any given day.
A few days after the data breach was reported, Google took down the application from its store. This led to missing data around the end of November. In the days around the breach report , we noticed that low ratings were multiplied by 3, and that the high number of low ratings continued for a few days after the application was restored on the Google Play Store. However, the complaints appear to die down quite fast, and return to previous levels.
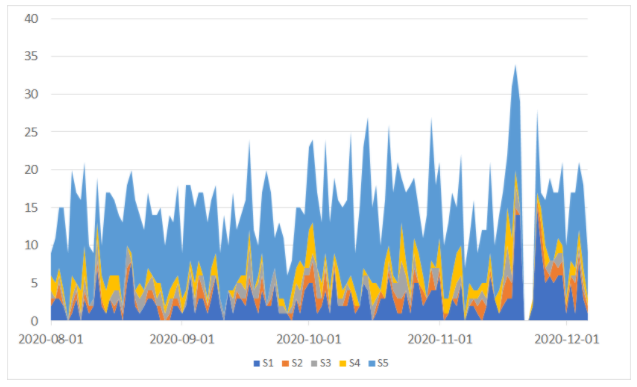
These results suggest that the application users were mildly concerned about the data breach, but continued nonetheless to report positive reviews of this application.
Can a Data Breach Protect Your Company?
A data breach of this magnitude could have sparked a wave of negative reviews and comments, especially since it was reported by multiple mainstream media, including The Verge, Bleeping Computer, and Times of India. However, that’s not what we witnessed, which suggests angry users did not uninstall the application en masse, either.
It is challenging for IT departments to convince their fellow co-workers not to create a shadow IT environment. Security teams should train colleagues to recognize the impact of data breaches in the cloud services they use, as well as drop any compromised service that did not limit damage. This is what happened in this case.
Another important takeaway is that security teams should publicize the major data breaches affecting cloud services inside their company. This would raise awareness about the dangers of certain applications, and remind employees to stop using a software that was the victim of a data breach.
Security teams should implement real-time digital footprint monitoring to detect potential data breaches stemming from shadow IT applications. This practice detects employee, customer, and intellectual property mentions in real-time. Keeping a close eye on your digital footprint will help you get started with your investigation faster, reduce incident costs, and significantly lower stress and impact associated with data breaches.
With the proper training, employees will understand the dangers of shadow IT, and will refrain from adopting unauthorized applications, no matter how tempting that may be. Training could turn a bad event such as a data breach into a strong signal that forces change and prevents the use of shadow IT applications.





