
A significant challenge for security teams is to extract intelligence from open-source information. Malicious actors routinely post advertisements like the one below. This actor is offering up a method, but provides little to no clues as to how that method works, and how to protect against it.
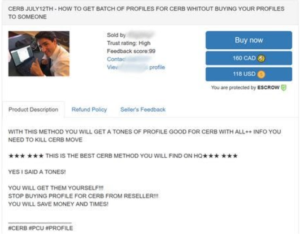
This is just an example of how challenging it can be to extract intelligence from a market or forum. In a previous entry on this blog, we developed a new method to monitor malicious actors by analyzing the contracts they posted on the largest English hacking forum.
While valuable, this analysis was limited by the public nature of the forum. Indeed, being a public website, the range of tools advertised in the contracts was limited, for fear of attracting the attention of authorities.
We overcome this limit in this blog post by analyzing the job postings (help wanted) section of a large private darkweb Russian hacking forum. The malicious actors advertising in that section may be inclined to be more open, given the privateness of the setting and the use of the Russian language.
This blog post describes the most common types of “help wanted” posts. Understanding the labor demands helps us identify the type of threats to be launched in upcoming weeks and months by identifying the most sought-after tools and skill sets. Where there is a demand for labor, there is likely a particularly profitable exploit or vulnerability in a firm’s or organization’s security infrastructure.
The Data
During May 2020, 154 “help wanted” posts were created on a large private dark web Russian forum.
As many as 102 (66%) of these were in search of a developer. Developers are brought on to a team of hackers to code just about any tool a malicious actor may need to achieve their goals. This includes creating new forms of malware, web scrapers, and tools designed for mounting phishing attacks.
The next most common type of job posting, with 32 (21%) postings, was for general hacking services. Hackers are enlisted to access secure networks and databases that other malicious actors may not have the skills or know-how to break into. These hackers are most commonly recruited to break into websites and email accounts. A small but significant portion are also hired for their skills in cracking encrypted files.
We identified 6 categories of interest:
- Malware development
- Phishing tools
- Website hacking
- Email hacking
- Encryption cracking
- Web scraping
The Job Postings
1. Malware development
Some 34% of job postings need a malware program developed. Those who know how to work with malware are among the most sought-out professionals by malicious actors. According to the job postings, the biggest challenge malicious actors actually face is bypassing the antivirus and other security software on the victims’ workstations. The custom nature of the malware vastly decreases the risks of detection and increases the chances of success of infection. With this in mind, many job postings for malware developers are requests for individuals who specialize in masking malicious software as legitimate programs. The quote below is requesting the help of someone to do just that.
“in search of someone who can disguise my executable as a certificate.”
2. Phishing tools
About 3% of “help wanted” posts were phishing related. As previously explored on this blog, phishing is a significant threat for firms of all shapes and sizes. Mounting a successful phishing attack is no small feat. It takes the coordination of several malicious actors, working together to assemble all the necessary pieces.
For example, a successful email phishing attack requires that the victim be convinced of the legitimacy of the attacker at every step. This means that every detail, down to the email received by the victim, appears legitimate. These so called “letters” often include randomized elements to avoid spam filters, and can be custom designed by malicious actors:
“On an ongoing basis, a coder of small HTML letters is required.
3 letters per week, payment fixed $600 per month”
Phishing websites are quickly flagged and taken down by major web hosting services. Likewise, most web browsers will detect fraudulent websites, and warn the end-user before continuing to webpages. Malicious actors are therefore on the lookout for new solutions and tools to eliminate these warning messages:
Hello everyone.
I am trying to spam.
I have my own bases [phishing sites] (not public).
But their contents are quickly flagged as dangerous sites.
Ready to work with people who have software for Windows and Android, or who knows how long to keep a phishing site so that it is not marked in red.“
3. Website hacking
About 9% of “help wanted” posts are in search of an individual capable of breaking into websites. Malicious actors typically want access to steal sensitive information found on the website’s backend. This can include customer data, executive credentials or credit card information. Malicious actors will most likely target websites they deem to have lower security standards:
“I am looking for a professional hacker for a website without strong protection.
Need to pull out the customer database.
Sites of the subject I need are not very protected.”
Backend databases are typically the primary targets of malicious actors. With access to this data, malicious actors can resell the information for a quick profit.
“I am looking for people who have experience in Internet security.
I am looking for people who know how to dump databases from websites.
I’ll be able to turn your dumps into money quickly and effectively.
I will not share your dumps, will not release them and nobody will know they exist.
If you prove that you’re capable, I’ll show you what I do with them.
I can give you targets, or we can work with what you have / get.”
4. Email hacking
Another 3% of “help wanted” posts are looking for hackers who can steal email credentials. With access to email account credentials, malicious actors can pursue a variety of tasks. For example, with access to a trusted email account, a malicious actor can mount a more convincing phishing attack. They can also use the account to access sensitive corporate or personal information. Finally, in the worst case scenario, with a compromised c-suite corporate email account, a malicious actor can utilize the account to authorize money transfers to their own accounts.
