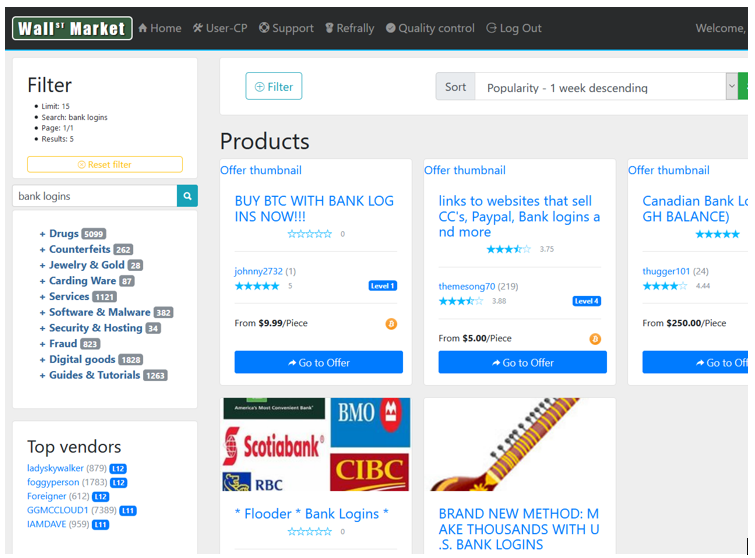
The darknet provides a relatively anonymous environment in which to buy and sell illicit goods and services. Transactions take place in illicit markets that operate in a similar fashion to eBay and Amazon. The markets invite independent vendors to create profiles and product pages which customers browse. Customers add products to their carts and pay for them with cryptocurrencies like bitcoin. In the case of physical goods, the customers receive their goods through the mail, hidden in packages.
Figure 1: Screenshot of the Wall Street online illicit market
Darknet illicit markets offer a wide range of illicit products such as drugs, hacking services and stolen financial information. One of the most entertaining listing that was posted recently was one for a cocaine lottery. Customers would purchase a lottery ticket and stand the chance of winning 100 grams of cocaine if their number was drawn at the end of the month! The product page did not indicate however if Deloitte was supervising the draw or not…
Nobody sells gold for the price of silver
Our clients pay a close attention to product listings that advertise stolen financial information. These come in many forms: logins to web banking accounts, credit card numbers with their owners’ personal details. There has been much debate in the scientific community as to whether these product listings were of any value. Indeed, many vendors never deliver on their promise to send the information they sold. Microsoft researchers published a paper on this issue in 2009 with the ominous title “Nobody Sells Gold for the Price of Silver”. The researchers wonder why vendors would list credit cards with a balance of thousands of dollars for sale for under $20. Could it be because while the theoretical value of the information is in the thousands the dollars, the actual value of the information is much lower? Could this be explained by the low quality of the stolen financial information?
It is often difficult to differentiate between the good and the bad stolen financial information on sale. Figure 2 presents a typical forum post advertising bank logins. That ad does not stand out from the many other posts that one can find on the darknet. The user describes the products for sale. He also boasts about his ability to steal information from U.S. banks, Canadian banks and retailers. The user also mentions that he can provide identity cards like driver licenses.
Figure 2: Product advertising on darknet forum
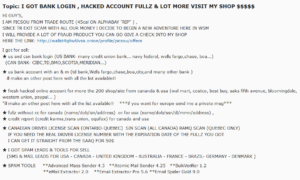
This advertising may seem suspicious at first. Indeed, very few vendors provide such a wide range of services reliably. Many analysts may classify this user as a scammer trying to make a quick buck by never delivering on his promises. A more thorough analysis however suggests that the user does have something of value to sell. Between October and December 2018, the user continues to advertise his products through forum posts and darknet illicit markets. He even goes as far as offering holiday discounts beginning on December 26th! On December 31st, the user posts an intriguing new message title “New method for generate bank login”. The post states that:
“I’m selling the new method for generate bank login […] I will provide a full guide + a video on how to generate the account, how to bypass the bank security, how to get the real security answer and how to change the password […] I will also give you all the assistance you need to generate your first login […] you can make minimum 10k a day with this method if you know how to cash out bank login by making transfer , emt, or bank take out”.
This is a shift for this user as anyone can buy stolen financial information online in bulk and then resale it online card by card. Very few people actually have an exploit that will allow them to bypass bank security to gain access to customer files. On February 28th, the user makes another post of interest. It advertises logins for sale for the web logins of the Société des alcools du Québec (S.A.Q.). This is the government-run agency that sells all of the alcohol in the Province of Quebec. Of course, everyone knows about the S.A.Q. in Quebec – many of us are even loyal customers! The agency is not all that well known outside of Quebec. Could this indicate that this user, offering an exploit to bypass a Canadian bank security system AND logins for a Quebec agency, be located in Quebec? Perhaps…
Online illicit markets and cyber threat intelligence
At first, this user does not stand out from his peers. He is just another vendor advertising stolen financial information on the darknet. His case however showcases the value of cyber threat intelligence and the services of Flare Systems.
First, by receiving alerts on the user’s posts, a bank security analyst could be informed of the progression in the user’s activities. The analyst could notice that the user had suddenly become a person of interest that warranted further attention. Indeed, by offering a method to bypass bank security, the user casts himself in a whole new category. The December post could have therefore been a good reason to launch a code review at the bank to identify the exploit that was being sold.
It is possible that the code review would have turned up nothing and the threat at that point may have been categorized as inexistant. This is why the February post with the details of a bank user is crucial however. It provides a lead for the code review to identify how the account was accessed, by whom and to stop the exploit from exposing other client accounts.
Take-away
This user’s post lead us to believe that the threat he posed increased over time. His products could very well have impacted the bank’s operations if they had been distributed widely. A security team montoring the user’s posts would however have been ready to deal with this threat. The team could have used the actionable intelligence to prevent or limit the threat the user posed.
Subscribe to our blog to stay up to date on darknet and cybersecurity.