“I need hacking domain email, or the ability to get in the mailbox on a specific domain if possible.
In the worst case, I need to gain access to the domain.
I will consider any suggestions.
Orders with periodic frequency will arrive.”
5. Encryption cracking
Some 2% of “help wanted” posts are looking to recruit malicious actors to crack encrypted databases and documents. Even if a malicious actor is successful in stealing sensitive information from an individual or business, the raw data may be inaccessible, due to encryption or password protection. A malicious actor will therefore have to outsource to a hacker skilled in brute-forcing their way into these databases. The most elite of these hackers can provide specialized hardware to run through thousands of different decryption keys in a short time:
“Decryption of hashes and dumps.
We offer you decryption of your dumps.
We take a large list of algorithms.
The total capacity of more than 60 video cards is 1080ti.”
6. Web scraping
Finally, just under 5% of job postings are looking for an individual to develop web scraper programs. Web scraping is the process of collecting large amounts of data from a website, usually through an automated program, and then saved to a database. Although web scraping is not an inherently malicious activity, cybercriminals will scrape dozens of websites looking for credentials and other sensitive information that can then be resold for profit.
On the dark web hacker forum we investigated, malicious actors were looking for individuals to both develop and run these scrapers.
“I need an encoder to write custom software.
Short info:
There should be a premiere panel where I could add URLs, credentials and proxy accounts.
The software would then go to each URL with these credentials using a proxy.
It would open certain sections, run searches and collect emails by opening resumes files.
The emails would be stored in a file that I can then download locally.
Job starts at $150 with a ceiling around $500.
Price will depend on how everything is completed.
We can discuss the price.
We need a person who is ready to start work ASAP and do all the buzz.”
In some cases, a professional developer is not even needed, as the malicious actor may already have access to the necessary tools. It therefore only becomes a matter of outsourcing the tedious labour of scraping to anyone willing to take the job:
“I am looking for a performer, the knowledge of the student will also go. Good day, I’m looking for a person who needs work on a permanent basis. Knowledge is zero, you will need to walk on Google and collect the sites I need. A weekly payment of $ 350 =) For whom I have full time, please write to the contacts in the signature, I will drop the money in the guarantor or payment upon the fact of the work done) And yes, I ask you not to write to people with rega from this year, no offense, but there is little trust in such people) I am waiting for the daredevil, if the result suits me, the payment will increase!” (thread id: 172863)
Conclusion
The job postings on a large private darkweb Russian hacking forum draw a picture of the threats most companies are facing and are likely to face in the near future. In particular, we identified 4 trends worth keeping in mind for security teams.
- There are no silver bullets in cybersecurity. Security tools (antivirus, endpoint detection and response systems), especially those based on signature detection, are likely to offer only a limited protection against malicious actors active on private Russian forums. Many of the job postings we read discussed the requirement of having a custom malware or a custom phishing site that are much harder to detect. Behavior based tools may provide a higher level of security but will still be challenged by many malware. A solution to this problem is to increase employee training workshops so they can easily detect spam and suspicious files, and report them to security teams.
- Data is the most valuable resource in the 21st century and malicious actors are doing everything they can to steal them. Our analysis suggests that encrypting sensitive and confidential information is but a necessary first step, as malicious actors can rent massive cracking networks of servers to break encryption. Strong passwords and encryption algorithms provide a good first layer of protection. Intrusion detection systems and close monitoring of data exfiltration are also essential to detect breaches before they have had the opportunity to leak all of databases. Using digital risk prevention services such as that of Flare Systems can also help your firm detect breaches in a matter of minutes, or days, rather than months. This can prevent most of the USD$4 million average cost of a data breach.
- Malicious actors are always on the lookout for open-source intelligence that can be used to attack firms. Their interest in web scraping and collecting contact information shows that malicious actors are organized and have built a long supply chain to ensure the success of their attacks. Firms should ensure they control their information that is made public, either on corporate servers or on the personal pages of their employees. Any leak could provide the information needed to successfully take over an account.
- Finally, email accounts are a very valuable target for malicious actors. Brain Krebs astutely estimates the value of a hacked email account. Email accounts should be protected with the same energy and attention to details as the main corporate databases. Employees should also receive the proper training to detect if their email account has been compromised to reduce the time to know of cyberthreats.
By reading job postings, security teams can better understand where next threats are likely to come from, what that threat might look like, and understand if their current security tools can stand a chance against future attacks. Only by knowing the malicious actors can security teams build the right defenses for their firms. There is, after all, no use building a wall when the attacker can dig a tunnel or use a helicopter.
With a slate of robust tools designed to automatically monitor the dark web, Flare Systems can provide daily updates on how your organization or company may be targeted by malicious actors. For more information or for a demonstration of our services, contact [email protected].





